What is a Subnet in AWS?
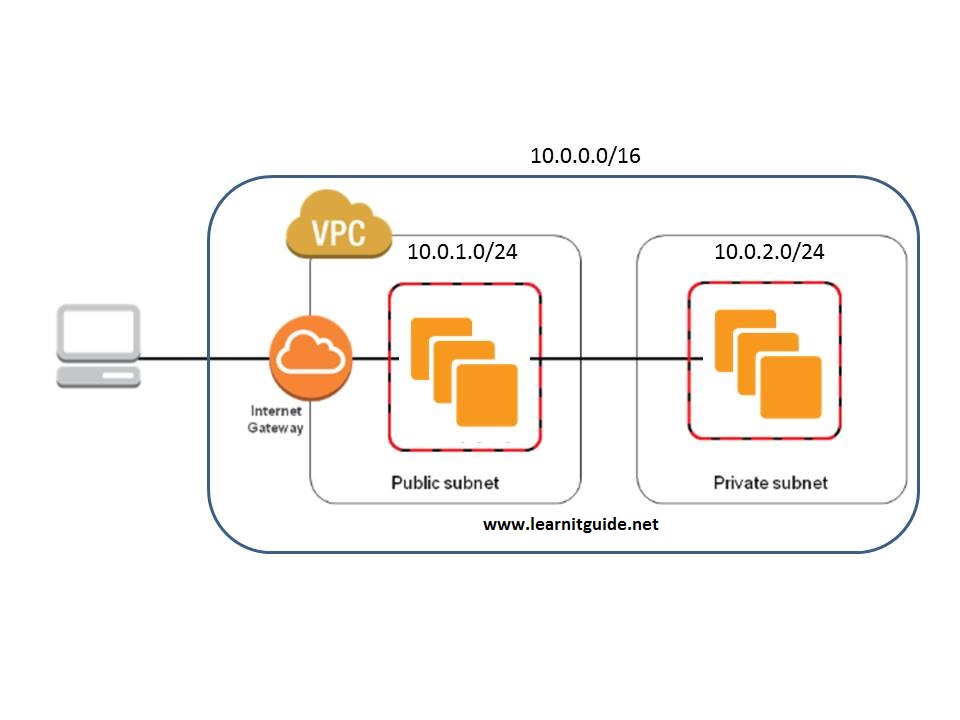
In Amazon Web Services (AWS), a subnet is a segment of a larger network that is created within a Virtual Private Cloud (VPC). Subnets are used for network segmentation and security, allowing for the isolation of resources and the implementation of access controls. The significance of subnets in AWS cannot be overstated, as they play a critical role in managing network infrastructure in the cloud. By dividing a larger network into smaller segments, subnets enable organizations to implement security policies, control traffic flow, and optimize network performance.
Creating and Configuring Subnets in AWS
To create and configure subnets in AWS, follow these steps:
- Log in to the AWS Management Console and navigate to the VPC dashboard.
- Click on “Subnets” in the left-hand menu and then click the “Create subnet” button.
- Select the VPC in which you want to create the subnet and specify the IPv4 CIDR block.
- Choose a availability zone and give the subnet a name and description.
- Click “Create” to create the subnet.
- To configure the subnet, select it from the list and click the “Actions” button, then select “Edit subnet settings”.
- Here, you can configure various settings such as the IPv6 CIDR block, map public IPs, and assign tags.
- Click “Save” to apply the changes.
When creating and configuring subnets in AWS, it is important to consider the implications on network performance and security. For example, choosing a smaller CIDR block will result in fewer available IP addresses, but it can also improve network performance by reducing the size of the broadcast domain. Additionally, mapping public IPs should be done carefully to ensure that only necessary resources are exposed to the internet.
Subnet Types and Their Use Cases in AWS
In AWS, there are three main types of subnets: public, private, and VPN-only. Each type has its own unique characteristics and use cases.
Public Subnets
Public subnets are connected to the internet and are assigned public IP addresses. They are typically used for resources that need to be accessible from the internet, such as web servers and load balancers. In a public subnet, it is important to implement security measures to protect against unauthorized access and attacks.
Private Subnets
Private subnets, on the other hand, are not connected to the internet and are not assigned public IP addresses. They are used for resources that do not need to be accessible from the internet, such as databases and application servers. Private subnets provide an additional layer of security, as resources are not directly exposed to the internet.
VPN-Only Subnets
VPN-only subnets are used to provide secure access to resources in a VPC over a VPN connection. They are not connected to the internet and are not assigned public IP addresses. VPN-only subnets are typically used for resources that need to be accessed remotely, but still require a high level of security.
When deciding which type of subnet to use, it is important to consider the specific needs and requirements of the resources being deployed. Public subnets are best suited for resources that need to be accessible from the internet, while private and VPN-only subnets are better suited for resources that require a higher level of security.
Subnet Routing and Internet Gateways
In order to connect subnets in AWS to the internet, you need to set up routing and configure internet gateways. An internet gateway is a horizontally scaled, redundant, and highly available VPC component that allows communication between instances in your VPC and the internet. It is the default method for allowing internet-bound traffic to flow out of your VPC.
To set up routing for a subnet, you need to create a route table and specify the routes for the traffic. A route table contains a set of rules, known as routes, that are used to determine where network traffic is directed.
Here are the steps to set up routing and configure an internet gateway:
- Create an internet gateway and attach it to your VPC.
- Create a custom route table and specify the internet gateway as the target for internet-bound traffic.
- Associate the route table with the subnet that you want to connect to the internet.
- Verify that the route table is associated with the subnet by checking the subnet’s details in the VPC dashboard.
It is important to note that the internet gateway and the route table must be in the same region and VPC. Additionally, the subnet’s network access control list (NACL) and security group rules must allow the necessary traffic.
Subnet Security and Access Control
When it comes to network security, subnets in AWS can be configured with various measures to control traffic and access. Two of the most important security measures are Network Access Control Lists (NACLs) and security groups.
Network Access Control Lists (NACLs)
NACLs are a type of firewall that controls inbound and outbound traffic at the subnet level. They are stateless, meaning that they do not track the state of the traffic, and each inbound and outbound rule is evaluated independently. NACLs are associated with a subnet and provide an additional layer of security to the instances within the subnet.
Security Groups
Security groups are a virtual firewall that controls inbound and outbound traffic at the instance level. They are stateful, meaning that they track the state of the traffic and allow return traffic automatically. Security groups are associated with instances and provide an additional layer of security to the instances.
Best Practices for Securing Subnets in AWS
Here are some best practices for securing subnets in AWS:
- Use NACLs and security groups in conjunction to provide multiple layers of security.
- Limit inbound traffic to only what is necessary and allow all outbound traffic by default.
- Use the principle of least privilege and only allow access to specific IP addresses or ranges.
- Regularly review and update NACLs and security group rules to ensure they are up-to-date and accurate.
- Consider using VPC peering or VPN connections to securely connect subnets in different VPCs or on-premises networks.
Subnet Monitoring and Troubleshooting
Monitoring and troubleshooting subnets in AWS is crucial to ensure network performance and security. There are several tools and services available in AWS to monitor and troubleshoot subnets. In this section, we will discuss some of these tools and services, common issues that can arise in subnets, and how to troubleshoot them.
Tools and Services for Monitoring Subnets
AWS provides several tools and services for monitoring subnets, including:
- Amazon VPC Flow Logs: VPC Flow Logs capture information about the IP traffic going to and from network interfaces in your VPC. You can use this information to troubleshoot connectivity issues, and to ensure that security group rules and network ACLs are working as expected.
- AWS CloudTrail: CloudTrail records API calls made to AWS services and provides visibility into user activity in your AWS environment. You can use CloudTrail to troubleshoot issues related to subnet configuration and changes.
- AWS CloudWatch: CloudWatch monitors resources and applications in real-time and provides visibility into resource and application performance. You can use CloudWatch to monitor network traffic, performance metrics, and to set alarms for specific conditions.
Common Issues in Subnets and How to Troubleshoot Them
Some common issues that can arise in subnets include:
- Connectivity issues: Connectivity issues can occur due to misconfigured security groups, network ACLs, or routing tables. You can use VPC Flow Logs, CloudTrail, and CloudWatch to troubleshoot connectivity issues and identify the root cause.
- Performance issues: Performance issues can occur due to high network traffic, low bandwidth, or network congestion. You can use CloudWatch to monitor network traffic and performance metrics and identify the root cause of performance issues.
- Security issues: Security issues can occur due to misconfigured security groups, network ACLs, or lack of access control. You can use VPC Flow Logs, CloudTrail, and CloudWatch to monitor network traffic and identify security issues.
Best Practices for Monitoring and Troubleshooting Subnets
Here are some best practices for monitoring and troubleshooting subnets in AWS:
- Enable VPC Flow Logs, CloudTrail, and CloudWatch for all subnets in your VPC.
- Regularly monitor network traffic, performance metrics, and security group rules and network ACLs.
- Set up alarms for specific conditions, such as high network traffic or low bandwidth.
- Use the information provided by VPC Flow Logs, CloudTrail, and CloudWatch to troubleshoot connectivity, performance, and security issues.
- Regularly review and update security group rules and network ACLs to ensure they are up-to-date and accurate.
Subnet Best Practices in AWS
When working with subnets in AWS, it’s important to follow best practices to ensure optimal performance, security, and scalability. In this section, we’ll discuss some of the best practices for working with subnets in AWS, including planning, organizing, configuring, and monitoring subnets.
Planning and Organizing Subnets
When planning and organizing subnets in AWS, it’s important to consider the following:
- Plan your subnets based on your network requirements, such as the number of instances, expected traffic, and security requirements.
- Organize your subnets into logical groups, such as development, staging, and production, to simplify management and maintenance.
- Use descriptive and meaningful names for your subnets to make it easier to identify and manage them.
Configuring Subnets Correctly
When configuring subnets in AWS, it’s important to consider the following:
- Configure your subnets with the appropriate IP address range and network mask to ensure optimal performance and security.
- Configure your subnets with the appropriate routing tables and internet gateways to allow traffic to flow in and out of the subnets.
- Configure your subnets with the appropriate network access control lists (NACLs) and security groups to control traffic in and out of the subnets.
Monitoring and Troubleshooting Subnets Regularly
When monitoring and troubleshooting subnets in AWS, it’s important to consider the following:
- Monitor your subnets regularly for performance, security, and availability issues.
- Use tools and services, such as Amazon CloudWatch and VPC Flow Logs, to monitor network traffic and performance metrics.
- Troubleshoot any issues quickly and efficiently to minimize downtime and ensure optimal performance and security.
Common Mistakes to Avoid
When working with subnets in AWS, there are some common mistakes to avoid, including:
- Not planning and organizing your subnets properly, leading to confusion and difficulty in management and maintenance.
- Configuring your subnets incorrectly, leading to performance, security, and availability issues.
- Not monitoring and troubleshooting your subnets regularly, leading to undetected issues and potential downtime.
By following these best practices and avoiding common mistakes, you can ensure optimal performance, security, and scalability for your subnets in AWS. With proper planning, organization, configuration, and monitoring, you can create and manage subnets that meet your network requirements and support your business needs.