Essential Strategies for Web Application Firewall Implementation
In today’s digital landscape, where web applications are central to business operations, the importance of robust cybersecurity cannot be overstated. Among the various security measures, Web Application Firewalls (WAFs) stand out as a crucial line of defense. A WAF acts as a security checkpoint, meticulously examining HTTP traffic to and from a web application. It is designed to identify and block malicious requests, thereby safeguarding against a plethora of web-based attacks. This filtering process is a vital component of a comprehensive security strategy, distinguishing between legitimate user requests and potentially harmful activities targeting application vulnerabilities. Understanding the fundamental mechanics of how a WAF works—analyzing traffic patterns, identifying known attack signatures, and applying predefined rules—is essential before delving into web application firewall best practices. This foundational knowledge sets the stage for adopting a proactive approach to web application security, ensuring that applications are adequately shielded from constantly evolving threats. The role of the WAF is not just to react to attacks, but to prevent them from reaching the application in the first place, making it an indispensable tool in modern cybersecurity. The implementation of web application firewall best practices, therefore, becomes a strategic imperative for organizations looking to protect their digital assets.
The operational framework of a WAF involves a detailed analysis of web traffic, comparing it against a constantly updated database of known attack patterns and malicious codes. This comparison process allows the WAF to detect and block malicious HTTP requests, effectively preventing a wide array of attacks such as SQL injection, cross-site scripting (XSS), and other forms of web-based exploitation. A well-implemented WAF is not merely a passive filter; it is an active security mechanism that dynamically adapts to the ever-evolving threat landscape. By continuously analyzing and learning from the patterns of both legitimate and malicious traffic, WAFs enhance their ability to differentiate between the two, thereby minimizing false positives and ensuring that only legitimate requests reach the intended application. The effectiveness of a WAF hinges on its ability to perform this sophisticated traffic analysis with minimal latency, thereby ensuring that the user experience is not compromised while bolstering the security posture of the web application. Adopting web application firewall best practices is key to leveraging the full potential of this critical security component and establishing a resilient security posture for your online assets.
How to Fortify Your Web Apps Using Robust WAF Configuration
Transitioning from understanding the foundational importance of Web Application Firewalls (WAFs), the next critical step involves practical application through effective configuration. This stage is crucial for transforming a WAF from a mere presence into a powerful defense mechanism. A well-configured WAF hinges on several key elements, including meticulously crafted rule sets, precisely defined policies, and settings tailored to the unique characteristics of different web applications. A critical aspect of implementing web application firewall best practices is the avoidance of default settings, which often provide generic protection, as these fail to address the nuances of each application. It’s essential to move beyond pre-set configurations and create rules that specifically target the vulnerabilities associated with your particular web environment. This means taking the time to analyze your application’s traffic patterns, potential entry points, and historical attack vectors. The creation of custom rules is paramount, offering a more refined and potent security posture. A WAF, when properly set up, becomes the first line of defense against known and unknown threats. Customizing the WAF configuration is not a one-time task but an ongoing process to match the application’s evolution and changing threat landscapes. Think of this as a continuous fine-tuning, adapting the rules to match any change in the web applications architecture to maintain consistent and dependable protection.
Further enhancing the WAF’s performance requires a deep understanding of both its capabilities and the specific security needs of the web application. Implementing web application firewall best practices also involves the creation of strict, but not overly restrictive, policies. These policies act as the governing rules of engagement, dictating how the WAF handles various types of traffic. The goal is to block malicious requests while permitting legitimate user interactions without undue latency. For example, a policy could be designed to prioritize requests from known geographical areas or to flag traffic that exhibits suspicious patterns. Furthermore, the rule sets must be designed in conjunction with these policies to prevent attacks such as SQL injection, cross-site scripting (XSS), and other OWASP top 10 vulnerabilities. The process of WAF configuration also includes defining exceptions for certain types of traffic or specific URLs which may be necessary for the application’s operational needs. However, such exceptions should be thoroughly vetted and implemented cautiously, as they might inadvertently open up security gaps if not handled with precision. Therefore, ongoing review and evaluation of the WAF policies and rule sets are necessary to maintain a balanced and highly effective security profile. Regularly testing the effectiveness of configured rules is important to identify gaps or areas that require adjustments, ensuring the WAF continues to act as a strong shield against potential web attacks.
Regular Updates and Patching: Keeping Your WAF Shield Strong
Maintaining an effective web application firewall requires a proactive approach to security, particularly when it comes to updates and patching. The cybersecurity landscape is in constant flux, with new vulnerabilities and attack vectors emerging regularly. Consequently, a static web application firewall configuration will quickly become outdated and ineffective. Regularly updating the WAF’s rule sets is crucial; these rules are the core of the firewall’s ability to identify and block malicious traffic. Keeping the software itself patched is equally important because vulnerabilities in the WAF software could be exploited, negating its protective capabilities. Neglecting updates is akin to leaving the doors of a house unlocked – attackers will find the path of least resistance. Therefore, organizations should establish a robust schedule for applying updates, ensuring they stay ahead of the evolving threats. Furthermore, staying informed about new vulnerabilities and recommended patches is essential, often through security newsletters, vendor notifications, and industry publications. The principle underlying this process is that a web application firewall is not a ‘set-it-and-forget-it’ solution but needs continuous attention to remain effective as part of robust web application firewall best practices.
A well-managed update process also includes proper testing and verification. Before applying changes to the production environment, organizations should use staging environments for testing. This procedure allows assessment of any impact the updates or new rules may have on legitimate traffic. Ignoring this step can result in false positives, which may disrupt the user experience. The process should also include checks to ensure that new rules do not conflict with existing ones, creating unintended loopholes in security. By meticulously planning and implementing updates, organizations ensure their web application firewall remains a potent tool for protecting their web applications and their customers’ data. Remember that the agility to adapt and update is a fundamental component of web application firewall best practices, without which any security system will become rapidly obsolete. The consistent pursuit of these updates ensures the WAF continues to offer the necessary level of protection against the evolving threat landscape. Organizations who prioritize regular updates and patching demonstrate a commitment to superior web application firewall best practices, reducing their exposure to vulnerabilities and potentially costly security breaches.
The Significance of Monitoring and Alerting in Web Application Firewall Management
Proactive monitoring is paramount for effective web application firewall best practices. Continuous vigilance is crucial to ensure the web application firewall remains a robust security layer. Regularly reviewing web application firewall logs is essential for identifying potential security breaches and mitigating threats in a timely manner. By analyzing log data, administrators can gain insights into attack patterns, identify vulnerabilities, and fine-tune the web application firewall’s rules and configurations for optimal performance. This proactive approach helps maintain the security posture of web applications and prevents potential damage from successful attacks. Alerting systems should be configured to notify administrators of suspicious activities or unusual traffic patterns, enabling swift responses to emerging threats. This real-time monitoring provides a critical layer of defense, especially against sophisticated attacks that might otherwise go undetected.
Anomaly detection plays a significant role in modern web application firewall management. This advanced technique goes beyond simply matching known attack signatures; it also identifies unusual traffic patterns that may indicate previously unknown threats. By analyzing network traffic behavior and establishing baselines, anomaly detection systems can flag deviations from the norm, allowing security teams to investigate potential intrusions promptly. These systems use sophisticated algorithms and machine learning to identify anomalies that would be missed by traditional rule-based systems, making them invaluable in enhancing the overall security of web applications. Effective anomaly detection requires careful configuration and regular calibration to minimize false positives while maximizing the detection of genuine threats. Integrating anomaly detection capabilities with a robust web application firewall significantly strengthens the security posture of the application and improves the effectiveness of web application firewall best practices.
Effective monitoring and alerting systems are not simply about reacting to security incidents; they also provide valuable insights for ongoing improvements to the web application firewall’s security strategy. Analyzing the data generated by the monitoring system allows organizations to identify weaknesses in their security posture and make adjustments accordingly. This feedback loop is essential for ensuring the web application firewall remains effective in the face of evolving threats and changing business needs. By combining real-time monitoring with comprehensive log analysis, organizations can gain a detailed understanding of their security landscape and refine their web application firewall best practices to maintain a high level of security and resilience. This data-driven approach to web application firewall management contributes significantly to the overall effectiveness of the security strategy, reducing the risk of successful attacks and minimizing potential damage.
Choosing the Right Web Application Firewall: Cloud-Based vs. On-Premises Solutions
Selecting the appropriate web application firewall (WAF) is a critical step in implementing robust web application firewall best practices. Businesses must carefully weigh the advantages and disadvantages of cloud-based and on-premises solutions to determine the best fit for their specific needs and infrastructure. Cloud-based WAFs offer scalability and ease of management, often integrating seamlessly with other cloud services. Their pay-as-you-go pricing models can be attractive for smaller organizations or those with fluctuating traffic demands. However, reliance on a third-party provider introduces potential vendor lock-in and concerns regarding data sovereignty and compliance. On-premises WAFs, conversely, provide greater control and customization, allowing for deep integration with existing security systems and offering enhanced security for highly sensitive data. The initial investment, however, is typically higher, and ongoing maintenance and upgrades require dedicated IT resources. The choice hinges on a thorough assessment of factors such as budget, technical expertise, scalability requirements, regulatory compliance needs, and the level of control desired over the WAF’s configuration and management. Understanding these key considerations is paramount for establishing effective web application firewall best practices.
A key aspect of choosing the right WAF involves evaluating its feature set and capabilities in relation to the specific vulnerabilities and threats faced by the target web applications. Some WAFs offer advanced features like bot management, API protection, and machine learning-based threat detection, while others may focus on more basic rule-based filtering. Furthermore, the ease of integration with existing security infrastructure is a critical factor. Seamless integration with intrusion detection systems (IDS), security information and event management (SIEM) systems, and other security tools is crucial for a holistic security posture. Organizations should prioritize WAFs that offer robust reporting and analytics capabilities, providing valuable insights into attack patterns and overall security posture. This data-driven approach is fundamental to implementing effective web application firewall best practices and maintaining a proactive security stance.
Beyond the core functionalities, the vendor’s reputation, support services, and overall track record are also important considerations. Choosing a reputable vendor with a proven history of providing reliable and effective WAF solutions can significantly reduce the risk of security breaches and operational disruptions. The vendor’s commitment to regular updates and patching is crucial for maintaining the WAF’s effectiveness against emerging threats. Furthermore, the availability of comprehensive documentation, training resources, and responsive customer support can significantly improve the overall operational efficiency and reduce the learning curve associated with deploying and managing the WAF. By carefully considering these factors and prioritizing web application firewall best practices, organizations can select a WAF solution that effectively protects their web applications from a wide range of cyber threats.
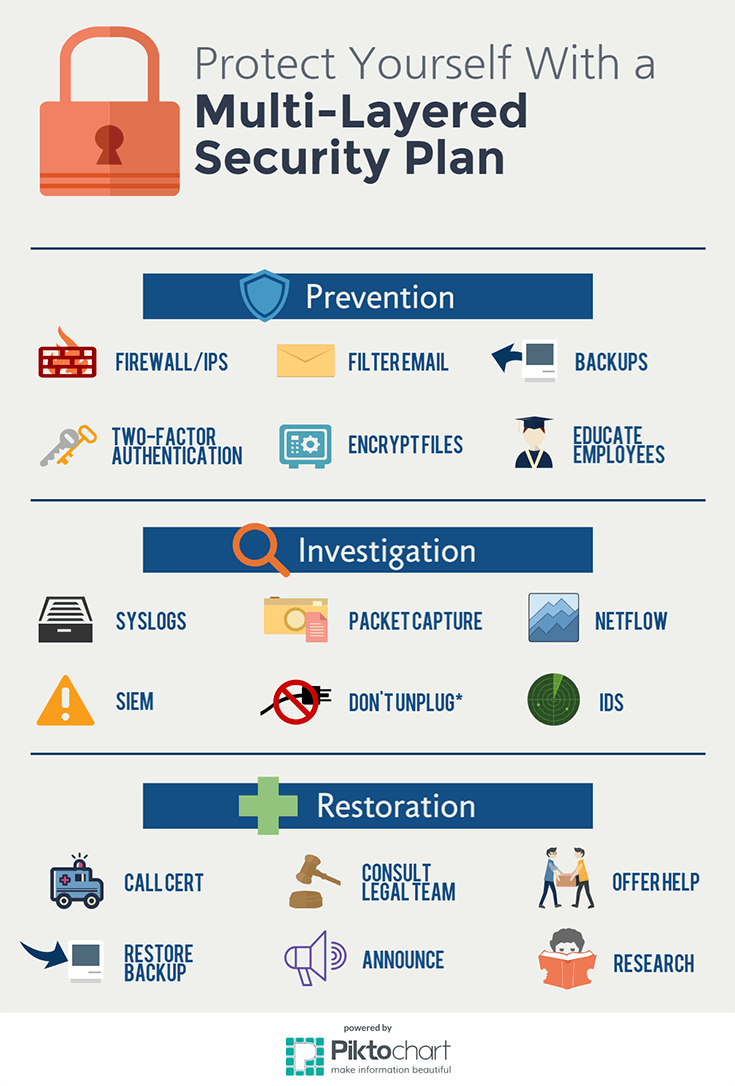
Implementing a Multi-Layered Security Approach with WAFs
A robust web application security strategy relies on a multi-layered approach, and a web application firewall (WAF) forms a crucial, yet not standalone, component. Effective web application firewall best practices dictate integrating a WAF with other security tools to create a comprehensive defense-in-depth strategy. This layered approach significantly reduces the risk of a single point of failure, ensuring that even if one security layer is compromised, others remain to protect the web application. Consider this analogy: a castle’s defenses don’t rely solely on a single wall; instead, they incorporate moats, drawbridges, multiple walls, and guards—each layer offering an additional level of protection. Similarly, a comprehensive web application security architecture should combine a WAF with other security measures.
For instance, an intrusion detection system (IDS) can monitor network traffic for malicious activity, while a security information and event management (SIEM) system can collect and analyze security logs from various sources, including the WAF, to identify patterns and potential threats. By correlating data from different security tools, organizations can gain a holistic view of their security posture and respond more effectively to incidents. This integrated approach is essential for achieving optimal protection, because web application firewall best practices aren’t limited to the WAF itself, but encompass its strategic integration within the larger security ecosystem. The synergy between these different layers significantly enhances the overall effectiveness of the security infrastructure. Successful implementation requires careful planning and coordination to ensure seamless data exchange and coordinated responses to security events.
Furthermore, incorporating regular security audits and penetration testing into the overall security strategy is paramount. These assessments help identify vulnerabilities within the entire system, not just the WAF, and highlight areas for improvement. By actively seeking out and addressing weaknesses, organizations can proactively mitigate risks and ensure their web application remains resilient against a wide range of attacks. A holistic security approach that incorporates these multiple layers, along with regular testing and updates, adheres to web application firewall best practices and offers the most effective protection against modern cyber threats. This layered approach is key to ensuring the long-term security and stability of web applications.
Testing and Fine-Tuning Your WAF for Optimal Performance
The effectiveness of any web application firewall best practices implementation hinges significantly on rigorous testing and subsequent fine-tuning. Initial configuration, while crucial, is merely the starting point. Thorough penetration testing and vulnerability scans are essential steps that must be conducted after the initial setup of the web application firewall and following any significant adjustments to its configurations. These tests are designed to simulate real-world attack scenarios, revealing weaknesses in the WAF’s defenses and allowing security teams to identify areas for improvement. The insights gained from such assessments are invaluable; they highlight potential vulnerabilities and reveal if the WAF is blocking malicious traffic as intended, without hindering legitimate user access. Without this critical phase of testing, a WAF, regardless of its sophistication, may offer a false sense of security, leaving applications vulnerable to exploitation. The testing process should not be viewed as a one-time event, but as a recurring practice, especially after making any changes to the application or the WAF configuration.
Fine-tuning a web application firewall involves carefully adjusting its rules and policies based on the data collected from penetration testing and vulnerability scans. The aim is to strike a balance between robust security and optimal application performance. Overly aggressive settings in a WAF can lead to the blocking of legitimate user traffic, resulting in a poor user experience, which is as detrimental as a security breach itself. Therefore, the tuning process is essential to reduce instances of false positives where benign traffic is mistakenly flagged as malicious. Through carefully analyzing the WAF’s logs and alerts, security teams can identify patterns and make nuanced adjustments to its configuration. This ongoing optimization should focus on aligning the WAF’s rules with specific application needs and mitigating vulnerabilities that are pertinent to the environment. The goal is to ensure that the web application firewall best practices are not just deployed, but intelligently adapted to the specific operational context of the application.
Adapting Your WAF Strategy to New Threats and Changing Environments
A critical aspect of maintaining robust security is the continuous adaptation of your web application firewall best practices. The digital landscape is in constant flux, with new vulnerabilities and attack vectors emerging regularly. Therefore, a static web application firewall (WAF) configuration is insufficient. Organizations must implement a dynamic strategy that involves routinely reviewing and adjusting WAF settings to address newly discovered threats. This should include a thorough analysis of security bulletins, industry advisories, and research reports. Moreover, changes within the web application itself often necessitate alterations to the WAF. If new features or functionalities are introduced, the WAF’s rules and policies need to be updated to ensure proper protection without hindering legitimate user traffic. Failing to adapt promptly and efficiently to these changes can expose applications to a multitude of risks, jeopardizing both data and operations. Therefore, the approach to web application firewall best practices must be proactive and iterative.
Effective adaptation also extends to changing business requirements. As the organization grows or pivots its focus, the WAF configuration must evolve to support these transitions. For example, an increased user base or a change in the application’s primary function can impact the traffic patterns and security needs. Thus, regular reviews of WAF performance metrics are essential to identify areas requiring optimization and to fine-tune policies for improved accuracy and effectiveness. This ongoing process of evaluation and adjustment is not a one-time event but a continuous commitment to ensure that the web application firewall remains an invaluable component of the overall security architecture. By treating the WAF as a living tool that constantly evolves with the environment, organizations can maintain optimal protection and respond effectively to the unpredictable nature of cyber threats. Embracing these web application firewall best practices can significantly reduce the risk of successful attacks and safeguard digital assets.