What is a Virtual Network Cloud and Why Should You Use It?
A virtual private cloud, commonly referred to as a VPC, represents a fundamental concept in cloud computing, serving as a logically isolated section within a public cloud environment. Essentially, a VPC allows organizations to carve out their own private network space within a shared cloud infrastructure, granting a high degree of control and customization. This isolation is achieved through network virtualization techniques, allowing a VPC to operate independently of other networks within the same cloud provider’s infrastructure. One of the primary reasons organizations adopt VPCs is to establish secure and controlled network environments. A VPC provides the necessary framework for implementing granular access controls, enabling firms to dictate which resources can communicate with each other and with the outside world. This level of control is paramount for protecting sensitive data and ensuring compliance with industry standards.
The isolation offered by a VPC also plays a crucial role in ensuring the stability and performance of applications. By preventing network interference from other users of the public cloud, a VPC guarantees that resources operate in a dedicated and reliable environment. Furthermore, the customization aspect is another compelling reason for organizations to embrace VPCs. It empowers users to define their network architecture in line with specific business needs, implementing unique configurations for subnets, routing tables, and network gateways. This flexibility allows the creation of tailored network environments suited to diverse application requirements. The concept of a virtual private cloud is, therefore, pivotal in fostering a secure, isolated and customizable cloud experience, allowing organizations to fully leverage the power of public cloud while maintaining a high degree of control over their networking infrastructure. A virtual private cloud infrastructure enables companies to take advantage of cloud computing while ensuring all the benefits of a privately controlled network segment.
How to Create a Virtual Private Cloud: Step-by-Step
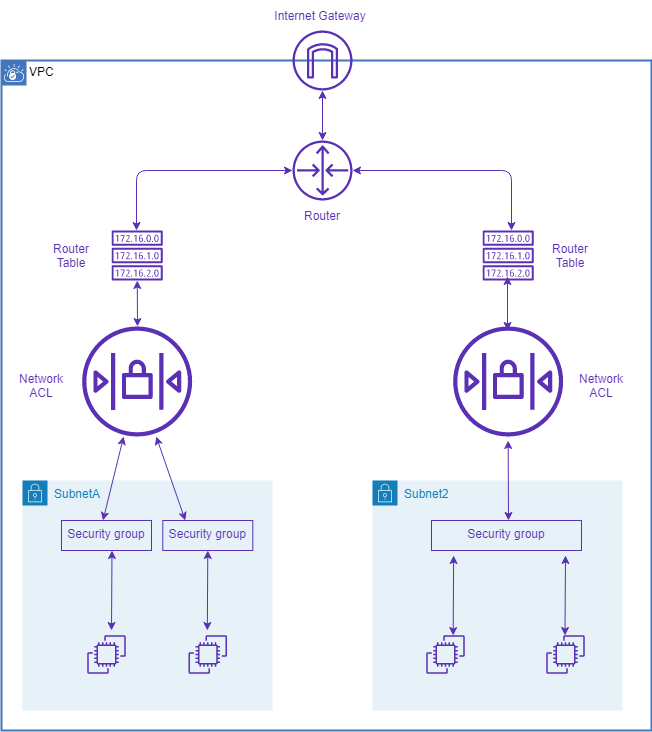
Setting up a virtual private cloud (VPC) involves a series of key steps that are essential for establishing a secure and functional network environment in the cloud. The process begins with choosing a suitable CIDR (Classless Inter-Domain Routing) block, which defines the range of IP addresses available within the VPC. This initial decision is crucial as it determines the scale and capacity of your virtual network. Subsequently, the chosen CIDR block is divided into subnets, allowing for the organization of resources into logical groups. These subnets can be designed to segregate different types of applications or services, further enhancing security and manageability. The number and size of the subnets are tailored to meet the specific needs of the organization’s architecture. The configuration also involves establishing network gateways, which serve as entry and exit points for traffic. These gateways include internet gateways for communication with the public internet and NAT (Network Address Translation) gateways for allowing private resources to access external resources. The careful design of the initial vpc configuration is fundamental to ensuring network performance and security. This includes planning for adequate address space for current and future expansion, and proper separation of public and private facing resources.
While these steps provide a general framework, the specific implementation may vary depending on the cloud provider being used. However, the underlying principles of selecting an appropriate CIDR block, subnetting, and gateway setup remain consistent across most platforms. It’s also worth noting that the selection of the vpc’s CIDR is a one-time choice as it cannot be easily modified once the vpc is created. Thus, planning for future growth and resource allocation is vital at this phase. For a secure and well architected vpc, proper planning and configuration of route tables, will be covered in subsequent sections. This includes defining explicit rules for how traffic should be routed within and out of the vpc which is fundamental for connecting internal resources, accessing internet based services, and establishing peering connections with other VPCs, or on premises networks. In summary, setting up a vpc requires careful consideration of the address space, resource allocation, and network access points. It represents a crucial foundation for all subsequent cloud deployments and will impact performance, security and scalability of your environment. Therefore, a well-planned virtual private cloud is key to leveraging the full potential of cloud computing.
Subnets Within a Cloud Network
A virtual private cloud (VPC) is further organized into smaller, logical divisions called subnets. These subnets segment the VPC’s IP address space, making it easier to manage and control network resources. Each subnet is assigned a unique range of IP addresses from the overall VPC CIDR block. This division allows for greater control over resource placement and network security within the vpc. For example, one could dedicate a subnet for web servers, another for databases, and yet another for internal applications, promoting isolation and security. Effective subnet planning is crucial for optimal VPC performance and scalability.
The distinction between public and private subnets is critical within a VPC. Public subnets have IP addresses that are directly accessible from the internet, typically used for web servers or other publicly facing applications. Conversely, private subnets possess IP addresses that are not directly routable from the internet, providing enhanced security for sensitive internal applications and databases within the vpc. This segregation enhances security by limiting exposure to external threats. By carefully placing resources within appropriate subnets, organizations can create a robust security posture for their vpc. Proper subnet design is an essential aspect of any well-architected vpc.
Effective subnet design within a VPC allows for the separation of resources based on their security needs, functionality, and location. This separation simplifies network administration, improves security, and facilitates scalability. For example, placing development and production environments in separate subnets within the same vpc prevents unintended access or interference. Similarly, separating databases from web servers on different subnets enhances security by isolating critical data. Careful consideration of subnet size, number, and placement is crucial for optimizing resource utilization and maintaining a secure vpc. Utilizing subnets is a fundamental strategy in designing secure and manageable VPC environments.
Enhancing Security with Access Control Lists and Security Groups
Access Control Lists (ACLs) and Security Groups are fundamental components for securing a virtual private cloud (VPC) and controlling network traffic flow. They act as virtual firewalls, filtering network traffic based on pre-defined rules. Understanding their distinct roles is crucial for effective VPC security. ACLs operate at the subnet level, inspecting traffic entering and leaving the subnet. This means they control traffic based on source and destination IP addresses, ports, and protocols. By contrast, security groups function at the instance level, controlling inbound and outbound traffic for individual virtual machines within the VPC. They provide a more granular level of control, allowing for instance-specific security policies. This difference is vital; ACLs provide a broad, subnet-wide approach, while security groups offer precise control over individual instances within that subnet, which can be especially helpful in complex VPC architectures. Properly configuring both ACLs and security groups is essential for a robust VPC security posture.
Effective VPC security relies on implementing a layered approach, combining both ACLs and security groups for comprehensive protection. For example, an ACL might restrict all inbound traffic to a specific subnet, except for traffic destined for a specific port used by a web server. Then, security groups could further restrict access to that web server only to trusted IP addresses or ranges, preventing unauthorized access. This layered defense significantly strengthens the security of the VPC. Consider also the implications of default security group settings; often they are more permissive than necessary. It’s a best practice to review and modify these defaults to align with your specific security requirements for your VPC. Regularly auditing these rules is essential to ensure the continued effectiveness of your VPC’s security measures, mitigating any potential vulnerabilities. Regular reviews of security group and ACL rules are crucial in maintaining a secure VPC.
Beyond ACLs and security groups, other security best practices for VPCs include regular security assessments, implementing intrusion detection and prevention systems, and employing robust logging and monitoring capabilities. These measures, in conjunction with appropriately configured ACLs and security groups, form a multi-layered defense-in-depth strategy to safeguard the resources within your VPC. By embracing a proactive approach to security and regularly reviewing and updating configurations, organizations can significantly reduce the risk of vulnerabilities and breaches in their VPC environments. The goal is to create a VPC environment that is both secure and efficient, facilitating business operations while minimizing the exposure to potential threats. Careful planning and consistent attention to security best practices are paramount for successful and secure VPC deployment and management.
Connecting Your On-Premise Infrastructure to the Cloud Through VPC Peering
VPC peering is a crucial mechanism that facilitates secure and efficient connections between different virtual private clouds (VPCs) or between a VPC and an on-premises network. This capability is invaluable for organizations operating hybrid cloud environments or needing to seamlessly integrate their existing infrastructure with cloud-based resources. By establishing a connection, organizations can effectively share data and applications across these distinct environments, improving collaboration and streamlining workflows. The benefits extend beyond simple connectivity; VPC peering enhances security by allowing fine-grained control over network traffic between peered networks, minimizing the exposure of sensitive data.
Several compelling use cases demonstrate the power of VPC peering. For example, an organization might leverage VPC peering to connect its development VPC, containing staging environments, with its production VPC, allowing developers to test and deploy applications without compromising the security or stability of live systems. Another common scenario involves extending an on-premises data center to the cloud, creating a hybrid infrastructure. This allows organizations to leverage cloud-based resources for scalability and cost-effectiveness while retaining control over sensitive data housed on-premises. The VPC acts as a bridge, ensuring seamless communication between both environments. The setup enables easier migration of applications and data to the cloud in a phased approach, minimizing disruption.
Implementing VPC peering offers significant advantages. Improved security is paramount, as traffic remains within the controlled environment of the VPC network. This reduces the risk of exposure to external threats. Moreover, VPC peering often results in lower latency compared to using the public internet for inter-network communication, leading to faster data transfer and improved application performance. The ability to easily share resources and applications across different VPCs or between a VPC and an on-premises network simplifies management and reduces operational complexity. Careful consideration of security groups and network access control lists remains crucial even within a peered VPC environment to maintain a robust and secure network infrastructure. Choosing the right VPC peering configuration depends heavily on the specific needs and security requirements of your organization and its cloud strategy.
Exploring the Functionality of Route Tables
Route tables are fundamental components within a VPC, acting as the traffic directors that determine how network traffic is routed within and outside the virtual private cloud. They function by associating specific IP address ranges (destinations) with corresponding network gateways or subnets. When a packet enters the VPC, the route table consults its entries to find the optimal path for the packet, based on its destination IP address. This allows for the precise control of network traffic flow, ensuring that data reaches its intended recipient efficiently and securely. Effective route table management is crucial for ensuring optimal performance and security within the vpc.
Configuring route tables involves defining rules that specify the destination IP address range and the next hop. The next hop could be another subnet within the VPC, an internet gateway for external traffic, or a VPN gateway for connections to on-premises networks. For instance, a route could be created to send all traffic destined for the public internet through the internet gateway. Alternatively, internal communication within the VPC can be routed directly between subnets, bypassing the internet gateway and enhancing security and performance. Understanding these routing rules and their implications is crucial to designing a well-architected VPC network. Sophisticated route table configurations can implement complex network topologies, enabling efficient traffic management and providing flexibility in how the VPC interacts with both internal and external resources. Properly configured route tables are essential for a secure and effective vpc.
Moreover, managing multiple route tables within a single VPC offers increased flexibility and granular control over network traffic. This allows for the segregation of traffic based on different criteria, such as security zones or application requirements. For example, a company might have separate route tables for sensitive data traffic and less critical application traffic, allowing for different security policies and levels of access to be implemented. This approach improves security, increases efficiency, and enables more refined control over the internal workings of the vpc. The ability to modify routing rules dynamically allows for adaptive responses to network conditions or changes in security requirements. This dynamic nature makes route tables an invaluable tool in managing and securing a vpc.
Choosing the Right Cloud Provider for Your Virtual Cloud
Selecting the appropriate cloud provider for your VPC needs is a crucial decision impacting your infrastructure’s security, scalability, and cost-effectiveness. Several factors merit careful consideration. The provider’s feature set should align with your specific requirements; some offer advanced VPC features like advanced networking options or robust security tools, which may be essential for complex applications. Pricing models vary significantly; understanding the cost structure, including per-hour charges for virtual machines and data transfer fees, is essential for budgeting. Security is paramount when dealing with a VPC, and providers offer varying levels of security features and certifications. Investigate their security measures, compliance certifications, and data residency policies to ensure alignment with your security requirements. Finally, robust customer support is crucial; evaluate the provider’s support options, response times, and documentation quality to ensure you have the assistance needed when managing your VPC.
Major cloud providers such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP) all offer comprehensive VPC solutions. Each provider’s VPC implementation has its nuances, strengths, and weaknesses, and the optimal choice depends on your specific needs and existing infrastructure. Consider factors like integration with existing on-premises systems, the availability of specific services (like databases or managed services) within the VPC environment, and the provider’s global reach and data center locations. A thorough evaluation of these factors will help ensure a smooth transition and effective utilization of your VPC. Remember that selecting the right cloud provider is not a one-time decision; your needs may evolve, so regular reassessment of your chosen provider’s capabilities in relation to your evolving VPC needs is recommended.
Beyond the major players, several other cloud providers offer VPC services, each with its own unique selling proposition. Some specialize in specific industries or offer niche services that might better suit certain business models or application requirements. The ideal VPC solution is highly context-dependent, and careful research is crucial. The choice of a cloud provider fundamentally influences your VPC’s performance, security, and overall operational efficiency. Consider the long-term implications of your decision, accounting for potential growth, scalability demands, and anticipated changes in your infrastructure needs. A well-informed decision contributes to a stable and secure VPC environment, maximizing the benefits of cloud computing.
Key Benefits and Considerations When Using Virtual Networks
Utilizing a Virtual Private Cloud (VPC) offers significant advantages for businesses of all sizes. The primary benefit lies in the enhanced security a VPC provides. By creating a logically isolated section within a larger public cloud infrastructure, organizations can effectively segment their network resources, minimizing the risk of unauthorized access and data breaches. This isolation is crucial for protecting sensitive data and maintaining compliance with industry regulations. Furthermore, a VPC allows for greater customization and control over network infrastructure. Unlike traditional shared hosting environments, VPCs empower organizations to tailor their network configurations to their specific needs, including the choice of IP address ranges, subnet configurations, and security policies. This level of control leads to improved efficiency and optimized resource utilization. The flexibility offered by a VPC extends to scaling operations, allowing organizations to easily expand or contract their network resources as needed, without impacting existing applications or services. Properly configured VPCs enable efficient management and improved performance, ultimately contributing to cost optimization.
However, the implementation and management of a VPC also present certain considerations. Setting up a secure and efficient VPC requires careful planning and configuration. Organizations need to define clear network security policies, implement robust access control mechanisms, and regularly monitor network traffic for any suspicious activity. Failure to properly configure a VPC can lead to security vulnerabilities, performance issues, or increased operational costs. Therefore, understanding the intricacies of VPC networking, including routing tables, subnets, and security groups, is essential for successful deployment. Moreover, the ongoing management of a VPC requires expertise and dedicated resources. Regular security audits, updates, and monitoring are vital to maintain the security and efficiency of the VPC infrastructure. The choice of cloud provider also significantly impacts the overall experience with a VPC; careful consideration should be given to the features, pricing model, and support offered by different providers to ensure a seamless and efficient integration within existing IT infrastructure.
In conclusion, the strategic implementation of a well-architected VPC offers considerable benefits, particularly in terms of security, isolation, and customization. However, organizations must carefully weigh the complexities of configuration and management. By proactively addressing potential challenges and investing in the necessary expertise, businesses can effectively leverage the power of VPCs to build secure, scalable, and cost-effective cloud environments. A well-planned VPC strategy can be instrumental in achieving long-term business objectives and ensuring the security and integrity of critical data and applications. Investing time in understanding and optimizing your VPC infrastructure is paramount for maximizing the return on investment in cloud computing.