Understanding the Essence of Virtual Machine Containers
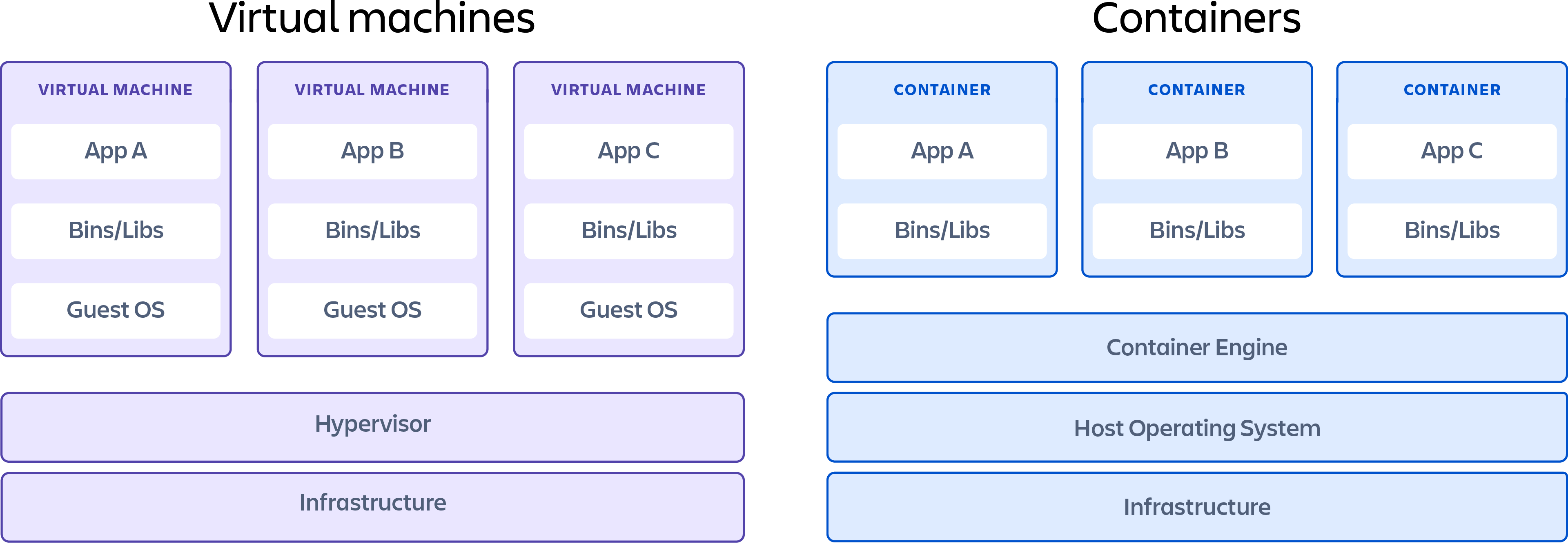
Virtual machine containers represent a compelling evolution in virtualization technology, bridging the gap between traditional virtual machines (VMs) and standard OS-level containers, such as Docker. Unlike traditional VMs, which require a full-fledged guest operating system for each instance, virtual machine containers encapsulate applications within lightweight VMs. These lightweight VMs share the host operating system’s kernel but maintain strong isolation through hardware virtualization. This approach offers a significant advantage in terms of resource efficiency. A virtual machine container consumes far less resources compared to its traditional VM counterpart because it avoids the overhead of running a complete guest OS. Resource efficiency translates directly into cost savings, improved density, and faster startup times.
The key characteristic that distinguishes virtual machine containers is their robust isolation. This isolation stems from the hardware virtualization technology that underlies them. Each virtual machine container operates within its own isolated environment, preventing applications from interfering with each other or the host system. This enhanced isolation provides a superior level of security compared to standard containers, where applications share the same kernel and are more susceptible to security breaches. Virtual machine container technology addresses the security concerns associated with traditional containerization, making them suitable for sensitive workloads and multi-tenant environments. A virtual machine container implements a secure barrier against potential threats and vulnerabilities.
Underlying technologies like Intel VT-x or AMD-V enable the creation of these lightweight virtual machines. These technologies provide hardware-level support for virtualization, allowing the host system to efficiently manage and isolate virtual machine containers. The resource efficiency and robust isolation of a virtual machine container make them an increasingly attractive option for modern application deployment. As organizations prioritize security and optimize resource utilization, virtual machine containers offer a powerful solution that combines the benefits of both traditional VMs and standard containers. The increasing adoption of virtual machine containers reflects the growing need for secure and efficient containerization solutions in the cloud-native era. A virtual machine container is a key technology for many organizations in the world.
How to Leverage Virtualized Containers for Application Deployment
Deploying applications using virtual machine containers involves a structured approach, balancing ease of use with the robust isolation they offer. The initial step is setting up the environment. This typically involves installing a virtual machine container runtime, such as Kata Containers or Firecracker. These runtimes provide the necessary infrastructure to create and manage lightweight virtual machines. Ensure the chosen runtime is compatible with the host operating system and hardware. Setting up the environment may also require configuring networking and storage resources that the virtual machine containers will utilize. This might involve creating virtual networks and defining storage volumes.
Next, the application needs to be containerized, similar to how it would be for Docker. This involves creating a container image using a tool like Docker. However, instead of running this image directly with Docker, it will be used as the basis for a virtual machine container. Configuration is a critical step. Define resource limits for the virtual machine container, such as CPU and memory allocation. This ensures that the application has the resources it needs without impacting other applications or the host system. Security is paramount when deploying applications in any containerized environment. With virtual machine containers, the stronger isolation provides an inherent security advantage. However, it’s still crucial to implement security best practices, such as using minimal base images, regularly updating software, and implementing network segmentation. The virtual machine container enhances security by isolating the application within its own kernel, minimizing the attack surface.
Finally, run the application within the virtual machine container. This involves using the chosen runtime to create a new virtual machine instance based on the container image. Monitor the application’s performance and resource usage to identify any bottlenecks or issues. Virtual machine container technology offers scalability benefits. Multiple instances of the application can be deployed across different hosts or within a single host, depending on resource availability. To achieve optimal performance with virtual machine containers, consider the following best practices: Use lightweight operating system images to minimize the virtual machine’s footprint. Optimize the application code for efficient resource utilization. Implement caching mechanisms to reduce latency. Virtual machine container offers a compelling solution for secure and scalable application deployment. The use of virtual machine container technology provides a balance between the agility of containers and the security of virtual machines. The virtual machine container provides the advantages of both worlds.
Virtualization Evolution: VM Containers vs. Standard Containers
This section delves into a comparative analysis of virtual machine containers and traditional OS-level containers, exemplified by Docker. While both technologies address application isolation and portability, they differ significantly in their underlying architectures and resulting characteristics. Understanding these distinctions is crucial for selecting the appropriate containerization strategy for specific workloads and environments. A key differentiator lies in the level of isolation provided. Virtual machine containers offer stronger isolation by encapsulating each container within a lightweight virtual machine. This approach provides a dedicated kernel for each container, minimizing the risk of interference or security breaches between containers. Standard containers, on the other hand, share the host operating system’s kernel, which can lead to potential security vulnerabilities and resource contention.
Resource utilization is another critical area for comparison. Standard containers generally have a smaller footprint and lower overhead compared to virtual machine containers. This is because they leverage the host OS kernel directly, avoiding the overhead of running a separate kernel for each container. However, the increased isolation offered by virtual machine containers can sometimes lead to more predictable performance and better resource management, especially in multi-tenant environments. The performance overhead associated with virtual machine containers has decreased significantly in recent years with the advent of lightweight virtualization technologies. Factors such as the choice of hypervisor and the configuration of the virtual machine can impact performance. When making a decision, it’s important to evaluate the trade-offs between resource efficiency, security, and performance based on the specific requirements of the application.
The choice between virtual machine containers and standard containers depends heavily on the specific use case. Scenarios that demand strong isolation and enhanced security, such as running untrusted code or handling sensitive data, often favor virtual machine containers. In such cases, the added overhead is a worthwhile trade-off for the increased security. For applications with less stringent security requirements and a focus on maximizing resource efficiency, standard containers may be a more suitable choice. Furthermore, the portability and ecosystem advantages of Docker often make it a preferred option for many general-purpose applications. Technologies like Kata Containers represent an effort to bridge the gap between the two approaches, offering the security of virtual machine containers with a performance profile closer to that of standard containers. The continued evolution of containerization technologies promises to further blur the lines between these two approaches, offering developers a wider range of options to meet their specific needs. The concept of virtual machine container is gaining traction as security concerns become paramount in modern application deployments.
Security Advantages of Virtual Machine Based Containers
Virtual machine containers offer enhanced security features, primarily stemming from their strong isolation capabilities. This isolation is a key differentiator compared to traditional OS-level containers. A virtual machine container encapsulates an application within its own isolated environment. This environment includes its own kernel, providing a robust barrier against potential security breaches. This architecture significantly reduces the “blast radius” of any security incident. If one virtual machine container is compromised, the impact is generally limited to that specific container. The stronger isolation inherent in virtual machine containers makes them particularly well-suited for multi-tenant environments. In these environments, multiple users or applications share the same physical infrastructure. The isolation provided by virtual machine containers helps prevent unauthorized access or interference between tenants. This is a critical factor for maintaining data confidentiality and integrity.
The enhanced security of virtual machine containers also addresses several security risks associated with traditional containerized applications. One such risk is kernel exploitation. Because each virtual machine container has its own kernel, a vulnerability in one kernel does not necessarily affect other containers. This contrasts with OS-level containers, which share the host operating system’s kernel. Another security benefit is reduced attack surface. The minimal operating system within a virtual machine container contains fewer components than a full-fledged operating system. This reduces the number of potential vulnerabilities that an attacker could exploit. This stronger isolation offered by the virtual machine container can have a positive impact on compliance and regulatory requirements. Many regulations require organizations to implement strong security controls to protect sensitive data. The isolation provided by virtual machine containers can help meet these requirements by providing a secure and isolated environment for sensitive applications and data.
The benefits of virtual machine container’s improved security extend to various aspects of application deployment and management. For example, running untrusted code becomes safer. The isolation ensures that malicious code cannot easily escape the container and compromise the host system or other applications. Isolating sensitive data within virtual machine containers adds an extra layer of protection. Even if an attacker gains access to the container, accessing data outside the container becomes significantly more difficult. This is vital for applications that handle confidential or regulated information. Organizations should carefully evaluate the security features of different virtual machine container solutions. Factors such as the type of hypervisor used, the security hardening of the guest operating system, and the availability of security updates can all affect the overall security posture of the virtual machine container environment. By understanding and addressing these factors, organizations can leverage virtual machine containers to enhance the security of their applications and data. This is particularly relevant in regulated industries with strict security requirements.
Streamlining Operations: Use Cases for Virtual Machine Containers
Virtual machine containers are finding increasing adoption across various industries, offering a unique blend of isolation and efficiency. This makes them suitable for a wide array of use cases where security and performance are paramount. Their ability to run applications in isolated environments provides significant advantages over traditional containerization and full virtualization solutions. The practical applications span across different sectors, addressing specific challenges related to security, portability, and resource management. This section explores some key real-world scenarios where virtual machine containers demonstrate their value.
One prominent use case for virtual machine containers is running untrusted code. Organizations can leverage the strong isolation offered by virtual machine containers to execute potentially malicious or vulnerable code without compromising the host system. This is particularly useful in environments like online sandboxes or automated testing platforms. Similarly, virtual machine containers excel at isolating sensitive data. Industries like finance and healthcare, where data privacy is critical, can utilize virtual machine containers to protect sensitive information from unauthorized access. The enhanced security features of virtual machine containers create a secure environment for handling confidential data, aiding in compliance with strict regulatory requirements. Another key application is improving application portability. Virtual machine containers enable applications to run consistently across different platforms, simplifying deployment and management. This is beneficial for organizations that need to deploy applications in diverse environments, such as on-premises data centers, public clouds, and edge devices. The virtual machine container encapsulates the application and its dependencies, ensuring consistent behavior regardless of the underlying infrastructure.
Moreover, virtual machine containers can solve specific challenges related to resource utilization and application security. In multi-tenant environments, virtual machine containers provide a strong layer of isolation between tenants, preventing resource contention and security breaches. This is particularly valuable for cloud service providers who need to ensure the security and performance of their services. For example, a financial institution might use virtual machine containers to isolate different applications handling sensitive customer data, preventing cross-contamination and minimizing the risk of data breaches. A software development company could use virtual machine containers to create isolated testing environments, ensuring that test code does not interfere with the production environment. Virtual machine containers offer a powerful tool for streamlining operations and enhancing security in a variety of scenarios, making them an increasingly attractive option for organizations looking to optimize their IT infrastructure. The lightweight nature of the virtual machine container makes it an optimal solution.
Kata Containers in Practice: A Case Study
Kata Containers represent a practical implementation of virtual machine container technology, offering a compelling blend of the speed of containers and the security of virtual machines. This approach addresses a growing need for secure and isolated container environments, particularly in multi-tenant cloud infrastructures. Kata Containers leverage lightweight virtual machines to encapsulate individual containers, providing a strong isolation boundary. Unlike traditional containers that share the host OS kernel, each Kata Container runs within its own micro-kernel, enhancing security and preventing potential cross-container contamination. This makes them a suitable choice for running untrusted code or workloads that require stringent security measures. The use of virtual machine container technology like Kata Container is gaining momentum.
The architecture of Kata Containers involves several key components. A lightweight virtual machine monitor (VMM), such as QEMU or Firecracker, manages the virtual machine. A minimal guest operating system, often based on Linux, runs inside the VM. The container runtime interface (CRI), typically containerd or CRI-O, interacts with the Kata runtime to launch and manage containers within the virtual machine. This architecture allows for a high degree of isolation without sacrificing the performance benefits associated with containerization. Features like memory deduplication and optimized I/O paths contribute to efficient resource utilization. Deploying applications using Kata Containers involves a few straightforward steps. First, the Kata runtime needs to be installed and configured on the host system. Next, the container image is pulled from a registry and launched using a CRI-compatible tool. The Kata runtime then creates a new virtual machine for the container, providing the necessary isolation.
Let’s consider a simplified deployment example. Assume you have a Kubernetes cluster and want to deploy an application using Kata Containers. You would first ensure that the Kata runtime is configured as a runtime class within your Kubernetes cluster. Then, when deploying your application, you would specify the Kata runtime class in the pod’s specification. Kubernetes will then use the Kata runtime to create a virtual machine container for your application. Managing applications within Kata Containers is similar to managing standard containers. You can use familiar tools like `kubectl` to monitor, scale, and update your deployments. However, it’s essential to consider the resource overhead associated with running virtual machines. While Kata Containers are designed to be lightweight, they still consume more resources than traditional containers. Careful monitoring and resource allocation are crucial for optimal performance. Kata Containers showcases the value of virtual machine container technology in modern application deployments.
Evaluating Performance: Benchmarking Virtualized Container Solutions
Factors influencing the performance of virtual machine containers are diverse and require careful consideration. Network latency, storage I/O, CPU overhead, and memory management all play significant roles. Benchmarking different virtual machine container solutions is crucial for identifying the optimal choice for specific workloads. The selection of appropriate benchmarking tools and methodologies is vital for obtaining accurate and reliable results. Understanding these elements is key to maximizing the efficiency of any virtual machine container deployment.
Key Performance Indicators (KPIs) to monitor include container startup time, application response time, CPU utilization, memory footprint, and network throughput. Container startup time reflects the efficiency of the container creation process. Application response time indicates the user experience within the containerized environment. CPU utilization and memory footprint demonstrate resource consumption. Network throughput assesses the communication speed between containers and the external network. Monitoring these KPIs provides insights into the overall performance and resource efficiency of virtual machine containers. Tools like Prometheus, Grafana, and cAdvisor can assist in monitoring and analyzing these metrics, offering a comprehensive view of the system’s behavior. Properly configured monitoring helps identify bottlenecks and areas for optimization within the virtual machine container infrastructure.
Optimizing the performance of virtual machine containers involves several strategies. Resource allocation should be carefully tuned to match the application’s needs, avoiding over-provisioning or under-provisioning. Using lightweight operating system images reduces the overall footprint of the virtual machine container. Implementing efficient networking configurations minimizes latency and maximizes throughput. Caching frequently accessed data can improve application response times. Regularly profiling the application helps identify performance bottlenecks within the code. Furthermore, employing techniques like CPU pinning and memory locking can improve resource utilization and reduce context switching overhead. Through these measures, the efficiency and responsiveness of virtual machine containers can be significantly enhanced. The goal is to strike a balance between isolation, security, and performance, ensuring that the virtual machine container environment operates optimally. Therefore, virtual machine container solutions require continuous monitoring and fine-tuning to adapt to changing application demands and workload characteristics.
The Future of Lightweight Virtualization
The landscape of containerization is continuously evolving, and virtual machine containers are poised to play a significant role in its future. Several emerging trends and potential applications suggest a promising trajectory for this technology. The increasing adoption of cloud-native architectures is creating a demand for more secure and isolated container solutions, a need that virtual machine containers directly address. Their inherent isolation capabilities make them ideal for running security-sensitive workloads in multi-tenant cloud environments. The rise of confidential computing, where data is encrypted in use, further amplifies the importance of strong isolation. Virtual machine containers can provide the necessary hardware-level isolation to protect sensitive data during processing.
One significant trend is the convergence of containerization and virtualization technologies. Innovations are blurring the lines between traditional virtual machines and containers, leading to more flexible and efficient deployment options. We can anticipate further optimization in areas like resource utilization and performance overhead, making virtual machine containers even more appealing for a wider range of applications. Serverless computing is another area where virtual machine containers could have a substantial impact. The ability to quickly and securely spin up isolated environments is crucial for serverless functions, and virtual machine container technology provides a viable solution. As the demand for edge computing grows, lightweight virtualization solutions become increasingly important. Virtual machine containers are well-suited for deployment in resource-constrained edge environments, enabling secure and efficient execution of applications closer to the data source. This will drive further innovation in the virtual machine container space, with a focus on reducing footprint and improving performance on edge devices. The development of new container runtimes and orchestration tools is also shaping the future of virtual machine containers. Projects like Kata Containers are constantly evolving, incorporating new features and improvements to enhance security, performance, and usability. As the technology matures, we can expect to see wider adoption of virtual machine container solutions across various industries.
Ultimately, the future of virtual machine container technology hinges on its ability to provide a compelling balance between security, performance, and resource efficiency. The ongoing efforts to optimize these aspects will determine the extent to which virtual machine containers become a mainstream containerization solution. The virtual machine container offers a compelling proposition for organizations seeking a more secure and isolated container environment. As the cloud-native landscape continues to evolve, the virtual machine container is expected to maintain relevance and contribute to the ongoing innovation in the containerization ecosystem. The focus will be on developing tools and platforms that simplify the deployment and management of virtual machine container applications, making them accessible to a wider audience. The virtual machine container’s secure isolation will be key for highly regulated industries.

.png?width=8328&height=3322&name=Virtual%20machine%20containerization%20(1).png)