Understanding the Basics of AWS Key Management and Secrets Management
In the realm of cloud security, Amazon Web Services (AWS) offers robust solutions for managing sensitive data. Two pivotal services in this domain are AWS Key Management Service (KMS) and AWS Secrets Manager. Understanding their distinct roles is crucial for securing your cloud infrastructure. This article begins a comparative analysis of these two essential services, highlighting their functionalities and use cases. The ongoing discussion aims to help you make informed decisions about which service best suits your specific needs, especially when deciding between aws key management service vs secrets manager.
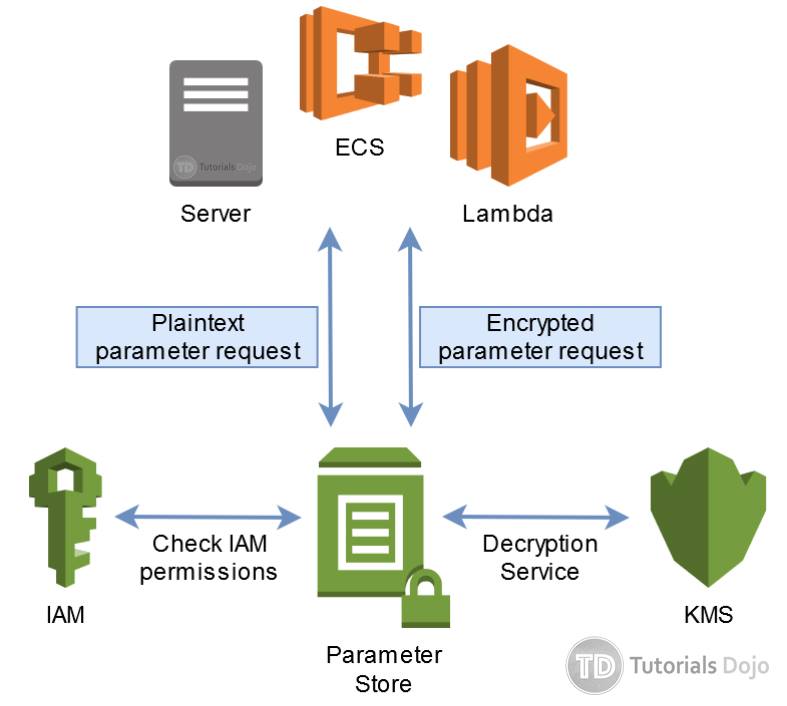
AWS Key Management Service (KMS) is a managed service that simplifies the creation and control of cryptographic keys used to encrypt your data. KMS enables you to centrally manage encryption keys and define the policies that control how these keys can be used. It integrates seamlessly with other AWS services, allowing you to encrypt data at rest in services like Amazon S3, Amazon EBS, and Amazon RDS. KMS focuses primarily on encryption and decryption operations, ensuring the confidentiality of your data. With its robust features and integration capabilities, KMS is a cornerstone of aws key management service vs secrets manager. AWS KMS excels at providing encryption capabilities at scale.
AWS Secrets Manager, on the other hand, is designed to securely store and manage sensitive information, such as passwords, API keys, database credentials, and other secrets. Unlike KMS, which focuses on encryption, Secrets Manager is tailored to the secure storage and retrieval of secrets. It enables you to rotate secrets automatically, reducing the risk of unauthorized access. Secrets Manager integrates with services like Amazon RDS, Amazon Redshift, and Amazon ECS, allowing you to retrieve secrets programmatically from your applications. Choosing between aws key management service vs secrets manager depends largely on whether your primary need is encryption or the secure storage and management of secrets. Secrets Manager helps you to follow security best practices by regularly rotating credentials, thereby minimizing the risk of compromise. It offers a centralized, secure repository for your sensitive credentials. AWS Secrets Manager is a critical component for managing and protecting access credentials effectively.
Key Differences Between KMS and Secrets Manager: A Detailed Breakdown
When comparing AWS Key Management Service (KMS) and AWS Secrets Manager, several key distinctions emerge. Understanding these differences is crucial for selecting the appropriate service for your specific security needs. KMS primarily focuses on encryption, providing the tools to create, manage, and control encryption keys used to protect your data. Secrets Manager, on the other hand, specializes in securely storing and managing sensitive information like passwords, API keys, and database credentials.
Encryption capabilities are a core differentiator. KMS offers a robust suite of cryptographic functions, allowing you to encrypt data at rest and in transit. It integrates seamlessly with other AWS services, such as EBS, S3, and RDS, enabling you to easily encrypt your resources. Secrets Manager doesn’t directly encrypt data; instead, it stores secrets in an encrypted format using KMS. This adds a layer of security to the secrets themselves. Rotation policies also differ significantly. Secrets Manager provides automatic secret rotation for supported database services, reducing the risk of compromised credentials. While KMS doesn’t offer automatic key rotation in the same way, it does support key rotation, requiring a more manual approach to update encrypted data with the new key.
Access control is managed through IAM in both services, but the granularity differs. KMS allows fine-grained control over who can use specific keys for encryption and decryption. Secrets Manager controls access to the secrets themselves, determining who can retrieve and manage them. Supported secret types also play a role in the choice between aws key management service vs secrets manager. KMS is agnostic to the type of data it encrypts, while Secrets Manager is specifically designed for managing credentials and other sensitive text-based information. Finally, pricing models vary. KMS charges based on key usage and storage, while Secrets Manager charges based on the number of secrets stored and API requests. Understanding these pricing differences is essential for optimizing costs. Choosing between aws key management service vs secrets manager requires a careful consideration of these factors. For encrypting data at rest, KMS is the superior option; for managing credentials, Secrets Manager is the right choice. A comprehensive understanding of aws key management service vs secrets manager is critical for making informed decisions. Ultimately, a robust understanding of aws key management service vs secrets manager ensures optimal security within the AWS cloud environment.
How to Choose the Right AWS Security Service for Your Needs
Selecting between AWS Key Management Service (KMS) and AWS Secrets Manager requires careful consideration of your specific security needs and infrastructure. This section provides a framework to guide your decision-making process, helping you determine which service best aligns with your requirements. The first consideration is: What type of data are you protecting? If you need to encrypt data at rest, such as EBS volumes or S3 buckets, KMS is the ideal choice. If you’re managing sensitive credentials like database passwords or API keys, Secrets Manager is more appropriate. Understanding the nature of your data is the first step in making the right choice in the aws key management service vs secrets manager debate.
Next, consider the level of encryption needed. KMS provides robust encryption capabilities using hardware security modules (HSMs) and supports various cryptographic algorithms. Secrets Manager focuses on secure storage and rotation of secrets, but relies on KMS for encrypting those secrets at rest. If compliance regulations dictate specific encryption standards, KMS offers greater flexibility. Evaluate your compliance requirements to determine if KMS’s advanced encryption options are necessary. Another vital factor is access control. Both services integrate with AWS Identity and Access Management (IAM), allowing you to grant granular permissions to users and services. However, Secrets Manager simplifies the process of granting access to secrets, as it is specifically designed for managing credentials. Assess your existing IAM policies and how easily you can integrate each service into your current access control framework. This aws key management service vs secrets manager discussion highlights the IAM strengths.
To further assist your decision, the table below summarizes key features and use cases for quick reference, adding more clarity to the aws key management service vs secrets manager decision.
| Feature | AWS KMS | AWS Secrets Manager |
|———————-|—————————————–|———————————————–|
| Core Functionality | Encryption and key management | Secure storage and rotation of secrets |
| Data Type | Data at rest (EBS, S3), code signing | Passwords, API keys, database credentials |
| Encryption | Strong encryption with HSM support | Encryption at rest (integrates with KMS) |
| Rotation | Manual key rotation | Automatic secret rotation |
| Access Control | IAM integration | IAM integration, simplified secret access |
| Compliance | Meets various compliance standards | Helps meet compliance requirements |
| Use Cases | Encrypting data, code signing | Managing database credentials, API keys |
Secrets Manager vs KMS: Use Cases and Practical Examples
Context_4: AWS Key Management Service (KMS) and AWS Secrets Manager address distinct security needs, and their application varies based on specific scenarios. KMS excels when encryption is paramount, while Secrets Manager shines in centralized secret storage and rotation. Understanding these differences is crucial for choosing the right service or combining them for enhanced security. This section explores practical examples, highlighting when to use each service and demonstrating basic implementation steps via the AWS console or CLI. The goal is to clarify when to use aws key management service vs secrets manager.
Consider encrypting EBS volumes. If you want to encrypt your Elastic Block Storage (EBS) volumes, KMS is a perfect fit. Using the AWS console, you can specify a KMS key when creating a new volume or encrypt an existing one. This key encrypts all data written to the volume, protecting it at rest. Similarly, KMS is ideal for encrypting data stored in S3 buckets. When uploading objects, you can specify a KMS key to encrypt the data. KMS manages the encryption keys, controlling who can access the data. For example, using the AWS CLI, you can specify the `–ssekms-key-id` parameter when uploading an object to S3, ensuring it’s encrypted with your chosen KMS key. These processes enhance aws key management service vs secrets manager.
Secrets Manager is best for handling database credentials. Imagine a web application needs to connect to a database. Storing the database password directly in the application code is a security risk. Secrets Manager provides a secure, centralized location to store this password. You can create a secret in Secrets Manager, storing the database credentials. The application can then retrieve these credentials programmatically at runtime. Secrets Manager also supports automatic rotation of these credentials, further enhancing security. The AWS CLI command `aws secretsmanager create-secret` allows you to create a new secret, specifying the secret name and the initial credentials. The application retrieves the secret using the `aws secretsmanager get-secret-value` command. Consider a scenario where an application needs an API key to interact with a third-party service. Secrets Manager can securely store and manage this API key, preventing unauthorized access. This ability to rotate and centralize sensitive credentials showcases aws key management service vs secrets manager, demonstrating how Secrets Manager simplifies credential management. When dealing with sensitive information like API keys, passwords, and database connection strings, Secrets Manager is often the most appropriate solution.
Step-by-Step Guide: How to Store Database Credentials Securely with Secrets Manager
This section offers a hands-on tutorial for securing database credentials using AWS Secrets Manager. Securing database credentials is a critical aspect of cloud security, and AWS Secrets Manager simplifies this process. We will walk through creating a secret, configuring automatic rotation, and retrieving it programmatically. This ensures that sensitive information remains protected, and regularly updated, reducing the risk of unauthorized access. This detailed guide showcases how AWS Secrets Manager effectively addresses the challenges of aws key management service vs secrets manager in practical application.
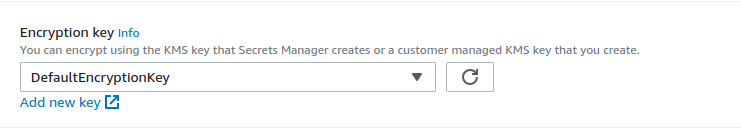
Step 1: Creating a Secret Access the AWS Secrets Manager console. Choose “Store a new secret.” Select the type of secret you want to store. For database credentials, choose “Credentials for RDS database”. Specify the database username, password, and the RDS instance. Choose an encryption key. The default AWS managed key can be used, or a custom key from AWS Key Management Service (KMS) can be selected. The encryption key adds a layer of protection. Give your secret a descriptive name. This name helps in identifying and managing the secret later. Add optional tags for better organization and resource management. Review the configuration and store the secret. Step 2: Configuring Automatic Rotation Automatic rotation is an important security practice. Edit the secret and navigate to the “Rotation configuration” section. Enable automatic rotation. Select a Lambda function that Secrets Manager uses to rotate the credentials. Secrets Manager provides pre-built Lambda functions for common database types. Configure the rotation schedule. Define how often the credentials should be rotated (e.g., every 30 days). Ensure the Lambda function has the necessary permissions to access the database and update the secret. Regular rotation of credentials significantly enhances security, a key differentiator in aws key management service vs secrets manager decisions. Step 3: Retrieving the Secret Programmatically (Python/Boto3) To retrieve the secret, use the AWS SDK (Boto3) in Python. First, install the Boto3 library: pip install boto3. Use the following Python code snippet to retrieve the secret:
import boto3
import json
def get_secret():
secret_name = "your-secret-name"
region_name = "your-aws-region"
session = boto3.session.Session()
client = session.client(service_name='secretsmanager', region_name=region_name)
try:
get_secret_value_response = client.get_secret_value(SecretId=secret_name)
except ClientError as e:
raise e
secret = get_secret_value_response['SecretString']
return json.loads(secret)
secret_data = get_secret()
username = secret_data['username']
password = secret_data['password']
print(f"Username: {username}")
print(f"Password: {password}")
Replace “your-secret-name” and “your-aws-region” with the appropriate values. This code retrieves the secret, parses the JSON, and extracts the username and password. Properly managing access through IAM roles is crucial for aws key management service vs secrets manager implementations.
By following these steps, you can effectively use AWS Secrets Manager to store and manage database credentials securely. This hands-on approach helps in understanding the practical benefits and implementation details, solidifying the knowledge of aws key management service vs secrets manager. Remember to adhere to best practices, such as using least privilege access and regularly monitoring secret access logs, to maintain a strong security posture. This detailed walkthrough helps illustrate the differences when considering aws key management service vs secrets manager.
Boosting Security: Combining KMS and Secrets Manager for Enhanced Protection
In complex cloud environments, a layered security approach is crucial. While AWS Key Management Service (KMS) and AWS Secrets Manager offer robust security independently, combining them provides enhanced protection. This strategy addresses various threat vectors and strengthens your overall security posture. The synergy between these services provides a more robust defense than either could offer alone, especially when considering aws key management service vs secrets manager.
One powerful combination involves using KMS to encrypt the secrets stored within Secrets Manager. Secrets Manager natively encrypts secrets at rest, but integrating KMS allows you to manage the encryption keys yourself. You maintain full control over the keys used to protect your sensitive information. This is particularly valuable when dealing with highly sensitive data or strict compliance requirements. The process involves creating a KMS key and then configuring Secrets Manager to use that key for encrypting the secrets it stores. This way, even if Secrets Manager were compromised, the attacker would still need access to the KMS key to decrypt the secrets, adding a significant barrier. This is a critical differentiator when evaluating aws key management service vs secrets manager for sensitive data.
Another effective strategy is leveraging KMS to encrypt data outside of Secrets Manager, such as database connection strings or API keys stored in application configuration files. Secrets Manager can then be used to securely store the KMS key itself, albeit with appropriate access controls. This approach ensures that your data is encrypted at rest and in transit, and that the key required to decrypt it is also securely managed. The combined use of these services also simplifies auditing and compliance efforts. AWS CloudTrail can track all API calls made to both KMS and Secrets Manager. This allows you to monitor who is accessing secrets, when they are being accessed, and whether any unauthorized attempts are being made. Regular monitoring and auditing are essential for maintaining a strong security posture. When considering aws key management service vs secrets manager, remember that the best approach may involve using both services in a coordinated manner to achieve optimal security and control. The choice of whether to use aws key management service vs secrets manager depends on your specific needs. However, using them in conjunction offers a superior approach.
Cost Considerations: Analyzing the Pricing of KMS and Secrets Manager
Understanding the pricing structures of AWS Key Management Service (KMS) and AWS Secrets Manager is crucial for cost optimization. AWS key management service vs secrets manager offer distinct pricing models reflecting their functionalities. KMS primarily charges based on the number of KMS keys stored and the number of cryptographic requests made. The cost per key is relatively low, but the request fees can accumulate with high-volume encryption or decryption operations. Secrets Manager, on the other hand, charges based on the number of secrets stored and the number of API calls made to retrieve those secrets. This includes charges for secret storage per month and per 10,000 API calls.
When comparing aws key management service vs secrets manager, it’s vital to analyze usage patterns. For infrequent secret access and limited encryption needs, KMS might prove more economical. If your application requires frequent rotation and retrieval of numerous secrets, Secrets Manager could be more cost-effective. For example, encrypting EBS volumes using KMS will incur costs based on the encryption keys and API requests during volume creation and access. Storing database credentials in Secrets Manager will involve costs for storing each secret and API calls made by your application to fetch those credentials. Consider a scenario where a web application needs to access database credentials multiple times per minute. The API call costs associated with Secrets Manager could become significant over time.
Strategies to optimize costs involve careful planning and monitoring. For KMS, consider caching frequently used keys to reduce API calls or utilizing batch operations where possible. With Secrets Manager, reduce unnecessary API calls by caching secrets within your application, while still adhering to security best practices and rotation policies. Regularly review AWS Cost Explorer reports to identify cost drivers and areas for optimization. Evaluate whether automatic secret rotation is truly necessary for all secrets. Adjust the rotation frequency to balance security needs with cost efficiency. By understanding the nuances of each service’s pricing model and implementing cost optimization strategies, organizations can effectively manage their AWS security expenses while maintaining a strong security posture. This ensures that aws key management service vs secrets manager are used efficiently and effectively within your cloud environment.
Long-Term Security: Best Practices for Managing Secrets and Keys in AWS
Securing secrets and keys in AWS requires a proactive, ongoing approach. It is not a one-time setup. Implementing robust strategies for access control, rotation, monitoring, and disaster recovery is critical. These practices ensure the confidentiality and integrity of sensitive information. Regularly reviewing and updating security measures is crucial to adapt to emerging threats and evolving AWS best practices. The comparison between aws key management service vs secrets manager highlights the necessity of choosing the right tool and practices.
Least privilege access is a fundamental principle. Grant only the minimum necessary permissions to users and services. Utilize IAM roles and policies effectively. Regularly rotate secrets. Automatic rotation, a key feature of Secrets Manager, reduces the risk of compromised credentials. Implement comprehensive monitoring and auditing. AWS CloudTrail logs API calls to both KMS and Secrets Manager. This allows for tracking access and identifying potential security breaches. Integrate these logs with security information and event management (SIEM) systems for real-time threat detection. A well-defined disaster recovery plan is also essential. Regularly back up encryption keys and secrets. Test the recovery process to ensure business continuity. Understanding the nuances of aws key management service vs secrets manager in disaster recovery scenarios is vital.
Stay informed about the latest AWS security updates and best practices. AWS continuously releases new features and recommendations. Adapt your security strategies accordingly. Consider employing multi-factor authentication (MFA) for accessing AWS accounts and resources. This adds an extra layer of security against unauthorized access. Regularly assess your security posture through vulnerability scanning and penetration testing. Address any identified weaknesses promptly. Proper management of secrets and keys is an ongoing responsibility. This includes a combination of technical controls, policies, and awareness training. Using aws key management service vs secrets manager effectively relies on a strong understanding of these best practices. Staying up-to-date and proactive will allow for a stronger security posture and adapting to evolving threats.