What Are Networking Concepts?
Networking concepts refer to the principles and practices that govern the design, implementation, and management of computer networks. These concepts are crucial for effective communication, data sharing, and security in a connected world. With the increasing reliance on digital technologies, understanding networking concepts has become more important than ever before. At its core, networking involves connecting multiple devices, such as computers, servers, and mobile devices, to enable communication and data sharing. Networking concepts provide a framework for designing, implementing, and managing these networks in a way that ensures optimal performance, security, and reliability.
Some of the key networking concepts include network topologies, protocols, addressing schemes, and security measures. Network topologies refer to the physical and logical layout of a network, while protocols are the rules that govern communication between devices. Addressing schemes, such as IP addresses, provide a unique identifier for each device on a network, while security measures, such as firewalls and access controls, protect the network from unauthorized access and data breaches.
Understanding networking concepts is essential for anyone working in the field of information technology, as well as for business owners and managers who rely on computer networks to operate their businesses. By mastering these concepts, you can ensure that your network is designed and managed effectively, providing a solid foundation for your digital operations.
Key Networking Concepts Explained
Networking concepts are the building blocks of computer networks, providing a foundation for effective communication, data sharing, and security. Here are some of the fundamental networking concepts that you should know:
Network Topologies
Network topology refers to the physical and logical layout of a network. There are several types of network topologies, including star, ring, bus, mesh, and tree. Each topology has its advantages and disadvantages, and the choice of topology depends on the specific needs of the network.
Protocols
Network protocols are the rules that govern communication between devices on a network. Some of the most common network protocols include TCP/IP, HTTP, FTP, and DNS. These protocols define the format, sequence, and error handling of data transmission, ensuring that devices can communicate effectively.
Addressing Schemes
Addressing schemes provide a unique identifier for each device on a network. The most common addressing scheme is the Internet Protocol (IP) address, which is a numerical label assigned to each device connected to a network. Other addressing schemes include Media Access Control (MAC) addresses and Domain Name System (DNS) names.
Security Measures
Security measures are essential for protecting computer networks from unauthorized access, data breaches, and other threats. Some of the most common security measures include firewalls, access controls, intrusion detection systems, and encryption. These measures help ensure that only authorized users can access the network and that data is protected from theft or damage.
Understanding these fundamental networking concepts is essential for anyone working with computer networks. By mastering these concepts, you can ensure that your network is designed and managed effectively, providing a solid foundation for your digital operations.
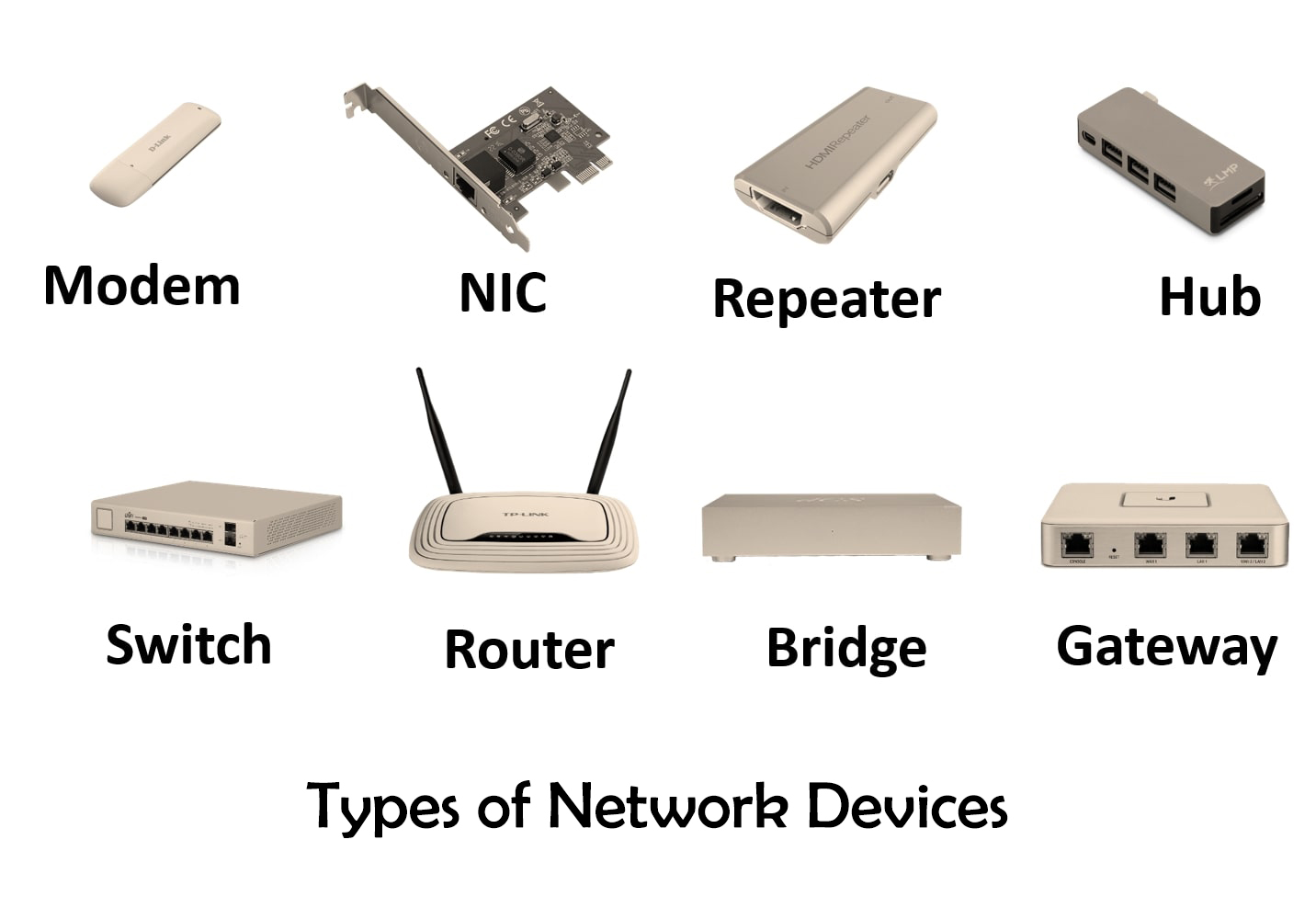
The Role of Network Devices in Modern Networking
Network devices are the building blocks of computer networks, enabling communication and data sharing between devices. Here are some of the most common network devices and their functions:
Routers
Routers are network devices that connect multiple networks and route data between them. They use routing tables to determine the best path for data transmission, ensuring that data is delivered efficiently and effectively. Routers are essential for connecting networks in different locations, such as branch offices and remote workers.
Switches
Switches are network devices that connect multiple devices on a network and facilitate communication between them. They use MAC addresses to forward data between devices, ensuring that data is delivered to the correct destination. Switches are essential for creating high-performance networks and supporting applications that require fast data transmission, such as video streaming and online gaming.
Hubs
Hubs are simple network devices that connect multiple devices on a network. They broadcast data to all connected devices, regardless of the destination. Hubs are less common than switches and routers, as they can create network congestion and reduce network performance.
Firewalls
Firewalls are network devices that protect networks from unauthorized access and data breaches. They use access controls, intrusion detection systems, and other security measures to prevent hackers and other threats from accessing the network. Firewalls are essential for protecting sensitive data and maintaining network security.
Understanding the role of network devices is essential for effective network design and management. By selecting the appropriate network devices and configuring them correctly, you can ensure that your network is reliable, secure, and high-performing.
How to Choose the Right Networking Solutions for Your Business
Choosing the right networking solutions for your business can be a daunting task, given the wide range of options available in the market. However, by considering the following factors, you can make an informed decision that aligns with your business needs:
Scalability
Scalability is the ability of a network to grow and adapt to changing business needs. When choosing a networking solution, consider the scalability of the solution and whether it can accommodate future growth. A scalable networking solution can save you time and money in the long run, as you won’t have to replace the entire network when your business expands.
Reliability
Reliability is the ability of a network to perform consistently and without failure. When choosing a networking solution, consider the reliability of the solution and whether it can provide the uptime and availability required by your business. A reliable networking solution can minimize downtime and ensure that your business operations run smoothly.
Security
Security is the protection of a network from unauthorized access and data breaches. When choosing a networking solution, consider the security features of the solution and whether they can provide the level of protection required by your business. A secure networking solution can protect sensitive data and maintain network integrity.
Cost-effectiveness
Cost-effectiveness is the balance between the cost of a networking solution and its benefits. When choosing a networking solution, consider the cost of the solution and whether it provides value for money. A cost-effective networking solution can provide the required functionality at a price that fits your budget.
By considering these factors, you can choose a networking solution that meets your business needs and provides a solid foundation for your digital operations. Remember that networking concepts are constantly evolving, so it’s essential to stay up-to-date with the latest trends and innovations in networking technologies.
Emerging Trends in Networking Technologies
In today’s rapidly evolving digital landscape, networking concepts are continually advancing to keep pace with the growing demands of businesses and individuals alike. This section explores some of the latest trends and innovations in networking technologies, including software-defined networking (SDN), network function virtualization (NFV), and 5G networks. Understanding these emerging technologies is crucial for staying ahead in a competitive and connected world.
Software-Defined Networking (SDN)
SDN is an innovative approach to networking that separates the control plane from the data plane, enabling centralized management and programmability of network resources. By abstracting network intelligence and decoupling it from hardware, SDN simplifies network design, automates network configuration, and improves network agility. As a result, SDN has gained significant traction in modern networking, particularly in data centers, cloud computing, and network security applications.
Network Function Virtualization (NFV)
NFV is another emerging trend in networking that involves virtualizing network functions, such as firewalls, load balancers, and intrusion detection systems, to run as software applications on standard servers. By virtualizing network functions, NFV reduces the dependency on proprietary hardware, increases network flexibility, and lowers operational costs. NFV is often used in conjunction with SDN to create more agile, scalable, and cost-effective network architectures.
5G Networks
5G networks represent the next generation of wireless communication technology, promising faster speeds, lower latency, and improved network reliability compared to their 4G counterparts. With 5G networks, users can expect to experience download speeds of up to 20 Gbps, latency as low as 1 ms, and support for a massive number of connected devices. These enhancements will enable new use cases, such as real-time augmented reality, autonomous vehicles, and smart cities, further driving the need for advanced networking concepts and technologies.
Challenges and Opportunities
While these emerging trends in networking technologies offer numerous benefits, they also present challenges in terms of complexity, security, and interoperability. For instance, SDN and NFV require new skill sets and expertise to design, deploy, and manage, while 5G networks introduce new security threats and vulnerabilities that must be addressed. Nevertheless, the opportunities for innovation and growth in the networking space are immense, making it an exciting time for professionals and enthusiasts alike.
Best Practices for Network Security and Management
Effective network security and management are essential for maintaining the confidentiality, integrity, and availability of computer networks. This section outlines best practices for securing and managing networks, covering topics such as access control, intrusion detection, network segmentation, and disaster recovery planning. By implementing these best practices, organizations can minimize the risk of security breaches, improve network reliability, and ensure business continuity.
Access Control
Access control is a fundamental aspect of network security that involves managing user access to network resources. Implementing robust access control policies and mechanisms, such as role-based access control (RBAC) and multi-factor authentication (MFA), can help prevent unauthorized access and mitigate the risk of insider threats. Regularly reviewing and updating access control policies is also crucial for maintaining a secure network environment.
Intrusion Detection
Intrusion detection systems (IDS) monitor network traffic for signs of malicious activity, such as unauthorized access attempts, malware infections, and denial-of-service (DoS) attacks. By deploying IDS solutions, organizations can detect and respond to security threats in real-time, minimizing the potential damage and downtime associated with security breaches. Regularly updating and tuning IDS rules and signatures is essential for ensuring their effectiveness against evolving threats.
Network Segmentation
Network segmentation involves dividing a network into smaller, isolated segments to reduce the attack surface and improve security. By segmenting a network, organizations can contain security threats, limit lateral movement, and simplify network management. Implementing virtual local area networks (VLANs) and firewall rules are common methods for achieving network segmentation.
Disaster Recovery Planning
Disaster recovery planning involves creating and maintaining a comprehensive plan for restoring network operations in the event of a catastrophic failure, such as a natural disaster, cyber attack, or hardware failure. A well-designed disaster recovery plan includes backup and recovery strategies, redundancy and failover mechanisms, and communication and coordination procedures. Regularly testing and updating the disaster recovery plan is essential for ensuring its effectiveness in a real-world scenario.
Continuous Monitoring and Improvement
Effective network security and management require continuous monitoring and improvement. Regularly reviewing network logs, performance metrics, and security alerts can help identify potential issues and vulnerabilities, enabling organizations to proactively address them before they become critical. Implementing a culture of continuous learning and improvement can also help organizations stay up-to-date with emerging threats and technologies, ensuring their networks remain secure, reliable, and efficient.
Real-World Applications of Networking Concepts
Networking concepts are not just theoretical constructs; they have far-reaching implications in various real-world applications. Here are some examples of how networking concepts enable the functioning of modern technologies:
Cloud Computing
Cloud computing is a paradigm that allows users to access shared resources, such as servers, storage, applications, and services, over the internet. Networking concepts, such as virtualization, load balancing, and traffic management, play a crucial role in enabling cloud computing to function seamlessly.
Internet of Things (IoT)
IoT is a network of interconnected devices, sensors, and actuators that communicate with each other to collect, exchange, and analyze data. Networking concepts, such as addressing schemes, protocols, and network topologies, are essential in enabling IoT devices to communicate and share data effectively.
Edge Computing
Edge computing is a paradigm that involves processing data closer to the source, rather than in a centralized data center. Networking concepts, such as network function virtualization (NFV) and software-defined networking (SDN), enable the deployment of distributed computing resources and the management of data flows in edge computing environments.
Content Delivery Networks (CDNs)
CDNs are a system of distributed servers that deliver content to users based on their geographical location. Networking concepts, such as caching, load balancing, and traffic management, are essential in enabling CDNs to deliver content quickly and efficiently to users around the world.
Cyber-Physical Systems (CPS)
CPS is a network of interconnected physical devices, such as machines, vehicles, and buildings, that communicate with each other to collect, exchange, and analyze data. Networking concepts, such as protocols, addressing schemes, and network topologies, are essential in enabling CPS to function effectively and securely.
Smart Cities
Smart cities are urban areas that use technology to improve the quality of life for citizens. Networking concepts, such as wireless networks, sensors, and actuators, are essential in enabling smart cities to collect, exchange, and analyze data to optimize traffic flow, energy consumption, and public safety.
Telemedicine
Telemedicine is the use of technology to deliver healthcare services remotely. Networking concepts, such as secure communication protocols, network segmentation, and access control, are essential in enabling telemedicine to function securely and efficiently.
Virtual Reality (VR) and Augmented Reality (AR)
VR and AR are immersive technologies that allow users to experience virtual environments. Networking concepts, such as low-latency networks, high-bandwidth connections, and real-time communication protocols, are essential in enabling VR and AR to function seamlessly and provide a realistic user experience.
5G Networks
5G networks are the next generation of wireless communication technology, offering faster speeds, lower latency, and higher capacity than previous generations. Networking concepts, such as network slicing, virtualization, and edge computing, are essential in enabling 5G networks to deliver on their promises of faster and more reliable communication.
In conclusion, networking concepts are essential in enabling various real-world applications to function effectively. By understanding the principles and practices that govern the design, implementation, and management of computer networks, professionals can leverage networking concepts to optimize the performance, security, and reliability of modern technologies.
Conclusion: The Future of Networking Concepts
Networking concepts have come a long way since the early days of computer networking. Today, networking concepts are more critical than ever, with the rise of cloud computing, IoT, edge computing, and other emerging technologies. Understanding networking concepts is essential for effective communication, data sharing, and security in a connected world.
As we look to the future, we can expect to see continued innovation and development in networking technologies. Software-defined networking (SDN) and network function virtualization (NFV) are poised to revolutionize network design and management, offering greater flexibility, scalability, and cost-effectiveness. Meanwhile, 5G networks promise to deliver faster speeds, lower latency, and higher capacity than ever before, enabling new applications and services in industries such as healthcare, manufacturing, and transportation.
However, these emerging technologies also present new challenges and risks. As networks become more complex and distributed, securing them becomes more difficult. Network administrators must stay up-to-date with the latest threats and vulnerabilities and implement best practices for network security and management. Access control, intrusion detection, network segmentation, and disaster recovery planning are all critical components of a robust network security strategy.
In conclusion, networking concepts are at the heart of modern computing and communication. By understanding the principles and practices that govern the design, implementation, and management of computer networks, professionals can leverage networking concepts to optimize the performance, security, and reliability of modern technologies. As we look to the future, we can expect to see continued innovation and development in networking technologies, along with new challenges and opportunities for network administrators and professionals.