Understanding Authorization in Oracle Cloud: A Comprehensive Overview
Authorization within Oracle Cloud Infrastructure (OCI) is the cornerstone of a secure and compliant cloud environment. Controlling access to resources is not merely a best practice; it is a fundamental requirement for protecting sensitive data and ensuring operational integrity. A well-defined authorization strategy dictates who can access specific resources and what actions they are permitted to perform. Without robust authorization, organizations risk unauthorized access, data breaches, and compliance violations. This underscores the critical need for a robust OCI policy system.
OCI offers various methods for managing access, ranging from broad permissions to highly granular controls. The choice of method depends on the specific security requirements and operational needs of the organization. However, a centralized policy system provides a consistent and auditable approach to access management. This involves defining policies that explicitly grant or deny permissions based on factors such as user identity, group membership, and resource type. A key aspect of OCI policy is its declarative nature; policies define the desired state of access control, and the system enforces that state automatically. Effectively, an OCI policy ensures proper management and compliance.
The importance of a robust OCI policy system cannot be overstated. It provides a centralized and auditable mechanism for managing access to cloud resources, reducing the risk of unauthorized access and data breaches. By implementing fine-grained access controls, organizations can ensure that users only have the permissions they need to perform their jobs, minimizing the potential impact of security incidents. Furthermore, a well-designed OCI policy framework simplifies compliance efforts by providing a clear record of who has access to what resources. By leveraging the power of OCI policy, organizations can build a secure and compliant cloud environment that protects their valuable data and applications. Furthermore, meticulous OCI policy implementation is vital for maintaining a strong security posture within the Oracle Cloud environment.
How to Implement Fine-Grained Access Control in OCI
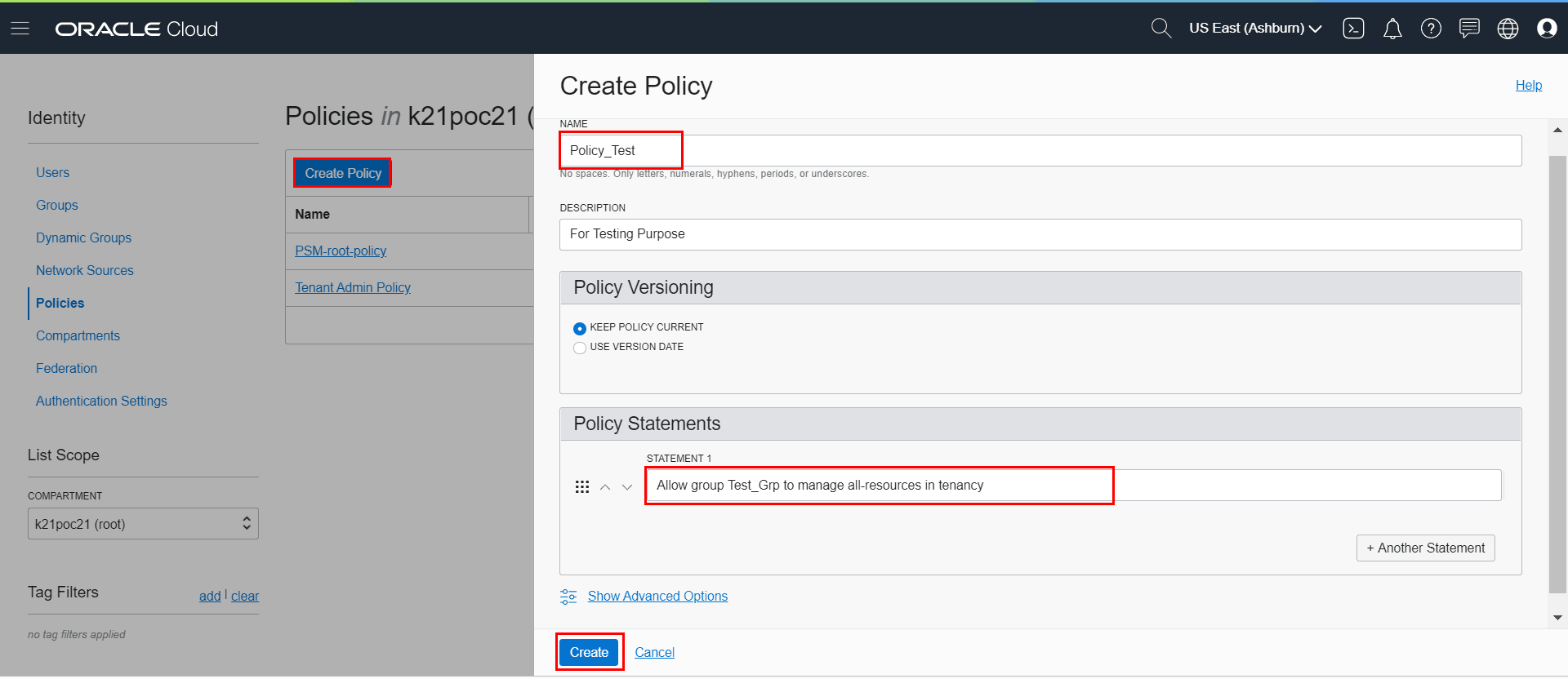
Implementing fine-grained access control in Oracle Cloud Infrastructure (OCI) is essential for maintaining a secure cloud environment. This involves carefully crafting and applying oci policy statements to control which users or groups can perform specific actions on OCI resources. The OCI console provides a user-friendly interface to manage these policies. To begin, navigate to the Identity and Access Management (IAM) section within the OCI console. From there, you can access the Policies area, where you can create, edit, and manage your authorization policies. The process starts with defining a policy name and description, followed by crafting the policy statements themselves. These statements dictate the permissions granted.
Creating a new oci policy involves specifying the resources to which the policy applies, the actions that are allowed (or denied), and the users or groups to whom the policy applies. Use the *allow* statement to grant permissions. For example, to allow a group named “DBAdmins” to manage database instances in a specific compartment, you would create a policy that grants them the “manage database-instances” permission within that compartment. Policies are attached to compartments, which act as logical containers for your OCI resources. By attaching a policy to a compartment, you grant the specified permissions to the users or groups within that compartment. When creating oci policy, always adhere to the principle of least privilege. Grant only the minimum necessary permissions required for a user or group to perform their tasks. Avoid granting broad permissions, as this can increase the risk of unauthorized access.
To effectively implement oci policy, consider organizing your users into groups based on their roles and responsibilities. Then, assign policies to these groups rather than individual users. This simplifies access management and ensures consistency across your organization. Regularly review your policies to ensure they remain relevant and effective. As your OCI environment evolves, you may need to adjust your policies to reflect changes in user roles, resource requirements, or security best practices. By following these steps and adhering to best practices, you can effectively implement fine-grained access control in OCI and enhance the security of your cloud environment. Always test your oci policy after implementation to confirm its effectiveness and make sure to address any unintended consequences.
Key Elements of an Effective Oracle Cloud Infrastructure Authorization Management Policy
An effective Oracle Cloud Infrastructure authorization management policy hinges on several core components that work together to define precisely who can access what resources, and under what conditions. Understanding these elements is crucial for building a secure and well-managed cloud environment. At the heart of every oci policy is the *allow* statement. This statement dictates the permissions granted to a specified group of users. It’s the foundation upon which access control is built, and its careful construction is paramount.
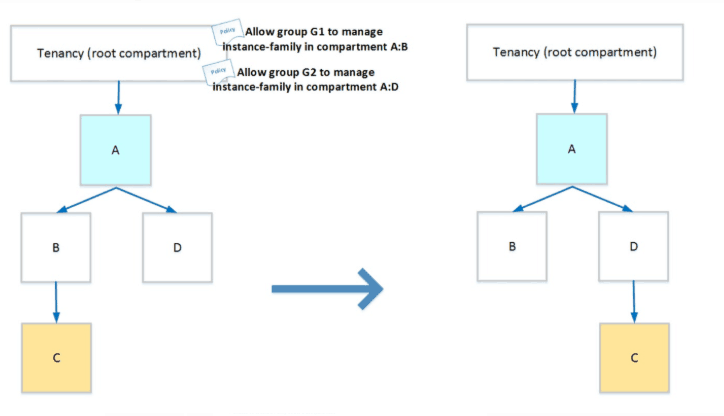
The verb, resource type, and target compartment are critical determinants within an oci policy. The verb specifies the action that the policy allows. Common verbs include *inspect*, *read*, *use*, and *manage*, each granting progressively broader levels of access. The resource type identifies the specific kind of resource being protected, such as instances, volumes, or networks. Finally, the target compartment defines the scope of the policy, restricting access to resources within that particular compartment. Consider this example: Allow group NetworkAdmins to manage virtual-network-family in compartment NetworkCompartment. This policy grants the “NetworkAdmins” group the ability to manage all virtual network resources within the “NetworkCompartment.” Breaking it down, “allow” initiates the permission, “group NetworkAdmins” identifies the grantee, “manage” is the verb defining the action, “virtual-network-family” specifies the resource type, and “compartment NetworkCompartment” limits the scope.
The *allow* statement’s impact on resource access is profound. A well-crafted oci policy using the *allow* statement ensures that users have only the necessary permissions to perform their tasks, adhering to the principle of least privilege. Conversely, an overly permissive policy can create significant security risks. It’s essential to regularly review and refine oci policy definitions. Doing so ensures that they accurately reflect the current needs of the organization and minimize the potential for unauthorized access. For instance, granting broad “manage” permissions should be carefully considered and typically reserved for administrative roles. The effective utilization of the *allow* statement, in conjunction with carefully defined verbs, resource types, and compartments, is the cornerstone of robust authorization management in Oracle Cloud Infrastructure.
Leveraging Groups and Compartments for Simplified OCI Access Management
Oracle Cloud Infrastructure (OCI) access management becomes significantly more streamlined by effectively leveraging groups and compartments. Organizing users into groups based on their roles within the organization simplifies the assignment of permissions. Instead of assigning policies to individual users, policies are attached to groups, and users inherit the permissions granted to their group. This approach reduces administrative overhead and ensures consistent access control across the organization. For instance, a ‘Database Administrators’ group can be created and granted the necessary permissions to manage database resources, automatically granting those rights to any user added to that group. This is a better approach than managing oci policy for each user. This makes OCI policy implementation much easier.
Compartmentalization provides another layer of simplification by isolating resources logically. Compartments act as containers for OCI resources, enabling you to control access at a higher level. Policies can be applied to compartments, granting specific groups or users access to all resources within that compartment. For example, a ‘Development’ compartment might contain all resources related to software development projects. An OCI policy applied to this compartment can grant developers the necessary permissions to manage compute instances, storage, and networking resources within that specific environment. This prevents developers from accidentally accessing or modifying resources in other compartments, such as production environments.
The combination of groups and compartments provides a powerful mechanism for simplified OCI access management. By carefully organizing users into groups based on their roles and isolating resources into compartments based on their purpose, it becomes easier to define and manage access control policies. The OCI policy can be more generic when applied at a compartment level and inherited by all the resources within it. Regularly reviewing group memberships and compartment structures is crucial to maintaining a secure and well-organized OCI environment. This approach not only simplifies administration but also enhances security by minimizing the risk of unintended access and ensuring that resources are protected according to their criticality and function. Using oci policy simplifies management and provides a robust security framework. Using an oci policy is key to a secure environment.
Common Scenarios and Best Practices for Crafting OCI Authorization Policies
In Oracle Cloud Infrastructure (OCI), authorization policies are fundamental for controlling access to resources. Several common scenarios demonstrate the practical application of crafting effective OCI policy statements. Consider the case of granting database administrators access to manage specific database instances. The appropriate OCI policy should precisely define the allowed actions on the target resource. For instance, to permit a group named `DatabaseAdmins` to manage databases within the `Production` compartment, the following OCI policy syntax could be used:
`Allow group DatabaseAdmins to manage database-family in compartment Production`
This OCI policy allows the `DatabaseAdmins` group to perform actions such as creating, updating, and deleting databases, but only within the `Production` compartment. Another frequent scenario involves enabling developers to manage compute resources within a designated compartment, such as `Development`. In this case, an OCI policy similar to the following would be suitable:
`Allow group Developers to manage instance-family in compartment Development`
This OCI policy grants the `Developers` group the necessary permissions to launch, terminate, and manage compute instances within the `Development` compartment. It’s crucial to adhere to the principle of least privilege when crafting these OCI policy statements. Instead of granting broad permissions, policies should be tailored to provide only the minimum access required for users to perform their tasks. For example, if developers only need to restart instances, the policy should reflect this limited scope:
`Allow group Developers to use instance-power-action in compartment Development`
In addition to specific resource types, policies can also be applied to resource groups. For instance, to allow network administrators to manage virtual network components like VCNs and subnets, the following OCI policy could be implemented:
`Allow group NetworkAdmins to manage virtual-network-family in compartment Network`
This OCI policy empowers the `NetworkAdmins` group to configure and maintain network infrastructure within the `Network` compartment. Furthermore, when constructing OCI policy statements, always specify the target compartment to restrict the scope of the permissions. Avoid using the root compartment unless absolutely necessary, as this grants access across the entire OCI tenancy. Proper implementation of OCI policy statements ensures a secure and well-managed cloud environment, adhering to security best practices and compliance requirements.
Troubleshooting Authorization Issues in Oracle Cloud Infrastructure
Encountering authorization issues within Oracle Cloud Infrastructure (OCI) is a common challenge when managing access to resources. These issues often manifest as users being denied access to resources they believe they should have or policies that don’t seem to function as intended. Effective troubleshooting requires a systematic approach to identify and resolve the root cause. A frequent cause is incorrect oci policy syntax. Even a small typo can render an entire policy ineffective. Carefully review the policy using the OCI console or API, paying close attention to spelling, capitalization, and the correct use of verbs and resource types. OCI provides tools for policy validation, which can help identify syntax errors before a policy is deployed. Ensure all necessary elements are present, such as the allow statement, the subject (user or group), the verb (e.g., read, use, inspect), and the target resource.
User group membership is another critical area to investigate. A user might be denied access if they are not a member of the correct group or if their group memberships have not been updated to reflect their current role. Verify the user’s group memberships in the OCI Identity and Access Management (IAM) console. Confirm that the groups to which the user belongs have the appropriate oci policy attached to grant the necessary permissions. Keep in mind that changes to group memberships may take a few minutes to propagate throughout the system. If a user is a member of multiple groups, be aware of potential conflicts between policies. A restrictive policy applied to one group can override a more permissive policy applied to another. Compartment hierarchies also play a significant role in authorization. An oci policy applied to a parent compartment automatically applies to all its child compartments, unless explicitly overridden. If a user is having trouble accessing a resource in a child compartment, ensure that the policy is either defined in the child compartment or inherited from a parent compartment. Check for any policies in the child compartment that might be restricting access.
When troubleshooting, utilize OCI’s logging and auditing capabilities to track access attempts and identify policy violations. OCI Logging captures detailed information about API calls, including the user who made the request, the resource being accessed, and the outcome of the authorization check. Analyze these logs to pinpoint the exact reason why a request was denied. The error messages in the logs often provide valuable clues about the source of the problem. For instance, a “NotAuthorizedOrNotFound” error typically indicates that the user lacks the necessary permissions to perform the requested action on the specified resource. Regularly review your oci policy configurations and user group memberships. Over time, roles and responsibilities can change, and policies may become outdated or overly permissive. Implement a process for periodic policy reviews to ensure they remain aligned with your organization’s security requirements. By systematically addressing these potential issues, you can effectively troubleshoot authorization problems in OCI and maintain a secure cloud environment.
Advanced Techniques: Using Conditions and Variables in Your OCI Policy
Oracle Cloud Infrastructure (OCI) authorization management extends beyond simple allow statements. Advanced techniques like conditions and variables provide granular control. They enhance the flexibility and security of your oci policy implementations. Conditions add contextual restrictions. Variables promote reusability and simplify management across compartments.
Conditions refine when an oci policy takes effect. They allow access based on specific criteria. For example, restrict access to certain hours using `time.between`. Limit access to a specific IP range using `request.source.ip`. The syntax involves specifying a condition key, operator, and value. An example is: `Allow group Developers to read objects in compartment Project1 where time.between(‘08:00’, ‘17:00’)` This oci policy grants access only during business hours. Another example is `Allow group NetworkAdmins to manage virtual-network-family in compartment Network where request.source.ip = ‘203.0.113.0/24’`. This allows managing network resources only from a specific network. Conditions enhance security by enforcing contextual access controls. Carefully consider the available condition keys and operators to tailor policies to your specific needs. Incorrectly configured conditions can lead to unexpected access denials. Thorough testing is crucial.
Variables introduce dynamism and reusability in oci policy definitions. They allow creating generic policies applicable across multiple compartments. Instead of hardcoding compartment names, use a variable like `${compartment.id}`. This variable resolves to the actual compartment ID at runtime. For example: `Allow group DatabaseAdmins to manage database-family in compartment ${compartment.id}`. To use variables effectively, understand their scope. Some variables are predefined, such as `${compartment.id}`. Others can be custom defined within your organization’s policies. Variables simplify policy management by reducing redundancy. A single, parameterized oci policy can replace multiple specific policies. This improves consistency and reduces the risk of errors. Variables make policies easier to understand and maintain. When using variables, document their purpose and expected values clearly. Incorrect variable usage can lead to unintended access grants. Test policies thoroughly after introducing variables.
Auditing and Monitoring Your Oracle Cloud Authorization Management Policies for Continuous Security
Context_8: Maintaining a secure Oracle Cloud Infrastructure (OCI) environment necessitates continuous auditing and monitoring of your OCI policy configurations. Proactive monitoring enables the detection of unauthorized access attempts, policy misconfigurations, and potential security vulnerabilities. OCI Logging and Monitoring services are invaluable tools for tracking access patterns and ensuring policy enforcement. Implementing a robust auditing strategy provides visibility into who is accessing what resources and when, facilitating timely responses to security incidents and demonstrating compliance with regulatory requirements. Regularly reviewing your oci policy configurations is critical to adapt to evolving security threats and changes in your organization’s access needs.
OCI Logging service captures a comprehensive record of actions performed within your OCI tenancy, including authorization-related events. These logs can be analyzed to identify patterns of suspicious activity, such as repeated failed login attempts or unauthorized access to sensitive data. Configuring alerts based on specific log events enables proactive notification of potential security breaches. OCI Monitoring service provides metrics related to resource utilization and performance, which can be correlated with authorization events to gain a holistic view of your security posture. For example, spikes in resource consumption following a change in an oci policy could indicate unintended consequences or malicious activity. Integrating your OCI logging and monitoring data with a Security Information and Event Management (SIEM) system can further enhance your security analysis capabilities.
Regular oci policy reviews are essential to ensure that your authorization configurations remain aligned with your organization’s security policies and business requirements. These reviews should involve verifying that the principle of least privilege is being followed, that policies are not overly permissive, and that access is granted only to authorized users and services. Consider automating the policy review process using scripts or third-party tools that can identify potential vulnerabilities and inconsistencies. Documenting your oci policy configurations and review procedures is crucial for maintaining accountability and facilitating audits. By continuously monitoring and auditing your OCI authorization management policies, you can proactively mitigate security risks, ensure compliance, and maintain a secure cloud environment.