Unlocking the Power of Publish-Subscribe with SNS
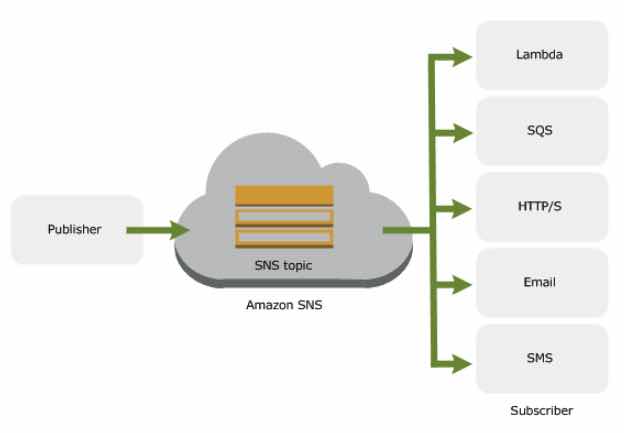
AWS Simple Notification Service (SNS) is a fully managed publish-subscribe (pub/sub) messaging service. It simplifies the process of decoupling applications. SNS improves scalability and enables asynchronous communication. Using an sns topic in aws allows developers to build flexible and responsive systems. This service provides a reliable platform for sending messages to a large number of subscribers. Common use cases include event notifications and mobile push notifications.
The benefits of using SNS are numerous. It allows for decoupling applications. This means that services can operate independently. Changes in one service do not directly impact others. SNS promotes scalability by distributing messages efficiently. The pub/sub model ensures that messages reach all interested subscribers. An sns topic in aws facilitates asynchronous communication, enabling near-real-time updates. Consider a scenario where multiple microservices need to react to a user action. Instead of direct service-to-service calls, an SNS topic can broadcast the event. Each microservice, subscribed to the sns topic in aws, processes the event independently.
SNS supports various messaging scenarios. One common application is sending event notifications. For example, when a new order is placed in an e-commerce system. SNS can notify relevant departments like fulfillment and customer service. Mobile push notifications are another popular use. Applications can use SNS to send alerts and updates directly to users’ mobile devices. SNS also enables application-to-application messaging. Different components within a distributed system can communicate through SNS topics. The key is the sns topic in aws which acts as a central point for message distribution. By leveraging SNS, organizations can build robust and scalable communication systems.
Architecting Scalable Notification Systems on AWS
AWS Simple Notification Service (SNS) is pivotal in constructing scalable and resilient notification systems within the AWS cloud. Its architecture is inherently designed to manage substantial message volumes, ensuring reliable distribution to numerous subscribers. An sns topic in aws acts as a central hub, facilitating the decoupling of message producers from message consumers. This decoupling fosters independent scaling and enhances overall system resilience.
SNS plays a crucial role in handling fluctuating workloads. It automatically scales to accommodate varying message rates without requiring manual intervention. This auto-scaling capability ensures consistent performance even during peak demand. The service integrates seamlessly with other AWS offerings, such as Simple Queue Service (SQS), AWS Lambda, and Amazon CloudWatch. An sns topic in aws can trigger Lambda functions, enabling event-driven architectures. Furthermore, messages can be routed to SQS queues for asynchronous processing, ensuring that no messages are lost during periods of high traffic. CloudWatch integration provides comprehensive monitoring capabilities, allowing users to track key metrics and identify potential bottlenecks. The ability to create an sns topic in aws that integrates with SQS offers a robust solution for building microservices, allowing to process messages independently. An sns topic in aws is the core for several solutions.
The integration of SNS with other AWS services empowers the creation of sophisticated notification workflows. For instance, an sns topic in aws can be configured to send notifications to mobile devices via AWS Pinpoint, enabling targeted marketing campaigns and real-time alerts. Additionally, SNS can be used to disseminate critical system alerts to operations teams, ensuring prompt responses to incidents. This capability makes it an essential component of any well-architected AWS environment, guaranteeing both scalability and reliability. Securing an sns topic in aws via IAM and encryption ensures data protection and compliance, making SNS a cornerstone of modern cloud architecture. Using an sns topic in aws is the best solution for notification systems.
Configuring an SNS Topic: A Step-by-Step Guide
Creating an SNS topic in AWS is a fundamental step in leveraging the power of publish-subscribe messaging. This guide provides a clear, concise walkthrough for beginners using the AWS Management Console to configure an sns topic in aws. Begin by logging into your AWS account and navigating to the SNS service within the AWS Management Console. Once in the SNS dashboard, locate and click the “Create topic” button. This will initiate the topic creation process, where you’ll define the core attributes of your sns topic in aws.
The first step is choosing a topic name. Select a descriptive and meaningful name that reflects the purpose of the sns topic in aws. This name will help you easily identify the topic later. Next, configure the access policy for your sns topic in aws. Access policies control who can publish messages to the topic and who can subscribe to it. For initial configuration, you can start with a basic policy that allows your AWS account to publish and subscribe. However, for enhanced security, it’s crucial to refine these policies based on your specific needs, granting access only to authorized users and services. Furthermore, consider enabling message delivery status tracking. This feature allows you to monitor the success and failure rates of message deliveries, providing valuable insights into the reliability of your notification system related to your sns topic in aws.
To enable message delivery status tracking, you will need to configure CloudWatch Logs. This involves specifying an IAM role that grants SNS permission to write logs to CloudWatch. By monitoring these logs, you can quickly identify and address any issues related to message delivery. Remember to keep your sns topic in aws secure by regularly reviewing and updating access policies as your application evolves. These steps will ensure a solid foundation for building robust and scalable notification systems using an sns topic in aws.
Securing Your SNS Topic for Enhanced Data Protection
Securing your sns topic in aws is paramount to prevent unauthorized access and message tampering, ensuring the confidentiality and integrity of your data. Implementing robust security measures safeguards your notification system from potential threats and maintains the trust of your users. A fundamental aspect of securing an sns topic in aws involves leveraging Identity and Access Management (IAM) roles and policies. IAM roles define the permissions granted to various AWS resources, dictating what actions they can perform on your sns topic in aws. By carefully crafting IAM policies, you can restrict access to only authorized users and services, preventing unauthorized publishing or subscription to your sns topic in aws. For example, you can create a policy that allows only specific EC2 instances to publish messages while restricting subscription to only authorized Lambda functions.
Encryption is another crucial layer of security for your sns topic in aws. Encryption at rest, achieved through AWS Key Management Service (KMS), encrypts the messages stored within the sns topic in aws. This ensures that even if an unauthorized party gains access to the underlying storage, the message content remains protected. Encryption in transit, enforced through HTTPS, secures the communication channel between publishers, sns topic in aws, and subscribers. By requiring HTTPS connections, you prevent eavesdropping and ensure that messages are transmitted securely. When configuring your sns topic in aws, always enable encryption at rest using KMS and enforce HTTPS for all communication to maintain a high level of security. Examples of access policies include restricting publishing to specific AWS accounts or IP addresses, and limiting subscription to only authenticated users. Regularly review and update these policies to adapt to evolving security threats.
Furthermore, monitor your sns topic in aws activity using AWS CloudTrail to detect any suspicious behavior or unauthorized access attempts. CloudTrail logs all API calls made to your sns topic in aws, providing an audit trail for security investigations. Implement alerting mechanisms based on CloudTrail logs to notify you of any potential security breaches. By combining IAM roles and policies, encryption, and continuous monitoring, you can create a comprehensive security posture for your sns topic in aws, protecting your data and ensuring the reliability of your notification system. By taking these precautions, you can maintain data privacy and adhere to compliance requirements. Proactive security measures will help maintain the integrity of your AWS environment and protect sensitive data.
Integrating SNS with Other AWS Services
AWS Simple Notification Service (SNS) excels when integrated with other AWS services, unlocking powerful application architectures. A key strength of an sns topic in aws lies in its ability to trigger actions in other services based on message publication. For example, an SNS message can automatically invoke an AWS Lambda function. This allows for serverless processing of events, such as resizing images or updating database records, in response to notifications. The lambda function will respond to the sns topic in aws automatically, triggering it with the message that was sent to the topic. This integration streamlines workflows and reduces the need for constantly running servers.
Another valuable integration involves using SNS to route messages to Amazon Simple Queue Service (SQS) queues. This pattern enables asynchronous processing of messages. Instead of directly processing messages upon arrival, SNS fans out messages to multiple SQS queues. Each queue can then be processed by a separate worker service, enhancing scalability and resilience. This is especially useful for handling tasks that require significant processing time or have varying workloads. An sns topic in aws, therefore, becomes a central point for distributing tasks across a distributed system, ensuring that no message is lost and that processing is handled efficiently, automatically sending notifications to the correct end points.
Furthermore, SNS integrates seamlessly with Amazon CloudWatch for monitoring and logging. CloudWatch can track various SNS metrics, such as the number of messages published, delivery success rates, and the number of filtered messages. This provides valuable insights into the health and performance of your notification system. Alerts can be configured in CloudWatch to notify administrators of potential issues, such as delivery failures or unexpected spikes in message volume. Real-world scenarios leveraging these integrations include e-commerce platforms using SNS to notify customers of order updates (triggering Lambda functions to send emails or SMS messages), financial institutions using SNS to alert users of fraudulent activity (routing notifications to SQS queues for further analysis), and IoT applications using SNS to process data from connected devices (using CloudWatch to monitor device health and performance). The flexibility of an sns topic in aws allows for these diverse integrations, making it a cornerstone of many modern AWS applications.
Understanding SNS Message Filtering Techniques
SNS offers robust message filtering capabilities, enabling subscribers to receive only the messages that align with their specific interests. This is achieved through attribute-based filtering, a powerful mechanism that allows subscribers to define rules based on message attributes. By leveraging attribute-based filtering, you can significantly reduce the volume of irrelevant messages delivered to subscribers, optimizing resource utilization and improving the overall efficiency of your asynchronous communication workflows. A well-configured sns topic in aws environment benefits greatly from this feature.
Attribute-based filtering operates by examining message attributes, which are key-value pairs included in the message metadata when publishing to an sns topic in aws. Subscribers define filtering policies that specify the attributes and values they are interested in. When a message is published, SNS compares the message attributes against the filtering policies of each subscriber. Only subscribers whose filtering policies match the message attributes will receive the message. This targeted delivery mechanism ensures that subscribers are not inundated with unwanted information, leading to more efficient processing and reduced costs. The creation and proper set up of the sns topic in aws is key to take advantage of the filtering capabilities.
To configure message filtering rules, you’ll typically interact with the AWS Management Console, the AWS CLI, or the AWS SDKs. The process involves specifying the attribute names and the corresponding values or patterns that subscribers are interested in. For instance, you can filter messages based on attributes such as region (e.g., “us-east-1”, “eu-west-2”), product type (e.g., “Electronics”, “Books”), or severity level (e.g., “Critical”, “Warning”). Imagine a scenario where you have an application that sends notifications about server status updates. By using message filtering, you can ensure that developers in the “us-east-1” region only receive notifications related to servers in their region, while operations teams receive all “Critical” alerts regardless of region. Correctly configuring your sns topic in aws for filtering will help streamline operations. This level of granularity empowers subscribers to tailor their message streams to their exact needs, maximizing the value of the information they receive and minimizing unnecessary noise.
Troubleshooting Common SNS Messaging Issues
When working with AWS Simple Notification Service (SNS), encountering occasional issues is part of the process. Message delivery failures represent a frequent challenge. These failures can stem from various sources, including incorrect subscription configurations, network connectivity problems, or issues on the subscriber’s end. Verifying the subscription’s status and ensuring the endpoint is active and reachable constitutes the initial troubleshooting step. Examining CloudWatch metrics associated with the sns topic in aws, like “NumberOfMessagesPublished” and “NumberOfNotificationsFailed,” offers valuable insights into delivery performance. Permission errors also commonly arise, typically due to improperly configured IAM roles or policies. Access Denied errors indicate that the entity attempting to publish or subscribe lacks the necessary permissions. Carefully reviewing IAM policies attached to the SNS topic and the user or service attempting the action is crucial. The sns topic in aws should have proper authorization.
Subscription issues, such as pending confirmations or filtering problems, also warrant attention. A subscription remains in a “pending confirmation” state until the endpoint owner explicitly approves it. If subscriptions are not confirmed, messages will not be delivered. Message filtering problems occur when the filtering rules are not correctly configured, preventing subscribers from receiving relevant messages. Double-checking the attribute names and values specified in the filter policies for the sns topic in aws is essential. Effective troubleshooting necessitates leveraging AWS CloudWatch for monitoring SNS metrics. Metrics such as “PublishSize,” “NumberOfMessagesPublished,” and “NumberOfNotificationsFailed” provide a comprehensive view of SNS performance. Analyzing these metrics can help pinpoint bottlenecks, identify error patterns, and proactively address potential issues. Examining the “NumberOfNotificationsFailed” metric, broken down by failure reason, offers specific clues about delivery problems. For instance, “FilterPolicyEvaluationError” suggests an issue with the message filtering rules.
To effectively resolve SNS issues, a systematic approach is crucial. Begin by examining CloudWatch logs and metrics to identify the scope and nature of the problem. Review IAM policies and subscription settings to ensure proper permissions and configurations. Test message delivery using the AWS Management Console or the AWS CLI to isolate potential issues. When encountering permission errors with your sns topic in aws, double-check the IAM roles and policies attached to both the SNS topic and the entities attempting to interact with it. Verify that the policies grant the necessary permissions for publishing, subscribing, and other relevant actions. If message filtering is not working as expected, carefully examine the filter policies associated with the subscription. Ensure that the attribute names and values in the policies match the corresponding attributes in the messages being published. By systematically investigating these areas, you can efficiently identify and resolve common SNS messaging issues, ensuring reliable and effective message delivery.
Optimizing SNS Usage for Cost Efficiency
Strategies for optimizing AWS Simple Notification Service (SNS) usage are crucial for minimizing costs while maintaining efficient messaging. Right-sizing topic configurations is a primary consideration. Evaluate the necessity of features and settings, ensuring they align with the application’s requirements. Unnecessary configurations can lead to increased operational expenses. Efficiently managing subscriptions also impacts cost. Analyze subscriber needs and remove inactive or redundant subscriptions. This reduces the number of message deliveries and associated charges. Leveraging message filtering is another effective method to reduce costs. By enabling subscribers to receive only relevant messages through attribute-based filtering, unnecessary message deliveries are minimized. This directly translates into cost savings, as you are not paying for messages that subscribers discard. The efficient use of sns topic in aws, through filtering, ensures targeted delivery and efficient resource allocation.
Monitoring SNS costs using AWS Cost Explorer provides valuable insights into spending patterns. AWS Cost Explorer allows you to visualize and analyze your SNS costs over time, identify cost drivers, and forecast future expenses. Regularly reviewing these reports helps pinpoint areas where optimization efforts can be focused. For example, if certain message attributes are consistently filtered out, it might indicate an opportunity to refine publishing practices or adjust subscription filters. It is important to analyze the delivery rates of your sns topic in aws. High failure rates often indicate configuration issues or delivery problems that waste resources. Addressing these issues promptly can prevent unnecessary costs.
Consider the message delivery protocols used by your sns topic in aws. Different protocols have varying cost implications. For example, HTTP/S deliveries might incur higher costs compared to SQS deliveries due to factors like retry policies and infrastructure overhead. Evaluate the cost-effectiveness of each protocol based on your application’s specific requirements and performance needs. Regularly review and adjust your SNS configurations, subscription management practices, and message filtering rules. Proactive cost optimization strategies are key to ensuring that you are leveraging SNS efficiently and cost-effectively. Efficient utilization of an sns topic in aws, is the key for cost optimization and delivering the proper messages.