Understanding Oracle’s Access Control System
Oracle’s access control mechanisms are fundamental to securing sensitive data within a database environment. These mechanisms govern who can access what data and how they can interact with it. At the heart of this system lies the concept of privileges, which are specific rights granted to users or roles. These privileges dictate the actions a user can perform, such as selecting data, inserting new records, updating existing information, or deleting entries. The system revolves around authentication, verifying user identity, and authorization, determining what actions an authenticated user is permitted to undertake.
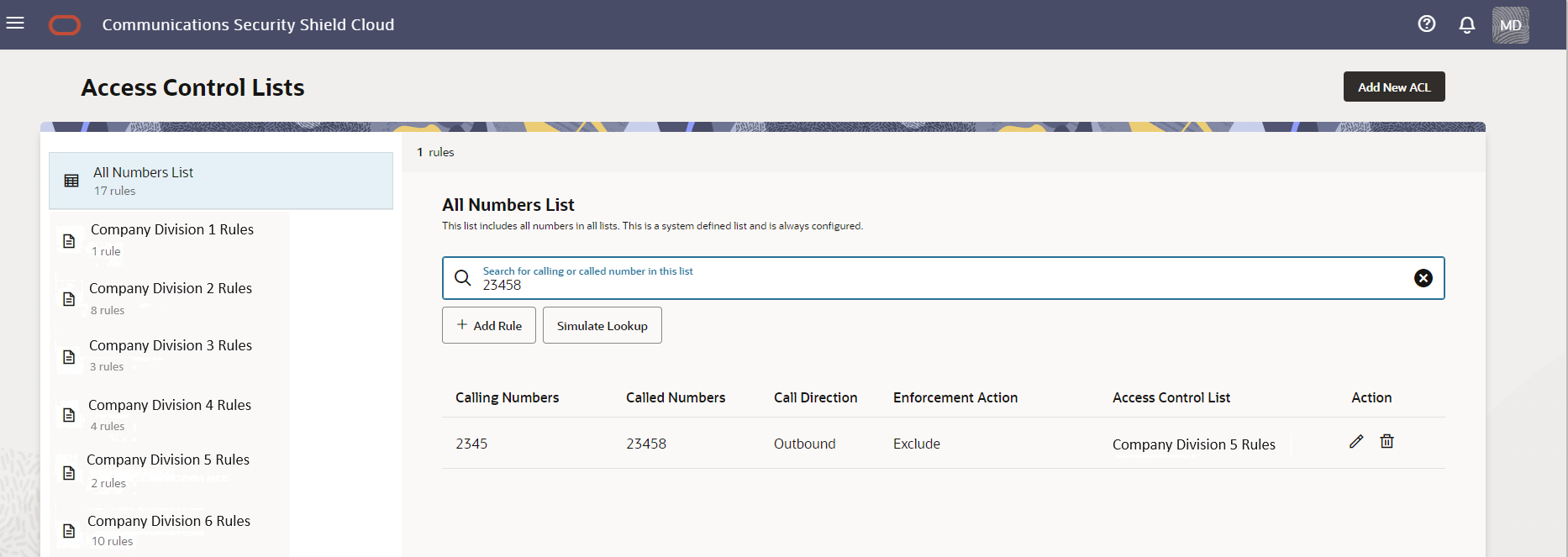
An oracle access control list (ACL) is a crucial component of Oracle’s security framework. An oracle access control list is essentially a list of permissions associated with a specific database object, such as a table, view, or procedure. It meticulously defines which users or roles have been granted access to that object and the precise nature of that access. Think of an oracle access control list as a gatekeeper, meticulously controlling entry to a protected resource. This enables a more granular and specific security configuration for your system, as access can be tailored to specific needs instead of granted universally. Managing oracle access control list effectively strengthens data protection measures within the Oracle environment.
Two core principles underpin effective Oracle permissions management: least privilege and separation of duties. The principle of least privilege dictates that users should only be granted the minimum level of access necessary to perform their job functions. This minimizes the potential damage from accidental or malicious actions. Separation of duties, on the other hand, ensures that no single individual has complete control over a critical process. This helps to prevent fraud and errors. By adhering to these principles and leveraging Oracle’s access control mechanisms, organizations can build a robust security posture that protects their valuable data assets. Implementing these principles requires careful planning, regular audits, and a thorough understanding of Oracle’s security features to properly configure oracle access control list.
How to Implement Fine-Grained Access Control in Oracle
Implementing fine-grained access control in Oracle involves strategically using the `GRANT` and `REVOKE` statements to manage user privileges on specific database objects. This approach allows administrators to define precisely what actions a user or role can perform, enhancing security and minimizing potential risks. The foundation of this control rests upon the effective use of the `oracle access control list` which will allow specific object access and modification rights.
The `GRANT` statement is used to assign privileges. The basic syntax is: `GRANT privilege_name ON object_name TO user_or_role`. For instance, to allow a user named ‘developer’ to select data from the ’employees’ table, the command would be: `GRANT SELECT ON employees TO developer`. Similarly, to grant update privileges: `GRANT UPDATE ON employees TO developer`. The `REVOKE` statement removes previously granted privileges. The syntax mirrors the `GRANT` statement: `REVOKE privilege_name ON object_name FROM user_or_role`. To revoke the select privilege from the ‘developer’: `REVOKE SELECT ON employees FROM developer`. For stored procedures, the `EXECUTE` privilege controls whether a user can run the procedure. `GRANT EXECUTE ON my_procedure TO developer` grants execution rights. Database views benefit significantly from `oracle access control list` to allow certain users and roles to see data. If a view joins sensitive tables, specific users can be granted select on the view without granting underlying table access. For a more structured method, the `WITH GRANT OPTION` clause can be added when using `GRANT`, so the grantee can extend the grant to other users. This must be used cautiously. The concept of least privilege should always dictate, granting only essential permissions to users and roles.
Consider a scenario involving a banking application. The ‘teller’ role needs to view account balances but should not be able to modify them. We would grant `SELECT` privilege on the ‘accounts’ table to the ‘teller’ role. The `oracle access control list` allows different access for different users and roles based on responsibilities. Simultaneously, the ‘manager’ role requires broader access, including the ability to update account information. Thus, ‘manager’ would be granted `SELECT` and `UPDATE` privileges on the ‘accounts’ table. Auditing successful and failed grant and revoke commands is useful to monitor configuration changes over time. By carefully managing `oracle access control list` privileges, the database administrator can enforce a secure environment where data access is tightly controlled and aligned with business requirements, preventing unauthorized access and potential data breaches.
Comparing Oracle ACLs with Roles: Which Approach is Right for You?
Oracle offers two primary mechanisms for managing database permissions: Access Control Lists (ACLs) and roles. Understanding the differences between these approaches is crucial for designing an effective and secure access control system. Roles are named groups of privileges that can be granted to users or other roles. When a user is granted a role, they inherit all the privileges associated with that role. This makes roles ideal for managing access control at a higher level, assigning broad permissions to groups of users based on their job functions. For instance, a “developer” role might have privileges to create tables and stored procedures in a development schema. Roles simplify administration by allowing you to manage permissions centrally. Rather than granting individual privileges to each user, you can manage roles and assign users to those roles as needed. This approach promotes consistency and reduces the risk of errors.
Oracle access control list, on the other hand, provides a more granular level of control. ACLs allow you to grant or deny specific privileges on individual database objects, such as tables, views, or procedures, to specific users or roles. This fine-grained control is useful when you need to restrict access to sensitive data or specific functionalities. For example, you might use an Oracle access control list to grant a user read-only access to a particular column in a table, while denying them access to other columns. This level of precision is not possible with roles alone. While ACLs offer greater flexibility, they can also be more complex to manage, especially in large databases with numerous objects and users. Implementing and maintaining a large number of ACLs can be time-consuming and prone to errors if not properly documented and managed. Therefore, choosing between roles and ACLs, or using a combination of both, depends on your specific requirements and the level of granularity needed for your access control policies.
The best approach often involves using roles for coarse-grained access control and ACLs for fine-grained control. Roles can be used to grant broad permissions based on job functions, while ACLs can be used to restrict access to specific resources or operations. For example, a role might grant a user the ability to access a specific application schema, while an ACL might restrict their access to certain tables within that schema. This hybrid approach provides a balance between manageability and security. Consider the complexity of your environment and the sensitivity of your data when deciding on the best approach. If you have a small database with a limited number of users and objects, ACLs may be sufficient. However, if you have a large, complex database with numerous users and sensitive data, a combination of roles and Oracle access control list is likely the best option. Regularly review and update your access control policies to ensure they remain effective and aligned with your organization’s security requirements.
Best Practices for Managing Oracle Database Permissions
Effective management of Oracle database permissions is crucial for maintaining data security and integrity. A cornerstone of this practice is adhering to the principle of least privilege, granting users only the minimum necessary access to perform their job functions. This approach limits the potential damage from both accidental errors and malicious activities. Implementing well-defined roles and carefully assigning users to those roles simplifies permission management and ensures consistency across the organization. Regularly reviewing and updating these roles is essential to reflect changes in job responsibilities and organizational structure. The oracle access control list is integral to this role based security.
Documented procedures are another vital component of a robust permissions management strategy. Clear, concise documentation outlining the process for granting, modifying, and revoking permissions ensures accountability and facilitates auditing. Naming conventions should be employed consistently across the database environment. Standardized naming conventions for roles, users, and database objects enhance clarity and simplify administration. Regular audits of access control policies are crucial for identifying potential vulnerabilities and ensuring compliance with internal policies and external regulations. These audits should examine user permissions, role assignments, and system access logs to detect any unauthorized activity or deviations from established procedures. The oracle access control list should be a main part of the regular audits.
Minimizing the “blast radius” of security breaches is a primary objective of effective permissions management. By carefully controlling access to sensitive data and implementing granular permissions, organizations can limit the potential impact of a security incident. For example, instead of granting broad access to an entire table, consider granting access only to specific columns or rows that a user needs. Employing features like Virtual Private Databases (VPD) can further restrict access based on context, such as the user’s location or department. The goal is to contain any potential breach and prevent it from spreading to other parts of the database or network. Proper management of the oracle access control list, combined with these strategies, constitutes a layered security approach to protect sensitive data assets. This also includes continuous monitoring and alerting on suspicious activities.
Troubleshooting Common Oracle Access Control Issues
One of the most frequent issues encountered in Oracle databases involves users being denied access to resources they believe they should have. This often stems from incorrect or incomplete privilege assignments within the Oracle access control list. Begin troubleshooting by verifying the user’s assigned roles and individual privileges. Use the `DBA_ROLE_PRIVS` and `DBA_SYS_PRIVS` data dictionary views to inspect these assignments. Ensure that the user possesses the necessary object privileges (e.g., SELECT, INSERT, UPDATE, DELETE) on the specific table, view, or stored procedure. Check for typos in object names or usernames, as these can easily lead to access denials. Remember, privilege grants must be explicitly given; simply being part of a role that *should* have access is insufficient if the role itself hasn’t been granted the necessary permissions. Also, consider the potential impact of negative grants. A negative grant overrides any positive grants obtained through roles or direct assignments, effectively denying access regardless of other permissions.
Another common problem involves permission conflicts, where a user’s privileges are unintentionally revoked or overridden. This frequently occurs in complex environments with numerous roles and overlapping permissions. Examine the grant history for the user and the affected objects to identify any conflicting grants or revokes. The `DBA_TAB_PRIVS_RECD` view can be invaluable in tracing privilege changes. If a user belongs to multiple roles, ensure that these roles do not have conflicting privileges. Prioritize directly granted privileges over role-based privileges when resolving conflicts. Additionally, be aware of the potential for privilege escalation vulnerabilities, where users exploit unintended permissions to gain unauthorized access. Regularly review and audit user privileges to identify and mitigate these risks. A well-defined Oracle access control list strategy is critical in preventing this.
Performance bottlenecks related to access control can also arise, particularly in systems with extensive auditing enabled or complex security policies. Excessive auditing can generate significant overhead, impacting query performance and overall system responsiveness. Review your auditing policies and adjust them to focus on critical events and users. Consider using fine-grained auditing to minimize the performance impact. If Virtual Private Database (VPD) policies are in place, ensure that they are optimized for performance. Poorly written VPD policies can introduce significant overhead. Use SQL Developer or other performance tuning tools to identify and address any performance bottlenecks related to access control. Properly indexing tables used in VPD policies can also drastically improve performance. Regularly monitor system performance and adjust access control configurations as needed to maintain optimal performance while ensuring adequate security. Understanding the Oracle access control list and its implications on performance is key to a well-tuned system.
Leveraging Oracle Enterprise Manager for Access Control Administration
Oracle Enterprise Manager (OEM) significantly simplifies the complexities of managing oracle access control list policies within an Oracle database environment. OEM offers a centralized, web-based interface that allows database administrators (DBAs) to efficiently administer, monitor, and report on security configurations, reducing the manual effort often associated with command-line tools. Through OEM, DBAs can visualize the existing oracle access control list permissions assigned to users and roles across various database objects, such as tables, views, and stored procedures. This visual representation provides a clear understanding of who has access to what, facilitating better governance and compliance.
OEM’s features enable the generation of comprehensive reports detailing the current state of oracle access control list implementations. These reports are invaluable for auditing purposes, providing stakeholders with the necessary documentation to demonstrate adherence to security policies and regulatory requirements. Furthermore, OEM facilitates proactive security management by identifying potential vulnerabilities. For instance, it can highlight users with excessive privileges or objects lacking appropriate access controls. By identifying these weaknesses, DBAs can take corrective actions to mitigate risks and strengthen the overall security posture of the Oracle database. Oracle Enterprise Manager streamlines the process of granting and revoking privileges, ensuring that changes to access control policies are implemented quickly and accurately. The intuitive interface minimizes the risk of errors that can occur when using manual SQL commands, leading to improved security and operational efficiency.
Beyond basic administration, Oracle Enterprise Manager offers advanced features for managing oracle access control list that enhance security and compliance. These include the ability to define and enforce security standards, track changes to security configurations over time, and automate tasks such as user provisioning and de-provisioning. By automating these tasks, OEM helps to reduce the administrative burden on DBAs and ensures that security policies are consistently applied across the entire Oracle environment. The centralized management capabilities of OEM promote a more secure and efficient approach to Oracle database administration, empowering organizations to protect their sensitive data while streamlining operations.
Advanced Oracle Security Features: Beyond Basic Permissions
While Oracle access control list (ACL) mechanisms provide a strong foundation for securing data, Oracle offers a suite of advanced security features that can further enhance an organization’s security posture. These features work in conjunction with ACLs to provide defense-in-depth, addressing various threats and vulnerabilities that basic permissions alone cannot mitigate. One powerful tool is Virtual Private Database (VPD), which enables fine-grained access control at the row level. VPD dynamically modifies SQL queries to restrict access to specific rows based on user context, ensuring that users only see the data they are authorized to view. This is particularly useful for applications with sensitive data that needs to be segmented based on user roles or responsibilities. For example, a healthcare application might use VPD to restrict doctors’ access to patient records based on their specialty or department.
Auditing policies are another critical component of a comprehensive Oracle security strategy. By enabling auditing, organizations can track user activity, including login attempts, data access, and DDL changes. This information can be used to detect suspicious behavior, investigate security incidents, and ensure compliance with regulatory requirements. Oracle provides a flexible auditing framework that allows administrators to define specific audit policies based on their needs. These policies can be configured to capture detailed information about user actions, including the time, user, object, and SQL statement executed. Data masking is a valuable technique for protecting sensitive data in non-production environments. It involves replacing real data with realistic but fictitious data, such as substituting credit card numbers with masked values or replacing names with pseudonyms. This ensures that developers, testers, and other non-production users can work with data without exposing sensitive information. Oracle Data Masking and Subsetting Pack provides tools to automate the data masking process, making it easier to protect sensitive data across the enterprise. These advanced features complement Oracle access control list capabilities, creating a more robust and secure environment.
The combination of Oracle access control list with VPD, auditing, and data masking provides a layered approach to security. This layered approach minimizes the risk of data breaches and ensures that sensitive information is protected from unauthorized access. Furthermore, these features facilitate compliance with industry regulations and internal security policies. Organizations should carefully evaluate their security requirements and implement the appropriate combination of these features to achieve their desired level of security. Regular reviews and updates of security policies are essential to adapt to evolving threats and ensure the ongoing protection of sensitive data. By leveraging the full range of Oracle’s security capabilities, organizations can create a robust and resilient security posture that protects their data assets and supports their business objectives. The effective use of oracle access control list in conjunction with these advanced features demonstrates a commitment to data security and compliance.
Maintaining a Secure Oracle Environment: Ongoing Monitoring and Auditing
Effective maintenance of a secure Oracle environment requires continuous monitoring and meticulous auditing of oracle access control list policies. This proactive approach is essential for detecting and responding to unauthorized access attempts and potential policy violations. Organizations should implement robust tools and techniques to facilitate these critical processes. Comprehensive logging is the foundation of effective monitoring. All access attempts, privilege grants, and policy modifications should be recorded with detailed information, including timestamps, user identities, and objects accessed. These logs provide a valuable audit trail for investigating security incidents and identifying suspicious activities. Analyzing these logs regularly can reveal patterns of misuse or vulnerabilities in access control configurations. The goal is to promptly identify and address any deviations from established security protocols.
Automated monitoring tools play a crucial role in maintaining a secure Oracle environment. These tools can be configured to generate alerts when specific events occur, such as failed login attempts, unauthorized data access, or changes to critical system configurations. Real-time alerts enable security teams to respond quickly to potential threats, minimizing the impact of security breaches. Oracle provides several built-in auditing features that can be customized to meet specific security requirements. For example, database administrators can configure audit policies to track access to sensitive data or monitor changes to user privileges. Utilizing these features helps to identify and address security vulnerabilities proactively. In addition to automated monitoring, regular manual reviews of oracle access control list policies are essential. These reviews should be conducted by experienced security professionals who can assess the effectiveness of existing controls and identify areas for improvement. The reviews should encompass all aspects of access control, including user privileges, role assignments, and the use of advanced security features.
Regular security reviews and updates are vital for maintaining a robust security posture. Oracle access control list policies should be reviewed and updated regularly to reflect changes in business requirements, technology advancements, and the evolving threat landscape. New vulnerabilities are constantly being discovered, and organizations must stay informed about the latest security threats and best practices. Regular updates ensure that the environment is protected against known vulnerabilities and that access controls remain effective. Furthermore, organizations should conduct periodic penetration testing to identify weaknesses in their security defenses. Penetration testing simulates real-world attacks, allowing organizations to assess the effectiveness of their security controls and identify vulnerabilities that could be exploited by malicious actors. By combining continuous monitoring, regular audits, and proactive security reviews, organizations can create a secure Oracle environment that protects sensitive data and minimizes the risk of security breaches. Remember that proactive maintenance of oracle access control list and security policies is better than reacting to a disaster.