Understanding Terraform Configuration Files
Terraform configuration files are the cornerstone of Infrastructure as Code (IaC), defining and managing infrastructure resources in a declarative manner. These files, typically written in HashiCorp Configuration Language (HCL), specify the desired state of your infrastructure, enabling Terraform to provision and manage resources across various cloud providers and services. A core strength of Terraform lies in its ability to translate these configurations into actionable plans, automating the deployment and management of complex infrastructure. Understanding the structure and syntax of these files is crucial for effectively using Terraform.
A Terraform configuration file is composed of several key blocks. The `terraform` block specifies Terraform settings, such as required providers and Terraform version constraints. The `provider` block configures the specific cloud provider or service that Terraform will interact with, like AWS, Azure, or Google Cloud Platform. This block includes authentication details and region settings. The `resource` block is the most fundamental, defining individual infrastructure components, such as virtual machines, networks, or databases. Each `resource` block includes attributes that specify the desired properties of the resource. Finally, the `data` block allows you to fetch information about existing infrastructure or external data sources, which can be used to dynamically configure your resources. A simple terraform plan example might involve creating a basic virtual machine, where the resource block defines the VM’s size, image, and network settings. The relationship between these blocks ensures that Terraform understands both its own configuration and the desired state of your infrastructure.
The syntax of HCL is designed to be both human-readable and machine-parseable. Blocks are defined using curly braces `{}`. Attributes within blocks are assigned values using the `=` operator. Lists and maps are used to represent collections of values. Comments can be added using `#` for single-line comments or `/* … */` for multi-line comments. When constructing a terraform plan example, focus on readability and clarity. Use meaningful names for resources and variables. Structure your configuration files logically, grouping related resources together. Proper formatting and commenting will greatly enhance the maintainability of your Terraform code. By understanding the basic structure and syntax of Terraform configuration files, you can start defining and managing your infrastructure with greater efficiency and control. Remember that a well-structured configuration is key to a successful terraform plan example and overall infrastructure management.
How to Create a Basic Terraform Configuration
Creating a basic Terraform configuration involves defining the desired infrastructure state in a structured file. This file, typically named `main.tf`, acts as the blueprint for Terraform to provision and manage resources. The first step is to declare the required providers. Providers are plugins that allow Terraform to interact with specific infrastructure platforms, such as AWS, Azure, or Google Cloud. Specifying the provider block ensures that Terraform knows which platform to target. For example, to deploy resources to AWS, you would include a `provider “aws”` block, configuring it with necessary credentials and region information. This initial setup is crucial for establishing the connection between Terraform and the target environment. The next step involves defining the resources you want to create.
A resource block declares a specific piece of infrastructure, such as a virtual machine, network, or storage bucket. Each resource block includes a type, a name, and a set of attributes that define its properties. Consider deploying an AWS EC2 instance. The resource block would start with `resource “aws_instance” “example”`, where “aws_instance” specifies the resource type and “example” is a unique name for this instance within the configuration. Within this block, you would specify attributes like the Amazon Machine Image (AMI), instance type, and any tags. The AMI determines the operating system and base software of the instance, while the instance type defines its compute capacity. Tags are metadata labels that help organize and identify resources. This simple example provides a foundation for using terraform plan example configurations. Remember to save the file with `.tf` extension.
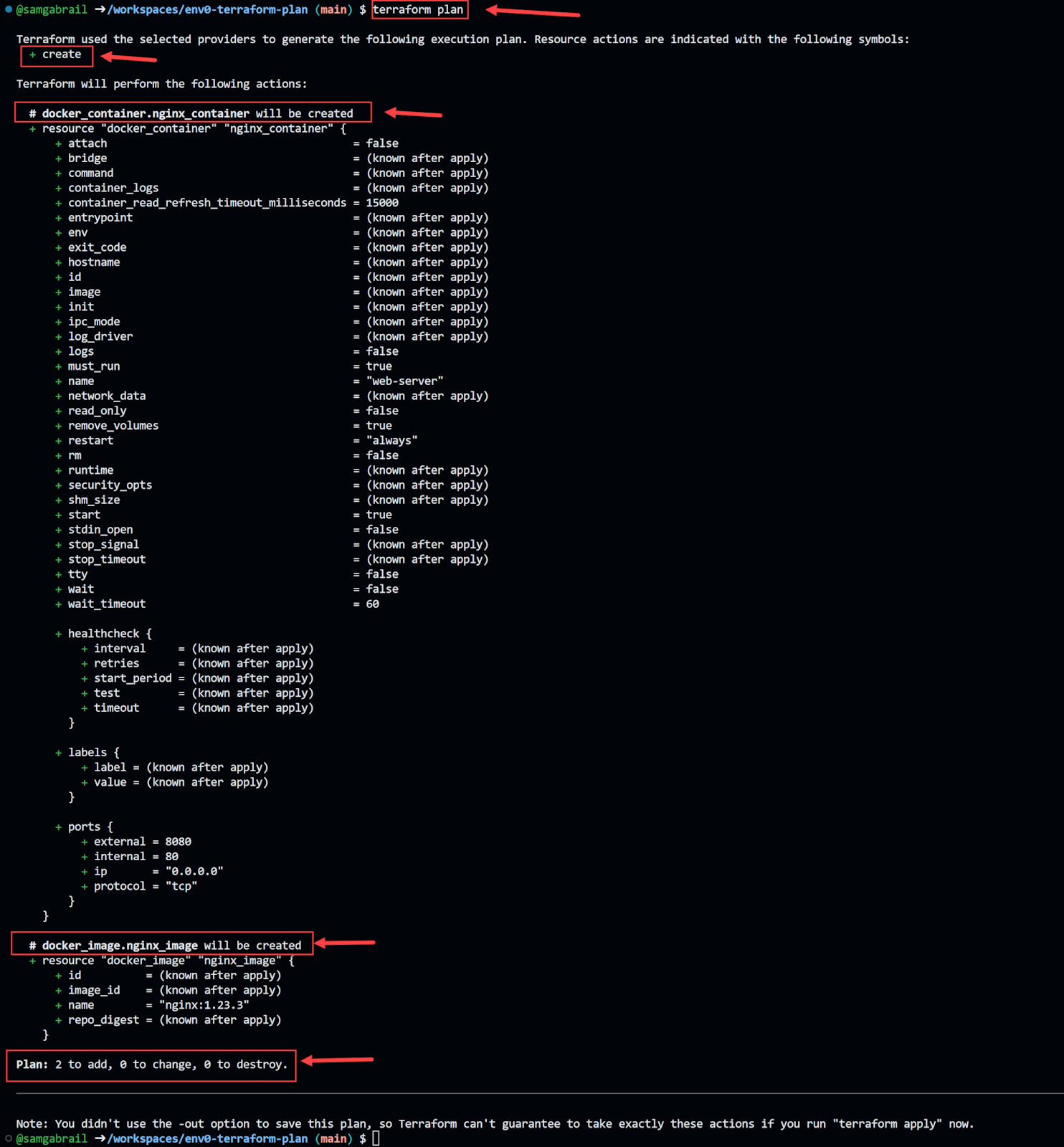
Before applying the configuration, it’s essential to initialize the Terraform working directory using the `terraform init` command. This command downloads the necessary provider plugins and sets up the environment. After initialization, you can use the `terraform plan` command to preview the changes that Terraform will make to your infrastructure. This command analyzes the configuration file and compares it to the current state of your infrastructure, generating a plan that outlines the resources to be created, modified, or destroyed. Reviewing the output of the `terraform plan example` command is crucial for ensuring that the changes align with your expectations. Once you are satisfied with the plan, you can apply the configuration using the `terraform apply` command. Terraform will then execute the plan, provisioning the resources defined in your configuration file. This process allows for consistent and repeatable infrastructure deployments.
Exploring a Simple Terraform Example: Deploying an AWS EC2 Instance
This section presents a practical Terraform example that demonstrates how to deploy an AWS EC2 instance. This example provides a foundational understanding of how Terraform configurations are structured and how they interact with cloud providers. The configuration detailed below defines a basic EC2 instance, specifying its Amazon Machine Image (AMI), instance type, and associated tags. Understanding this terraform plan example helps illustrate the core principles of Infrastructure as Code (IaC) using Terraform.
Below is a complete, runnable Terraform configuration for deploying an EC2 instance. The `resource` block defines the EC2 instance. The `ami` attribute specifies the operating system image to use. The `instance_type` attribute determines the hardware configuration of the instance. The `tags` attribute allows you to assign metadata to the instance, which is useful for organization and management. This terraform plan example showcases how Terraform translates code into real-world infrastructure. Before applying this configuration, it is crucial to run `terraform init` to initialize the Terraform working directory and download the necessary AWS provider plugin.
Analyzing Terraform State and its Significance
Terraform state is crucial for managing infrastructure effectively. It acts as a record of the resources Terraform manages. This record is stored in a state file. The state file maps resources defined in your configuration to real-world infrastructure objects. Without a state file, Terraform would not know what resources it manages or how to update them. The state file is essential for Terraform to function correctly. Understanding its role is key to using Terraform effectively.
Terraform uses the state file to determine the current state of your infrastructure. When you run `terraform plan`, Terraform compares your configuration with the state file. This comparison allows Terraform to identify any differences. These differences are then used to create a plan of changes. The `terraform plan example` demonstrates how Terraform interprets the state file to propose modifications. Without an accurate state file, Terraform may propose incorrect or unnecessary changes. Maintaining a consistent and up-to-date state file is paramount. Inconsistent state can lead to unexpected behavior and potential infrastructure damage. Therefore, it is vital to manage the state file carefully. A well-managed state file ensures that your infrastructure remains in sync with your Terraform configuration.
Several factors can lead to inconsistent state. Manual changes to infrastructure outside of Terraform can cause discrepancies. Multiple users modifying the same infrastructure without proper coordination can also lead to issues. To mitigate these risks, it’s recommended to use remote state storage. Remote state storage allows multiple users to access the same state file safely. Tools like Terraform Cloud or HashiCorp Consul provide remote state management capabilities. Regularly backing up your state file is another essential practice. Backups provide a safety net in case of accidental data loss or corruption. Furthermore, using state locking mechanisms can prevent concurrent modifications. State locking ensures that only one user can modify the state file at a time. When changes are complex, reviewing a `terraform plan example` output is important. This helps ensure you understand and agree with the changes Terraform will implement before applying them. By implementing these strategies, you can minimize the risks associated with inconsistent Terraform state and maintain a reliable infrastructure management workflow.
Executing Terraform Commands: Plan, Apply, and Destroy
The process of managing infrastructure with Terraform involves a series of essential commands. These commands facilitate the initialization, planning, application, and destruction of infrastructure resources. Understanding these commands is crucial for effectively utilizing Terraform.
The first command, `terraform init`, initializes the Terraform working directory. This command downloads the necessary provider plugins and sets up the backend for storing the Terraform state. Next, the `terraform plan` command is used to preview the changes that Terraform will make to the infrastructure. This is a critical step as it allows users to review the proposed changes before they are applied. The output of the `terraform plan` command shows the resources that will be created, modified, or destroyed. Analyzing the `terraform plan example` output is essential for ensuring that the planned changes align with the desired state. A well-understood `terraform plan example` will show you exactly what terraform will modify. The `terraform plan` command is a powerful tool for risk mitigation and proactive infrastructure management. The subsequent command, `terraform apply`, executes the changes defined in the Terraform configuration. This command provisions the resources as specified in the configuration files and updates the Terraform state. Finally, the `terraform destroy` command is used to deprovision all the resources managed by Terraform. This command effectively removes the infrastructure defined in the configuration.
Focusing on the `terraform plan` command, it’s vital to understand its purpose and how to interpret its output. The `terraform plan example` output displays a detailed list of actions that Terraform intends to perform. This includes creating new resources, modifying existing resources, or deleting resources. Each action is clearly identified, allowing users to understand the impact of the changes. The output also shows the attributes of each resource that will be modified, providing granular visibility into the planned changes. By carefully reviewing the `terraform plan example` output, users can identify potential issues or unintended consequences before applying the changes. This proactive approach helps to prevent errors and ensures that the infrastructure is provisioned as expected. Mastering the `terraform plan` command is a key skill for anyone working with Terraform. A detailed `terraform plan example` will include all resources that are to be modified, along with any dependencies.
Delving into Advanced Terraform Features: Variables and Outputs
Variables and outputs are pivotal for crafting flexible and reusable Terraform configurations. Variables enable parameterization, allowing configurations to adapt to different environments or scenarios without direct modification of the code. This promotes code reuse and reduces redundancy. Outputs, conversely, expose information about the provisioned infrastructure, making it accessible to other systems or Terraform configurations. This is particularly useful for chaining infrastructure deployments and automating post-provisioning tasks. Let’s explore how to effectively use these advanced features. Understanding a terraform plan example helps in appreciating the role of variables and outputs.
Variables are defined using the `variable` block, specifying a name, type, and optional default value. For instance, a variable for the AWS region can be defined as: variable "aws_region" { type = string default = "us-east-1" }. The `type` attribute constrains the allowed values, while the `default` attribute provides a fallback if no value is explicitly provided. To use a variable within a resource configuration, reference it using the syntax `var.variable_name`. This allows dynamic configuration of resources based on variable values. Utilizing a terraform plan example, we can see these variables in action, tailoring the infrastructure to specific requirements. A terraform plan example will highlight these dynamic aspects.
Outputs are defined using the `output` block, specifying a name and a value. The value can be any expression, including resource attributes or variable values. For example, to output the public IP address of an EC2 instance: output "instance_public_ip" { value = aws_instance.example.public_ip }. Outputs are displayed after a successful `terraform apply` and can be accessed using the `terraform output` command. Outputs facilitate integration with other systems and provide critical information about the deployed infrastructure. By examining a comprehensive terraform plan example, the interplay of variables and outputs becomes clear, showcasing how Terraform enables dynamic and informative infrastructure management. A well-structured terraform plan example demonstrates how to manage configurations effectively.
Best Practices for Writing Maintainable Terraform Configurations
Crafting maintainable Terraform configurations is crucial for long-term infrastructure management. Code readability is paramount. Use consistent formatting and clear, descriptive names for resources and variables. Well-formatted code enhances understanding and reduces the likelihood of errors. Comments are essential for explaining the purpose of different configuration sections, especially for complex logic or non-obvious choices. These practices will also help when writing a terraform plan example.
Modularity significantly improves maintainability. Terraform modules encapsulate reusable infrastructure components. Instead of repeating the same configuration across multiple environments or projects, create a module and reuse it. This promotes consistency and simplifies updates. Version control is indispensable. Use Git or a similar system to track changes to your Terraform code. This allows you to revert to previous versions if necessary and collaborate effectively with others. Tagging releases provides stable points for rolling back any change and helps when creating a terraform plan example. Automating infrastructure changes is very helpful.
To improve the configuration and create a good terraform plan example, consider using a linter. Linters like `terraform fmt` can automatically format your code according to a defined style guide. This ensures consistency across your entire codebase. Static analysis tools can also identify potential errors and security vulnerabilities before applying changes. Implementing a CI/CD pipeline for Terraform further enhances maintainability. Automate the process of testing and deploying infrastructure changes. This ensures that changes are thoroughly validated before being applied to production environments. Create a terraform plan example, test it and then apply the validated changes to your environment.
Troubleshooting Common Terraform Errors
Terraform, while powerful, can present challenges. Encountering errors is part of the infrastructure as code journey. This section provides guidance on diagnosing and resolving common Terraform issues. Addressing these errors efficiently is critical for maintaining smooth deployments. Mastering the interpretation of error messages is essential for effective troubleshooting.
One frequent issue involves provider configuration errors. These often arise from incorrect credentials or missing provider plugins. Ensure the provider block is correctly configured with the necessary authentication details. Syntax errors in Terraform configuration files are also common. Carefully review the code for typos, missing quotation marks, or incorrect block structures. Utilize a linter to catch these errors early. State management problems can lead to unpredictable behavior. When the Terraform state becomes inconsistent, it can cause issues. Remote state storage is recommended for collaborative environments to mitigate these problems. Analyzing a `terraform plan example` output is very useful to detect and solve this issue.
Another area to focus on is understanding error messages related to resource dependencies. Terraform relies on the relationships between resources. If a resource depends on another that hasn’t been created or is in an inconsistent state, errors can occur. Inspect the dependency graph to identify these issues. Furthermore, versioning conflicts between Terraform, providers, and modules can lead to unexpected errors. Specify version constraints to ensure compatibility and prevent conflicts. Regularly update Terraform and providers to benefit from bug fixes and improvements. Also, a `terraform plan example` provides a view to anticipate possible errors. Remember to validate your configuration using `terraform validate` before applying changes to catch simple errors. Finally, consult the Terraform documentation and community forums for specific error messages and solutions. By systematically addressing these common errors, users can significantly improve their Terraform workflow and maintain reliable infrastructure deployments. Understanding the output of a `terraform plan example` can illuminate potential issues before they are applied.