What are WAF Rules?
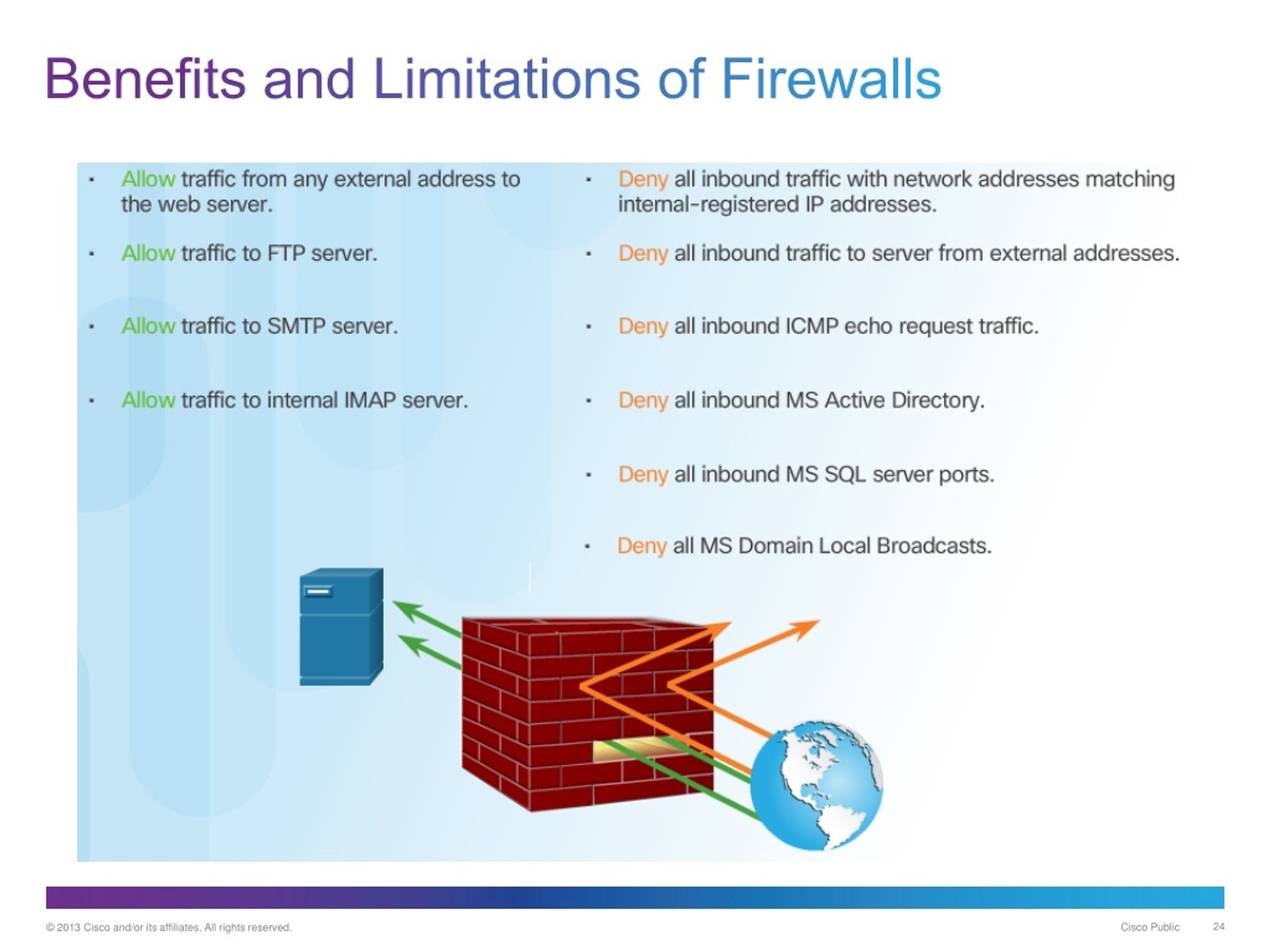
WAF rules are a set of instructions or conditions used by a web application firewall (WAF) to identify and block malicious traffic while allowing legitimate traffic to pass through. WAF rules play a crucial role in protecting web applications from various types of attacks, including SQL injection, cross-site scripting (XSS), and local/remote file inclusion. By implementing WAF rules, organizations can enhance their web application security and prevent unauthorized access, data breaches, and other cyber threats.
How to Create Effective WAF Rules
Creating effective WAF rules is a critical aspect of web application security. To create WAF rules that provide robust protection against various types of attacks, it is essential to understand the OWASP Top 10 web application security risks and other common attack vectors. By regularly reviewing and updating WAF rules, organizations can ensure that their WAF rules remain effective against the latest threats.
To create effective WAF rules, follow these steps:
- Understand the OWASP Top 10 web application security risks: The OWASP Top 10 is a standard awareness document for developers and web application security. By understanding the OWASP Top 10, organizations can identify the most common web application security risks and create WAF rules that provide protection against these risks.
- Identify common attack vectors: In addition to the OWASP Top 10, organizations should also identify other common attack vectors that may target their web applications. By understanding the various types of attacks that can target web applications, organizations can create WAF rules that provide comprehensive protection.
- Define WAF rules based on specific conditions: WAF rules should be defined based on specific conditions that identify malicious traffic. These conditions may include IP addresses, user agents, request methods, request headers, request parameters, and response headers.
- Test WAF rules: Before implementing WAF rules in a production environment, it is essential to test them thoroughly. Testing WAF rules can help identify any false positives or false negatives, ensuring that legitimate traffic is not blocked and that malicious traffic is effectively identified and blocked.
- Monitor WAF rules: Regularly monitoring WAF rules can help organizations identify any changes in attack patterns or techniques. By monitoring WAF rules, organizations can ensure that their WAF rules remain effective against the latest threats.
Creating effective WAF rules requires a deep understanding of web application security risks and attack vectors. By following best practices and regularly reviewing and updating WAF rules, organizations can ensure that their web applications are protected against various types of attacks, including SQL injection, cross-site scripting (XSS), and local/remote file inclusion.
Popular WAF Rule Sets and Solutions
There are several popular WAF rule sets and solutions available in the market, each with its own unique features and advantages. Here are some of the most widely used WAF rule sets and solutions:
ModSecurity
ModSecurity is an open-source web application firewall that provides robust security features for web applications. It is highly configurable and can be customized to meet the specific needs of an organization. ModSecurity supports regular expression-based rules and provides real-time application security monitoring and access control. However, it can be complex to configure and manage, and may require significant resources to run effectively.
OWASP ModSecurity Core Rule Set (CRS)
The OWASP ModSecurity Core Rule Set (CRS) is a set of generic attack detection rules for ModSecurity. It provides protection against the most common web application security risks, including SQL injection, cross-site scripting (XSS), and local/remote file inclusion. The CRS is highly customizable and can be easily integrated with ModSecurity. However, it may generate false positives and negatives, and may require regular tuning to ensure effective operation.
NGINX Plus WAF
NGINX Plus WAF is a commercial web application firewall solution that provides advanced security features for web applications. It includes a set of pre-configured rules that provide protection against the OWASP Top 10 web application security risks. NGINX Plus WAF also supports custom rules and provides real-time traffic analysis and reporting. However, it may be more expensive than other WAF solutions, and may require significant resources to run effectively.
When selecting a WAF rule set or solution, it is essential to consider the specific needs of the organization, including the type and size of web applications, the level of security required, and the available resources. It is also important to regularly review and update WAF rules to ensure they remain effective against the latest threats.
Best Practices for Implementing WAF Rules
Implementing WAF rules is a critical aspect of web application security. However, it is essential to ensure that WAF rules are properly configured, tested, and monitored to avoid over-blocking or under-protection. Here are some best practices for implementing WAF rules:
Proper Configuration
Properly configuring WAF rules is essential to ensure that they are effective in identifying and blocking malicious traffic. This includes configuring WAF rules to match the specific needs of the web application, including the type and size of the application, the level of security required, and the available resources. It is also essential to ensure that WAF rules are configured to allow legitimate traffic to pass through, avoiding over-blocking.
Testing
Testing WAF rules is critical to ensure that they are functioning correctly and not generating false positives or negatives. Testing should include both positive and negative testing, where positive testing involves testing WAF rules with legitimate traffic, and negative testing involves testing WAF rules with malicious traffic. Testing should be conducted regularly, especially after updating WAF rules or making changes to the web application.
Monitoring
Monitoring WAF rules is essential to ensure that they are effectively identifying and blocking malicious traffic. Monitoring should include tracking WAF rule performance, identifying false positives or negatives, and analyzing WAF rule logs. Regular monitoring can help identify potential issues with WAF rules and ensure that they are updated and optimized to provide effective protection.
Balancing Security with Usability and Performance
Balancing security with usability and performance is essential when implementing WAF rules. Over-blocking can result in legitimate traffic being blocked, while under-protection can leave web applications vulnerable to attacks. It is essential to strike a balance between security, usability, and performance, ensuring that WAF rules provide effective protection without negatively impacting web application performance or user experience.
Avoiding Over-Blocking or Under-Protection
Avoiding over-blocking or under-protection is critical when implementing WAF rules. Over-blocking can result in legitimate traffic being blocked, while under-protection can leave web applications vulnerable to attacks. Regular testing and monitoring can help ensure that WAF rules are optimized to provide effective protection without negatively impacting web application performance or user experience.
By following these best practices, organizations can ensure that their WAF rules are properly configured, tested, and monitored, providing effective protection against various types of attacks while balancing security with usability and performance.
Challenges and Limitations of WAF Rules
While WAF rules are an essential component of web application security, they are not without their challenges and limitations. Here are some of the most common challenges and limitations of WAF rules:
False Positives and Negatives
False positives and negatives are common challenges in WAF rules. False positives occur when legitimate traffic is incorrectly identified as malicious and blocked, while false negatives occur when malicious traffic is incorrectly identified as legitimate and allowed to pass through. Both false positives and negatives can negatively impact web application performance and user experience, and can leave web applications vulnerable to attacks.
Bypass Techniques
Attackers can use various bypass techniques to evade WAF rules. These techniques include encoding or obfuscating attack payloads, using multiple attack vectors, and exploiting vulnerabilities in WAF rules or configurations. Bypass techniques can leave web applications vulnerable to attacks, and can be challenging to detect and prevent.
Difficulty of Creating Rules that Cover All Possible Attack Scenarios
Creating WAF rules that cover all possible attack scenarios can be challenging. Web applications are constantly evolving, and new vulnerabilities and attack techniques are constantly emerging. Creating WAF rules that cover all possible attack scenarios requires significant resources, expertise, and time, and may not be feasible for many organizations.
Mitigating Challenges and Limitations
While WAF rules have challenges and limitations, there are ways to mitigate these challenges and limitations. Advanced WAF features, such as machine learning and behavioral analysis, can help detect and prevent bypass techniques and false positives and negatives. Regularly reviewing and updating WAF rules can also help ensure that they remain effective against the latest threats. Collaborating with other organizations and security professionals can also help identify new vulnerabilities and attack techniques, and develop WAF rules that cover all possible attack scenarios.
By understanding the challenges and limitations of WAF rules, organizations can take steps to mitigate these challenges and limitations, ensuring that their WAF rules provide effective protection against various types of attacks while balancing security with usability and performance.
Case Studies: Real-World WAF Rule Implementations
Implementing WAF rules can be a complex and challenging process, but many organizations have successfully implemented WAF rules to protect their web applications from various types of attacks. Here are some case studies of real-world WAF rule implementations:
Case Study 1: A Large E-commerce Website
A large e-commerce website implemented WAF rules to protect against SQL injection and cross-site scripting (XSS) attacks. The WAF rules were customized to match the specific needs of the website, including the type and size of the application, the level of security required, and the available resources. The WAF rules were regularly reviewed and updated to ensure they remained effective against the latest threats. The implementation of WAF rules resulted in a significant reduction in the number of attacks and improved the overall security posture of the website.
Case Study 2: A Government Agency
A government agency implemented WAF rules to protect against local/remote file inclusion attacks. The WAF rules were integrated with other security solutions, including intrusion detection and prevention systems (IDPS) and security information and event management (SIEM) systems. The implementation of WAF rules resulted in improved visibility and control over web application traffic, and helped the agency comply with regulatory requirements for web application security.
Case Study 3: A Healthcare Provider
A healthcare provider implemented WAF rules to protect against patient data breaches and other types of attacks. The WAF rules were customized to match the specific needs of the healthcare provider, including the type and size of the application, the level of security required, and the available resources. The WAF rules were regularly reviewed and updated to ensure they remained effective against the latest threats. The implementation of WAF rules resulted in improved patient data security and helped the healthcare provider comply with regulatory requirements for web application security.
These case studies demonstrate the benefits and challenges of implementing WAF rules in real-world scenarios. While implementing WAF rules can be complex and challenging, the benefits of improved web application security and regulatory compliance make it a worthwhile investment for many organizations.
Future Trends and Developments in WAF Rules
Web application firewall (WAF) rules have been an essential component of web application security for many years. However, as attack techniques and strategies continue to evolve, WAF rules must also evolve to keep up with these changes. Here are some future trends and developments in WAF rules that organizations should be aware of:
Increasing Use of Artificial Intelligence and Automation
Artificial intelligence (AI) and automation are becoming increasingly important in web application security. AI and automation can help detect and prevent attacks more quickly and accurately than traditional WAF rules. In the coming years, we can expect to see more organizations using AI and automation to enhance their WAF rules and improve their web application security posture.
Integration of WAF Rules with Other Security Solutions
WAF rules are often used in isolation, but integrating them with other security solutions can provide more comprehensive protection for web applications. In the coming years, we can expect to see more organizations integrating their WAF rules with other security solutions, such as intrusion detection and prevention systems (IDPS), security information and event management (SIEM) systems, and threat intelligence platforms.
Evolution of Attack Techniques and Strategies
Attack techniques and strategies are constantly evolving, and WAF rules must evolve to keep up with these changes. In the coming years, we can expect to see more sophisticated and targeted attacks, such as zero-day exploits and advanced persistent threats (APTs). WAF rules must be able to detect and prevent these types of attacks to provide effective protection for web applications.
Mitigating Future Challenges and Limitations
As WAF rules continue to evolve, they will face new challenges and limitations. Mitigating these challenges and limitations will require the use of advanced WAF features, such as machine learning and behavioral analysis. These features can help detect and prevent attacks more accurately and efficiently, while minimizing false positives and negatives.
By staying up-to-date with the latest trends and developments in WAF rules, organizations can ensure that their web applications are protected against the latest threats and attack techniques. Investing in proper WAF rule management and maintenance is essential for ensuring the long-term success and security of web applications.
Conclusion: The Importance of WAF Rules in Web Application Security
Web application firewall (WAF) rules are a critical component of web application security. By defining a set of instructions or conditions used by a WAF to identify and block malicious traffic, WAF rules help protect web applications from various types of attacks, such as SQL injection, cross-site scripting (XSS), and local/remote file inclusion. However, creating effective WAF rules is not a one-time task. It requires ongoing effort and attention to ensure that WAF rules remain effective against the latest threats.
To create effective WAF rules, it is essential to understand the OWASP Top 10 web application security risks and other common attack vectors. Regularly reviewing and updating WAF rules is also crucial to ensure they remain effective against the latest threats. Popular WAF rule sets and solutions, such as ModSecurity, the OWASP ModSecurity Core Rule Set (CRS), and the NGINX Plus WAF, provide a range of features and advantages, as well as notable disadvantages. Choosing the right WAF rule set or solution depends on the specific needs and resources of the organization.
Implementing WAF rules requires careful configuration, testing, and monitoring. Balancing security with usability and performance is essential to avoid over-blocking or under-protection. Challenges and limitations of WAF rules, such as false positives and negatives, bypass techniques, and the difficulty of creating rules that cover all possible attack scenarios, can be mitigated through the use of advanced WAF features, such as machine learning and behavioral analysis.
Real-world WAF rule implementations highlight the benefits and challenges of each implementation. By studying these case studies, organizations can learn from the experiences of others and apply those lessons to their own WAF rule configurations. Future trends and developments in WAF rules, such as the increasing use of artificial intelligence and automation, the integration of WAF rules with other security solutions, and the evolution of attack techniques and strategies, will continue to impact the design and implementation of WAF rules in the coming years.
In conclusion, organizations must invest in proper WAF rule management and maintenance to ensure the long-term success and security of their web applications. Staying up-to-date with the latest WAF rule best practices and trends, and continuously evaluating and improving WAF rule configurations, is essential for ensuring the security and integrity of web applications in an ever-evolving threat landscape.