Understanding Terraform Workflow: From Configuration to Execution
Terraform, a leading Infrastructure as Code (IaC) tool, empowers users to define and manage infrastructure through declarative configuration files. The core purpose of Terraform is to streamline and automate the provisioning and management of infrastructure resources across various cloud providers and on-premises environments. The typical Terraform workflow consists of three essential stages: write, plan, and apply. This workflow describes the process of defining the desired infrastructure state, previewing the changes, and then implementing those changes. This section introduces the critical execution phase, often associated with the concept of a “terraform run command,” within this established workflow. Understanding the execution phase is paramount to effectively utilizing Terraform for infrastructure management. While there isn’t a direct “terraform run command,” the execution phase encompasses commands like `terraform init`, `terraform plan`, and `terraform apply`, working together to deploy and manage your infrastructure.
The execution phase is where the defined configuration comes to life. It involves initializing the Terraform working directory, planning the infrastructure changes, and applying those changes to achieve the desired state. The series of commands effectively simulate the purpose of a “terraform run command”. Proper execution ensures infrastructure is provisioned correctly and consistently. Initializing the environment with `terraform init` prepares the working directory. Planning with `terraform plan` generates a preview of the changes to be made. Applying with `terraform apply` then enacts those changes. Understanding each step is crucial for managing infrastructure effectively and preventing unexpected issues. This approach provides a controlled and predictable way to manage infrastructure, with each step playing a crucial role.
In essence, the “terraform run command” concept is realized through the strategic execution of a sequence of Terraform commands. Each command contributes to the overall goal of provisioning and managing infrastructure. The execution phase confirms that the infrastructure matches the configuration defined in the Terraform files. By understanding the individual roles of `terraform init`, `terraform plan`, and `terraform apply`, users can grasp the importance of the execution phase. Terraform eliminates manual processes and reduces the risk of human error. Mastering Terraform execution is essential for infrastructure automation. Terraform’s “run” process assures infrastructure stability and simplifies management, solidifying its position as a vital IaC tool for modern cloud environments.
How to Initiate Terraform Deployment: A Step-by-Step Execution Guide
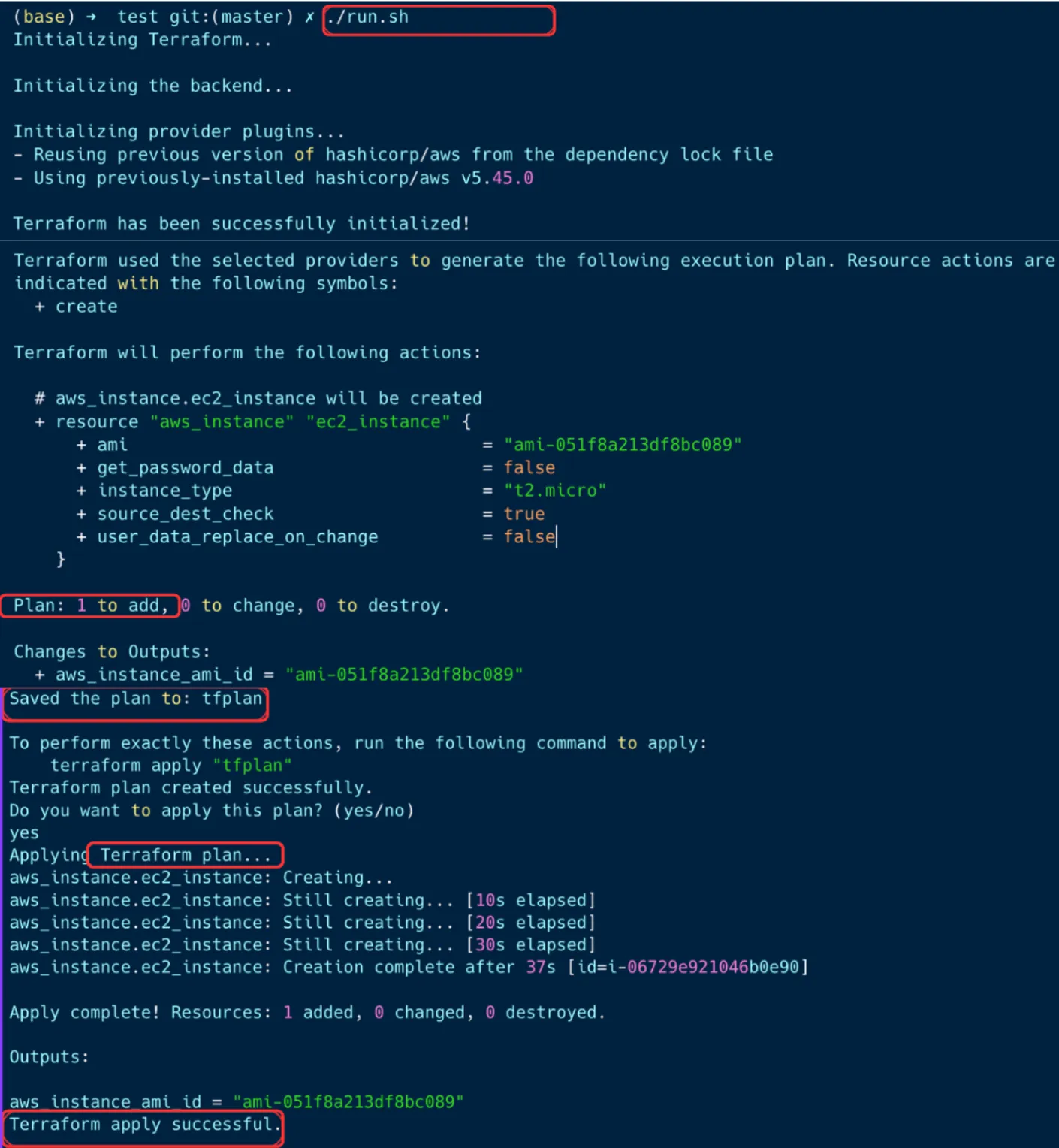
This section details the precise commands necessary to initiate a Terraform deployment, acting as a practical guide to the execution phase. The standard workflow begins with initializing the Terraform environment, followed by planning the changes, and concluding with applying those changes. Understanding the correct sequence is crucial for a successful infrastructure deployment. The initial step involves the terraform init command, which prepares the working directory for use with Terraform. This command performs several essential tasks, including downloading the necessary provider plugins and setting up the backend for state management. Without running terraform init, subsequent commands will fail. Think of terraform init as the essential preparation step before using any other terraform run command.
Following initialization, the next step is to create a plan using the terraform plan command. This command allows you to preview the changes Terraform will make to your infrastructure. It compares the current state of your infrastructure, as recorded in the Terraform state file, with the desired state defined in your configuration files. The output of terraform plan shows which resources will be created, modified, or destroyed. This is a critical step for understanding the impact of your changes before applying them. Reviewing the plan allows you to catch any potential errors or unexpected modifications. The terraform plan command is a read-only operation; it doesn’t make any actual changes to your infrastructure. It’s a safe way to understand what the terraform run command terraform apply will do.
Finally, after reviewing the plan and confirming that the proposed changes are correct, you can apply the configuration using the terraform apply command. This command executes the changes described in the plan, provisioning or modifying infrastructure resources as needed. Terraform prompts for confirmation before applying the changes, giving you a final opportunity to review the plan and ensure that you’re comfortable proceeding. Once you confirm, Terraform will execute the changes and update the state file to reflect the new state of your infrastructure. The terraform apply command is the core of the terraform run command process. It brings your infrastructure to the desired state defined in your Terraform configuration. It’s important to note that running terraform apply will modify resources. The correct order of execution of these commands is critical to the Terraform workflow. terraform init prepares, terraform plan previews, and terraform apply executes.
Planning Your Infrastructure Changes: Previewing with Terraform
The `terraform plan` command is a crucial step in the Terraform workflow, acting as a dry run to preview the changes Terraform intends to make to your infrastructure. It allows you to understand exactly what will be created, modified, or destroyed before any actual actions are taken. This is essential for risk mitigation and preventing unintended consequences. Think of `terraform plan` as a safety net, catching potential errors before they impact your live environment. This ensures a controlled and predictable deployment process. Using the `terraform run command` equivalent, `terraform plan`, helps prevent unwanted modifications to your infrastructure. Before executing any changes, examining the `terraform plan` output allows for a comprehensive overview of the projected actions, aiding in informed decision-making and averting potential disruptions.
The output of `terraform plan` provides a detailed report of the proposed changes. It will list each resource that Terraform intends to modify, specifying the attributes that will be changed and their new values. Pay close attention to resources marked for destruction, as this could indicate a configuration error or an unintended consequence of your changes. Also, review any modifications to critical infrastructure components, such as databases or network configurations. By carefully analyzing the `terraform plan` output, you can identify potential issues like misconfigured resources, incorrect dependencies, or security vulnerabilities before they are implemented. Regularly utilizing `terraform plan` as part of your workflow helps ensure your deployments are safe, reliable, and aligned with your intended infrastructure configuration. Terraform plan uses the concept of `terraform run command` to simulate the environment before the user applies for real.
Best practices dictate that you should always review the output of `terraform plan` before running `terraform apply`. Treat the plan as a contract between you and Terraform, outlining the exact changes that will be made. Encourage team collaboration by sharing the plan output with colleagues for review, especially when dealing with complex infrastructure changes. For added security, consider integrating automated plan analysis tools into your CI/CD pipeline to automatically detect potential issues and enforce organizational policies. Remember, a well-reviewed `terraform plan` is the best defense against unexpected infrastructure changes. Properly utilizing the `terraform run command` through careful examination of the `terraform plan` output will empower you to confidently and safely manage your infrastructure with Terraform.
Applying Configuration Changes: Executing Terraform with Confidence
The `terraform apply` command is the core of the Terraform workflow, responsible for provisioning and updating infrastructure resources as defined in your configuration files. It’s the point where the desired state of your infrastructure becomes a reality. Before executing `terraform apply`, a careful review of the execution plan generated by `terraform plan` is paramount. This dry run outlines the exact changes Terraform will make, including resource creation, modification, and deletion. Understanding the plan helps prevent unintended consequences and ensures that the proposed changes align with your expectations. Reviewing the plan is a critical step to validate that the configuration behaves as expected, catching potential errors or misconfigurations before they impact your infrastructure.
Executing the `terraform apply` command without a plan review can lead to unexpected outcomes, potentially disrupting existing services or creating security vulnerabilities. Therefore, treat the plan as a blueprint for your infrastructure changes. Analyze it meticulously, paying close attention to resource attributes, dependencies, and any warnings or errors reported. Once you are confident in the plan’s accuracy, you can proceed with applying the changes. The `terraform run command` equivalent, `terraform apply`, is the final step to create or modify your infrastructure.
In non-production environments, the `-auto-approve` flag can streamline deployments by bypassing the manual approval prompt. This is particularly useful in CI/CD pipelines where automated infrastructure provisioning is desired. However, the use of `-auto-approve` in production environments is strongly discouraged. The manual approval step provides a crucial safety net, allowing for a final check of the plan before any irreversible changes are applied. While the `terraform run command` is technically absent, the `terraform apply` command fulfills the execution stage. Bypassing this step in production increases the risk of deploying faulty configurations, leading to downtime, data loss, or security breaches. Weigh the convenience of automation against the potential consequences before using `-auto-approve` in any environment. The `terraform run command` ideology is embodied in the `terraform apply` execution.
Terraform Apply -Auto Approve: Streamlining Deployments
The `-auto-approve` flag is a powerful option available with the `terraform apply` command. It bypasses the manual approval step, automatically applying the changes defined in your Terraform configuration. While this can significantly speed up deployments, particularly in certain environments, understanding its appropriate use and potential risks is crucial. The `terraform run command` equivalent, when using `-auto-approve`, executes without human intervention. Use cases dictate whether automating is beneficial or detrimental.
The primary benefit of `-auto-approve` lies in automating infrastructure deployments. This is particularly valuable in Continuous Integration/Continuous Delivery (CI/CD) pipelines. In these environments, automated testing and deployment are common. The `-auto-approve` flag allows Terraform to seamlessly integrate into the pipeline. This eliminates the need for manual intervention at the application stage. Development environments also benefit from `-auto-approve`. Rapid iteration and frequent deployments are common during development. Using `-auto-approve` allows developers to quickly test and deploy changes without waiting for manual approval. However, it is imperative that the `terraform run command` and its automated execution are thoroughly tested in non-production settings before implementation.
Despite its advantages, using `-auto-approve` in production environments is generally discouraged. The manual approval step provides a crucial safety net. It allows engineers to carefully review the planned changes before they are applied. This review can catch potential errors or unintended consequences before they impact the live environment. Bypassing this step introduces significant risk. A misconfigured Terraform file or an unforeseen interaction between resources can lead to outages or data loss. While the `terraform run command` can streamline operations, the potential for errors in production outweighs the benefits of automation in many cases. The decision to use `-auto-approve` should be made carefully, considering the specific risks and benefits in each environment. A robust testing and validation process should always be in place, regardless of whether `-auto-approve` is used. Employing comprehensive monitoring and alerting systems will also help mitigate potential issues arising from automated deployments initiated through a `terraform run command` with the `-auto-approve` flag.
Troubleshooting Common Terraform Execution Errors
Encountering errors during Terraform execution is a common experience, even for seasoned infrastructure professionals. The key to resolving these issues lies in understanding the error messages and having a systematic approach to troubleshooting. One frequently seen problem is provider configuration failure. This often stems from incorrect credentials, missing API keys, or an improperly configured provider block in your Terraform code. Always verify your provider settings and ensure that the necessary authentication details are in place. Sometimes, running the terraform run command seems to fail because of this configuration error, and the error message will clearly point to the specific provider and the missing or invalid credential.
Another prevalent category of errors involves syntax and configuration issues within your Terraform files. These can range from simple typos to more complex problems like incorrect resource attributes or malformed expressions. Carefully examine the error messages, as they typically pinpoint the exact line and file where the error occurs. Use a linter or a Terraform-aware IDE to catch syntax errors early on. Dependency conflicts can also halt Terraform execution. These arise when resources depend on each other in a way that creates a circular dependency or when Terraform is unable to determine the correct order in which to create or modify resources. Review your resource dependencies and use the depends_on attribute to explicitly define the order of execution where necessary. Understanding how the terraform run command resolves dependencies is crucial in preventing these conflicts. Often, the error messages related to dependency issues will guide you towards the problematic resources. Also, confirm that the version of Terraform you are using is compatible with the providers and modules you are using.
Furthermore, issues with Terraform state can lead to execution errors. State corruption or inconsistencies can cause Terraform to misinterpret the current state of your infrastructure and attempt to make incorrect changes. If you suspect state corruption, consider using the terraform state pull and terraform state push commands to refresh your local state file from the remote backend (if using one). If the problem persists, you might need to manually edit the state file (with extreme caution) to correct any discrepancies. When troubleshooting, remember to run terraform init, terraform plan, and then terraform apply again, following the proper workflow of a terraform run command. By methodically addressing each potential issue, you can successfully resolve most Terraform execution errors and ensure the smooth deployment of your infrastructure. Remember to scrutinize the output of the terraform run command for clues, and consult the Terraform documentation or community forums for assistance with more complex problems.
Best Practices for Efficient Terraform Execution
Optimizing Terraform execution is crucial for speed and reliability. Several techniques can significantly improve the efficiency of your infrastructure deployments. One key aspect is leveraging infrastructure as code modules. Modularization promotes code reuse and reduces redundancy, leading to faster deployments and easier maintenance. When you define reusable modules, you avoid duplicating configurations across different environments. This ensures consistency and reduces the risk of errors. Using a well-structured module library accelerates the provisioning process and simplifies updates. To improve the speed and reliability of your “terraform run command” execution, consider using specialized platforms.
Terraform Cloud and Terraform Enterprise offer remote state management and execution capabilities, streamlining the “terraform run command” workflow. Remote state storage ensures consistency and facilitates collaboration among team members. State locking prevents conflicts when multiple users are working on the same infrastructure. These platforms often include features like automated plan and apply workflows, role-based access control, and audit logging. These features add security and compliance to the deployment process. By centralizing state management and execution, you reduce the risk of inconsistencies and improve the overall reliability of your Terraform deployments. Moreover, adopting a consistent naming convention and tagging strategy can enhance the organization and manageability of your infrastructure.
Another factor contributing to efficient “terraform run command” execution is optimizing provider configurations. Ensure that you are using the latest versions of providers and that they are configured correctly. Overly verbose or poorly configured providers can slow down the planning and application phases. Regularly review and update your provider configurations to take advantage of performance improvements and bug fixes. Parallelizing resource creation is another optimization technique. Terraform can create multiple resources concurrently, reducing the overall deployment time. Use the `depends_on` attribute to manage dependencies between resources. This ensures that resources are created in the correct order. Using input variables effectively simplifies configuration and promotes code reuse. When you parameterize your configurations, you can easily adapt them to different environments without modifying the core code. By following these best practices, you can significantly improve the efficiency and reliability of your “terraform run command” executions, resulting in faster deployments and reduced operational overhead.
Managing Terraform State: Ensuring Consistency and Collaboration
Terraform state is crucial for managing infrastructure effectively. It acts as a single source of truth, mapping resources defined in your configuration to the real-world infrastructure. Proper management of this state file is essential for consistency and successful collaboration when multiple team members are involved in managing the same infrastructure. Without a well-managed state, you may encounter issues like resource conflicts, drift, and unexpected changes when running the terraform run command.
Several options exist for storing Terraform state. The default option is local storage, where the state file is saved on your machine. While suitable for individual experimentation, local storage is not recommended for team environments due to the risk of inconsistencies and data loss. A better practice is to use remote state storage. Remote state stores the Terraform state file in a centralized location, such as AWS S3, Azure Blob Storage, or HashiCorp’s Terraform Cloud. Remote storage facilitates collaboration, ensures data durability, and enables state locking, preventing concurrent modifications that could lead to corruption or inconsistencies when running the terraform run command. Choosing the right remote backend ensures the smooth operation of the terraform run command.
State locking is a critical feature for collaborative Terraform workflows. When a terraform run command is executed, Terraform acquires a lock on the state file, preventing other users or processes from making concurrent changes. This lock ensures that only one operation can modify the state at a time, avoiding conflicts and maintaining data integrity. Terraform Cloud and Terraform Enterprise provide built-in state locking mechanisms. For other remote backends, you may need to configure state locking manually. Tools like DynamoDB (for S3) can be used to implement state locking. A correctly configured state management system is vital for efficient team collaboration when running the terraform run command, ensuring consistency and preventing unintended infrastructure modifications. Proper management of Terraform state ensures consistent and predictable results when using any terraform run command.