What are VPN Gateways and How Do They Work?
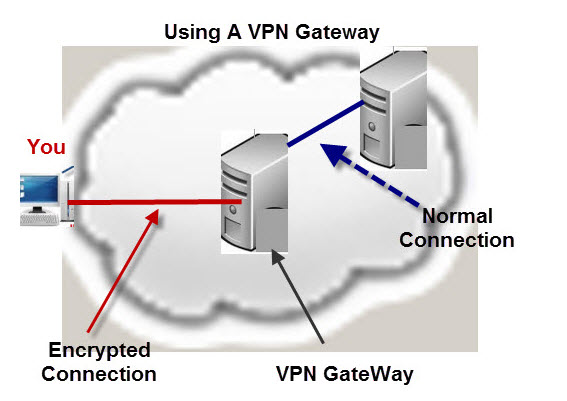
VPN gateways, also known as virtual private network concentrators or routers, are network devices that provide secure and encrypted connections between different networks, such as a company’s internal network and remote users or sites. By establishing a VPN tunnel, VPN gateways enable remote access and data transmission as if the users were directly connected to the private network.
VPN gateways use various components and features to ensure secure and efficient data transmission. One of the critical elements is encryption, which converts plain text data into a coded format that only authorized users can decipher. Authentication is another essential feature that verifies the identity of users and devices before granting access to the network. VPN gateways also support different tunneling protocols, such as PPTP, L2TP, IPSec, and SSL/TLS, which determine the rules and standards for data transmission and encryption.
VPN gateways play a crucial role in enhancing the security, privacy, and flexibility of remote access and network connectivity. By encrypting and authenticating data, VPN gateways prevent unauthorized access, data breaches, and eavesdropping. Additionally, VPN gateways enable businesses to extend their network infrastructure and connect remote sites, partners, and employees, regardless of their geographical location. This flexibility allows organizations to improve their productivity, collaboration, and agility while reducing their operational costs and complexity.
Key Components and Features of VPN Gateways
VPN gateways consist of several essential components and features that contribute to secure and efficient data transmission. One of the critical components is encryption, which converts plain text data into a coded format that only authorized users can decipher. Encryption ensures that even if an attacker intercepts the data, they cannot read or use it without the decryption key.
Authentication is another crucial feature of VPN gateways that verifies the identity of users and devices before granting access to the network. Authentication methods can include passwords, digital certificates, or biometric factors, such as fingerprints or facial recognition. By verifying the identity of users and devices, VPN gateways prevent unauthorized access and ensure that only legitimate users can access the network.
VPN gateways also support various tunneling protocols, such as PPTP, L2TP, IPSec, and SSL/TLS, which determine the rules and standards for data transmission and encryption. Tunneling protocols create a secure tunnel between two endpoints, such as a remote user and a VPN gateway, and encapsulate the data within the tunnel. This encapsulation ensures that the data remains secure and private during transmission, even over public networks.
Other features of VPN gateways can include load balancing, which distributes network traffic across multiple servers or connections to ensure optimal performance and availability. VPN gateways can also support network segmentation, which divides the network into smaller, isolated segments to improve security and control. Additionally, VPN gateways can provide firewall protection, intrusion detection and prevention, and logging and reporting capabilities to enhance network security and compliance.
Benefits of Using VPN Gateways
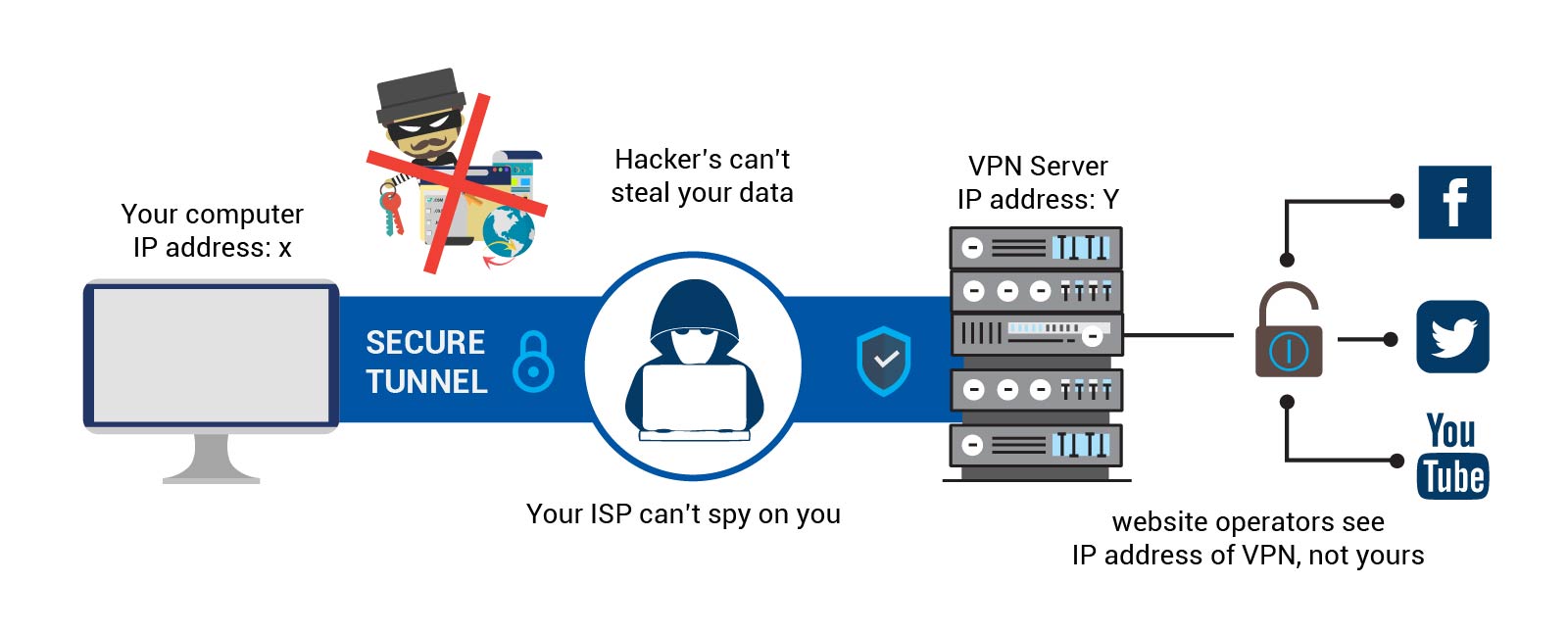
VPN gateways offer numerous benefits to businesses and organizations, including enhanced security, privacy, and flexibility in remote access and network connectivity. By using VPN gateways, businesses can ensure that their data and communications are secure and protected from unauthorized access, interception, or theft.
One of the primary benefits of VPN gateways is their ability to provide secure remote access to employees, contractors, and partners who need to access the company’s network or resources from outside the office. By using a VPN gateway, remote users can establish a secure and encrypted connection to the company’s network, allowing them to access files, applications, and other resources as if they were physically present in the office. This capability can improve productivity, collaboration, and agility while reducing the need for travel or physical office space.
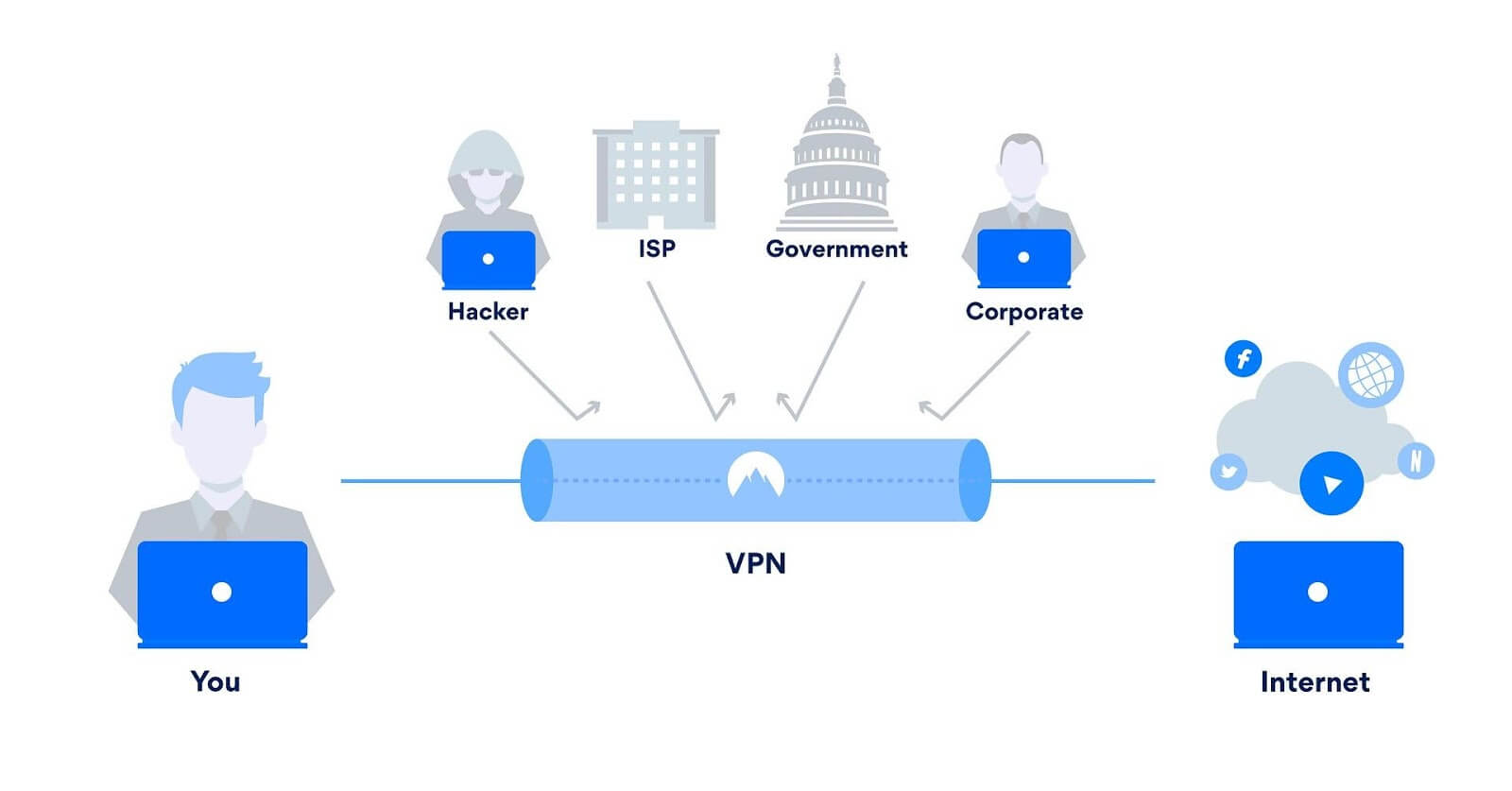
Another benefit of VPN gateways is their ability to provide privacy and anonymity for users who need to access the internet or web-based applications from public or untrusted networks. By using a VPN gateway, users can encrypt their traffic and hide their IP address and location from prying eyes, such as hackers, cybercriminals, or government surveillance agencies. This capability can protect users from online threats, such as phishing, malware, or identity theft, and enable them to access content or services that may be restricted or censored in their location.
VPN gateways can also offer businesses greater flexibility in network connectivity and architecture. By using VPN gateways, businesses can create virtual networks that span multiple sites, regions, or countries, allowing them to centralize their resources, optimize their traffic flow, and reduce their operational costs. VPN gateways can also support various tunneling protocols, such as SSL/TLS, IPSec, or PPTP, which can provide different levels of security, performance, and compatibility, depending on the business needs and requirements.
How to Choose the Right VPN Gateway for Your Business
Choosing the right VPN gateway for your business can be a challenging task, given the wide range of options and vendors available in the market. However, by following a systematic approach and considering the essential factors, you can make an informed decision that meets your business needs and requirements.
The first step in choosing the right VPN gateway is to assess your business needs and requirements. You should consider factors such as the number of remote users, the type and volume of data traffic, the level of security and compliance, and the scalability and flexibility of the VPN gateway. You should also consider the compatibility and integration with your existing network infrastructure and applications.
The second step is to compare the features and specifications of the leading VPN gateway solutions available in the market. Some of the essential features and specifications to consider include the encryption and authentication methods, the tunneling protocols, the firewall and VPN concentrator capabilities, the redundancy and failover mechanisms, and the management and monitoring tools. You should also consider the vendor support, the cost, and the reputation and track record of the vendor.
The third step is to evaluate the performance and security of the VPN gateway solutions in a test environment or a proof-of-concept (POC) scenario. You should test the VPN gateway solutions under various scenarios and workloads, such as high traffic, low latency, and high availability. You should also test the VPN gateway solutions for vulnerabilities and attacks, such as denial-of-service (DoS), man-in-the-middle (MitM), and password cracking.
The fourth step is to deploy and configure the VPN gateway solution that meets your business needs and requirements. You should follow the vendor’s guidelines and best practices for setting up and configuring the VPN gateway. You should also test the VPN gateway connection and functionality, such as the VPN tunnel, the authentication, and the encryption. You should monitor and maintain the VPN gateway performance and security, such as updating the software, backing up the configurations, and monitoring the traffic.
Top VPN Gateway Solutions in the Market
When it comes to choosing a VPN gateway solution for your business, there are several leading vendors and products to consider. Each vendor offers unique features, strengths, and weaknesses, so it’s essential to compare and evaluate them based on your specific needs and requirements.
Cisco VPN Gateways
Cisco is a well-known and established vendor in the networking and security market. Cisco offers a range of VPN gateway solutions, such as the Adaptive Security Appliance (ASA) series and the Meraki MX series. The Cisco ASA series provides advanced security features, such as firewall, IPS, and VPN, while the Meraki MX series offers cloud-based management and automation. Cisco VPN gateways support various VPN protocols, such as IPsec, SSL, and L2TP, and offer scalability, reliability, and performance.
Juniper VPN Gateways
Juniper is another leading vendor in the networking and security market. Juniper offers a range of VPN gateway solutions, such as the SRX series and the SA series. The Juniper SRX series provides high-performance security features, such as firewall, VPN, and IPS, while the SA series offers dedicated VPN concentrators. Juniper VPN gateways support various VPN protocols, such as IPsec, SSL, and IKEv2, and offer flexibility, scalability, and automation.
Palo Alto Networks VPN Gateways
Palo Alto Networks is a fast-growing and innovative vendor in the networking and security market. Palo Alto Networks offers a range of VPN gateway solutions, such as the GlobalProtect series and the Panorama series. The Palo Alto Networks GlobalProtect series provides advanced security features, such as firewall, VPN, and threat prevention, while the Panorama series offers centralized management and visibility. Palo Alto Networks VPN gateways support various VPN protocols, such as IPsec, SSL, and IKEv2, and offer integration, automation, and analytics.
When selecting a VPN gateway solution, it’s essential to consider factors such as scalability, compatibility, cost, and vendor support. You should also evaluate the features, strengths, and weaknesses of each vendor and product, and test them in a proof-of-concept (POC) scenario. By choosing the right VPN gateway solution, you can ensure secure and efficient remote access and network connectivity for your business.
How to Set Up and Configure a VPN Gateway
Setting up and configuring a VPN gateway can be a complex and challenging task, but with the right approach and tools, you can ensure secure and efficient remote access and network connectivity for your business.
Selecting a VPN Protocol
The first step in setting up and configuring a VPN gateway is to select a VPN protocol that meets your needs and requirements. Some of the most common VPN protocols include IPsec, SSL, L2TP, and PPTP. Each protocol has its strengths, weaknesses, and use cases, so it’s essential to evaluate them based on your specific criteria, such as security, performance, and compatibility.
Creating a VPN Tunnel
Once you have selected a VPN protocol, the next step is to create a VPN tunnel between the VPN gateway and the remote clients or networks. The VPN tunnel is a secure and encrypted connection that enables data transmission between the two endpoints. The process of creating a VPN tunnel involves configuring the VPN gateway and the remote clients or networks with the appropriate settings, such as the VPN protocol, the encryption and authentication methods, and the IP addresses and subnets.
Testing the Connection
After creating the VPN tunnel, the final step is to test the connection and ensure that the VPN gateway and the remote clients or networks can communicate and exchange data securely and efficiently. The testing process involves verifying the VPN tunnel status, the encryption and authentication methods, and the data transmission performance. You should also test the VPN gateway for vulnerabilities and attacks, such as denial-of-service (DoS), man-in-the-middle (MitM), and password cracking.
In conclusion, setting up and configuring a VPN gateway requires careful planning, configuration, and testing. By following the best practices and guidelines, you can ensure secure and efficient remote access and network connectivity for your business. You should also consider the future trends and developments in VPN gateways, such as the adoption of cloud-based VPN services, the integration of artificial intelligence and machine learning, and the evolution of VPN standards and protocols.
Best Practices for Managing and Maintaining VPN Gateways
Managing and maintaining VPN gateways is a critical task for ensuring secure and efficient remote access and network connectivity. By following the best practices and guidelines, you can optimize the performance, security, and reliability of your VPN gateways and minimize the risks and impacts of downtime, attacks, and failures.
Monitoring Traffic
One of the essential best practices for managing and maintaining VPN gateways is to monitor the traffic and usage patterns. By monitoring the traffic, you can detect and respond to any anomalies, threats, or issues, such as high latency, low bandwidth, or unauthorized access. You can also optimize the performance and capacity planning of your VPN gateways by analyzing the traffic trends, peaks, and valleys, and adjusting the resources, policies, and configurations accordingly.
Updating Software
Another critical best practice for managing and maintaining VPN gateways is to keep the software up-to-date with the latest patches, fixes, and updates. By updating the software, you can address the known vulnerabilities, bugs, and weaknesses, and enhance the security and stability of your VPN gateways. You should also test the software updates in a controlled and isolated environment before deploying them to the production environment, to ensure compatibility, functionality, and performance.
Backing Up Configurations
A third important best practice for managing and maintaining VPN gateways is to back up the configurations and settings regularly and consistently. By backing up the configurations, you can recover and restore the VPN gateways to the previous state in case of any failures, crashes, or errors. You should also store the backups in a secure and redundant location, such as a cloud storage or a network-attached storage (NAS), and test the backups periodically to ensure recoverability and consistency.
In conclusion, managing and maintaining VPN gateways requires a proactive, systematic, and comprehensive approach. By following the best practices and guidelines, you can ensure the optimal performance, security, and reliability of your VPN gateways, and provide a seamless and secure remote access and network connectivity experience for your users and customers.
Future Trends and Developments in VPN Gateways
VPN gateways have been a critical component of secure and efficient remote access and network connectivity for many years. However, the landscape of VPN gateways is constantly evolving, driven by the changing needs, threats, and technologies in the industry. In this section, we will explore some of the future trends and developments in VPN gateways, and how they can benefit your business.
Cloud-Based VPN Services
One of the most significant trends in VPN gateways is the adoption of cloud-based VPN services, which offer several advantages over traditional hardware-based VPN gateways. Cloud-based VPN services provide greater scalability, flexibility, and cost-effectiveness, as they can dynamically adjust the resources and capacity based on the demand and usage. They also offer easier deployment, management, and maintenance, as they do not require any physical infrastructure or on-site visits. Moreover, cloud-based VPN services can provide better security and performance, as they can leverage the advanced security features, such as multi-factor authentication, threat intelligence, and encryption, and the global network of data centers and points of presence (PoPs) of the cloud providers.
Integration of AI and ML
Another trend in VPN gateways is the integration of artificial intelligence (AI) and machine learning (ML) technologies, which can enhance the security, automation, and intelligence of VPN gateways. AI and ML can enable VPN gateways to detect and respond to the sophisticated and dynamic threats, such as zero-day attacks, advanced persistent threats (APTs), and botnets, by analyzing the patterns, behaviors, and anomalies in the network traffic and user activities. They can also enable VPN gateways to automate the configuration, optimization, and troubleshooting processes, by learning from the historical data and best practices, and providing the real-time insights and recommendations. Furthermore, AI and ML can enable VPN gateways to provide the personalized and contextual user experience, by adapting to the user preferences, roles, and environments, and offering the relevant and timely information and services.
Evolution of VPN Standards and Protocols
A third trend in VPN gateways is the evolution of VPN standards and protocols, which can improve the security, compatibility, and interoperability of VPN gateways. Some of the emerging VPN standards and protocols include WireGuard, OpenVPN 3, and IKEv2/IPsec, which offer several benefits over the traditional VPN standards and protocols, such as SSL/TLS, PPTP, and L2TP. For example, WireGuard provides faster and more secure connections, by using the state-of-the-art cryptography and peer-to-peer networking. OpenVPN 3 offers easier and more flexible deployments, by supporting the modern platforms and architectures, such as mobile devices, containers, and orchestrators. IKEv2/IPsec provides better performance and reliability, by using the optimized key exchange and encryption algorithms, and the NAT traversal and mobility features.
In conclusion, VPN gateways are constantly evolving to meet the changing needs, threats, and technologies in the industry. By adopting the future trends and developments in VPN gateways, such as cloud-based VPN services, AI and ML integration, and VPN standards and protocols evolution, you can enhance the security, performance, and value of your VPN gateways, and provide a seamless and secure remote access and network connectivity experience for your users and customers.