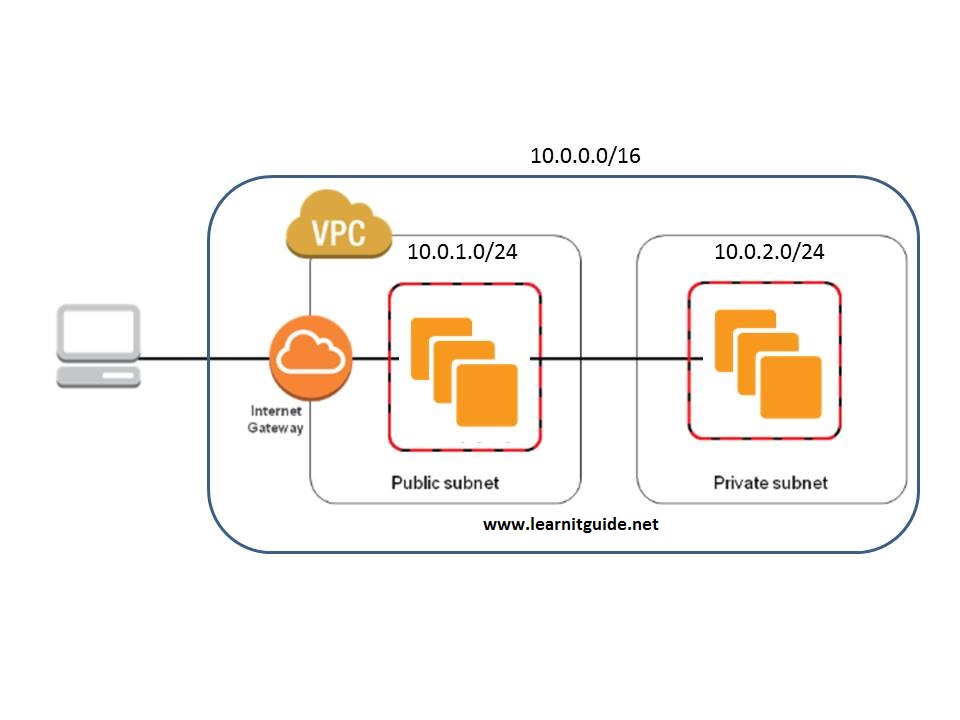
What is a VPC Subnet and Why is it Important?
A Virtual Private Cloud (VPC) subnet is a logically isolated network within a VPC that provides a secure and flexible environment for deploying and managing resources in the cloud. VPC subnets play a critical role in network security and isolation, allowing organizations to segment their network into smaller, more manageable subnets that can be customized to meet specific security and performance requirements. Proper subnet configuration is essential for optimal network performance and security, ensuring that resources are accessible only to authorized users and applications.
In a VPC, subnets are created within a specific IP address range, known as a CIDR block, which defines the range of IP addresses that can be assigned to resources within the subnet. Route tables, network access control lists (NACLs), and security groups are the main components of a VPC subnet, working together to control network traffic and ensure security. Route tables define the allowed traffic between subnets and the internet or other networks, while NACLs provide an additional layer of security by controlling inbound and outbound traffic at the subnet level. Security groups, on the other hand, control traffic at the instance level, allowing or denying traffic based on specific rules and conditions.
VPC subnets provide several benefits, including enhanced security, improved network performance, and simplified network management. By segmenting the network into smaller subnets, organizations can apply more granular security policies, reducing the risk of unauthorized access and data breaches. Additionally, VPC subnets provide greater control over network traffic, allowing organizations to optimize network performance and reduce latency. Finally, VPC subnets simplify network management by providing a centralized location for managing network resources, reducing the complexity and overhead associated with traditional network architectures.
Key Components of a VPC Subnet
A VPC subnet is a fundamental building block of cloud networking, providing a secure and flexible environment for deploying and managing resources in the cloud. At the heart of a VPC subnet are several key components that work together to control network traffic and ensure security. These components include CIDR blocks, route tables, network access control lists (NACLs), and security groups.
CIDR Blocks
A CIDR block is a range of IP addresses that defines the address space of a VPC subnet. CIDR blocks are used to allocate IP addresses to resources within the subnet, such as virtual machines, databases, and load balancers. When creating a VPC subnet, it is essential to choose a CIDR block that provides enough IP addresses to accommodate future growth and expansion. A well-designed CIDR block strategy can help ensure optimal network performance and security by reducing the risk of IP address conflicts and simplifying network management.
Route Tables
A route table is a set of rules that define the allowed traffic between subnets and the internet or other networks. Route tables are used to control the flow of network traffic within a VPC subnet, ensuring that resources are accessible only to authorized users and applications. When creating a VPC subnet, it is essential to configure the route tables properly to ensure that resources are accessible and secure. Route tables can be associated with one or more subnets, allowing for granular control over network traffic.
Network Access Control Lists (NACLs)
A network access control list (NACL) is a security layer that controls inbound and outbound traffic at the subnet level. NACLs provide an additional layer of security by allowing or denying traffic based on specific rules and conditions. NACLs are stateless, meaning that they do not maintain session information or track the state of network connections. When creating a VPC subnet, it is essential to configure the NACLs properly to ensure that only authorized traffic is allowed.
Security Groups
A security group is a virtual firewall that controls traffic at the instance level. Security groups allow or deny traffic based on specific rules and conditions, providing granular control over network traffic. Unlike NACLs, security groups are stateful, meaning that they maintain session information and track the state of network connections. When creating a VPC subnet, it is essential to configure the security groups properly to ensure that only authorized traffic is allowed.
By understanding the key components of a VPC subnet, organizations can design and implement a secure and flexible network architecture that meets their specific needs and requirements. Proper configuration of CIDR blocks, route tables, NACLs, and security groups is essential for optimal network performance and security, ensuring that resources are accessible only to authorized users and applications.
How to Create a VPC Subnet: A Step-by-Step Guide
Creating a VPC subnet is a straightforward process that can be accomplished using popular cloud service providers such as Amazon Web Services (AWS) or Microsoft Azure. In this section, we will provide a detailed, step-by-step guide on how to create a VPC subnet in AWS.
Step 1: Create a VPC
Before creating a VPC subnet, you must first create a VPC. In the AWS Management Console, navigate to the VPC dashboard and click on “Create VPC.” Enter a name for your VPC, select a CIDR block, and click on “Create.”
Step 2: Create a Subnet
Once your VPC is created, you can create a subnet. Navigate to the “Subnets” section of the VPC dashboard and click on “Create subnet.” Select your VPC from the dropdown menu, enter a name for your subnet, and select a CIDR block. Make sure to choose a CIDR block that is within the range of your VPC’s CIDR block. Click on “Create” to create your subnet.
Step 3: Configure Subnet Settings
After creating your subnet, you can configure its settings. Navigate to the “Subnets” section of the VPC dashboard and select your subnet. In the “Subnet Details” tab, you can configure settings such as the availability zone, map public IP addresses, and assign tags. In the “Network Access Control Lists” tab, you can configure the NACLs for your subnet. In the “Route Tables” tab, you can configure the route tables for your subnet.
Step 4: Test Your Subnet
Once you have configured your subnet settings, you can test your subnet by launching an instance. Navigate to the EC2 dashboard and click on “Launch Instance.” Select your VPC and subnet, and follow the prompts to configure your instance settings. Once your instance is launched, you can test your subnet by connecting to your instance using SSH or RDP.
Creating a VPC subnet is a simple process that can be accomplished in just a few steps. By following best practices for designing and implementing VPC subnets, such as proper subnet sizing, subnet layout, and subnet security, you can ensure optimal network performance and security. With the ability to create and configure VPC subnets, organizations can take advantage of the flexibility and scalability of cloud computing while maintaining control over their network architecture.
Best Practices for Designing and Implementing VPC Subnets
Designing and implementing VPC subnets requires careful planning and consideration to ensure optimal network performance and security. In this section, we will outline best practices for designing and implementing VPC subnets, including subnet sizing, subnet layout, and subnet security.
Subnet Sizing
When designing VPC subnets, it is essential to consider subnet sizing. Subnet sizing refers to the number of IP addresses allocated to a subnet. Proper subnet sizing ensures that there are enough IP addresses to accommodate future growth and expansion. When determining subnet sizing, consider the number of resources that will be deployed in the subnet and the expected growth rate. It is recommended to allocate at least a /24 CIDR block for each subnet, providing 256 IP addresses.
Subnet Layout
Subnet layout refers to the organization of subnets within a VPC. Proper subnet layout ensures that resources are logically organized and easily manageable. When designing subnet layout, consider the following best practices:
- Create subnets in different availability zones to ensure high availability and fault tolerance.
- Create subnets for different resource types, such as web servers, application servers, and databases, to simplify network management and security.
- Create subnets for different environments, such as development, testing, and production, to ensure proper resource isolation and security.
Subnet Security
Subnet security is critical to ensuring the confidentiality, integrity, and availability of resources deployed in a VPC. When implementing subnet security, consider the following best practices:
- Use security groups to control inbound and outbound traffic to instances in the subnet.
- Use network access control lists (NACLs) to control traffic at the subnet level.
- Use VPC flow logs to monitor and audit network traffic in the subnet.
- Use encryption for data in transit and at rest to protect against data breaches and unauthorized access.
By following these best practices for designing and implementing VPC subnets, organizations can ensure optimal network performance and security. Proper subnet sizing, layout, and security are essential for ensuring that resources are accessible, secure, and easily manageable. With the ability to design and implement VPC subnets, organizations can take advantage of the flexibility and scalability of cloud computing while maintaining control over their network architecture.
Real-World Examples of VPC Subnet Implementation
VPC subnets are used in a variety of industries and applications to provide network security and isolation within a VPC. In this section, we will provide real-world examples of how VPC subnets are implemented and the benefits and challenges of each implementation.
Example 1: E-commerce Website
An e-commerce website can use VPC subnets to isolate and secure different components of their application, such as web servers, application servers, and databases. By creating subnets for each component, the e-commerce website can apply different security policies and controls to each subnet, reducing the risk of data breaches and unauthorized access. For example, the web servers can be placed in a public subnet with restricted access, while the application servers and databases can be placed in private subnets with more stringent security policies.
Example 2: Multi-tenant SaaS Application
A multi-tenant SaaS application can use VPC subnets to isolate and secure customer data and applications. By creating subnets for each customer, the SaaS application can ensure that customer data is isolated and secure, reducing the risk of data breaches and unauthorized access. Additionally, the SaaS application can apply different security policies and controls to each subnet, such as restricting access to specific IP addresses or applying network access control lists (NACLs) to control traffic at the subnet level.
Example 3: Hybrid Cloud Architecture
A hybrid cloud architecture can use VPC subnets to connect and secure on-premises networks with cloud-based resources. By creating subnets in the VPC that match the on-premises network, the hybrid cloud architecture can ensure that resources are logically organized and easily manageable. Additionally, the hybrid cloud architecture can use VPC peering or VPN connections to connect the on-premises network with the VPC, providing secure and low-latency connectivity between the two networks.
These are just a few examples of how VPC subnets are used in real-world scenarios. By implementing VPC subnets, organizations can take advantage of the flexibility and scalability of cloud computing while maintaining control over their network architecture. However, there are also challenges to implementing VPC subnets, such as managing subnet layout, security policies, and network traffic. It is essential to follow best practices for designing and implementing VPC subnets to ensure optimal network performance and security.
Troubleshooting Common VPC Subnet Issues
VPC subnets are a powerful tool for network security and isolation within a VPC, but they can also be complex to manage and configure. In this section, we will identify common VPC subnet issues and provide troubleshooting steps for each issue. By understanding these common issues and how to resolve them, you can ensure optimal network performance and security.
Issue 1: Incorrect Subnet Configuration
One of the most common VPC subnet issues is incorrect subnet configuration. This can include issues such as incorrect CIDR blocks, improper route table associations, or misconfigured network access control lists (NACLs) and security groups. To troubleshoot this issue, check the configuration of each component of the VPC subnet and ensure that they are correctly configured. Use the VPC dashboard or command-line tools to verify the configuration and make any necessary changes.
Issue 2: Network Connectivity Issues
Another common VPC subnet issue is network connectivity issues. This can include issues such as inability to connect to instances in the subnet, slow network performance, or issues with DNS resolution. To troubleshoot this issue, check the network configuration and ensure that routes, NACLs, and security groups are correctly configured. Additionally, check the instance configuration and ensure that the instance is correctly configured and running.
Issue 3: Security Issues
Security issues are a common VPC subnet issue, particularly in multi-tenant environments. This can include issues such as unauthorized access to instances or data, data breaches, or issues with data encryption. To troubleshoot this issue, check the security configuration of the VPC subnet and ensure that security groups, NACLs, and encryption policies are correctly configured. Additionally, monitor network traffic and use VPC flow logs to identify and respond to security threats.
By understanding these common VPC subnet issues and how to troubleshoot them, you can ensure optimal network performance and security. It is essential to regularly monitor and audit VPC subnets to identify and respond to issues as they arise. Additionally, following best practices for designing and implementing VPC subnets can help prevent many common issues and ensure optimal network performance and security.
Comparing VPC Subnets to Other Network Architectures
VPC subnets are a powerful tool for network security and isolation within a VPC, but they are not the only network architecture available. In this section, we will compare VPC subnets to other network architectures, such as traditional on-premises networks and other cloud-based networks. By understanding the advantages and disadvantages of each architecture, you can make informed decisions about which architecture is best for your needs.
VPC Subnets vs. Traditional On-Premises Networks
Traditional on-premises networks are built on physical infrastructure, such as routers, switches, and firewalls. These networks are typically managed by IT staff and are located on-premises, within the organization’s physical location. VPC subnets, on the other hand, are built on virtual infrastructure and are managed through a cloud service provider’s web console or API.
The main advantage of VPC subnets over traditional on-premises networks is their flexibility and scalability. VPC subnets can be easily provisioned, modified, and decommissioned as needed, without the need for physical infrastructure changes. Additionally, VPC subnets can be easily scaled up or down to meet changing network demands, without the need for additional physical infrastructure.
However, VPC subnets also have some disadvantages compared to traditional on-premises networks. For example, VPC subnets may have higher latency than traditional on-premises networks due to the additional network hops required to reach the cloud service provider’s infrastructure. Additionally, VPC subnets may have more complex security configurations due to the need to manage both virtual and physical security controls.
VPC Subnets vs. Other Cloud-Based Networks
Other cloud-based networks, such as virtual private servers (VPS) or container networks, are also available. These networks are similar to VPC subnets in that they are built on virtual infrastructure and are managed through a cloud service provider’s web console or API. However, they differ in their architecture and capabilities.
VPC subnets offer more advanced network security and isolation capabilities than other cloud-based networks. For example, VPC subnets allow for the creation of subnets with unique CIDR blocks, route tables, network access control lists (NACLs), and security groups. This provides fine-grained control over network traffic and ensures that resources are isolated and secure.
However, other cloud-based networks may offer simpler configurations or lower costs for certain use cases. For example, VPS or container networks may be more appropriate for simple web applications or development environments where advanced network security is not required.
By understanding the advantages and disadvantages of VPC subnets compared to other network architectures, you can make informed decisions about which architecture is best for your needs. It is essential to consider factors such as network security, isolation, flexibility, scalability, latency, and cost when selecting a network architecture.
The Future of VPC Subnets: Trends and Predictions
Virtual Private Cloud (VPC) subnets have become a critical component of modern network architectures, providing network security and isolation within a VPC. As cloud computing continues to evolve, so too will VPC subnets, with new technologies and techniques being developed to improve network performance, security, and scalability.
Trend 1: Increased Adoption of Hybrid Cloud Architectures
As organizations continue to adopt cloud computing, many are turning to hybrid cloud architectures that combine on-premises and cloud-based resources. VPC subnets will play a critical role in these architectures, providing network security and isolation for cloud-based resources while integrating with on-premises networks.
Trend 2: Improved Network Performance with AWS VPC Ingress Routing
AWS recently announced VPC Ingress Routing, a new feature that allows traffic to be routed to network virtual appliances, such as firewalls or intrusion detection systems, before reaching the target instance. This feature can improve network performance and security by allowing for more granular control over network traffic.
Trend 3: Enhanced Security with VPC Security Groups
Security groups are a critical component of VPC subnets, providing fine-grained control over network traffic. In the future, we can expect to see enhanced security features in VPC security groups, such as more sophisticated rules and policies, as well as integration with other security tools and services.
Trend 4: Greater Scalability with VPC Subnet Expansion
As cloud computing continues to grow, so too will the need for greater scalability in VPC subnets. We can expect to see new technologies and techniques for expanding VPC subnets, such as the ability to add more subnets or increase the size of existing subnets, without disrupting network performance or security.
Prediction 1: Increased Use of Containers and Serverless Architectures
Containers and serverless architectures are becoming increasingly popular in cloud computing, and we can expect to see more VPC subnets being used to provide network security and isolation for these environments. This will require new tools and techniques for managing VPC subnets in container and serverless environments.
Prediction 2: Greater Integration with Artificial Intelligence and Machine Learning
Artificial intelligence and machine learning are being used to improve network performance, security, and scalability in cloud computing. We can expect to see greater integration of these technologies with VPC subnets, such as the use of machine learning algorithms to optimize network traffic or detect security threats.
By understanding these trends and predictions, you can be better prepared for the future of VPC subnets and ensure that your network architecture is optimized for performance, security, and scalability. As cloud computing continues to evolve, so too will VPC subnets, and it is essential to stay up-to-date with the latest technologies and techniques to ensure optimal network performance and security.