Understanding Terraform Providers and the Importance of Updates
Terraform providers are plugins that allow Terraform to interact with various cloud platforms and services. They act as the bridge between your Terraform configuration and the infrastructure you’re managing. Keeping providers updated is critical for several reasons. Outdated providers may contain bugs that can lead to infrastructure misconfigurations or failures. Newer provider versions often include important security patches, mitigating potential vulnerabilities in your infrastructure. Furthermore, updates frequently introduce new features and performance enhancements, allowing for more efficient and robust infrastructure management. Regularly performing a terraform update provider ensures you benefit from these improvements. The `terraform init` command downloads and installs providers, while `terraform update` applies your infrastructure configuration using the installed providers. Understanding these commands is the foundation for effective provider management. A well-maintained provider configuration is crucial for a stable infrastructure. Regularly performing a terraform update provider is a best practice.
Using outdated providers poses significant security risks. These risks include vulnerabilities that malicious actors could exploit. Regular updates mitigate these threats by incorporating the latest security patches. Delaying updates increases the likelihood of falling victim to attacks. Therefore, a crucial aspect of securing your infrastructure is staying current with provider updates. A proactive approach to terraform update provider ensures your infrastructure remains secure and up-to-date. Failing to update exposes your infrastructure to unnecessary risks. Regularly updating providers is a fundamental aspect of responsible infrastructure management. Neglecting updates increases vulnerabilities, thus jeopardizing security and stability.
The benefits of using the latest provider versions extend beyond security. New features often simplify complex tasks or introduce innovative capabilities. Performance improvements can streamline your infrastructure workflows. For example, updated providers might optimize resource creation, leading to faster deployments and reduced costs. Regularly executing a terraform update provider guarantees access to the most current features and enhancements. This ensures that your infrastructure management is efficient and adaptable to changing requirements. Regular updates are key to maintaining a performant and secure infrastructure, utilizing the latest functionalities.
How to Efficiently Update Your Terraform Providers
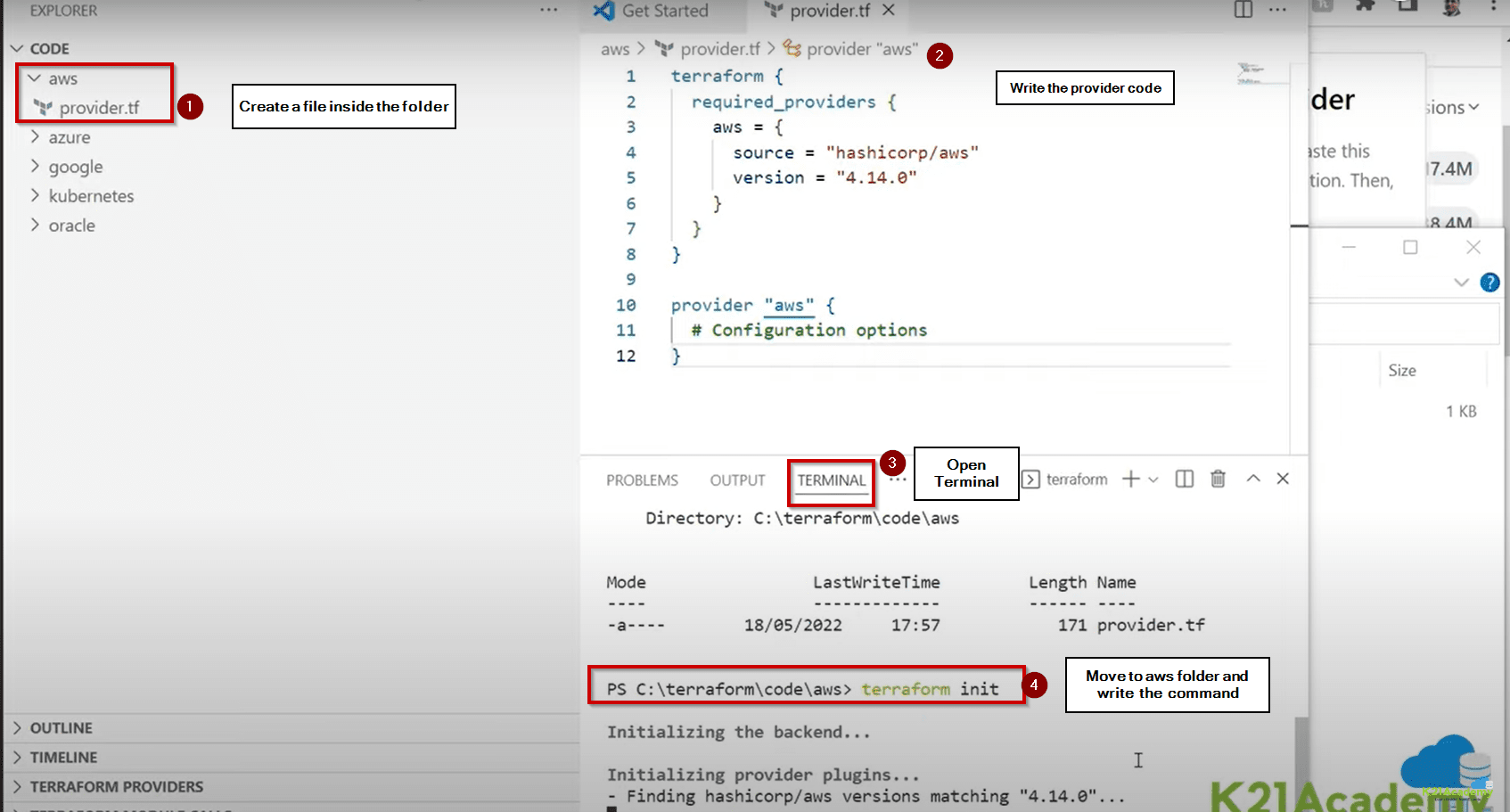
Updating Terraform providers ensures access to the latest features, bug fixes, and performance improvements. To check for updates, use the command `terraform init`. This command downloads and initializes the necessary providers, indicating available updates. The output clearly shows which providers need updating. Alternatively, `terraform plan` can also highlight outdated providers before applying changes, providing a preview of the update process. This allows for a review of changes before executing a terraform update provider command.
Updating providers can be done individually or all at once. To update a single provider, specify the provider name in the `terraform init` command. For instance, to update the AWS provider, one might use `terraform init -upgrade=aws`. To update all providers, simply run `terraform init -upgrade`. This command will download and install the latest versions of all required providers. It’s important to note that updating providers may involve resolving dependency conflicts. Terraform will often try to resolve these automatically. However, manual intervention might be needed in complex scenarios. Carefully review any conflict messages generated by `terraform init` to understand and address them. Successfully executing a terraform update provider ensures your infrastructure is current.
During the update process, be mindful of potential breaking changes introduced in newer provider versions. Always review the release notes for any provider you update. These notes often highlight significant changes that may require modifications to your Terraform configuration. Testing updates in a non-production environment is crucial before applying them to production systems. This step minimizes risks and allows for identifying and addressing any unforeseen issues early in the process. This approach significantly reduces the chance of disrupting production infrastructure. Before implementing a terraform update provider, a thorough testing procedure should always be followed.
Managing Provider Versions for Multiple Environments
Maintaining consistent Terraform provider versions across different environments—development, staging, and production—is crucial for preventing unexpected behavior and ensuring smooth deployments. Inconsistencies can lead to infrastructure discrepancies and complicate troubleshooting. A robust strategy for managing provider versions minimizes these risks. Using different provider versions in various environments introduces potential compatibility issues and complicates the terraform update provider process. To mitigate this, one effective technique involves using a centralized configuration file, such as `terraform.tfvars`, to define provider versions. This file allows for easy modification and distribution of provider versions across environments without altering the core Terraform configuration files. This approach streamlines the terraform update provider process and enhances maintainability. The `terraform.tfvars` file can specify provider versions based on environment, promoting consistency and simplifying deployments. For instance, a development environment might use the latest version for faster iteration, while production may stick to a stable, well-tested release.
Workspace management in Terraform offers another powerful approach to managing provider versions across environments. Terraform workspaces allow isolating different infrastructure configurations within a single project. Each workspace can be configured to use specific provider versions, completely separating the environments. This isolation prevents conflicts between environments and ensures that terraform update provider operations within one workspace don’t affect others. Switching between workspaces is simple, enabling seamless transitions between environments for testing and deployment purposes. This granular control over provider versions enhances consistency and simplifies managing complex infrastructure deployments. Careful planning and clear labeling of workspaces are key to successfully utilizing this method to manage your terraform update provider.
Implementing a version control system like Git for your Terraform code is essential for tracking changes to provider versions and enabling easy rollback if issues arise. This is critical for a smooth terraform update provider process. Version control allows tracking who made what changes and when, enabling a complete audit trail. This history allows for quick identification of the source of any issues introduced by a provider update. Combining version control with a clear naming convention for environments and provider versions will maintain an organized and manageable system for managing your infrastructure and conducting the terraform update provider process. Regularly reviewing and updating the provider versions in a controlled manner minimizes disruptions and ensures that security updates and new features are seamlessly integrated into your infrastructure. This combined approach of using `terraform.tfvars`, workspaces, and version control ensures a reliable and streamlined process for managing provider versions and executing terraform update provider efficiently across diverse environments.
Troubleshooting Common Terraform Update Provider Issues
During a terraform update provider process, various issues might arise. Dependency conflicts are a common problem. These occur when different providers require incompatible versions of other providers. To resolve this, carefully examine the error messages. They usually pinpoint the conflicting dependencies. Consider using version constraints in the `required_providers` block to explicitly specify compatible versions. This helps avoid conflicts during the terraform update provider operation. A well-defined `required_providers` block is key to managing dependencies effectively.
Breaking changes introduced in new provider versions can also disrupt the workflow. Always review the release notes for any provider you intend to update. These notes often highlight breaking changes and provide guidance on migration. Thorough testing in a non-production environment before deploying to production minimizes the risk of disruption caused by breaking changes during a terraform update provider. A well-defined testing process is essential for managing the terraform update provider safely.
Errors during the `terraform apply` process after updating providers often stem from configuration inconsistencies. Carefully review your Terraform configuration files for any syntax errors or outdated resource definitions. The error messages usually guide you to the problematic section. Ensure that your configuration is compatible with the newly updated provider versions. If you encounter persistent issues, check the provider’s documentation for any relevant troubleshooting advice. Debugging involves meticulously examining the error messages and using the documentation effectively. Remember that successful terraform update provider hinges on careful planning and execution.
Leveraging Terraform’s required_providers Block for Version Control
Effectively managing Terraform provider versions is crucial for maintaining a stable and secure infrastructure. The required_providers block offers a powerful mechanism for explicitly defining and controlling these versions within your Terraform configuration. By specifying version constraints, you prevent unexpected updates and ensure compatibility across your infrastructure. This proactive approach to managing provider versions simplifies the terraform update provider process and reduces the risk of disruptions.
Defining provider versions within the required_providers block allows for granular control. You can specify exact versions, version ranges (e.g., “~> 2.0”), or even use the latest version with a constraint (e.g., “>= 2.0”). This approach eliminates the guesswork involved in implicit provider updates during terraform init. The specified versions are enforced, making the entire process of terraform update provider more predictable and manageable. When you run terraform init, Terraform will download and use the exact provider version you specified, preventing accidental use of incompatible or insecure versions. This helps avoid issues that might arise from unexpected changes introduced in later versions. Properly managing your terraform update provider process through this method promotes consistency and reliability across your infrastructure.
Consider a scenario where a new provider version introduces breaking changes. If you haven’t explicitly defined your provider version using required_providers, you might encounter unexpected failures during a terraform update provider. However, by pinning your provider version, you ensure compatibility until you’re ready to upgrade. This allows for controlled updates. You can thoroughly test the newer provider version in a separate environment before implementing it in production. This measured approach minimizes the risk of disruptions and maximizes the stability of your infrastructure. Using required_providers provides a robust approach to terraform update provider management, ensuring a smooth and reliable update process for your Terraform configurations.
Best Practices for Provider Update Management
Incorporating regular terraform update provider checks into your workflow is crucial for maintaining a secure and efficient infrastructure. Establish a schedule for these checks, perhaps weekly or bi-weekly, depending on your project’s needs. This proactive approach helps identify potential issues early, minimizing disruption. Always test provider updates thoroughly in a non-production environment before deploying them to production systems. This allows you to validate the changes and identify any unexpected behavior before impacting live systems. This mitigates risk and ensures a smooth transition. Document all provider updates, including versions and any associated changes. Detailed records are vital for troubleshooting and auditing purposes, aiding in future maintenance and updates.
Version control systems play a critical role in managing terraform update provider versions. By tracking changes to your Terraform configurations, including provider versions, you create a clear audit trail. This enables easy rollback to previous versions if necessary and simplifies collaboration among team members. Consider using a branching strategy to manage different versions concurrently. For instance, a `develop` branch for testing updates and a `main` branch for production deployments allows for a controlled rollout. Automated testing, integrated into your CI/CD pipeline, can automate the process of testing provider updates. This streamlines the process, reducing manual effort and increasing the frequency of updates, leading to a more stable and secure infrastructure.
Employing a robust change management process for terraform update provider actions is essential for managing updates effectively in larger teams. This process should define roles and responsibilities, approval workflows, and communication protocols. Clear communication ensures that all stakeholders are informed of upcoming updates and their potential impact. It also helps in mitigating any potential issues arising from these updates. Prioritize using the `required_providers` block in your Terraform configurations to specify explicit provider versions. This approach enhances control and predictability, reducing the risk of unexpected updates. Regularly review and update your dependency management strategy to address potential conflicts and ensure compatibility across your infrastructure. This proactive approach is essential for maintaining a secure and reliable infrastructure that scales effectively.
Working with Provider Plugins and their Updates
Terraform utilizes provider plugins to interact with various cloud platforms and infrastructure services. These plugins are essentially self-contained executables that handle the specifics of interacting with a given API. Understanding how these plugins are updated is crucial for effective terraform update provider management. Each provider plugin is downloaded and managed independently, allowing for granular control over versions. The `terraform init` command downloads and installs the necessary plugins based on the requirements specified in your configuration files. Regularly checking for updates ensures access to bug fixes, performance improvements, and new features offered by the provider. A key aspect of managing these plugins is ensuring compatibility between the plugin version, the Terraform version, and the configuration files. Incompatibilities can lead to unexpected behavior or failures during a terraform update provider operation.
The update process for provider plugins is intrinsically linked to the `terraform init` command. When you run `terraform init`, Terraform checks for updates for all configured providers. It then downloads and installs the latest compatible versions. To explicitly specify a provider version, you should use the `required_providers` block in your main Terraform configuration file. This approach allows for precise version control and prevents unintended updates that might introduce breaking changes. For example, specifying `~> 3.0` indicates a version within the 3.x series, offering flexibility while maintaining a degree of control. When managing multiple environments, consistency in provider versions across all environments is recommended. Using a `terraform.tfvars` file to manage provider configurations can help maintain this consistency and simplify the terraform update provider process. Using this approach reduces the risk of inconsistencies and simplifies managing infrastructure across environments.
Addressing potential conflicts during plugin updates requires careful consideration. Dependency conflicts, where two providers rely on incompatible versions of the same underlying library, are possible. These situations can be resolved by carefully inspecting the provider dependency tree, potentially adjusting version constraints in your `required_providers` blocks, or searching for solutions on the provider’s documentation or community forums. Always prioritize testing any terraform update provider in a non-production environment before deploying to production systems. This mitigates the risk of introducing unexpected issues into your live infrastructure. Remember, proactive management of provider plugins, along with careful version control, is essential for maintaining a stable and secure infrastructure. Regularly updating providers through the proper channels will ensure your Terraform configurations remain current and compatible, ultimately simplifying future terraform update provider operations.
Advanced Techniques for Managing Complex Terraform Provider Dependencies
Managing terraform update provider in large-scale infrastructure projects presents unique challenges. Complex dependencies between providers can make updates difficult to manage. Modules help organize Terraform code into reusable components. This improves organization and simplifies updates. By updating a module, you update all using infrastructure. This approach reduces the risk of errors associated with manual updates.
Remote state management offers a centralized approach to infrastructure configuration. It simplifies terraform update provider across multiple environments. Terraform Cloud or similar tools provide robust features for managing remote state. They enable collaboration and version control. Automated update processes are essential for large projects. Continuous Integration/Continuous Delivery (CI/CD) pipelines can automate provider updates. Testing thoroughly in a staging environment before production deployment is critical. Automated testing confirms the updates work correctly. This prevents costly errors in production.
For complex scenarios, consider using a configuration management tool. This helps manage provider versions and dependencies consistently. Tools like Ansible or Puppet can manage provider versions. They ensure consistency across environments. This helps to streamline the terraform update provider process significantly. Regularly reviewing and updating your dependency management strategy is essential. This ensures your infrastructure remains secure and efficient. Adapting these strategies ensures successful and efficient terraform update provider operations, even within intricate infrastructure setups. Careful planning minimizes disruption during updates.