Understanding Virtual Private Clouds: Your Private Network in the Cloud
A virtual private cloud (VPC) can be understood as a secure, isolated private network within a public cloud environment. Think of it as having your own dedicated data center, but one that exists entirely within the cloud provider’s infrastructure. This offers a significant departure from traditional on-premises networks, where you are responsible for physically maintaining servers, network hardware, and security infrastructure. With a VPC, the cloud provider handles the underlying infrastructure, allowing you to focus on configuring and managing your network environment.
Unlike traditional networks that require substantial upfront investment in hardware and ongoing maintenance costs, VPCs offer scalability and cost-effectiveness. You only pay for the resources you consume, and you can easily scale your network up or down as your needs change. The cloud provider takes care of the physical infrastructure, power, and cooling, reducing your operational burden. This makes VPCs an attractive option for businesses of all sizes, from startups to large enterprises. One of the most important features of a vpc define its role in the network.
Isolation and security are paramount in a VPC environment. By default, a VPC is isolated from other networks in the cloud, providing a secure space for your applications and data. You have complete control over your VPC’s network configuration, including defining IP address ranges, creating subnets, and configuring route tables. Security groups and network access control lists (ACLs) allow you to implement granular security policies to control traffic flow in and out of your VPC. Essentially, a vpc define a logically isolated section of the cloud, this provides a level of control and security comparable to, or even exceeding, that of a traditional private network. The ability to define custom security rules and network configurations makes the vpc define your security perimeter within the cloud. In fact, a vpc define security for cloud computing.
Key Benefits of Cloud-Based Private Networks
Using a Virtual Private Cloud (VPC) offers numerous advantages, primarily revolving around scalability, cost-effectiveness, enhanced security, and greater control over your network environment. A core benefit is scalability. VPCs allow resources to be adjusted on demand, scaling up or down based on real-time needs. This dynamic allocation optimizes resource utilization, preventing over-provisioning and reducing unnecessary costs. Defining needs is easier with scalable solutions, making the concept of “vpc define” more practical.
Cost-effectiveness is another significant driver for VPC adoption. Traditional on-premises networks require substantial upfront investment in hardware, infrastructure, and ongoing maintenance. With a VPC, these costs are significantly reduced as the cloud provider handles the underlying infrastructure. You only pay for the resources consumed, leading to considerable savings. Customization is also a key aspect. VPCs allow you to tailor your network environment to precisely match specific requirements. You have the flexibility to define network topologies, configure routing rules, and implement security policies. This level of control ensures that the network aligns perfectly with the applications and workloads it supports. Understanding what a “vpc define” entails is key to customization.
VPCs are valuable for hosting web applications, handling sensitive data, and managing demanding enterprise workloads. Security is a paramount concern in today’s digital landscape. VPCs offer robust security features, including network isolation, security groups, and network ACLs. These features allow you to implement a layered security approach, protecting your resources from unauthorized access and potential threats. Each cloud provider, such as AWS, Azure, or Google Cloud, offers its specific implementation of VPCs, while maintaining the core principles of isolation and control. The ability to “vpc define” security parameters is a fundamental advantage. Overall, the benefits derived from employing VPCs translate into agile, secure, and cost-optimized IT infrastructure, perfectly suited to modern business demands.
How to Set Up a Virtual Private Network on AWS
Creating a Virtual Private Cloud (VPC) on Amazon Web Services (AWS) involves a series of well-defined steps. This process allows users to establish a private, isolated network within the AWS cloud. Understanding these steps is crucial for leveraging the full potential of AWS’s networking capabilities. The ability to define a vpc is essential for any organization using cloud resources.
The initial step involves choosing a CIDR (Classless Inter-Domain Routing) block for the VPC. This block defines the IP address range that the VPC will use. Selecting an appropriate CIDR block is important as it determines the maximum number of IP addresses available within the VPC. Next, one must create subnets within the VPC. Subnets are subdivisions of the VPC’s IP address range. Public subnets are designed to allow resources within them to directly access the internet. Private subnets, conversely, do not have direct internet access, enhancing security. The user will need to configure route tables to control the flow of traffic within the VPC and between subnets. Route tables contain rules that specify where network traffic should be directed. An internet gateway is attached to the VPC to enable communication with the internet.
Security is paramount, and AWS provides tools to manage network security. Security groups act as virtual firewalls for EC2 instances, controlling inbound and outbound traffic at the instance level. Network ACLs (Access Control Lists) provide an additional layer of security, operating at the subnet level. These ACLs allow or deny traffic based on IP addresses and ports. Customization is a key advantage of VPCs. The flexibility to define vpc configurations, subnet structures, route tables, and security policies allows organizations to tailor their network environment to meet specific application requirements. This level of control enables the building of highly secure and optimized cloud infrastructures. The concept of vpc define is very important when deciding about security in the cloud. When you properly define a vpc, you can properly configure its security measures, giving you control over your data and applications. The ability to define vpc parameters for your cloud implementation ensures that they align perfectly with your operational needs.
Core Components of a VPC Architecture
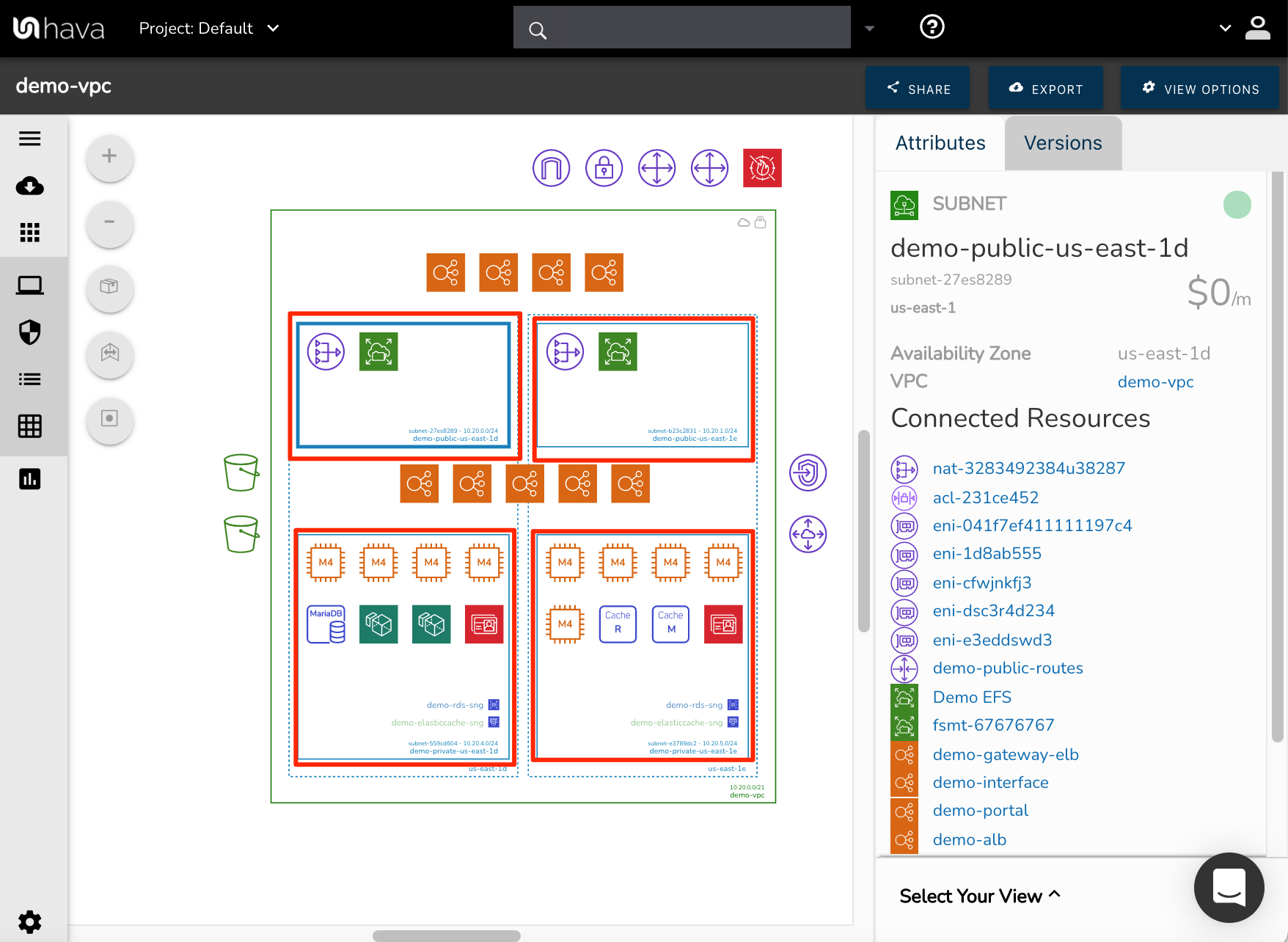
A Virtual Private Cloud (VPC) is built upon several key components that work together to provide a secure and functional network environment in the cloud. Understanding these components is crucial for designing, deploying, and managing your cloud infrastructure effectively. Each component plays a specific role in defining the network’s behavior and security posture. This section aims to provide a clear explanation of these core elements, showing how they contribute to the overall architecture of a VPC. A deep understanding of these components allows one to effectively utilize and also vpc define the required cloud infrastructure and security guidelines.
Subnets are fundamental building blocks of a VPC, representing a range of IP addresses within the VPC’s CIDR block. Subnets can be either public or private. Public subnets have a route to an internet gateway, allowing instances within them to communicate with the internet. Private subnets, on the other hand, do not have a direct route to the internet, enhancing security. Route tables contain a set of rules, called routes, that determine where network traffic is directed. Each subnet must be associated with a route table. An internet gateway is a horizontally scaled, redundant, and highly available VPC component that allows communication between instances in your VPC and the internet. A NAT gateway allows instances in private subnets to connect to the internet or other AWS services, but prevents the internet from initiating a connection with those instances. Security groups act as virtual firewalls for your instances, controlling inbound and outbound traffic at the instance level. Network ACLs (Access Control Lists) are another layer of security that control traffic at the subnet level, allowing or denying traffic based on IP addresses and ports.
The interplay between these components is what defines a VPC. For example, an instance launched in a public subnet can communicate with the internet because the subnet’s route table directs traffic to the internet gateway. The security group attached to the instance controls which traffic is allowed in and out, providing instance-level security. The network ACL associated with the subnet adds an additional layer of control at the subnet level. In contrast, an instance in a private subnet might use a NAT gateway to access the internet for software updates while remaining protected from unsolicited inbound traffic. Understanding how to configure these components is essential for creating a secure and functional network environment. The ability to vpc define the network architecture and rules greatly enhances the security. By properly configuring subnets, route tables, security groups, and network ACLs, businesses can create a layered security approach. Vpc define the network traffic rules also contributes to creating a robust and secure cloud infrastructure tailored to specific business needs and security requirements.
Securing Your Cloud Network: Best Practices
Securing a Virtual Private Cloud (VPC) requires a multi-layered approach. Implementing robust security measures is critical to protect sensitive data and applications. A key principle is least privilege. Grant only the necessary permissions to users and resources. This minimizes the potential impact of security breaches. Network segmentation is another vital technique. Divide the VPC into smaller, isolated segments. Security groups and Network ACLs (Access Control Lists) are essential tools for implementing segmentation. Security groups act as virtual firewalls. They control inbound and outbound traffic at the instance level. Network ACLs provide similar control at the subnet level. A well-defined security strategy contributes to a secure and functional network. The concept of a vpc define its security parameters, providing a confined and protected environment.
Enabling logging and monitoring provides visibility into network activity. Services like AWS CloudTrail and VPC Flow Logs capture valuable data. These logs can be used to detect suspicious behavior and troubleshoot issues. Regularly auditing security configurations is also crucial. Automated tools and manual reviews can identify vulnerabilities and misconfigurations. Addressing these issues promptly reduces the risk of attacks. Employing strong encryption methods protects data at rest and in transit. Encryption keys should be managed securely using dedicated key management services. Regular security assessments, including penetration testing, are valuable practices. These assessments help identify weaknesses. They enable proactive remediation. When we vpc define our strategy, security considerations must be paramount for any modern business.
A layered security strategy is essential. It combines multiple security controls to protect against a wide range of threats. Security groups and Network ACLs are integral components of this strategy. Security groups filter traffic based on defined rules. Network ACLs provide an additional layer of security by controlling traffic at the subnet level. These tools should be configured carefully to allow legitimate traffic. They block unauthorized access. Organizations must stay informed about the latest security threats and best practices. Adapting security measures to address emerging risks is paramount. Security is not a one-time task. It is an ongoing process that requires constant vigilance and improvement. By understanding how vpc define network access, security administrators can create a more secure environment. Organizations can protect their cloud resources from cyberattacks by using these best practices and maintaining a proactive security posture.
Common Use Cases for VPCs in Modern Businesses
Businesses today leverage virtual private clouds (VPCs) for a multitude of critical operations, enhancing agility and security. One prevalent application is hosting e-commerce websites. VPCs provide the isolation needed to protect sensitive customer data, such as credit card information and personal details. By deploying web servers, database servers, and application servers within a VPC, companies can create a secure environment for online transactions. A properly configured vpc define perimeter safeguards against unauthorized access and data breaches. This is critical for maintaining customer trust and complying with data protection regulations.
Microservices architectures also benefit significantly from VPCs. Each microservice can be deployed within its own subnet, further isolating it from other parts of the application. This modular approach enhances fault tolerance and allows for independent scaling of individual microservices. A vpc define strategy is beneficial in managing the communication and dependencies between microservices through controlled network policies. This allows developers to update and deploy individual services without impacting the entire application. This level of granularity is crucial for modern, agile software development practices.
VPCs are instrumental in managing big data analytics platforms. Companies can deploy their data lakes and analytics tools within a vpc define environment. This provides a secure and scalable platform for processing large volumes of data. By controlling network access and implementing security policies, organizations can ensure the confidentiality and integrity of their data. VPCs also support disaster recovery strategies by enabling the replication of data and applications to multiple availability zones. This ensures business continuity in the event of a failure. The ability to quickly recover from disruptions is a key advantage of using VPCs for critical workloads. With the right approach to vpc define architecture, businesses can enable innovation and agility while maintaining security and compliance.
VPC Peering and Connectivity Options
Virtual Private Clouds (VPCs) offer various connectivity options, extending their reach and integration capabilities. VPC peering allows you to connect one VPC with another, enabling network traffic routing between them. This is useful for sharing resources and services across different VPCs within the same cloud provider account or even across different accounts. VPC peering connections are established using the private IP addresses of the instances within the VPCs, providing secure communication. The configuration involves setting up routing rules in each VPC’s route table to direct traffic to the peer VPC. Understanding how vpc define network connections enhances network design.
Beyond VPC peering, other connectivity options provide links to on-premises networks. A VPN (Virtual Private Network) creates an encrypted connection over the internet between your VPC and your on-premises data center. This allows you to extend your corporate network into the cloud, creating a hybrid cloud environment. Direct Connect provides a dedicated network connection between your on-premises infrastructure and your VPC, bypassing the public internet. This offers lower latency, increased bandwidth, and a more consistent network experience compared to VPN. Choosing the right connectivity option depends on factors such as bandwidth requirements, security needs, and cost considerations.
Hybrid cloud environments, blending on-premises infrastructure with cloud resources, are increasingly common. VPCs are central to enabling hybrid cloud architectures. By using VPN or Direct Connect, organizations can seamlessly integrate their existing IT infrastructure with the scalability and flexibility of the cloud. This allows them to run applications and store data in the most appropriate location, optimizing performance, cost, and security. Security configurations when using vpc define the degree of isolation between connected networks. The choice between VPC peering, VPN, and Direct Connect hinges on the specific use case and desired level of integration. Each option offers distinct benefits and trade-offs, allowing organizations to tailor their cloud connectivity strategy to meet their unique requirements. VPCs facilitate hybrid cloud adoption by offering secure and reliable connectivity options to on-premises environments.
Troubleshooting Common VPC Issues
Encountering issues within a Virtual Private Cloud (VPC) environment is not uncommon. Effective troubleshooting is crucial for maintaining network stability and security. This section provides guidance on diagnosing and resolving typical VPC problems. When connectivity fails, begin by examining the network configuration. Verify that security group rules and network ACLs permit traffic flow between the source and destination. Incorrectly configured rules are a frequent cause of connectivity disruptions. Confirm that the route tables contain the necessary routes to direct traffic appropriately, including routes to the internet gateway or NAT gateway for external communication. A proper vpc define network requires meticulous attention to these details.
Routing errors can prevent instances within the VPC from reaching external resources or other instances within the same VPC. Utilize network monitoring tools to trace the path of network packets. Tools like `traceroute` or `ping` can help pinpoint where the connection is failing. Confirm that the CIDR blocks for subnets do not overlap, as this can lead to unpredictable routing behavior. Examine the effective routes associated with each subnet to ensure traffic is being directed as intended. If using VPC peering, verify that the peering connection is active and that the route tables on both sides are configured to route traffic to the peer VPC’s CIDR block. Understanding how to vpc define network routes is vital for resolving these issues.
Security misconfigurations can expose the VPC to potential threats. Regularly audit security group rules and network ACLs to ensure they adhere to the principle of least privilege. Overly permissive rules can inadvertently grant unauthorized access to resources. Review logs from network devices and security tools to identify suspicious activity. Implement intrusion detection systems (IDS) and intrusion prevention systems (IPS) to proactively detect and respond to security incidents. Ensure that all instances within the VPC have the latest security patches installed. Consider using AWS Trusted Advisor or similar services to identify potential security vulnerabilities. Remembering to vpc define these security configurations will contribute to a more robust cloud infrastructure.
Future Trends and the Evolution of VPC Technology
Context_9: Explore emerging trends in VPC technology, such as serverless computing integration, enhanced automation capabilities, and advanced security features. Discuss how these trends are shaping the future of cloud networking and enabling businesses to build more agile, scalable, and secure applications. Consider the impact of technologies like Kubernetes and containerization on VPC design and management.
The landscape of virtual private clouds is continuously evolving, driven by the increasing demands of modern businesses and technological advancements. One notable trend is the deeper integration of VPCs with serverless computing architectures. As organizations adopt serverless technologies like AWS Lambda or Azure Functions, the underlying network infrastructure, often a VPC, must adapt to provide seamless connectivity and security. This involves designing VPCs that can efficiently handle the ephemeral nature of serverless functions, automatically scaling network resources as needed. Enhanced automation capabilities are also becoming increasingly important. Infrastructure-as-Code (IaC) tools, such as Terraform and CloudFormation, are used to automate the deployment and management of VPC resources, reducing manual effort and improving consistency. The goal is to create self-healing and self-optimizing networks that can adapt to changing application requirements in real-time. Security remains a top priority, leading to the development of advanced security features for VPCs. These features include more granular network segmentation, intrusion detection and prevention systems, and automated threat response mechanisms. The aim is to provide a layered security approach that protects against a wide range of threats, from unauthorized access to data breaches. The concept of “vpc define” how the security must evolve to stay relevant. For example, machine learning algorithms are increasingly being used to analyze network traffic and identify suspicious patterns, enabling proactive security measures. Kubernetes and containerization technologies have a significant impact on VPC design and management. As organizations embrace containerized applications, the network infrastructure must be able to support the dynamic and distributed nature of these workloads. This involves creating VPCs that can efficiently manage container networking, providing isolation and security for individual containers, while allowing them to communicate with each other and with external services. VPCs are becoming more programmable and software-defined. This allows organizations to customize their network environment to meet the specific needs of their applications. Software-Defined Networking (SDN) technologies enable fine-grained control over network traffic, allowing organizations to optimize performance, improve security, and reduce costs.
Looking ahead, the future of VPC technology is likely to be shaped by several key factors. The increasing adoption of hybrid and multi-cloud environments will drive the need for VPCs that can seamlessly connect to on-premises networks and other cloud providers. This will involve the use of technologies such as VPNs, Direct Connect, and VPC peering to create a unified network infrastructure. The rise of edge computing will also have a significant impact on VPC design. As organizations deploy applications closer to the edge, VPCs will need to extend their reach to these edge locations, providing secure and reliable connectivity. This will involve the use of technologies such as content delivery networks (CDNs) and edge computing platforms. Ultimately, the evolution of VPC technology is about enabling businesses to build more agile, scalable, and secure applications. By embracing emerging trends and adopting best practices, organizations can leverage the power of VPCs to drive innovation and achieve their business goals. The core principle to “vpc define” is still valid, and VPCs will continue to play a crucial role in the cloud computing landscape.
Future Trends and the Evolution of VPC Technology
The realm of Virtual Private Clouds (VPCs) is not static; it is continuously evolving to meet the dynamic demands of modern cloud computing. Several trends are shaping the future of VPCs, promising increased flexibility, enhanced security, and improved automation. One significant trend is the rise of serverless computing. As serverless architectures gain traction, VPCs are adapting to provide the necessary isolation and networking capabilities for serverless functions. This involves finer-grained control over network access and security policies, ensuring that serverless applications operate within a secure and well-defined environment. The integration of artificial intelligence (AI) and machine learning (ML) is also influencing VPC technology. AI-powered security tools can automate threat detection and response within VPCs, proactively identifying and mitigating potential security breaches. Furthermore, ML algorithms can optimize network performance by dynamically adjusting routing configurations and resource allocation based on real-time traffic patterns. Infrastructure-as-Code (IaC) is becoming increasingly prevalent, enabling organizations to define and manage their VPC infrastructure through code. This approach facilitates automation, version control, and repeatability, streamlining the deployment and management of VPCs. IaC tools allow for the creation of consistent and reproducible environments, reducing the risk of configuration errors and improving overall operational efficiency. As cloud adoption expands, the need for seamless hybrid and multi-cloud connectivity is driving innovations in VPC technology. VPC peering and other connectivity options are becoming more sophisticated, allowing organizations to seamlessly connect their on-premises networks and multiple cloud environments. This enables the creation of hybrid cloud architectures that leverage the strengths of both on-premises and cloud resources. Defining what a vpc define implies understanding its architectural importance.
Security remains a paramount concern in the evolution of VPCs. Enhanced security features, such as micro-segmentation and network isolation, are being integrated into VPC architectures to provide granular control over network traffic and minimize the attack surface. Micro-segmentation allows organizations to divide their VPCs into smaller, isolated segments, limiting the lateral movement of attackers in the event of a breach. Network isolation techniques, such as zero-trust networking, are also gaining popularity, requiring strict authentication and authorization for all network traffic. Automation is playing an increasingly important role in VPC management. Automated provisioning, configuration, and monitoring tools are simplifying the deployment and operation of VPCs, reducing the burden on IT teams. These tools can automatically scale VPC resources based on demand, ensuring optimal performance and availability. Furthermore, automated security checks and compliance audits can help organizations maintain a strong security posture and meet regulatory requirements. These advances are crucial to properly vpc define its relevance.
The concept of software-defined networking (SDN) is also influencing the evolution of VPCs. SDN allows for centralized control over network resources, enabling organizations to dynamically adjust network configurations based on changing business needs. This provides greater flexibility and agility, allowing organizations to quickly adapt to new opportunities and challenges. SDN also facilitates network virtualization, enabling the creation of virtual networks that are isolated from the underlying physical infrastructure. Ultimately, the future of VPCs is characterized by increased automation, enhanced security, and improved flexibility. As cloud technology continues to evolve, VPCs will play an increasingly critical role in enabling organizations to securely and efficiently deploy and manage their applications and data in the cloud. Understanding properly what vpc define allows to anticipate these changes.
What is a Private Network in the Cloud?
A virtual private cloud (VPC) is essentially a private network within a public cloud environment. Think of it as your own secure data center existing within a larger cloud infrastructure. Unlike traditional on-premises networks that require physical hardware and dedicated infrastructure, a VPC offers a software-defined network that is logically isolated from other networks. This provides enhanced control and security, with the benefits of cloud scalability and flexibility. When we vpc define its network boundaries it’s about security and control within shared infrastructure.
One key advantage of a VPC is its ability to isolate your resources. This isolation is crucial for security and compliance. You have full control over who can access your resources and how they can access them. Using familiar network concepts like IP addresses, subnets, and routing tables, you can customize your VPC environment to mirror your existing on-premises network or create a completely new network architecture. Resources launched within the VPC can communicate securely with each other and with the outside world, based on the rules you define. The flexibility to vpc define your security parameters is a massive advantage.
Compared to traditional networks, VPCs offer significant cost savings and increased agility. You avoid the upfront capital expenditure of purchasing and maintaining physical hardware. Instead, you pay only for the resources you consume. Cloud-based VPCs can scale up or down quickly to meet changing demands, which allows you to respond rapidly to new business opportunities. Further, the agility allows to vpc define new configurations. Security is paramount, VPCs provide a secure and isolated environment for your applications and data, helping you meet regulatory requirements and protect sensitive information. The ability to control network access and isolate resources reduces the risk of unauthorized access and data breaches. By allowing you to logically vpc define cloud spaces, these environments become a great place to host instances.
What is a Private Network in the Cloud?
A virtual private cloud (VPC) can be understood as a private network within a public cloud environment. It’s like having your own dedicated network space, but it resides within the infrastructure of a cloud provider. Think of it as a secure, isolated zone where you can launch and manage your applications and data. Traditional on-premises networks involve physical hardware, maintenance, and significant upfront costs. In contrast, VPCs offer scalability, flexibility, and cost-efficiency by leveraging the cloud provider’s infrastructure. With a VPC, resources can be scaled up or down as needed, and you only pay for what you use. The cloud based resources available where users can vpc define their needs.
One of the primary benefits of a VPC is the isolation it provides. It allows you to create a logically isolated section of the cloud, where you have complete control over your network configuration. This includes defining your own IP address ranges, creating subnets, and configuring route tables and network gateways. This level of control ensures that your resources are segregated from other users in the cloud, enhancing security and reducing the risk of unauthorized access. Security is a paramount concern for any organization, and VPCs offer robust security features to protect your data and applications. For example, resources can vpc define by setting up security groups and network ACLs, which act as virtual firewalls to control inbound and outbound traffic.
The ability to vpc define your network environment allows businesses to tailor their cloud infrastructure to meet specific compliance and regulatory requirements. Whether you need to comply with HIPAA, PCI DSS, or GDPR, a VPC can provide the necessary controls and security measures to ensure compliance. VPCs offer a powerful combination of flexibility, scalability, and security, making them an essential component of modern cloud computing strategies. The functionality to vpc define, ensures that businesses are empowered to build and manage their applications and data in a secure and efficient manner.
Understanding Virtual Private Clouds: Defining Your Secure Space
A virtual private cloud (VPC) serves as a logically isolated section within a public cloud, essentially creating a “private network in the cloud.” Think of it as renting a secure, dedicated office space within a large co-working building. Unlike traditional on-premises networks that require physical hardware and infrastructure management, a VPC leverages the cloud provider’s existing resources. This provides unparalleled flexibility and scalability. A key benefit is the inherent isolation; resources within a VPC are shielded from other users of the public cloud, enhancing security. When we vpc define, it’s about creating that digital boundary.
Traditional networks often require significant upfront investment in hardware, ongoing maintenance, and physical security measures. A VPC eliminates these burdens. Resources can be provisioned and de-provisioned on demand, optimizing costs and allowing businesses to adapt quickly to changing needs. This dynamic allocation is a significant advantage over the static nature of traditional infrastructure. Furthermore, cloud providers offer a range of security features and compliance certifications that can be difficult and expensive to achieve independently. To vpc define is also to establish a parameter of security. With that parameter established, the environment within the VPC can be further protected.
The core concept of a VPC revolves around isolation and security. It allows users to define their own network topology, including subnets, route tables, and security policies. This level of control is crucial for organizations that need to meet specific regulatory requirements or protect sensitive data. In essence, a VPC empowers businesses to create a secure and customized cloud environment that aligns perfectly with their unique requirements. If we want to vpc define in just a sentence, it could be said that it empowers businesses to create a secure and customized cloud environment. The flexibility and security it offers make it an invaluable tool for modern cloud computing. When discussing vpc define, we must emphasize the concept of logical isolation within a multi-tenant cloud environment. This is a defining characteristic and a major factor in its widespread adoption.


.png)