Why Create Your Own Terraform Provider?
There are compelling reasons to develop a specialized resource provider, especially when existing, general-purpose providers fall short. Organizations often find themselves managing infrastructure components or interacting with internal APIs that are not adequately supported by the standard offerings. In such scenarios, a custom Terraform extension becomes invaluable.
One primary driver is the need for increased control. A terraform custom provider allows you to precisely define how Terraform interacts with your infrastructure, ensuring that configurations align perfectly with your specific requirements. This level of control is simply unattainable when relying solely on pre-built providers that may not expose all the necessary parameters or functionalities. Tailored functionality is another significant advantage. You can design the extension to perform specific tasks or implement unique logic that is relevant to your environment. This ensures your terraform custom provider exactly meets your operational demands.
Moreover, creating a terraform custom provider enables seamless integration with proprietary systems. Many organizations have internal APIs or legacy infrastructure that are not publicly accessible or compatible with existing Terraform providers. By building a custom solution, you can bridge this gap and manage these resources using Terraform’s declarative configuration language. This brings the benefits of infrastructure-as-code to previously isolated parts of your environment. This includes version control, automated deployments, and consistent state management. Therefore, a terraform custom provider grants the freedom to model and manage resources that would otherwise be beyond Terraform’s reach, delivering enhanced automation and improved operational efficiency. A well-designed terraform custom provider gives you complete command over your infrastructure, offering benefits that standard providers cannot match. The flexibility it provides makes complex integrations manageable and boosts automation capabilities.
Understanding Terraform Provider Architecture
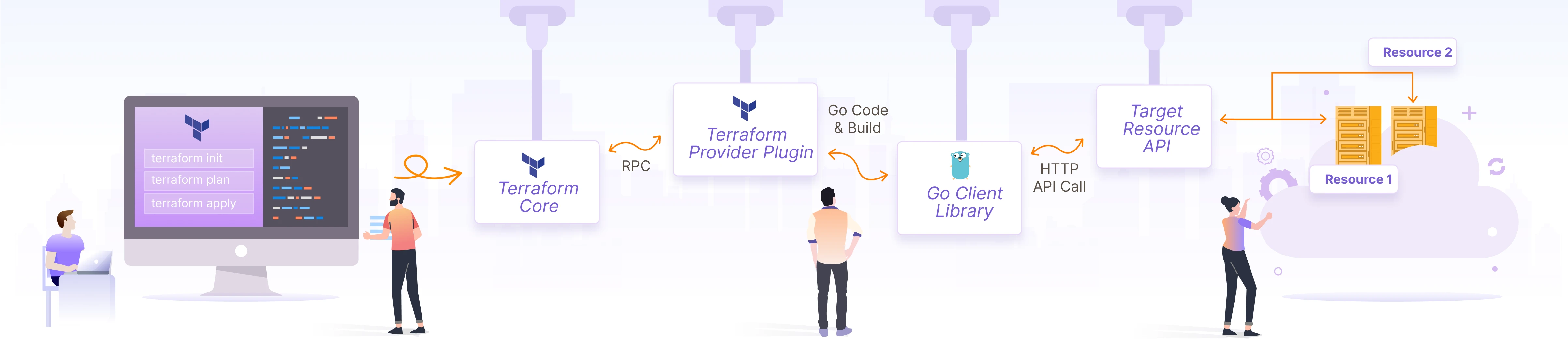
The architecture of a Terraform provider acts as the crucial bridge between Terraform configurations and the underlying infrastructure or service being managed. At its core, a terraform custom provider translates the declarative language of Terraform’s HashiCorp Configuration Language (HCL) into API calls specific to the target system. This translation allows Terraform to manage resources through a consistent interface, regardless of the underlying technology.
Key components within a terraform custom provider architecture include schemas, resources, and data sources. Schemas define the structure and data types of resources and data sources, ensuring that the Terraform configuration is valid and that the provider knows how to interpret the specified attributes. Resources represent the infrastructure components being managed, such as virtual machines, databases, or network configurations. Data sources, on the other hand, allow Terraform to retrieve information about existing infrastructure, enabling dynamic configuration and integration with external systems. The provider itself is responsible for implementing the CRUD (Create, Read, Update, Delete) operations for each resource type, interacting with the target API to provision, modify, and destroy infrastructure. Think of it as a translator. Terraform speaks HCL, and the provider translates that into the specific language (API calls) that the infrastructure understands.
The interaction between Terraform and a terraform custom provider can be visualized as follows: Terraform parses the HCL configuration, identifies the resources to be managed, and then invokes the corresponding functions within the provider. The provider then translates the configuration into API calls, sends those calls to the target system, and retrieves the results. The provider also manages the state of the infrastructure, storing the current configuration and any relevant metadata. This state management is essential for tracking changes and ensuring that Terraform can accurately plan and apply updates. Using a well-defined architecture for a terraform custom provider ensures a clear separation of concerns, promoting maintainability and scalability. This design allows developers to extend Terraform’s capabilities to manage almost any infrastructure component or service, solidifying Terraform’s position as a universal infrastructure-as-code tool. By leveraging these architectural principles, building a terraform custom provider becomes a manageable and powerful way to tailor infrastructure automation to specific needs.
How to Develop a Custom Terraform Resource Provider
Creating a terraform custom provider involves several key steps, starting with setting up the development environment. The primary language for terraform custom provider development is Go, so ensure that Go is installed and configured correctly. Additionally, the Terraform SDK (Software Development Kit) is essential. This SDK provides the necessary libraries and tools to interact with Terraform’s core functionalities.
Next, define the provider’s schema. The schema specifies the attributes that can be configured for the provider. This includes authentication details or any global settings required for interacting with the target infrastructure. Following the provider schema, define the resource schemas. A resource schema describes the attributes of each manageable resource. For example, if creating a terraform custom provider for an internal service, the resource schema might include attributes like service name, instance count, and resource allocation. These schemas act as blueprints, dictating the structure and validation rules for resource configurations. The heart of a terraform custom provider lies in its CRUD (Create, Read, Update, Delete) operations. Each resource type needs these functions implemented. The Create function provisions the resource via API calls to the underlying infrastructure. The Read function retrieves the current state of the resource. The Update function modifies the resource. The Delete function destroys or deprovisions the resource.
Consider a scenario where you are developing a terraform custom provider for managing internal services. A code snippet for the Create function might look like this:
Leveraging the Terraform Plugin Framework
The Terraform Plugin Framework significantly simplifies the development of a terraform custom provider. It offers a structured approach, reducing the boilerplate code and complexities typically associated with interacting directly with Terraform’s core functionalities. This framework acts as an intermediary, streamlining the communication between your terraform custom provider and Terraform itself.
One of the primary benefits of utilizing the Terraform Plugin Framework is automatic state management. The framework handles the intricacies of storing and retrieving resource states, ensuring data consistency and simplifying the development process. Schema validation is another key feature. The framework validates the schemas defined for resources and data sources, ensuring that the data provided by users conforms to the expected types and constraints. This validation helps prevent errors and ensures that the terraform custom provider operates correctly.
The framework abstracts away many of the complexities involved in interacting with the Terraform core. It offers specific features and libraries that handle tasks such as API compatibility, versioning, and error handling. By leveraging these features, developers can focus on implementing the specific logic of their terraform custom provider, rather than dealing with the underlying plumbing. Furthermore, the use of gRPC (Google Remote Procedure Call) as the communication protocol enhances the performance and reliability of the terraform custom provider. Overall, the Terraform Plugin Framework empowers developers to create robust, maintainable, and efficient Terraform extensions, making the process of building a terraform custom provider more accessible and manageable.
Testing Your Terraform Resource Provider
Testing a terraform custom provider is critical for ensuring its reliability and stability. A robust testing strategy encompasses various test types, each designed to validate different aspects of the provider’s functionality. Unit tests, integration tests, and acceptance tests are all vital components of a comprehensive testing approach.
Unit tests focus on individual functions and modules within the terraform custom provider code. These tests verify that each component performs as expected in isolation. For example, a unit test might check if a function correctly parses API responses or validates input parameters. Integration tests, on the other hand, verify the interaction between different components of the provider. These tests ensure that the various modules work together seamlessly. A typical integration test might involve creating a resource, modifying it, and then deleting it, all within a controlled environment. Acceptance tests provide the most comprehensive level of testing. They simulate real-world scenarios by deploying infrastructure using the terraform custom provider and verifying that the resulting infrastructure matches the desired state. These tests often involve using the `terraform apply` and `terraform destroy` commands with test configurations.
Writing effective tests for a terraform custom provider involves several key steps. First, define clear test cases that cover all CRUD (Create, Read, Update, Delete) operations for each resource type. Each test case should specify the expected input, the expected output, and the steps required to verify the outcome. It is important to simulate real-world conditions as closely as possible, including error scenarios and edge cases. Several tools and techniques can aid in testing terraform custom provider. The `terraform apply` command is used to create or update infrastructure, while the `terraform destroy` command removes it. By running these commands with test configurations, one can verify that the terraform custom provider correctly manages resources. Additionally, mocking frameworks can be used to simulate API responses and isolate the provider code from external dependencies. Thorough testing significantly reduces the risk of bugs and ensures that the terraform custom provider functions as expected in production environments. Neglecting testing can lead to unexpected behavior, infrastructure inconsistencies, and potential downtime. Therefore, investing in a robust testing strategy is essential for building a reliable and maintainable terraform custom provider.
Packaging and Distributing Custom Terraform Extensions
Once a custom Terraform extension, specifically a Terraform custom provider, is developed and tested, the next crucial step involves packaging and distributing it for use within Terraform configurations. This process ensures that the provider can be easily integrated into various projects and shared with other users. The initial stage involves building the provider binary, which is an executable file that Terraform utilizes to interact with the custom infrastructure component. This binary is typically created using the Go programming language, along with the Terraform SDK.
Distribution of the Terraform custom provider can occur through several methods. A straightforward approach is local installation, where the provider binary is placed in a directory that Terraform automatically searches for plugins. This is useful for individual use or during development. For broader sharing within an organization, a private registry offers a centralized repository for custom providers. This allows teams to easily discover, download, and use the Terraform custom provider in their projects. The Terraform Registry itself is another option, but is generally used for more widely applicable providers intended for public consumption. Regardless of the method chosen, proper versioning is essential. Semantic versioning should be employed to clearly indicate the compatibility and stability of each provider release.
Comprehensive documentation is paramount for a successful Terraform custom provider distribution. This documentation should include instructions on how to install the provider, configure its resources, and troubleshoot common issues. Clear examples of Terraform configurations that utilize the provider are also invaluable. By providing well-packaged and documented custom providers, organizations can empower their teams to effectively manage internal infrastructure and services through Terraform’s declarative approach. This meticulous process ensures the longevity and usability of the Terraform custom provider, facilitating its seamless integration into diverse Terraform environments. Therefore, robust packaging, strategic distribution, and comprehensive documentation are the final keystones in creating a valuable and accessible Terraform custom provider.
Best Practices for Designing Robust and Maintainable Providers
Building a robust and maintainable terraform custom provider requires careful planning and adherence to established best practices. Error handling is paramount; implement comprehensive error checking and informative error messages to aid in debugging. Utilize logging strategically to track provider behavior and diagnose issues. Effective logging provides insights into API interactions and internal processes, significantly simplifying troubleshooting efforts. Proper state management is equally crucial. Ensure that the provider correctly handles state persistence and updates to prevent inconsistencies and data loss. Leverage the Terraform Plugin Framework’s built-in state management capabilities to simplify this process. A well-structured codebase enhances maintainability. Organize code into logical modules and use meaningful names for variables and functions. Consistent coding style and clear documentation are essential for team collaboration and future maintenance. Adhering to Terraform provider development guidelines ensures compatibility and consistency across providers. These guidelines cover aspects like schema definition, data types, and API interaction patterns.
When designing a terraform custom provider, consider the scalability and performance implications of your design choices. Avoid unnecessary API calls and optimize data retrieval to minimize latency. Implement caching mechanisms where appropriate to reduce the load on external APIs. Asynchronous operations should be handled gracefully to prevent blocking the Terraform execution. Use appropriate concurrency controls to manage resources effectively. Thorough testing is essential for ensuring the reliability of a terraform custom provider. Implement unit tests to verify the correctness of individual components. Integration tests validate the interaction between the provider and external APIs. Acceptance tests simulate real-world scenarios and ensure that the provider behaves as expected in various conditions. These tests will minimize errors with the terraform custom provider.
Writing clean and well-documented code is essential for long-term maintainability of any terraform custom provider. Use comments liberally to explain the purpose of code sections and the rationale behind design decisions. Document all resources, data sources, and configuration options thoroughly. Provide clear examples of how to use the provider in Terraform configurations. Regularly review and update documentation to reflect changes in the codebase. By following these best practices, developers can create terraform custom providers that are reliable, scalable, and easy to maintain, ultimately improving the overall Terraform experience. Following these guidelines helps create a terraform custom provider that is both robust and user-friendly.
Addressing Common Challenges in Creating Custom Terraform Extensions
Creating a Terraform extension tailored to specific needs presents several potential hurdles. One frequent challenge involves interacting with APIs that are intricate or poorly documented. When the API lacks clarity, developers might struggle to map Terraform resources and data sources effectively. Thoroughly analyzing the API documentation and employing tools like API explorers can aid in understanding the API’s structure and behavior. Another approach involves building a thin abstraction layer on top of the API to simplify interactions with the Terraform provider.
Asynchronous operations within the target API can also introduce complexity. Terraform expects operations to complete within a reasonable timeframe. When an API call triggers a long-running process, the provider must handle this asynchronously. This often entails implementing polling mechanisms to check the status of the operation periodically. Developers can leverage Go’s concurrency features (goroutines and channels) to manage asynchronous tasks efficiently. Careful consideration should be given to timeout settings and error handling to prevent the provider from becoming unresponsive. Managing state inconsistencies is another area where developers may face difficulties when developing a specialized resource provider.
Ensuring that the Terraform state accurately reflects the actual state of the infrastructure can be tricky, especially when external factors influence the infrastructure outside of Terraform’s control. Implementing robust reconciliation logic is essential for detecting and resolving discrepancies. This involves periodically refreshing the state of resources and comparing it against the desired configuration. The `terraform custom provider` should also be designed to handle situations where resources are unexpectedly modified or deleted outside of Terraform. Effective logging and monitoring can significantly aid in debugging and troubleshooting issues that arise during the development and operation of a Terraform custom provider. Utilizing structured logging formats and integrating with monitoring systems can provide valuable insights into the provider’s behavior and identify potential problems early on. Furthermore, engaging with the Terraform community through forums and online resources can provide access to a wealth of knowledge and support from experienced provider developers. Remember to consult the official Terraform documentation and examples for guidance on best practices and common pitfalls. Seeking assistance from experienced developers can prove valuable in overcoming challenges associated with crafting a Terraform custom provider.