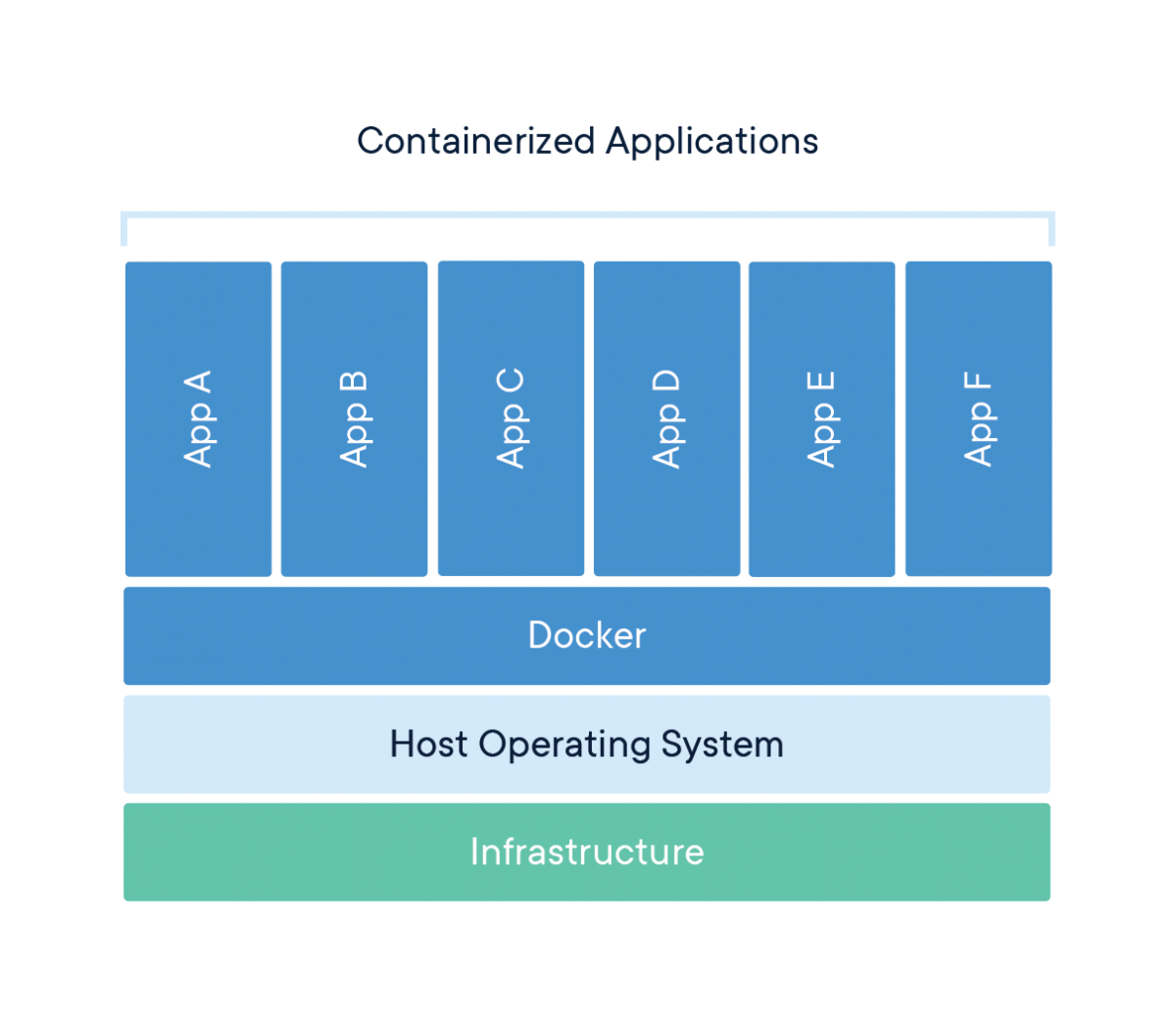
Understanding the Core Principles of Containerization
Containerization represents a significant advancement in operating system virtualization. It offers a powerful approach to application deployment and management. The core principle of what is containers revolves around isolation. Containers encapsulate an application and its dependencies. This ensures that the application runs consistently across different environments. Portability is another key aspect of what is containers. Container images can be easily moved and deployed on various platforms, from local machines to cloud servers. What is containers also highlight their lightweight nature. Unlike traditional virtual machines (VMs) that require a full operating system, containers share the host OS kernel. This results in significantly lower resource overhead.
The isolation provided by what is containers ensures that applications are isolated from each other. This prevents conflicts and improves security. Each container operates in its own isolated environment. This environment includes its own file system, processes, and network interfaces. This isolation ensures that changes within one container do not affect other containers or the host system. The portability of what is containers simplifies the deployment process. Developers can package their applications into container images. Then, they can deploy these images to any environment that supports containerization. This eliminates the “it works on my machine” problem and ensures consistency across development, testing, and production environments.
The benefits of using what is containers are numerous. They provide improved resource utilization. Containers share the host OS kernel, resulting in lower resource overhead compared to VMs. This allows for more applications to be run on the same hardware. Containers also enable faster deployment cycles. Container images can be created and deployed quickly, allowing for faster releases and updates. Enhanced scalability is another key advantage of what is containers. Containers can be easily scaled up or down to meet changing demands. This allows applications to handle increased traffic or load without performance degradation. In contrast to virtual machines, what is containers offer a more efficient and agile approach to application deployment and management, leading to significant cost savings and operational efficiencies.
How to Package and Deploy Applications Using Containers
Packaging and deploying applications using containers involves encapsulating an application and its dependencies into a single, portable unit. This process ensures consistency across different environments, from development to production. Understanding how to create a container image is fundamental to leveraging what is containers effectively. The initial step involves creating a Dockerfile, a text file that contains instructions for building the container image. This Dockerfile specifies the base image, application code, dependencies, and runtime configurations. A well-structured Dockerfile streamlines the image creation process and promotes reproducibility.
Container registries play a pivotal role in storing and distributing container images. Docker Hub is a popular public registry, while private registries can be used for proprietary applications. Once the Dockerfile is prepared, the ‘docker build’ command is used to create the container image. This command executes the instructions in the Dockerfile, layer by layer, creating a read-only image. The resulting image can then be tagged with a name and version for easy identification. Following the successful build, the image is pushed to a container registry using the ‘docker push’ command. This makes the image accessible for deployment across various environments. Using what is containers helps ensure that the application runs consistently, regardless of the underlying infrastructure.
To deploy the application, the container image is pulled from the registry to the target environment. The ‘docker run’ command is then used to create a container instance from the image. This command starts the application within the isolated container environment. Containerization offers numerous advantages, including simplified deployment, improved resource utilization, and enhanced scalability. Popular containerization tools like Docker simplify this process. They enable developers to focus on building applications. These applications can run anywhere without worrying about compatibility issues. Embracing what is containers enhances the efficiency and reliability of application deployment pipelines. Therefore resulting in faster time-to-market and reduced operational overhead.
Exploring the Benefits of Using Container Technology
Container technology offers a multitude of advantages, revolutionizing how applications are developed, deployed, and managed. One of the primary benefits of using containers is improved resource utilization. Unlike traditional virtual machines (VMs) that require a dedicated operating system for each instance, containers share the host operating system’s kernel. This shared kernel allows for a much higher density of applications to run on a single server, leading to significant cost savings and reduced infrastructure footprint. Understanding what is containers in this context highlights their efficiency.
Faster deployment cycles are another key advantage. Container images are lightweight and portable, making them easy to move between different environments, from development to testing to production. This streamlined process enables rapid application delivery and faster iteration cycles. The ability to quickly deploy and scale applications is crucial in today’s fast-paced business environment. Further enhancing the appeal of what is containers is their positive impact on scalability. Containerized applications can be easily scaled up or down based on demand, ensuring optimal performance and responsiveness. Orchestration platforms like Kubernetes automate this process, making it seamless to manage large-scale container deployments.
Operational efficiencies are also significantly enhanced through containerization. The standardized environment provided by containers eliminates inconsistencies between different environments, reducing the risk of errors and simplifying troubleshooting. This consistency allows development and operations teams to work more closely together, fostering a DevOps culture. In comparison with virtual machines, containers offer a more agile and efficient approach to application deployment and management. The reduced overhead and improved resource utilization translate into cost savings and operational efficiencies. Ultimately, understanding what is containers and embracing container technology empowers organizations to innovate faster, reduce costs, and improve their overall agility. The benefits that derive from what is containers makes them a central element in modern application architecture.
Container Runtimes: The Engine Behind Application Isolation
Container runtimes are essential components in the world of containerization. They are responsible for managing the complete lifecycle of containers. This includes creation, execution, and termination. Understanding container runtimes is crucial to grasp how “what is containers” achieve isolation and resource management.
Several popular container runtimes exist, each with its own strengths. Docker Engine is a widely used runtime, known for its ease of use and comprehensive features. Containerd is another popular choice, designed for simplicity and embeddability. CRI-O is specifically tailored for Kubernetes environments, focusing on interoperability. These container runtimes all play a critical role in managing “what is containers”.
Container runtimes interact directly with the operating system kernel. This interaction enables the isolation of containers from each other and from the host system. Runtimes leverage kernel features like namespaces and cgroups to achieve this isolation. Namespaces provide isolation of resources, such as process IDs, network interfaces, and file systems. Cgroups, or control groups, limit and account for the resource usage of containers, such as CPU, memory, and I/O. Through these mechanisms, container runtimes ensure that “what is containers” operate in a secure and resource-constrained environment, preventing interference between applications. They handle the low-level details of container execution, allowing developers to focus on building and deploying their applications. Without container runtimes, the portability and isolation benefits of containers would not be possible, fundamentally changing “what is containers”.
Orchestrating Containers: Managing Applications at Scale
Container orchestration is essential for managing containerized applications effectively. What is containers orchestration addresses the challenges of deploying, scaling, and managing numerous containers. As application scale increases, manual management becomes impractical. Container orchestration platforms automate these tasks, ensuring high availability and efficient resource utilization. Popular platforms include Kubernetes, Docker Swarm, and Apache Mesos. These tools provide features that streamline container management across diverse environments.
Kubernetes stands out as a leading orchestration platform. Its key features include automated deployment, scaling, and self-healing capabilities. Kubernetes automates the process of deploying containers, handling updates, and rolling back changes if needed. It dynamically scales applications based on demand, ensuring optimal performance. The self-healing feature automatically restarts failed containers, maintaining application uptime. Docker Swarm, another option, offers a simpler setup and integration with the Docker ecosystem. Apache Mesos is designed for managing diverse workloads, including both containerized and non-containerized applications. The choice of platform depends on specific needs and infrastructure requirements. Each of these platforms help with what is containers and how to manage them.
These orchestration platforms offer several core functionalities. They include service discovery, load balancing, and storage management. Service discovery allows containers to locate and communicate with each other. Load balancing distributes traffic across multiple container instances, preventing overload and ensuring responsiveness. Storage management provides persistent storage solutions for containerized applications. Furthermore, orchestration platforms offer health monitoring and logging capabilities. Health monitoring tracks the status of containers and applications, alerting administrators to potential issues. Logging aggregates logs from different containers, simplifying troubleshooting and analysis. Effective orchestration ensures that what is containers operate efficiently and reliably, even at scale.
Addressing Security Considerations in Container Environments
Containerization offers numerous benefits, but it also introduces unique security challenges. Securing container environments requires a multi-layered approach. This includes addressing vulnerabilities in container images, implementing robust access control, and monitoring container activity. Understanding these challenges and implementing best practices is crucial for ensuring the security of containerized applications. Addressing the security concerns for what is containers adoption is critical to ensure their safe and reliable operation, especially in production environments.
One of the primary concerns is image security. Container images often contain software packages and libraries with known vulnerabilities. Image scanning tools can help identify these vulnerabilities before deploying containers. Regularly scanning images and patching vulnerabilities reduces the attack surface. Furthermore, it’s essential to use trusted base images from reputable sources. Vulnerability management is an ongoing process. Organizations should continuously monitor for new vulnerabilities and update their images accordingly. A well-defined vulnerability management process is essential for maintaining a secure container environment. What is containers security posture is significantly improved through proactive vulnerability management, reducing the risk of exploitation.
Network segmentation is another critical security measure. By isolating containers within the network, organizations can limit the impact of a potential breach. Network policies can restrict communication between containers, preventing attackers from moving laterally within the environment. Implementing the principle of least privilege is also crucial. Containers should only have the necessary permissions to perform their tasks. Robust access control mechanisms should be implemented to restrict access to container resources. This can be achieved through role-based access control (RBAC) and other security policies. Properly configured network segmentation and access control are fundamental aspects of securing what is containers deployments, minimizing the potential damage from security incidents. Adhering to these security best practices helps to mitigate the risks associated with containerization. The continuous monitoring and improvement of security measures is required to effectively protect container environments from evolving threats.
Containers vs Virtual Machines: A Detailed Comparison
The choice between containers and virtual machines (VMs) depends heavily on specific application requirements and infrastructure goals. Both offer forms of virtualization, but they differ significantly in their approach, resource utilization, and performance characteristics. Understanding these distinctions is crucial for making informed decisions about infrastructure strategy. So, what is containers and what can VMs provide?
Virtual machines, using hypervisors, virtualize the entire hardware stack, allowing multiple operating systems (OS) to run on a single physical server. Each VM includes its own OS, kernel, and applications, leading to higher resource overhead. This overhead translates to slower boot times and greater consumption of CPU, memory, and storage. While VMs provide strong isolation, this comes at the cost of efficiency. This strong isolation also contributes to enhanced security, as processes within one VM are completely separated from others. Virtual machines are well-suited for running diverse applications with varying OS requirements or when strict isolation is paramount.
Containers, on the other hand, virtualize the operating system. They share the host OS kernel, making them significantly lighter and more efficient than VMs. This shared kernel approach allows containers to start much faster and consume fewer resources. Container technology, especially what is containers approach, excel in scenarios requiring rapid deployment, scalability, and high density. Application isolation is achieved through namespaces and control groups (cgroups), providing a degree of separation. While container isolation is generally considered less robust than VM isolation, it is often sufficient for many applications, especially when combined with other security measures like image scanning and network policies. Containers are ideal for microservices architectures, continuous integration/continuous deployment (CI/CD) pipelines, and applications that need to scale quickly and efficiently. What is containers’ benefits are improved resource utilization, faster deployment cycles, and enhanced scalability.
Real-World Use Cases of Containerization: Practical Examples
Containerization has revolutionized software development and deployment across numerous industries. This technology provides agility, scalability, and efficiency, making it a cornerstone of modern DevOps practices. Companies are leveraging what is containers technology to modernize legacy applications, accelerate digital transformation, and achieve significant cost savings. Containerization is employed by organizations of all sizes to optimize their IT infrastructure and streamline software delivery pipelines.
One prominent use case of what is containers is the migration of legacy applications. Many organizations have monolithic applications that are difficult to maintain and scale. Containerizing these applications allows them to be broken down into smaller, more manageable components. These components can then be independently updated and scaled. This approach reduces the risk associated with large-scale deployments and enables faster iteration cycles. For instance, a financial institution might containerize its core banking system to improve its responsiveness to market changes. Another compelling application of what is containers involves the deployment of microservices. Microservices architecture involves breaking down an application into a collection of small, independent services that communicate with each other over a network. Containers provide an ideal platform for deploying and managing microservices, because each microservice can be packaged as a separate container. This isolation enhances fault tolerance and enables independent scaling of individual services. E-commerce platforms often utilize microservices to handle various functionalities like product catalog management, order processing, and payment gateway integration.
Beyond legacy modernization and microservices, what is containers technology is instrumental in streamlining DevOps workflows. Containerized applications can be easily integrated into continuous integration and continuous delivery (CI/CD) pipelines. This automation allows teams to build, test, and deploy software more rapidly and reliably. Container registries serve as central repositories for storing and managing container images, ensuring consistency across different environments. Furthermore, containers facilitate hybrid cloud deployments, enabling applications to run seamlessly across on-premises data centers and public cloud platforms. This flexibility allows organizations to optimize their resource utilization and avoid vendor lock-in. A healthcare provider might use containers to deploy applications in a secure and compliant manner, leveraging the isolation and security features of containerization to protect sensitive patient data. The adaptability and efficiency of what is containers make it a vital tool for businesses seeking to innovate and stay competitive in today’s rapidly evolving digital landscape.