The Evolution of Data Security: From On-Premises to the Cloud
The rise of cloud computing has brought about a significant shift in the way organizations store and manage their data. Traditional on-premises data storage solutions are being replaced by cloud-based models, offering numerous benefits such as cost savings, scalability, and increased collaboration. However, this transition also introduces new challenges and potential risks related to data privacy and protection in the cloud era.
Cloud computing enables users to access and share data from anywhere, at any time, and on any device. This flexibility and convenience have made the cloud an attractive option for businesses of all sizes. However, the decentralized nature of cloud storage also increases the risk of data breaches, unauthorized access, and data misuse. As a result, it is essential to understand the privacy concerns associated with cloud computing and take appropriate measures to protect sensitive information.
When selecting a cloud service provider, it is crucial to consider factors such as data encryption, access controls, and compliance with data protection regulations. Leading cloud service providers, such as Amazon Web Services (AWS) and Microsoft Azure, offer robust security features and are committed to maintaining the highest standards of data privacy and protection. By carefully assessing cloud service providers and implementing strong access controls and encryption methods, organizations can mitigate the risks associated with cloud computing and ensure the privacy and protection of their data in the cloud era.

Understanding Privacy Concerns in the Cloud
As more organizations transition from traditional on-premises data storage to cloud-based solutions, it is essential to understand the privacy concerns associated with cloud computing. Privacy and protection in the cloud era are critical considerations for businesses of all sizes, as data breaches, unauthorized access, and data misuse can have severe consequences.
Data breaches can result in the unauthorized access and exposure of sensitive information, leading to financial losses, reputational damage, and legal liabilities. Unauthorized access can occur when hackers gain unauthorized access to cloud storage, while data misuse can occur when authorized users share or use data inappropriately. To mitigate these risks, it is essential to implement robust data privacy and protection measures in the cloud.
Data privacy is the protection of personal information, while data protection refers to the measures taken to safeguard data from unauthorized access, theft, or loss. In the cloud era, data privacy and protection are more critical than ever, as cloud storage enables users to access and share data from anywhere, at any time, and on any device. This flexibility and convenience increase the risk of data breaches, unauthorized access, and data misuse.
The potential consequences of privacy violations can be severe, including legal penalties, financial losses, and reputational damage. As a result, it is essential to take appropriate measures to protect sensitive information in the cloud. These measures include implementing strong access controls, using data encryption, and regularly monitoring and auditing cloud activities. By taking a proactive approach to data privacy and protection in the cloud era, organizations can mitigate the risks associated with cloud computing and ensure the confidentiality, integrity, and availability of their data.

Assessing Cloud Service Providers: Key Factors to Consider
When selecting a cloud service provider, it is essential to consider several key factors to ensure the privacy and protection of your data in the cloud era. These factors include data encryption, access controls, and compliance with data protection regulations. By carefully evaluating potential cloud service providers, you can choose a partner that meets your organization’s unique needs and requirements.
One of the most critical factors to consider when assessing cloud service providers is data encryption. Data encryption is the process of converting plain text into a coded format that can only be accessed with a decryption key. By encrypting data at rest and in transit, you can protect sensitive information from unauthorized access and data breaches. When evaluating cloud service providers, look for those that offer robust data encryption capabilities, such as Amazon Web Services (AWS) or Microsoft Azure. These providers offer a range of encryption tools and services, including symmetric and asymmetric encryption, to help protect your data in the cloud.
Access controls are another essential factor to consider when assessing cloud service providers. Access controls refer to the measures taken to ensure that only authorized users can access your data. When evaluating potential cloud service providers, look for those that offer multi-factor authentication, role-based access controls, and regular access log reviews. These measures can help prevent unauthorized access and data breaches, ensuring the privacy and protection of your data in the cloud era.
Compliance with data protection regulations is also critical when assessing cloud service providers. Data protection regulations, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), impose strict requirements on how organizations collect, store, and use personal data. When evaluating potential cloud service providers, look for those that are compliant with relevant data protection regulations. This compliance can help ensure that your organization is meeting its legal obligations and protecting the privacy and security of personal data in the cloud era.
In summary, when assessing cloud service providers, it is essential to consider data encryption, access controls, and compliance with data protection regulations. By carefully evaluating potential cloud service providers, you can choose a partner that meets your organization’s unique needs and requirements, ensuring the privacy and protection of your data in the cloud era.
How to Implement Strong Access Controls in the Cloud
Implementing strong access controls is a critical step in ensuring privacy and protection in the cloud era. Access controls refer to the measures taken to ensure that only authorized users can access your data. By implementing robust access controls, you can prevent unauthorized access, data breaches, and data misuse. In this article, we will offer practical tips on how to implement strong access controls in the cloud, including using multi-factor authentication, setting up role-based access controls, and regularly reviewing access logs.
Use Multi-Factor Authentication
Multi-factor authentication (MFA) is a security measure that requires users to provide two or more forms of identification before accessing a system or application. MFA can include something the user knows, such as a password, something the user has, such as a security token, and something the user is, such as a fingerprint. By implementing MFA, you can add an extra layer of security to your cloud-based systems and applications, making it more difficult for unauthorized users to gain access.
Set Up Role-Based Access Controls
Role-based access controls (RBAC) are a security measure that restricts access to systems and applications based on the user’s role within the organization. For example, you may grant certain users access to specific data or functions based on their job responsibilities. By implementing RBAC, you can limit the amount of access that each user has, reducing the risk of data breaches and data misuse. Additionally, RBAC can help simplify administration by allowing you to manage access for groups of users rather than individual users.
Regularly Review Access Logs
Regularly reviewing access logs is a critical step in ensuring strong access controls in the cloud. Access logs provide a record of who has accessed your systems and applications and what actions they have taken. By regularly reviewing access logs, you can identify any suspicious activity or unauthorized access attempts. Additionally, access logs can help you track user behavior and identify potential security threats. It is essential to review access logs regularly, as this can help you detect and respond to security incidents promptly.
Real-World Examples
Many cloud service providers offer tools and services to help you implement strong access controls in the cloud. For example, Amazon Web Services (AWS) offers Identity and Access Management (IAM), a service that allows you to manage access to AWS resources securely. With IAM, you can create and manage AWS users and groups and use permissions to allow and deny access to AWS resources. Similarly, Microsoft Azure offers Azure Active Directory, a cloud-based identity and access management service that provides centralized authentication and authorization for applications.
In summary, implementing strong access controls is critical in ensuring privacy and protection in the cloud era. By using multi-factor authentication, setting up role-based access controls, and regularly reviewing access logs, you can prevent unauthorized access, data breaches, and data misuse. Cloud service providers such as Amazon Web Services and Microsoft Azure offer tools and services to help you implement strong access controls in the cloud. By following these best practices, you can ensure the privacy and protection of your data in the cloud era.

The Role of Data Encryption in Cloud Security
Data encryption is a critical component of cloud security, providing an essential layer of protection for sensitive information. Encryption is the process of converting plain text into a coded format that is unreadable to unauthorized users. By encrypting data, organizations can protect sensitive information from data breaches, unauthorized access, and data misuse. In this article, we will discuss the importance of data encryption in cloud security, describing how it can protect data at rest and in transit. We will also provide examples of encryption tools and services that can help organizations implement robust data encryption in the cloud era.
Protecting Data at Rest
Data at rest refers to data that is stored in a static location, such as a database or file server. Protecting data at rest is critical in the cloud era, as data breaches can result in the unauthorized access and theft of sensitive information. Data encryption can help protect data at rest by converting plain text into a coded format that is unreadable to unauthorized users. Organizations can implement data encryption for data at rest using various encryption methods, such as symmetric and asymmetric encryption. Symmetric encryption uses the same key for encryption and decryption, while asymmetric encryption uses different keys for encryption and decryption. Examples of encryption tools and services that can help organizations implement data encryption for data at rest include Vormetric and SafeNet.
Protecting Data in Transit
Data in transit refers to data that is transmitted between two locations, such as from a user’s device to a cloud-based application. Protecting data in transit is critical in the cloud era, as data can be intercepted and accessed by unauthorized users during transmission. Data encryption can help protect data in transit by converting plain text into a coded format that is unreadable to unauthorized users. Organizations can implement data encryption for data in transit using various encryption methods, such as Transport Layer Security (TLS) and Secure Sockets Layer (SSL). TLS and SSL are cryptographic protocols that provide secure communication over the internet. Examples of encryption tools and services that can help organizations implement data encryption for data in transit include GlobalSign and DigiCert.
Best Practices for Data Encryption in the Cloud
Implementing data encryption in the cloud requires careful planning and execution. Organizations should follow best practices for data encryption in the cloud, including:
- Implementing strong encryption keys and key management practices
- Regularly monitoring and auditing encryption activities
- Providing employee training on encryption best practices
- Implementing multi-factor authentication for encryption key access
- Regularly testing encryption implementations for vulnerabilities
By following these best practices, organizations can ensure that their data is protected in the cloud era, reducing the risk of data breaches and unauthorized access.
In summary, data encryption is a critical component of cloud security, providing an essential layer of protection for sensitive information. By encrypting data at rest and in transit, organizations can protect sensitive information from data breaches, unauthorized access, and data misuse. By following best practices for data encryption in the cloud, organizations can ensure that their data is protected, reducing the risk of data breaches and unauthorized access. Cloud service providers such as Amazon Web Services and Microsoft Azure offer tools and services to help organizations implement data encryption in the cloud, providing a secure and protected environment for sensitive information.
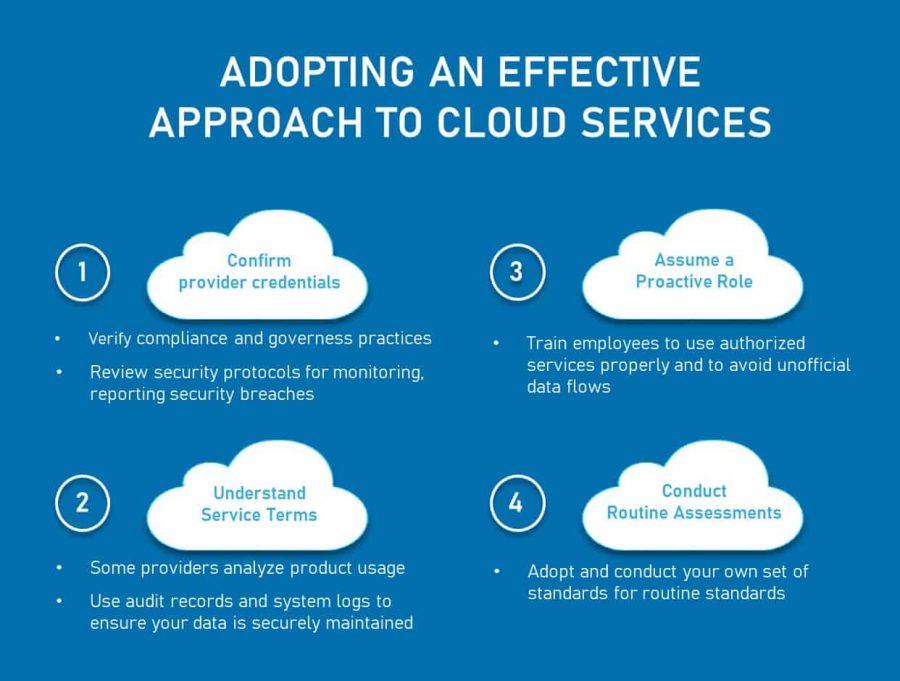
Monitoring and Auditing Cloud Activities: Best Practices
Monitoring and auditing cloud activities is a critical component of maintaining privacy and protection in the cloud era. With the increasing use of cloud-based solutions, organizations must ensure that their data is secure and protected from unauthorized access and misuse. By implementing best practices for monitoring and auditing cloud activities, organizations can detect and respond to potential security threats in a timely and effective manner.
Setting Up Alerts for Suspicious Activity
Cloud service providers offer various tools and services for monitoring and auditing cloud activities. One of the most effective ways to detect potential security threats is to set up alerts for suspicious activity. For example, organizations can set up alerts for failed login attempts, unusual data access patterns, or changes to critical system configurations. By setting up alerts for suspicious activity, organizations can quickly detect and respond to potential security threats, reducing the risk of data breaches and unauthorized access.
Regularly Reviewing Access Logs
Regularly reviewing access logs is another critical component of monitoring and auditing cloud activities. Access logs provide detailed information about who is accessing the system, when, and from where. By regularly reviewing access logs, organizations can detect potential security threats, such as unauthorized data access or suspicious user activity. Organizations should establish a regular schedule for reviewing access logs, such as daily or weekly, and should use automated tools to analyze access logs for potential security threats.
Using Third-Party Auditing Tools
Third-party auditing tools can provide additional visibility and insight into cloud activities. These tools can help organizations detect potential security threats, such as unauthorized data access or suspicious user activity, that may not be detected by native cloud service provider tools. Organizations should consider using third-party auditing tools to supplement native cloud service provider tools, providing a more comprehensive view of cloud activities.
Real-World Examples and Case Studies
Implementing best practices for monitoring and auditing cloud activities can provide significant benefits for organizations. For example, a financial services company used third-party auditing tools to detect unauthorized data access by a former employee. By detecting and responding to the security threat in a timely manner, the company was able to prevent potential data breaches and protect sensitive financial information.
In summary, monitoring and auditing cloud activities is a critical component of maintaining privacy and protection in the cloud era. By setting up alerts for suspicious activity, regularly reviewing access logs, and using third-party auditing tools, organizations can detect and respond to potential security threats in a timely and effective manner. Real-world examples and case studies demonstrate the benefits of implementing best practices for monitoring and auditing cloud activities, providing a more secure and protected environment for sensitive information.

Preparing for Data Breaches in the Cloud: Incident Response Planning
In today’s cloud era, data breaches have become a significant concern for organizations of all sizes. According to the Cost of a Data Breach Report 2021 by IBM and the Ponemon Institute, the average total cost of a data breach is $3.86 million. With the increasing adoption of cloud services, it’s crucial to have an incident response plan in place to minimize the impact of a data breach in the cloud.
An incident response plan is a set of instructions that help organizations detect, respond to, and recover from network security incidents. It outlines the steps to be taken before, during, and after a data breach to protect critical assets and minimize damage. Here are some key elements to include in an incident response plan for privacy and protection in the cloud era:
- Identify critical assets: Determine which data and systems are most important to your organization and prioritize their protection. This will help you focus your efforts on securing the most valuable assets in the event of a data breach.
- Establish communication protocols: Identify the key stakeholders who need to be notified in the event of a data breach, including employees, customers, and law enforcement agencies. Establish a clear communication plan to ensure that everyone is informed in a timely and accurate manner.
- Conduct regular drills: Practice your incident response plan regularly to ensure that everyone knows what to do in the event of a data breach. This will help you identify any weaknesses in your plan and make necessary adjustments.
- Implement multi-factor authentication: Multi-factor authentication (MFA) adds an extra layer of security to your cloud accounts by requiring users to provide two or more forms of identification before accessing sensitive data. This can help prevent unauthorized access to your cloud resources in the event of a data breach.
- Regularly review access logs: Regularly reviewing access logs can help you detect any suspicious activity in your cloud environment. This can help you identify and respond to data breaches more quickly, minimizing the impact of the breach.
In addition to these key elements, it’s essential to have a clear understanding of your cloud service provider’s incident response policies and procedures. Make sure you know what steps they will take in the event of a data breach and how they will communicate with you throughout the incident response process. By having a solid incident response plan in place, you can minimize the impact of a data breach in the cloud and protect your organization’s critical assets.

The Future of Cloud Security: Trends and Challenges
As we move forward in the cloud era, it’s essential to stay ahead of emerging trends and challenges in cloud security. With the increasing adoption of cloud services, the attack surface is expanding, and cybercriminals are becoming more sophisticated. Here are some of the key trends and challenges to consider in the future of cloud security:
- Artificial Intelligence (AI) and Machine Learning (ML): AI and ML are becoming increasingly important in cloud security, enabling organizations to detect and respond to threats more quickly and accurately. However, they can also be used by cybercriminals to launch more sophisticated attacks. It’s essential to have a solid understanding of AI and ML technologies and their potential risks and benefits to stay ahead of these trends.
- Internet of Things (IoT): The proliferation of IoT devices is creating new security challenges in the cloud. With more devices connected to the internet, there are more opportunities for cybercriminals to exploit vulnerabilities. It’s essential to have a clear understanding of the security risks associated with IoT devices and implement appropriate security measures to protect against these risks.
- Complexity of Cloud Environments: As cloud environments become more complex, with multiple cloud providers and services, it’s becoming increasingly challenging to manage security. It’s essential to have a clear understanding of your cloud environment and implement appropriate security measures to protect against potential threats.
To stay ahead of these trends and challenges, it’s essential to have a solid understanding of cloud security best practices and to implement appropriate security measures to protect your organization’s critical assets. This includes implementing strong access controls, using data encryption, regularly monitoring and auditing cloud activities, and preparing for data breaches with incident response planning. By staying informed and proactive, you can help ensure privacy and protection in the cloud era.
Moreover, it’s crucial to work with reputable cloud service providers that prioritize security and have a solid track record of protecting their customers’ data. Look for providers that offer robust security features, such as data encryption, access controls, and compliance with data protection regulations. Providers such as Amazon Web Services (AWS) and Microsoft Azure offer a wide range of security features and have a strong reputation for protecting their customers’ data.
In conclusion, the future of cloud security is likely to be characterized by emerging trends and challenges, such as the rise of AI and ML, the proliferation of IoT devices, and the increasing complexity of cloud environments. By staying informed and proactive, implementing appropriate security measures, and working with reputable cloud service providers, you can help ensure privacy and protection in the cloud era.
