Understanding Kubernetes ConfigMaps and Their Purpose
Kubernetes ConfigMaps are essential resources designed to decouple configuration details from application code. They serve as a centralized repository for storing configuration data, enabling applications to access this information without requiring modifications to the application’s image itself. The primary role of a ConfigMap is to inject configuration data into Pods, either as environment variables, command-line arguments, or files within a container’s filesystem. This approach avoids hardcoding configuration directly into container images, which promotes greater flexibility and portability. Using ConfigMaps to mount configmap as file offers several advantages, including simplified configuration management, easier updates, and improved application reusability across different environments.
The benefits of adopting ConfigMaps extend to streamlined deployments and enhanced operational efficiency. When configuration changes are needed, updating a ConfigMap is far simpler and faster than rebuilding and redeploying container images. This separation of concerns allows developers to focus on application logic while operations teams manage configuration settings independently. Furthermore, ConfigMaps facilitate environment-specific configurations. The same application image can be deployed across development, testing, and production environments, each with its own tailored configuration managed through separate ConfigMaps. By enabling the mount configmap as file strategy, the data is available directly within the container’s filesystem. This reduces the complexity of retrieving configuration data and makes application management more straightforward.
ConfigMaps address a significant problem in containerized environments: the difficulty of managing configuration that changes over time or varies across different deployments. Without ConfigMaps, developers often resort to hardcoding configuration values, which leads to inflexible and difficult-to-maintain applications. Using ConfigMaps, particularly when choosing to mount configmap as file, applications can dynamically access configuration data at runtime, adapting to different environments without requiring code changes. This separation of configuration from code not only simplifies development but also significantly improves the overall manageability and scalability of Kubernetes deployments, making ConfigMaps a cornerstone of modern cloud-native application architecture.
The Power of Externalized Configuration in Containerized Applications
Externalized configuration plays a pivotal role in the effective management of containerized applications. It offers a powerful approach to decouple application settings from the application’s core code. This separation promotes greater portability, reusability, and simplifies the update process. When you mount configmap as file, the configuration resides outside the container image, enabling the same image to be deployed across diverse environments without modification.
Managing configuration independently of the application lifecycle yields several advantages. Updating configuration parameters becomes straightforward. Changes can be applied without rebuilding or redeploying the entire application. This agility is particularly useful in dynamic environments where configuration adjustments are frequent. Moreover, externalized configuration facilitates easier rollbacks and versioning. If a new configuration introduces issues, reverting to a previous, stable version is a simple operation. This capability significantly reduces the risk associated with configuration changes and enhances the overall stability of the application. To mount configmap as file provides agility and control.
The practice of externalizing configuration addresses key challenges in containerized environments. By avoiding hardcoding configuration values directly into container images, it promotes consistency and reduces the potential for errors. Different environments, such as development, testing, and production, often require varying configurations. With externalized configuration, you can easily tailor the application’s behavior to each environment by simply providing a different set of configuration values. The ability to mount configmap as file allows for easy changes. Furthermore, this approach simplifies collaboration among development, operations, and security teams. Configuration data can be managed and updated separately from the application code, enabling teams to work independently and efficiently. This streamlined workflow accelerates the development and deployment process while improving the overall quality and reliability of the application. When you mount configmap as file, you are optimizing the containerized configuration management. The benefits of externalization highlight the importance of tools like ConfigMaps in modern application deployments. For example, you can mount configmap as file to enhance versioning of your data or configurations.
How to Expose ConfigMap Data as Files within Pods
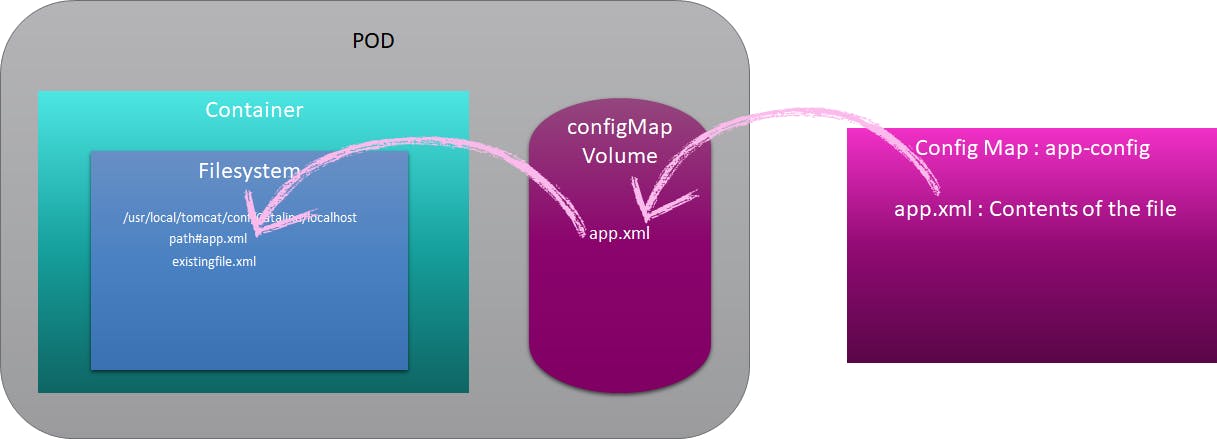
To effectively leverage Kubernetes ConfigMaps for file integration, understanding how to expose ConfigMap data as files within Pods is crucial. This involves configuring the Pod’s specification to mount the ConfigMap as a volume. The `volumeMounts` section dictates where the ConfigMap’s data will be accessible inside the container, while the `volumes` section defines the ConfigMap to be mounted. This method allows applications to read configuration data directly from files, simplifying access and management.
The process to mount configmap as file entails modifying the Pod’s YAML definition. The `volumes` section defines a volume, specifying the ConfigMap as its source. The `volumeMounts` section within a container definition then links this volume to a specific path. Any key-value pair in the ConfigMap is then represented as a separate file within this mounted path. Let’s examine the YAML code to mount configmap as file:
Creating a Sample ConfigMap for File Integration
To effectively demonstrate how to mount configmap as file, it’s crucial to first create a ConfigMap. Kubernetes offers several ways to accomplish this, including creating a ConfigMap from literal values directly within the command line or importing data from existing files. The `kubectl create configmap` command is the primary tool for these operations. ConfigMaps fundamentally store configuration data as key-value pairs; when you mount configmap as file, these key-value pairs become the contents of the file within the Pod.
For instance, to create a ConfigMap named “my-config” from literal values, you can use the following command: `kubectl create configmap my-config –from-literal=setting1=”value1″ –from-literal=setting2=”value2″`. This command creates a ConfigMap with two key-value pairs: “setting1” with the value “value1,” and “setting2” with the value “value2.” Alternatively, if you have existing configuration files, you can create a ConfigMap from them. For example, if you have a file named `application.properties`, the command `kubectl create configmap my-config –from-file=application.properties` will create a ConfigMap where the contents of `application.properties` are stored under the key `application.properties`. When you mount configmap as file, the file name serves as the key.
When you mount configmap as file, Kubernetes makes each key-value pair accessible as a separate file within the specified mount path. Therefore, in the first example, if you mount “my-config” to a directory `/config`, you would find two files within that directory: `/config/setting1` containing “value1” and `/config/setting2` containing “value2.” Similarly, in the second example, you would find `/config/application.properties` containing the content of your original `application.properties` file. This mechanism to mount configmap as file provides a straightforward way to inject configuration data into your applications without modifying the container image. Understanding how ConfigMaps store data and how this data translates into files when mounted is essential for effective configuration management in Kubernetes. Ensure that the filenames and directory structures within the ConfigMap align with your application’s expectations when you mount configmap as file.
Verifying Successful Mount and File Access Inside the Pod
To confirm that the ConfigMap is successfully mounted as a file within the Pod, utilize `kubectl exec` to gain access to the Pod’s shell. This command allows you to execute commands directly inside the running container. First, identify the name of the Pod. Then, use the following command structure, replacing `[pod-name]` with the actual Pod name:
kubectl exec -it [pod-name] -- /bin/bash
Once inside the Pod’s shell, navigate to the mount path specified in the Pod’s YAML definition. This path indicates where the ConfigMap data should be available as a file. For example, if the `volumeMount` configuration defined the mount path as `/etc/config`, use the `cd` command to change the directory:
cd /etc/config
Now, inspect the contents of the mounted file. The filename will correspond to the key in the ConfigMap. For instance, if the ConfigMap contained a key named `myconfig.txt`, a file with that name should exist in the mount path. Use the `cat` command to display the file’s contents:
cat myconfig.txt
The output should display the value associated with the `myconfig.txt` key in the ConfigMap. If the file contains the expected configuration data, the ConfigMap has been successfully mounted as a file. Another command to use will be:
ls -l
That will show the files under the directory. If problems are encounterd during the process to mount configmap as file, double check the volumeMounts specifications in the pod’s YAML to ensure that the mountPath is correctly specified. Also ensure that the configmap you are referencing exist within the namespace. If you can’t mount configmap as file, verify that the pod has the right permissions to access the configmap.
Best Practices for Managing ConfigMaps in Kubernetes
Effective management of ConfigMaps is crucial for maintaining a robust and secure Kubernetes environment. When you mount configmap as file, versioning becomes an important consideration. Kubernetes itself does not provide built-in ConfigMap versioning, but strategies can be implemented to track changes. One approach is to incorporate version numbers directly into the ConfigMap names (e.g., `my-config-v1`, `my-config-v2`). This allows for easy rollback to previous configurations if needed. Another method involves using Git to manage ConfigMap YAML definitions, providing a full audit trail of changes.
Security is paramount when dealing with configuration data. While ConfigMaps themselves are not inherently secure, sensitive information should never be stored directly within them. Instead, leverage Kubernetes Secrets to manage passwords, API keys, and other confidential data. A common pattern is to store references to Secrets within ConfigMaps, allowing your application to retrieve the sensitive information at runtime. Furthermore, consider using immutable ConfigMaps. Once created, immutable ConfigMaps cannot be modified, preventing accidental or malicious changes to the configuration. This feature, introduced in Kubernetes 1.19, enhances the stability and reliability of your deployments. To create an immutable ConfigMap, set the `immutable: true` field in the ConfigMap’s YAML definition. When you mount configmap as file, ensure that proper access controls are in place to restrict which Pods and users can access the ConfigMap data.
Updating ConfigMaps without restarting Pods is another key aspect of efficient management. While Kubernetes automatically updates mounted ConfigMaps, the changes are not immediately reflected in running applications unless they are designed to watch for ConfigMap updates. Tools like `Reloader` can automate the process of restarting Deployments or DaemonSets when a ConfigMap changes, ensuring that the updated configuration is applied. Another option is to use a sidecar container that monitors ConfigMap changes and signals the main application process to reload its configuration. This approach allows for seamless updates without downtime. When you mount configmap as file and need to update it, remember that simply changing the ConfigMap does not automatically propagate those changes to the application unless you have implemented a mechanism to detect and react to those changes. Remember to carefully plan your ConfigMap update strategy to minimize disruption to your applications.
Exploring Alternative Configuration Management Techniques
Kubernetes offers diverse methods for configuration management, extending beyond the “mount configmap as file” approach. While ConfigMaps effectively decouple configuration data, other tools cater to specific needs. Secrets, for instance, are designed to manage sensitive information like passwords and API keys. They encrypt data at rest, adding a crucial layer of security. Unlike ConfigMaps, which store data as plain text, Secrets provide a safer way to handle credentials. When security is paramount, Secrets are the preferred choice over attempting to “mount configmap as file” for sensitive data.
Helm charts provide another powerful alternative. They package applications into deployable units, including all necessary configurations and dependencies. Helm allows for templating configuration files, enabling customization during deployment. This is particularly useful for complex applications with numerous configuration options. Operators, a more advanced technique, automate the management of applications and their configurations. They can handle tasks such as scaling, upgrades, and backups, reducing the operational burden. Operators are ideal for stateful applications or those requiring custom management logic. While you can “mount configmap as file” with Helm, the tool also supports dynamically generated configuration files.
Tools like Kustomize facilitate customizing Kubernetes configurations without modifying the original YAML files. Kustomize employs a declarative approach, allowing users to define overlays that modify the base configuration. This simplifies managing different environments (e.g., development, staging, production) with varying configurations. Selecting the right configuration management technique depends on the application’s complexity, security requirements, and operational needs. While “mount configmap as file” offers simplicity, consider Secrets for sensitive data, Helm for complex deployments, and Operators for automated management. Each approach complements the Kubernetes ecosystem, empowering developers to effectively manage their applications’ configurations. Sometimes, a hybrid strategy, incorporating multiple techniques, provides the optimal solution.
Troubleshooting Common Issues When Mounting ConfigMaps as Files
When attempting to mount configmap as file, several issues can arise. One common problem involves incorrect `volumeMount` configurations within the Pod’s YAML file. Double-check the `mountPath` to ensure it exists and is writable by the container’s process. Verify that the `name` field in the `volumeMounts` section corresponds to the `name` defined in the `volumes` section. A mismatch here will prevent the configmap from being properly mounted as file. If you encounter an error message like “mount: permission denied”, it indicates a permission issue. This could mean the user running the container process does not have sufficient privileges to write to the specified `mountPath`. Adjusting the security context of the pod or the permissions of the directory can resolve this. Another issue might be a missing or incorrectly named ConfigMap. Kubernetes is case-sensitive, so ensure the ConfigMap name in the Pod’s YAML matches the actual ConfigMap name. Use `kubectl get configmaps` to confirm the ConfigMap exists and to verify its name. If the ConfigMap data is empty or contains unexpected values, the mounted file will reflect these inconsistencies. Inspect the ConfigMap contents using `kubectl describe configmap
Another frequent error occurs when the Pod attempts to access a ConfigMap that doesn’t exist or isn’t yet available. This often manifests as the file being empty or the container failing to start. Ensure the ConfigMap is created before the Pod attempts to mount configmap as file. Consider using init containers to wait for the ConfigMap to become available before the main application container starts. Examine the Pod’s events using `kubectl describe pod
Immutable ConfigMaps, introduced in recent Kubernetes versions, can lead to unexpected behavior if updates are attempted. Once marked as immutable, a ConfigMap cannot be modified. If your application expects the ConfigMap to be updated dynamically, ensure it’s not configured as immutable. Trying to update an immutable ConfigMap will result in an error. To address issues when you mount configmap as file, carefully review the Pod’s YAML definition, verify the ConfigMap’s existence and content, and check for permission problems. Thoroughly examining error messages and Pod events will guide you toward the root cause of the problem. Remember to test your configuration changes in a non-production environment before deploying them to production to minimize disruption.