IAM Roles vs. IAM Users: Key Concepts and Differences
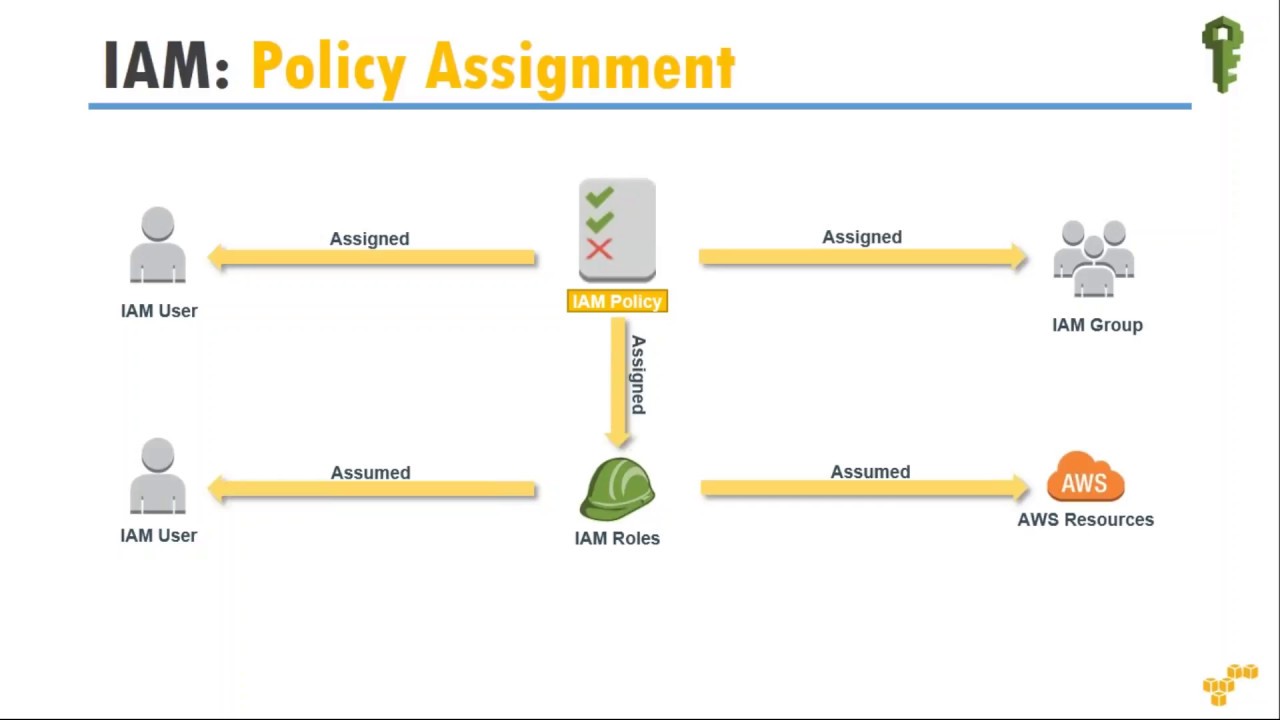
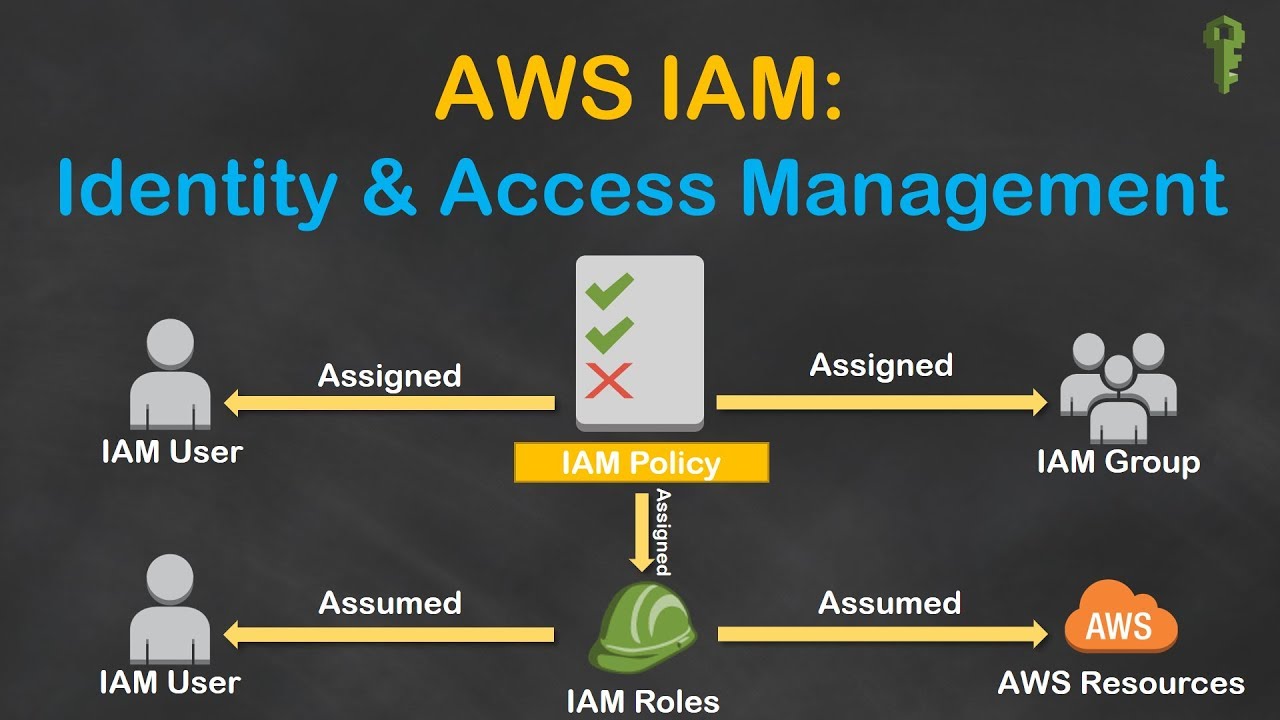
Identity and Access Management (IAM) is a crucial aspect of AWS, enabling you to manage user identities and control access to various resources. IAM Roles and IAM Users are two distinct entities within the IAM framework, each serving unique purposes. IAM Roles are designed for temporary access, while IAM Users cater to long-term access requirements. Moreover, IAM Roles are not tied to a specific user, whereas IAM Users are associated with individual users.
When to Use IAM Roles
IAM Roles are particularly useful in several scenarios where temporary access to AWS resources is required. Some common examples include granting access to AWS services, applications, or users who need to perform specific tasks without long-term credentials. This section will explore these scenarios in more detail.
Scenario 1: Granting Access to AWS Services
IAM Roles can be used to allow AWS services to access each other’s resources. For instance, an Amazon S3 bucket may need to grant permission to an Amazon EC2 instance to read or write data. In this case, you can create an IAM Role for the EC2 instance and attach a policy that grants the necessary permissions to the S3 bucket.
Scenario 2: Temporary Access for External Users
IAM Roles can be assumed by external users or systems that require temporary access to your AWS resources. For example, a third-party application might need to access your Amazon SNS topics or Amazon SQS queues for a limited period. By creating an IAM Role with the required permissions and sharing temporary security credentials, you can provide secure access without exposing your long-term AWS credentials.
Scenario 3: Applications Requiring Access to AWS Resources
IAM Roles can be used by applications that need to access AWS resources. For example, a custom application might require permissions to read from an Amazon S3 bucket or write to an Amazon DynamoDB table. By creating an IAM Role with the necessary permissions and configuring the application to assume the Role, you can ensure secure and controlled access to the required resources.
Scenario 4: Users with Short-Term Tasks
IAM Roles can be helpful for users who need to perform short-term tasks or have limited permissions. For instance, a developer might require access to specific AWS resources for a limited time to debug an issue or perform maintenance tasks. By creating an IAM Role with the required permissions and having the developer assume the Role, you can ensure that the user has the necessary access without granting long-term permissions.
When to Use IAM Users
IAM Users are designed for long-term access to AWS resources, primarily for human users who require consistent access to manage and interact with AWS services. This section will discuss scenarios where IAM Users are the ideal choice and the importance of associating IAM Users with specific groups and managing their permissions effectively.
Scenario 1: Long-Term Access for Human Users
IAM Users are the best option for human users who need consistent access to AWS resources. For example, developers, system administrators, and DevOps engineers require IAM Users to manage AWS services, deploy applications, and perform various tasks. By creating IAM Users for each human user, you can manage their access levels, permissions, and activities more effectively.
Scenario 2: Grouping Users with Similar Access Requirements
Associating IAM Users with specific groups is essential for managing permissions effectively. By grouping users with similar access requirements, you can assign policies to the group, ensuring that all members have the necessary permissions. This approach simplifies permission management and reduces the likelihood of errors or misconfigurations.
Scenario 3: Least Privilege Principle
Applying the principle of least privilege is crucial for maintaining a secure AWS environment. This principle involves granting users the minimum permissions required to perform their tasks. By creating IAM Users with the least privilege principle in mind, you can minimize the risk of unauthorized access or accidental modifications to AWS resources.
Scenario 4: Regularly Reviewing Permissions
Regularly reviewing IAM Users’ permissions is essential to ensure that access levels are up-to-date and reflect the current needs of the users. Removing unnecessary permissions and updating access levels as users’ roles change helps maintain a secure and well-managed AWS environment.
How to Implement IAM Roles and IAM Users
This section provides a step-by-step guide on creating and managing IAM Roles and IAM Users in the AWS environment. Additionally, it includes best practices and tips for organizing IAM entities and setting up permissions.
Step 1: Create an IAM Role
To create an IAM Role, sign in to the AWS Management Console, navigate to the IAM service, and choose “Roles” from the left-hand menu. Click the “Create role” button and select the appropriate trusted entity (e.g., another AWS service, a federated user, or an AWS account) for your use case. Attach the necessary policies to the Role, providing the required permissions.
Step 2: Create an IAM User
To create an IAM User, navigate to the IAM service, choose “Users” from the left-hand menu, and click the “Add user” button. Enter the user’s name and access type (programmatic access, AWS Management Console access, or both), then click “Next.” Add the user to a group with appropriate permissions or create a custom policy to attach to the user. Finally, review the settings and click “Create user” to complete the process.
Best Practices and Tips
- Organize IAM entities using paths to categorize and structure users, groups, and roles.
- Regularly review and update IAM permissions to ensure they align with the principle of least privilege.
- Implement multi-factor authentication (MFA) for IAM Users to add an extra layer of security.
- Use IAM roles for applications to avoid embedding long-term AWS credentials in your code.
- Monitor IAM activities and permissions using AWS services like CloudTrail and AWS Trusted Advisor.
Managing Access with IAM Policies
IAM Policies play a crucial role in controlling access to AWS resources by defining permissions for IAM Roles and IAM Users. This section explains how to attach policies to IAM Roles and IAM Users and how to create custom policies.
Predefined Policies
AWS provides a wide range of predefined policies that cover common use cases. These policies can be attached to IAM Roles or IAM Users directly or indirectly through groups. Predefined policies simplify the management of permissions, as they are maintained and updated by AWS.
Custom Policies
Custom policies can be created to address specific access requirements. A custom policy consists of one or more policy statements, each defining permissions, resources, and conditions. When creating custom policies, it is essential to follow the principle of least privilege, granting only the necessary permissions to perform specific tasks.
Attaching Policies to IAM Roles and IAM Users
Policies can be attached to IAM Roles or IAM Users directly or indirectly through groups. To attach a policy, navigate to the IAM Role or IAM User, click the “Permissions” tab, and choose “Attach policies.” Select the policy you want to attach and click “Attach policy.”
Creating Custom Policies
To create a custom policy, navigate to the IAM service, choose “Policies” from the left-hand menu, and click the “Create policy” button. You can create a policy using the JSON editor or the visual editor. After creating the policy, click “Review policy” and provide a name and description. Finally, click “Create policy” to save it.
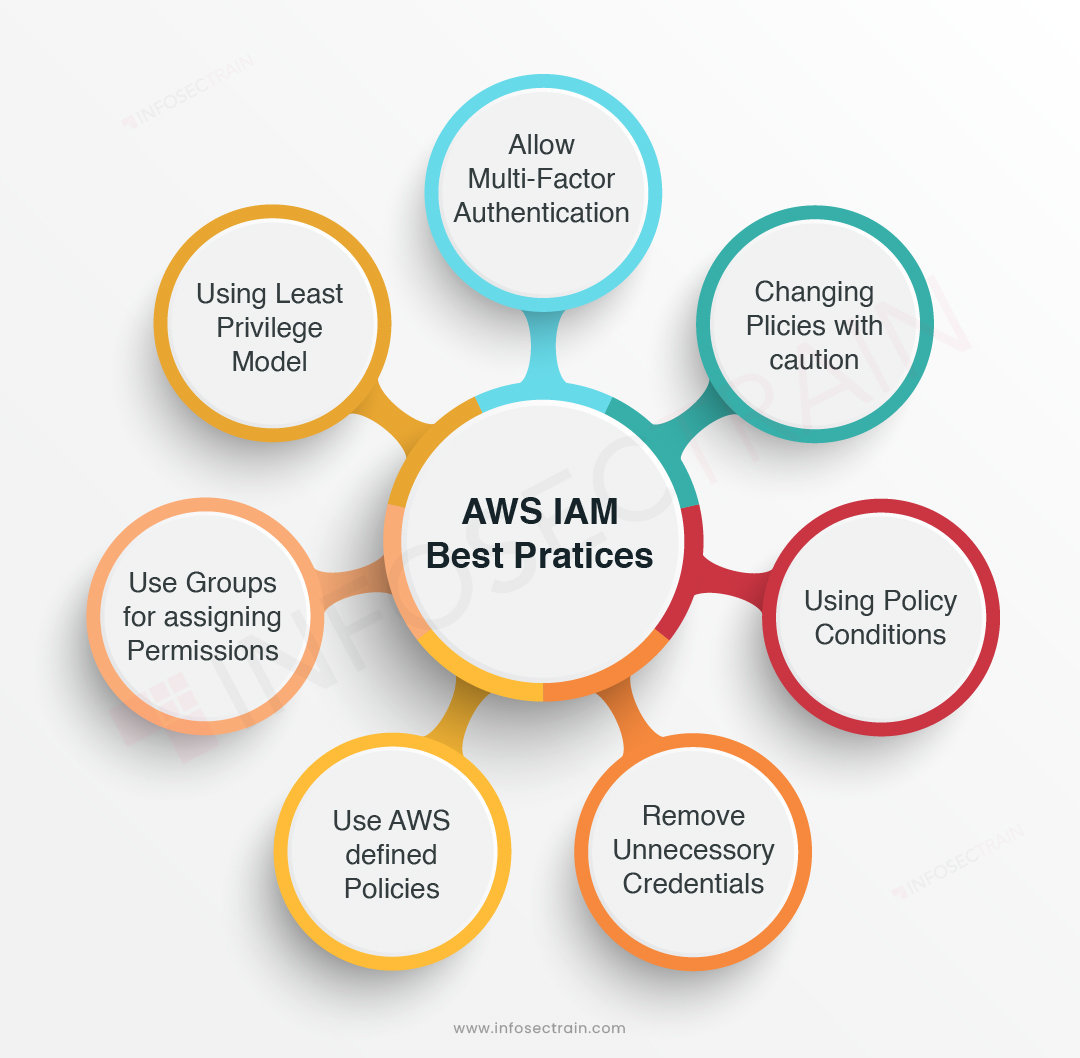
Security Best Practices for IAM Roles and IAM Users
Implementing security best practices for IAM Roles and IAM Users is crucial for maintaining a secure AWS environment. This section discusses several best practices, such as implementing multi-factor authentication (MFA), regularly reviewing permissions, and following the principle of least privilege.
Implement Multi-Factor Authentication (MFA)
Enabling MFA for IAM Users adds an extra layer of security by requiring a unique, one-time code in addition to the user’s password. MFA can be enabled for console sign-in and programmatic access, ensuring that even if a user’s password is compromised, the attacker cannot access the account without the MFA device.
Regularly Review Permissions
Regularly reviewing IAM permissions helps ensure that access levels are up-to-date and reflect the current needs of users and applications. Removing unnecessary permissions and updating access levels as users’ roles change helps maintain a secure and well-managed AWS environment.
Follow the Principle of Least Privilege
The principle of least privilege involves granting users the minimum permissions required to perform their tasks. By creating IAM Roles and IAM Users with the least privilege principle in mind, you can minimize the risk of unauthorized access or accidental modifications to AWS resources.
Additional Best Practices
- Use strong, unique passwords for IAM Users and periodically rotate them.
- Limit the number of IAM Users with administrative access.
- Monitor and audit IAM activities using AWS services like CloudTrail and AWS Trusted Advisor.
- Use IAM Roles for applications to avoid embedding long-term AWS credentials in your code.
Monitoring and Auditing IAM Activities
Monitoring and auditing IAM activities is essential for maintaining a secure AWS environment and staying informed about potential security risks. This section explains how to use AWS services like CloudTrail and AWS Trusted Advisor to monitor and audit IAM activities.
AWS CloudTrail
AWS CloudTrail is a service that enables auditing, monitoring, and compliance for AWS accounts. It records API calls made by or on behalf of IAM Users, IAM Roles, and AWS services and delivers log files to an S3 bucket for analysis and storage. CloudTrail helps you track IAM actions, identify security risks, and understand user behavior.
AWS Trusted Advisor
AWS Trusted Advisor is a service that helps you monitor your AWS resources and identify potential issues that could impact security or performance. It checks your AWS environment against best practices and provides recommendations for improving security and optimizing resources. Trusted Advisor includes checks for IAM entities, such as reviewing the use of MFA for IAM Users and identifying unused IAM roles and access keys.
Benefits of Tracking IAM Activities
- Detect unauthorized or suspicious activity in your AWS account.
- Ensure compliance with internal policies and external regulations.
- Identify potential security risks and take appropriate action.
- Monitor user behavior and optimize IAM entities for better resource management.
Troubleshooting Common IAM Issues: Resolving Access Denied Errors and Misconfigured Permissions
When working with AWS Identity and Access Management (IAM), you may encounter various issues related to IAM roles and IAM users. This article focuses on addressing common problems such as resolving access denied errors and fixing misconfigured permissions for the “iam role vs iam user” setup. Following these guidelines will help you effectively troubleshoot and overcome these challenges.
1. Access Denied Errors
Access denied errors typically occur when a user or role lacks the necessary permissions to perform a specific action. To resolve this issue, follow these steps:
- Review the error message: Carefully examine the error message to identify the resource, action, or service causing the issue. This information will help you pinpoint the required permissions.
- Check the IAM policy: Examine the IAM policy attached to the user or role to ensure it includes the necessary permissions. If not, update the policy accordingly.
- Verify resource-based policies: In some cases, resource-based policies (such as S3 bucket policies) may deny access. Ensure these policies are correctly configured and do not conflict with IAM policies.
- Confirm service control policies (SCPs): If you’re working in an AWS Organizations setup, SCPs may limit permissions. Verify that SCPs allow the required actions for the user or role.
2. Misconfigured Permissions
Misconfigured permissions can lead to unintended access or security vulnerabilities. To address this issue, consider the following best practices:
- Implement the principle of least privilege: Grant only the permissions required to perform specific tasks. Avoid overly permissive policies that may expose resources to unnecessary risks.
- Regularly review permissions: Periodically audit IAM policies, resource-based policies, and SCPs to ensure they remain up-to-date and aligned with your security requirements.
- Use IAM policy conditions: Utilize conditions in IAM policies to restrict access based on specific contexts, such as IP addresses, time of day, or request headers.
- Monitor IAM activity: Use AWS services like CloudTrail and AWS Trusted Advisor to track IAM actions and stay informed about potential security risks.
By following these troubleshooting steps and best practices, you can effectively resolve common IAM issues related to access denied errors and misconfigured permissions for “iam role vs iam user” scenarios. Maintaining a secure and well-managed IAM environment is crucial for ensuring the safe and efficient use of AWS resources.