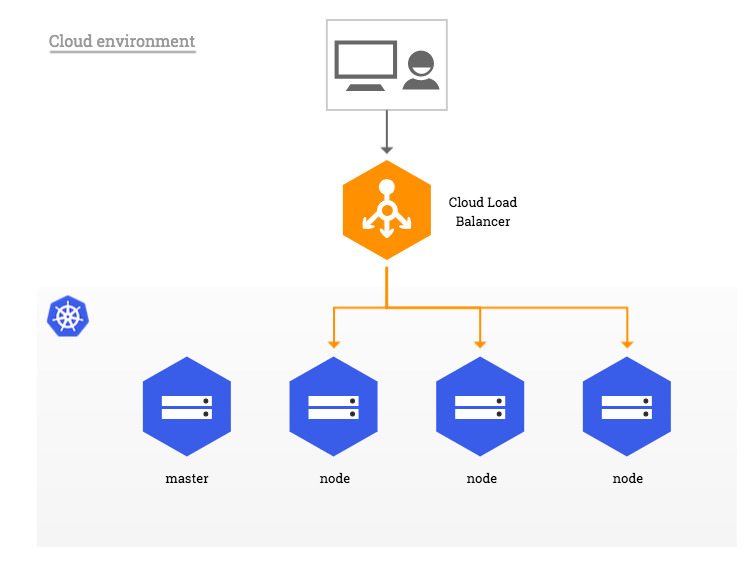
Understanding TLS and Its Role in Kubernetes Security
Transport Layer Security (TLS) is a cryptographic protocol that provides end-to-end security for communication between services in a Kubernetes cluster. TLS ensures data integrity, confidentiality, and authenticity by encrypting data in transit and verifying the identity of communicating parties. NGINX Ingress is a popular solution for implementing TLS in Kubernetes clusters.
TLS operates on the application layer of the network protocol stack, providing a secure communication channel between clients and servers. In a Kubernetes cluster, TLS is essential for securing communication between services, especially when data is transmitted over untrusted networks. NGINX Ingress TLS implementation provides a robust and flexible solution for securing communication between services in a Kubernetes cluster.
NGINX Ingress Controller is an open-source project that provides a reverse proxy, load balancer, and HTTP cache for Kubernetes. It supports TLS termination, allowing incoming HTTPS traffic to be decrypted and forwarded to backend services over HTTP. NGINX Ingress Controller also supports TLS passthrough, where incoming HTTPS traffic is forwarded to backend services without decryption.
Community-driven projects like kubernetes-ingress-controller also provide TLS implementation for Kubernetes clusters. These projects offer additional features and customization options, making them a suitable alternative to the official NGINX Ingress Controller. However, selecting the right NGINX Ingress TLS implementation depends on your specific requirements and the complexity of your Kubernetes cluster.
Choosing the Right NGINX Ingress TLS Implementation
When it comes to implementing NGINX Ingress TLS in your Kubernetes cluster, you have several options to choose from. The official NGINX Ingress Controller is a popular choice due to its robustness and flexibility. It supports TLS termination, allowing incoming HTTPS traffic to be decrypted and forwarded to backend services over HTTP. It also supports TLS passthrough, where incoming HTTPS traffic is forwarded to backend services without decryption.
Community-driven projects like kubernetes-ingress-controller also provide TLS implementation for Kubernetes clusters. These projects offer additional features and customization options, making them a suitable alternative to the official NGINX Ingress Controller. For instance, some community-driven projects provide support for advanced TLS features like OCSP stapling and session resumption.
Selecting the right NGINX Ingress TLS implementation depends on your specific requirements and the complexity of your Kubernetes cluster. Factors to consider when choosing an NGINX Ingress TLS implementation include the size of your cluster, the number of services you need to secure, and the level of customization you require.
For small to medium-sized clusters with a few services, the official NGINX Ingress Controller is a suitable choice. It provides a robust and flexible solution for securing communication between services in a Kubernetes cluster. However, for larger clusters with many services, community-driven projects may offer additional features and customization options that are better suited to your needs.
Regardless of the NGINX Ingress TLS implementation you choose, it’s essential to ensure that it meets your specific requirements and provides the level of security you need. By selecting the right NGINX Ingress TLS implementation, you can ensure that your Kubernetes cluster is secure and that communication between services is encrypted and authenticated.
Configuring NGINX Ingress TLS for Your Kubernetes Cluster
Configuring NGINX Ingress TLS for your Kubernetes cluster involves several steps, including creating TLS secret resources, configuring Ingress resources, and testing the setup. Here’s a step-by-step guide to help you get started:
-
Create a TLS secret resource: A TLS secret resource contains the necessary information to establish a secure TLS connection. To create a TLS secret resource, you can use the following command:
kubectl create secret tls my-tls-secret --key my-key.pem --cert my-cert.pem -
Configure Ingress resources: Once you have created a TLS secret resource, you can configure Ingress resources to use it. To do this, you can use the following Ingress resource configuration:
<h3>apiVersion: networking.k8s.io/v1 kind: Ingress metadata: name: my-ingress spec: tls: - secretName: my-tls-secret rules: - host: my-domain.com http: paths: - pathType: Prefix path: "/" backend: service: name: my-service port: number: 80 -
Test the setup: After configuring the Ingress resources, you can test the setup by accessing the service over HTTPS. If the setup is correct, you should see a secure connection in your browser.
It’s important to note that configuring NGINX Ingress TLS requires a good understanding of TLS and Kubernetes resources. Before configuring NGINX Ingress TLS, make sure you have a solid understanding of these concepts to avoid common mistakes and ensure a secure setup.
Best Practices for Managing NGINX Ingress TLS Secrets
Managing TLS secrets in a Kubernetes cluster is crucial for maintaining a secure environment. Here are some best practices for managing NGINX Ingress TLS secrets:
-
Rotation: Regularly rotate TLS secrets to reduce the risk of compromise. You can use automated tools to rotate TLS secrets at regular intervals or based on specific triggers, such as changes in access policies or user behavior.
-
Revocation: Revoke TLS secrets immediately if you suspect a compromise. You can use Kubernetes API to revoke TLS secrets and prevent unauthorized access to your cluster.
-
Storage: Store TLS secrets securely using Kubernetes secrets management tools, such as HashiCorp Vault or AWS Secrets Manager. Avoid storing TLS secrets in plaintext or in insecure locations, such as configuration files or environment variables.
-
Access control: Implement access control policies to restrict access to TLS secrets. Use Kubernetes role-based access control (RBAC) to define who can access TLS secrets and under what conditions.
-
Monitoring: Monitor TLS secrets for suspicious activity, such as unauthorized access or changes. Use Kubernetes audit logs and monitoring tools, such as Prometheus and Grafana, to detect and respond to security incidents.
By following these best practices, you can ensure that your NGINX Ingress TLS secrets are managed securely and effectively. This, in turn, can help you maintain a secure and compliant Kubernetes cluster.
Scaling and Monitoring NGINX Ingress TLS in Large Clusters
As your Kubernetes cluster grows, it becomes increasingly important to scale and monitor NGINX Ingress TLS effectively. Here are some tips on how to do so:
-
Load balancing: Use load balancing to distribute incoming traffic across multiple NGINX Ingress controllers. This can help improve performance and availability by ensuring that no single controller is overwhelmed with traffic. You can use Kubernetes Service resources to load balance traffic across multiple NGINX Ingress controllers.
-
Auto-scaling: Implement auto-scaling to automatically adjust the number of NGINX Ingress controllers based on demand. This can help ensure that your cluster can handle spikes in traffic and prevent performance degradation. You can use Kubernetes Horizontal Pod Autoscaler to automatically scale the number of NGINX Ingress controller pods based on CPU utilization or other metrics.
-
Performance monitoring: Monitor the performance of your NGINX Ingress controllers to ensure that they are running efficiently. You can use tools like Prometheus and Grafana to monitor performance metrics, such as request rate, response time, and error rate. This can help you identify and resolve performance issues before they impact your users.
-
Security monitoring: Monitor your NGINX Ingress controllers for security threats, such as unauthorized access or malicious traffic. You can use Kubernetes audit logs and monitoring tools to detect and respond to security incidents. This can help you maintain a secure and compliant Kubernetes cluster.
By following these best practices, you can ensure that your NGINX Ingress TLS is scalable and monitorable, even in large clusters. This can help you maintain a high level of performance and security as your cluster grows and evolves.
Troubleshooting Common NGINX Ingress TLS Issues
Implementing NGINX Ingress TLS can sometimes result in issues that can be challenging to diagnose and resolve. Here are some common issues and troubleshooting tips:
-
Certificate validation: If you encounter issues with certificate validation, ensure that the certificate is issued by a trusted certificate authority (CA) and that it is installed correctly. You can use tools like OpenSSL to verify the certificate and troubleshoot any issues.
-
Connection termination: If you experience issues with connection termination, ensure that the NGINX Ingress controller is configured correctly and that the termination mode is set appropriately. You can use Kubernetes logs and metrics to diagnose and resolve any issues.
-
Configuration errors: If you encounter configuration errors, ensure that the NGINX Ingress resources are configured correctly and that they match the TLS secret resources. You can use Kubernetes validation tools and manifests to diagnose and resolve any issues.
-
Performance degradation: If you experience performance degradation, ensure that the NGINX Ingress controllers are properly load balanced and that they have sufficient resources. You can use Kubernetes monitoring tools and metrics to diagnose and resolve any issues.
By following these troubleshooting tips, you can quickly diagnose and resolve common NGINX Ingress TLS issues. This can help you maintain a secure and performant Kubernetes cluster.
Staying Up-to-Date with NGINX Ingress TLS Security Updates
Staying up-to-date with NGINX Ingress TLS security updates and patches is crucial for maintaining a secure Kubernetes cluster. Here are some tips on how to monitor for updates and how to apply them in a timely manner:
-
Monitoring for updates: Use Kubernetes notifications and alerts to monitor for NGINX Ingress TLS updates and patches. You can also subscribe to NGINX and Kubernetes mailing lists and follow their official blogs to stay informed about new releases and security updates.
-
Applying updates: When a new update or patch is available, test it in a staging environment before applying it to your production cluster. This can help you identify and resolve any compatibility issues or conflicts before they impact your users. Once you have tested the update, apply it to your production cluster using Kubernetes rolling updates or other deployment strategies.
-
Backup and recovery: Before applying any updates or patches, ensure that you have a backup and recovery plan in place. This can help you quickly recover from any issues or failures that may occur during the update process.
By following these best practices, you can ensure that your NGINX Ingress TLS is up-to-date and secure. This can help you maintain a secure and compliant Kubernetes cluster and prevent security breaches and other incidents.