What are Security Groups in AWS?
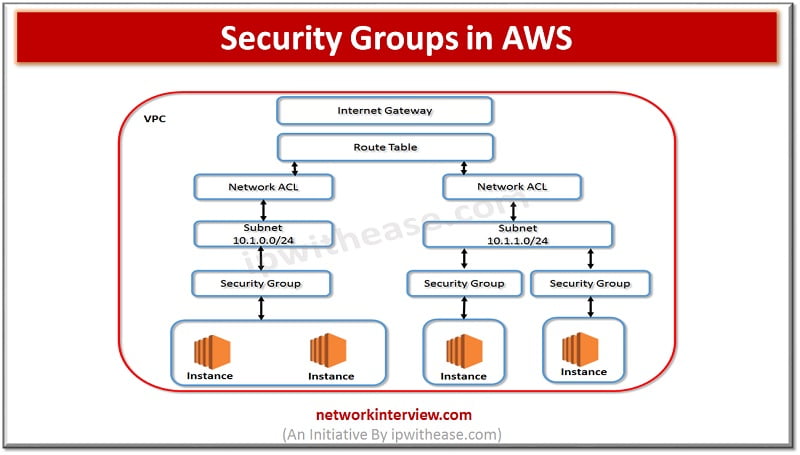
Security groups in Amazon Web Services (AWS) are a virtual firewall that control inbound and outbound traffic to and from resources in a Virtual Private Cloud (VPC). They are essential for maintaining the security and integrity of AWS environments, as they provide a way to manage network access to resources in a flexible and scalable manner. Security groups act at the instance level, allowing you to specify rules for allowing or denying traffic based on various parameters such as protocol, port, and source or destination IP address.
Key Features and Benefits of Security Groups
Security groups in AWS offer several key features and benefits that make them an essential component of any AWS environment. One of the main benefits of security groups is stateful inspection, which means that they automatically track the state of network connections and only allow return traffic that is associated with an established connection. This reduces the need for manual rule management and helps ensure that traffic flows as intended.
Another benefit of security groups is their ease of management through the AWS Management Console or API. Security groups can be easily created, modified, and deleted, and they can be attached to multiple resources, making it simple to manage network access for a group of resources. Additionally, security groups have default rules that allow unrestricted inbound and outbound traffic, which can be modified or removed as needed to meet specific security requirements.
How to Create and Configure Security Groups
Creating and configuring security groups in AWS is a straightforward process that can be done through the AWS Management Console or API. Here is a step-by-step guide to creating and configuring security groups:
- Navigate to the VPC dashboard in the AWS Management Console and click on “Security Groups” in the left-hand menu.
- Click the “Create Security Group” button and enter a name and description for the security group. Make sure to follow best practices for naming conventions, such as using a descriptive name that accurately reflects the security group’s purpose.
- Select the VPC in which you want to create the security group. Note that security groups are only applicable to the VPC in which they are created.
- Create rules for the security group by clicking the “Edit rules” button. You can create both inbound and outbound rules, which control traffic flowing into and out of the resources associated with the security group. Make sure to only allow traffic that is necessary for the resources to function, and to restrict access to specific IP addresses, protocols, and ports as needed.
- Test the security group rules to ensure that they are working as intended. You can test connectivity using tools such as telnet or nmap, or by launching resources and testing their connectivity to other resources.
It is important to regularly review and update security group rules to ensure that they are still relevant and necessary. Make sure to test any changes to security group rules before applying them to production resources.
How to Use Security Groups to Control Access to EC2 Instances
Security groups in AWS can be used to control access to EC2 instances, which are virtual machines that run on the AWS infrastructure. By default, EC2 instances are not accessible from the internet, but they can be made accessible by associating them with a security group. Here is how to use security groups to control access to EC2 instances:
- Create a security group with rules that allow inbound traffic to the EC2 instance. For example, you can allow traffic from a specific IP address or range of IP addresses, or from a specific protocol or port. Make sure to only allow traffic that is necessary for the EC2 instance to function.
- Associate the security group with the EC2 instance. This can be done when launching the EC2 instance, or after the instance has been launched. To associate a security group with an existing EC2 instance, navigate to the EC2 dashboard in the AWS Management Console, select the instance, and click on the “Actions” button. Then, select “Networking” and “Change security groups”. Select the security group that you created in step 1 and click “Assign”.
- Test the connectivity to the EC2 instance. You can test connectivity using tools such as telnet or nmap, or by launching resources and testing their connectivity to the EC2 instance. Make sure that the connectivity is working as intended and that only authorized traffic is able to reach the EC2 instance.
- Regularly review and update the security group rules to ensure that they are still relevant and necessary. Make sure to test any changes to security group rules before applying them to production resources.
It is important to note that security groups are stateful, which means that if you allow traffic in, the return traffic is automatically allowed, even if it is not explicitly allowed in the security group rules. This is an important feature that reduces the need for manual rule management and helps ensure that traffic flows as intended.
How to Monitor and Troubleshoot Security Groups
Monitoring and troubleshooting security groups is an important aspect of maintaining the security and integrity of AWS environments. Here are some steps to help you monitor and troubleshoot security groups:
- View security group rules: To view the rules for a security group, navigate to the VPC dashboard in the AWS Management Console, select the security group, and click on the “Actions” button. Then, select “View rules”. This will display a list of the inbound and outbound rules for the security group, including the protocol, port, and source or destination.
- Test connectivity: To test connectivity to a resource associated with a security group, you can use tools such as telnet or nmap. For example, if you want to test connectivity to an EC2 instance, you can use telnet to connect to the instance on a specific port. If the connection is successful, it means that the security group rules are allowing traffic to the instance on that port. If the connection is unsuccessful, it may indicate an issue with the security group rules or the resource itself.
- Identify and resolve common issues: Some common issues with security groups include incorrect rules, missing rules, and rules that allow too much traffic. To identify and resolve these issues, you can use the following steps:
- Check for incorrect rules: Make sure that the rules in the security group are allowing the correct traffic. For example, if you only want to allow traffic from a specific IP address, make sure that the rule only allows traffic from that IP address.
- Check for missing rules: Make sure that all necessary rules are present in the security group. For example, if you want to allow traffic to an EC2 instance on a specific port, make sure that there is a rule allowing traffic to that port.
- Check for rules that allow too much traffic: Make sure that the rules in the security group are not allowing too much traffic. For example, if you only want to allow traffic from a specific IP address, make sure that there is not a rule allowing traffic from any IP address.
By regularly monitoring and troubleshooting security groups, you can ensure that they are working as intended and that only authorized traffic is able to reach your resources. It is also important to regularly review and update security group rules to ensure that they are still relevant and necessary.
How to Manage Security Group Rules at Scale
Managing security group rules at scale can be a challenging task, especially in large and complex AWS environments. Here are some steps to help you manage security group rules at scale:
- Use security group rules to control access to multiple resources: Security group rules can be applied to multiple resources, making it easy to control access to a group of resources. For example, you can create a security group rule that allows traffic to a group of EC2 instances on a specific port. This can save time and reduce the complexity of managing security group rules for each individual resource.
- Use security group ingress and egress rules: Security group ingress rules control inbound traffic to a resource, while security group egress rules control outbound traffic. By using both ingress and egress rules, you can have more granular control over the traffic flowing to and from your resources. For example, you can create an ingress rule that allows traffic from a specific IP address to a resource, and an egress rule that allows the resource to send traffic to a specific IP address or range of IP addresses.
- Use AWS Security Hub to monitor security group compliance: AWS Security Hub is a service that helps you monitor and manage your security and compliance status across your AWS accounts. With Security Hub, you can view security group compliance status, identify non-compliant security groups, and take action to remediate any issues. This can help you ensure that your security groups are configured correctly and are following best practices.
- Regularly review and update security group rules: It is important to regularly review and update security group rules to ensure that they are still relevant and necessary. Make sure to test any changes to security group rules before applying them to production resources.
By following these steps, you can effectively manage security group rules at scale and ensure that your resources are secure and compliant with best practices. It is also important to regularly monitor and troubleshoot security groups to ensure that they are working as intended and that only authorized traffic is able to reach your resources.
Comparing Security Groups to Other AWS Security Mechanisms
Security groups are just one of the many security mechanisms available in AWS. Here is a comparison of security groups to other AWS security mechanisms, such as network ACLs and security groups in other AWS services:
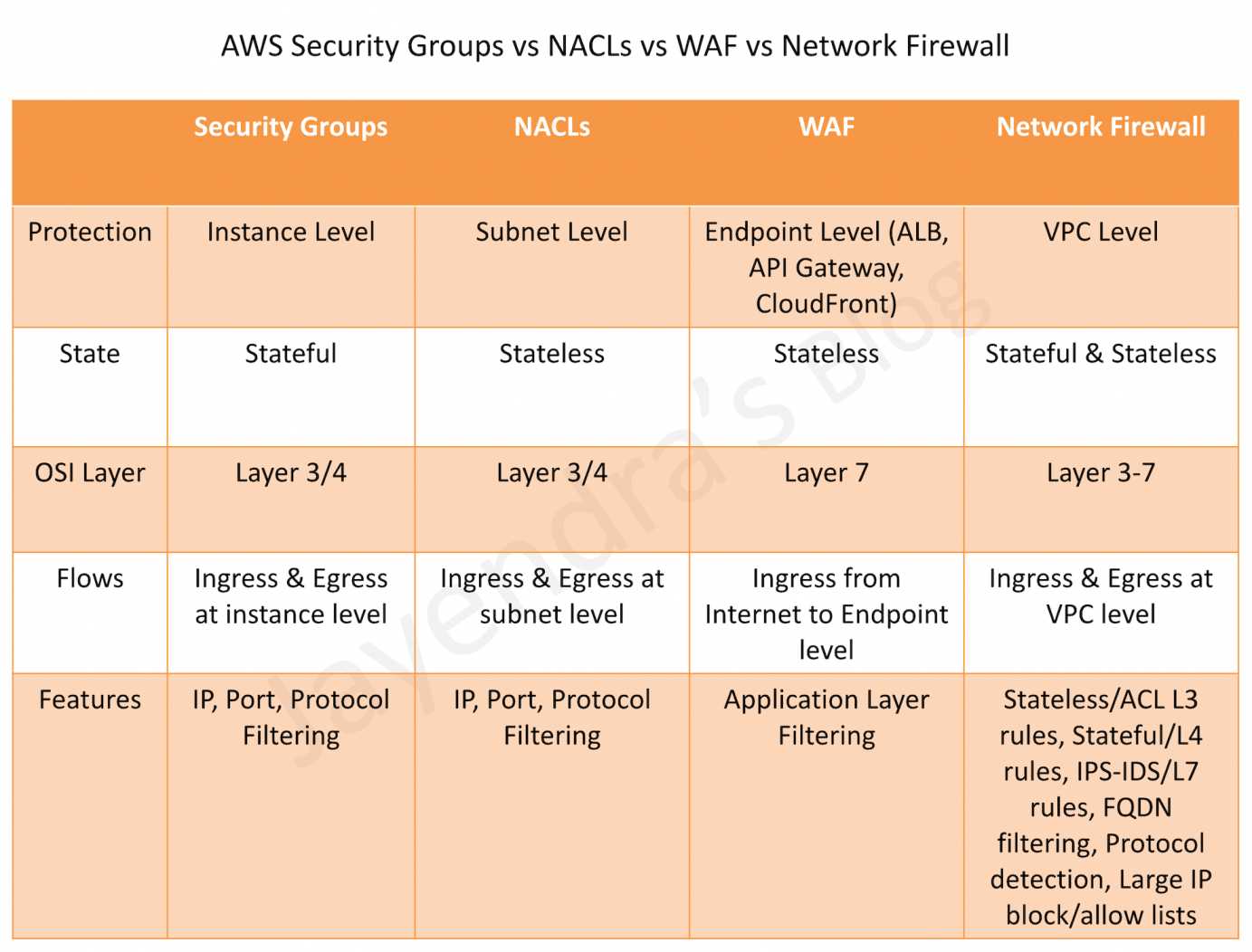
- Security groups vs network ACLs: Security groups and network ACLs are both used to control network access in AWS. However, there are some key differences between the two. Security groups are stateful, which means that they track the state of network connections and automatically allow return traffic. Network ACLs, on the other hand, are stateless, which means that they do not track the state of network connections and all traffic must be explicitly allowed. Security groups are also easier to manage than network ACLs, as they can be managed through the AWS Management Console or API, while network ACLs must be managed through the command line.
- Security groups in other AWS services: Security groups can also be used in other AWS services, such as Amazon Elastic Container Service (ECS) and Amazon Elastic Kubernetes Service (EKS). In these services, security groups can be used to control access to the containers or pods running in the cluster. However, it is important to note that the rules and management of security groups in these services may be different than in EC2.
Overall, security groups are a powerful and flexible security mechanism in AWS. They offer stateful inspection, default rules, and easy management through the AWS Management Console or API. However, it is important to consider other security mechanisms, such as network ACLs and security groups in other AWS services, when designing secure architectures in AWS.
Best Practices for Using Security Groups in AWS
Security groups are an essential part of maintaining the security and integrity of AWS environments. Here are some best practices for using security groups in AWS:
- Design secure architectures: When designing architectures in AWS, it is important to consider security from the beginning. This includes using security groups to control network access to resources. Make sure to follow the principle of least privilege, which means only allowing the minimum necessary access to resources. This can help reduce the attack surface and make it more difficult for attackers to gain access to your resources.
- Manage security group rules: It is important to regularly review and update security group rules to ensure that they are still relevant and necessary. Make sure to test any changes to security group rules before applying them to production resources. It is also a good idea to use descriptive and consistent naming conventions for security groups and rules, which can make it easier to manage and understand the rules.
- Monitor and troubleshoot security groups: Regularly monitoring and troubleshooting security groups can help ensure that they are working as intended and that only authorized traffic is able to reach your resources. Make sure to regularly view security group rules, test connectivity, and identify and resolve any common issues. You can also use tools such as AWS Security Hub to monitor security group compliance and identify any non-compliant security groups.
- Consider other security mechanisms: While security groups are a powerful and flexible security mechanism in AWS, it is important to consider other security mechanisms, such as network ACLs and security groups in other AWS services, when designing secure architectures in AWS. By using a combination of security mechanisms, you can create a more robust and secure environment in AWS.
By following these best practices, you can effectively use security groups in AWS to control network access to your resources and maintain the security and integrity of your AWS environments. It is also important to regularly review and update your security practices to ensure that they are still relevant and effective in the face of changing threats and attack vectors.