What is Microsoft Azure Key Vault?
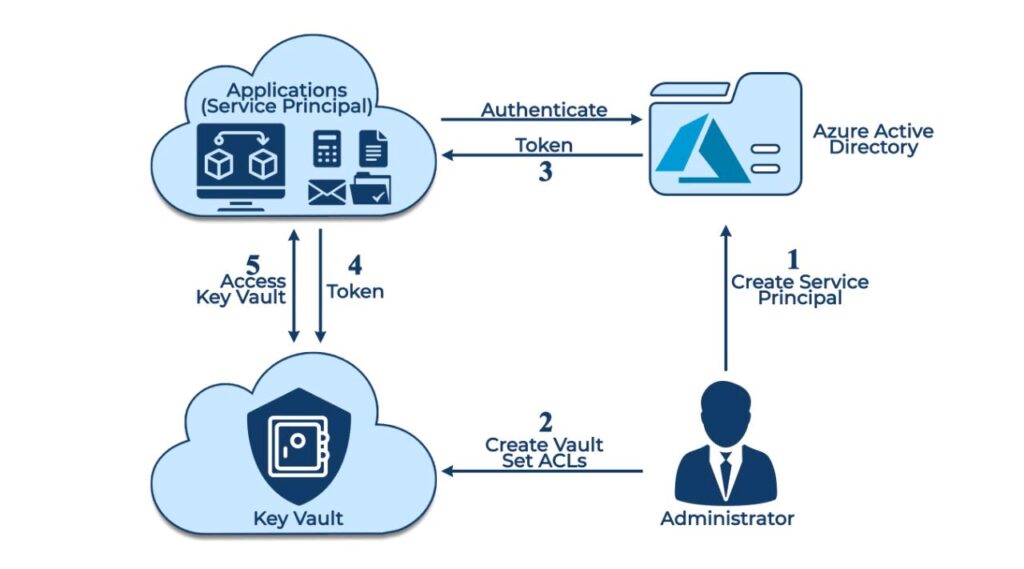
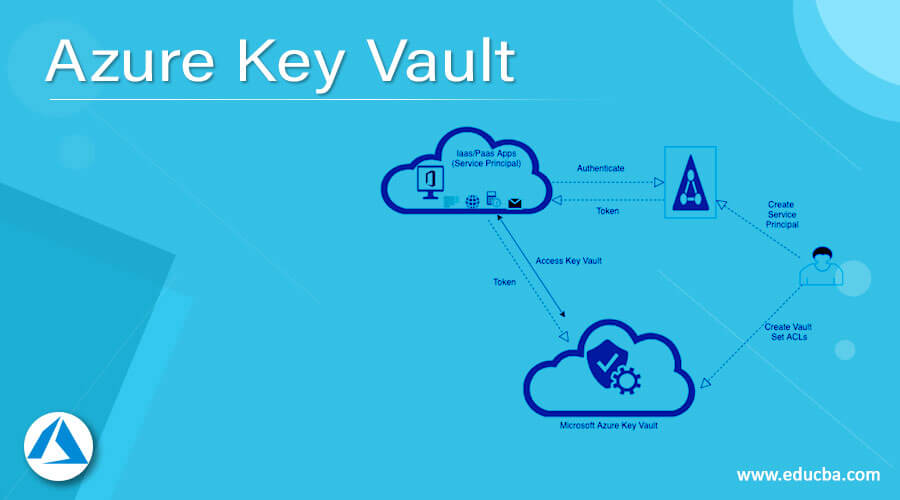
Microsoft Azure Key Vault is a cloud-based service that offers secure storage for keys, secrets, and certificates. As a crucial component of Azure’s security fabric, Key Vault enables organizations to safeguard sensitive data and streamline key management tasks. By centralizing the storage and management of cryptographic keys, Key Vault helps organizations meet compliance requirements and minimize the risk of data breaches.
Key Features and Benefits of Azure Key Vault
Microsoft Azure Key Vault offers a wide range of features and benefits that contribute to enhanced security and regulatory compliance for organizations. The service simplifies key management tasks and provides a centralized location for storing and managing cryptographic keys, secrets, and certificates.
One of the main features of Azure Key Vault is encryption, which ensures that data remains confidential both at rest and in transit. By using encryption, organizations can protect sensitive information from unauthorized access and safeguard their digital assets.
Access control is another crucial feature of Azure Key Vault. The service enables organizations to define and manage access policies, ensuring that only authorized users and applications can access stored keys and secrets. This level of control helps organizations maintain their security posture and prevent unauthorized access to sensitive data.
Auditing is also a key benefit of Azure Key Vault. The service provides detailed logs and reports, enabling organizations to track and monitor access to stored keys and secrets. This level of visibility is essential for maintaining regulatory compliance and identifying potential security threats.
By leveraging these features, organizations can simplify key management tasks, reduce the risk of data breaches, and maintain regulatory compliance. Azure Key Vault offers a robust and secure solution for managing cryptographic keys, secrets, and certificates, making it an ideal choice for organizations of all sizes and industries.
How to Implement Azure Key Vault in Your Organization
Implementing Azure Key Vault in your organization involves several steps, including creating a vault, configuring access policies, and integrating it with applications. To get started, follow these steps:
- Create a vault: To create a new vault, navigate to the Azure Key Vault service in the Azure portal and click on the “Add” button. Provide a name for the vault, select a subscription, create a new resource group or select an existing one, and choose a location. Once you have provided all the necessary information, click on the “Create” button to create the vault.
- Configure access policies: Access policies define who can access the vault and what permissions they have. To configure access policies, navigate to the “Access policies” section of the vault and click on the “Add access policy” button. Select the user or group you want to grant access to, and then select the permissions you want to grant. Once you have configured the access policy, click on the “Add” button to save your changes.
- Integrate with applications: Azure Key Vault can be integrated with applications using the Azure Key Vault SDK or REST API. To integrate with an application, first, install the Azure Key Vault SDK in your development environment. Then, authenticate your application with Azure Active Directory and create a Key Vault client. Once you have created the client, you can use it to interact with the vault, such as storing and retrieving keys, secrets, and certificates.
- Storing encryption keys for databases: Many organizations use Azure Key Vault to store encryption keys for their databases. By storing the keys in Azure Key Vault, organizations can ensure that their data is encrypted at rest and in transit, and that only authorized users and applications can access it.
- Managing API keys: Azure Key Vault can be used to manage API keys for web applications and services. By storing the API keys in Azure Key Vault, organizations can ensure that only authorized applications and users can access the APIs, and that the keys are rotated regularly to prevent unauthorized access.
- Securing access to cloud resources: Azure Key Vault can be used to secure access to cloud resources, such as virtual machines and storage accounts. By using Azure Key Vault to manage the keys and secrets required to access these resources, organizations can ensure that only authorized users and applications can access them, and that the keys and secrets are rotated regularly to prevent unauthorized access.
- Regulatory compliance: Azure Key Vault can help organizations achieve regulatory compliance by providing a secure and auditable storage solution for keys, secrets, and certificates. By using Azure Key Vault, organizations can demonstrate to auditors that they are following best practices for key management and that they have controls in place to prevent unauthorized access to sensitive data.
- AWS Key Management Service (KMS): AWS KMS is a cloud-based key management service that provides encryption keys for AWS services. While KMS is a powerful service, it is limited to AWS services and does not provide the same level of integration with non-AWS applications and services as Azure Key Vault. Additionally, KMS does not provide the same level of access control and auditing capabilities as Azure Key Vault.
- Google Cloud KMS: Google Cloud KMS is a cloud-based key management service that provides encryption keys for Google Cloud services. Like AWS KMS, Google Cloud KMS is limited to Google Cloud services and does not provide the same level of integration with non-Google Cloud applications and services as Azure Key Vault. Additionally, Google Cloud KMS does not provide the same level of access control and auditing capabilities as Azure Key Vault.
- Integration with existing applications and services: Ensure that the key management solution integrates with your existing applications and services. Azure Key Vault provides a wide range of integration options, including REST API, SDKs, and PowerShell cmdlets.
- Access control and auditing capabilities: Look for a key management solution that provides robust access control and auditing capabilities. Azure Key Vault provides fine-grained access control and detailed auditing capabilities, making it an ideal choice for organizations that need to meet regulatory compliance requirements.
- Pricing: Consider the pricing structure of the key management solution. Azure Key Vault provides a flexible pricing structure that allows organizations to choose the right plan based on their needs and budget.
- Scalability: Ensure that the key management solution can scale to meet the needs of your organization. Azure Key Vault provides scalability options that allow organizations to handle large volumes of keys and secrets.
- Implement multi-factor authentication: Multi-factor authentication (MFA) provides an additional layer of security by requiring users to provide two or more forms of authentication. By enabling MFA for Azure Key Vault, you can prevent unauthorized access to your keys and secrets.
- Monitor access logs: Azure Key Vault provides detailed access logs that track who is accessing your keys and secrets and what actions they are performing. By regularly monitoring access logs, you can detect and respond to suspicious activity and maintain the security and integrity of your sensitive data.
- Regularly review key rotations: Regularly reviewing key rotations ensures that your keys are up-to-date and secure. Azure Key Vault provides key rotation capabilities that allow you to automatically rotate your keys on a regular basis.
- Use hardware security modules (HSMs): HSMs provide a high level of security by storing keys in a hardware device that is tamper-resistant and physically isolated. By using HSMs with Azure Key Vault, you can ensure that your keys are stored in a secure and tamper-proof environment.
- Limit access to keys and secrets: Limit access to your keys and secrets to only those users and applications who need it. Azure Key Vault provides access control capabilities that allow you to define who can access your keys and secrets and what actions they can perform.
- Use private endpoints: Private endpoints provide a secure and private connection to Azure Key Vault. By using private endpoints, you can prevent unauthorized access to your keys and secrets and ensure that only authorized users and applications can access them.
- Operations: Azure Key Vault charges for the number of operations performed, such as key creations, deletions, and retrievals. The pricing is based on the number of operations per month and varies based on the region.
- Storage: Azure Key Vault charges for the amount of storage used to store keys, secrets, and certificates. The pricing is based on the amount of storage per month and varies based on the region.
- Transactions: Azure Key Vault charges for the number of transactions performed, such as get, set, and delete operations. The pricing is based on the number of transactions per month and varies based on the region.
- Key Vault Hierarchy: Azure Key Vault supports a hierarchical structure that allows you to organize keys and secrets into logical groups. By organizing keys and secrets into hierarchies, you can improve performance and reduce latency.
- Geo-Replication: Azure Key Vault supports geo-replication, which allows you to replicate keys and secrets across multiple regions. By replicating keys and secrets, you can ensure high availability and disaster recovery.
- Azure Key Vault Managed HSMs: Azure Key Vault Managed HSMs provide a high level of security by storing keys in hardware security modules (HSMs) that are FIPS 140-2 Level 2 certified. By using Managed HSMs, you can ensure that your keys are stored in a secure and tamper-proof environment.
- Number of operations: Consider the number of operations you will be performing and choose a plan that meets your needs.
- Amount of storage: Consider the amount of storage you will need and choose a plan that provides sufficient storage.
- Number of transactions: Consider the number of transactions you will be performing and choose a plan that provides sufficient transactions.
- Scalability requirements: Consider your scalability requirements and choose a plan that provides the necessary scalability options.
When implementing Azure Key Vault, there are several best practices to keep in mind. First, ensure that you follow the principle of least privilege when configuring access policies. Only grant the minimum permissions necessary to perform a task. Second, regularly review access logs to monitor for suspicious activity. Third, enable soft delete and purge protection to prevent accidental deletion of keys, secrets, and certificates. Fourth, use Azure Policy to enforce compliance with organizational standards and regulations.
By following these steps and best practices, you can successfully implement Azure Key Vault in your organization and take advantage of its key management features. With Azure Key Vault, you can simplify key management tasks, reduce the risk of data breaches, and maintain regulatory compliance.
Real-World Applications of Azure Key Vault
Azure Key Vault is a versatile service that can be used in a variety of industries and scenarios. Here are some examples of how organizations are using Azure Key Vault to secure their sensitive data and simplify key management:
These are just a few examples of how Azure Key Vault is being used in the real world. By providing a secure and centralized solution for key management, Azure Key Vault can help organizations of all sizes and industries protect their sensitive data and simplify key management tasks.
Comparing Azure Key Vault with Other Key Management Solutions
When it comes to key management solutions, there are several options available in the market, including Azure Key Vault, AWS Key Management Service (KMS), and Google Cloud KMS. While all three services provide key management capabilities, there are some differences in terms of features, pricing, and use cases. Here’s a comparison of Azure Key Vault with other key management solutions:
When choosing a key management solution, it’s essential to consider the following factors:
In summary, while there are several key management solutions available in the market, Azure Key Vault stands out due to its wide range of integration options, robust access control and auditing capabilities, flexible pricing structure, and scalability options. By choosing Azure Key Vault, organizations can simplify key management tasks, reduce the risk of data breaches, and maintain regulatory compliance.
Security Best Practices for Using Azure Key Vault
Azure Key Vault is a powerful service that provides secure storage of keys, secrets, and certificates. However, to ensure the security and integrity of your sensitive data, it’s essential to follow best practices when using Azure Key Vault. Here are some security best practices to keep in mind:
By following these security best practices, you can ensure the security and integrity of your sensitive data and maintain regulatory compliance. Additionally, by using Azure Key Vault in conjunction with other security services, such as Azure Security Center and Azure Active Directory, you can further enhance the security posture of your organization.
Pricing and Scalability of Azure Key Vault
Azure Key Vault offers flexible pricing and scalability options to meet the needs of organizations of all sizes. Here’s an overview of the pricing structure and scalability options of Azure Key Vault:
Pricing Structure
Azure Key Vault uses a pay-as-you-go pricing model based on the number of operations performed and the amount of storage used. The pricing structure includes the following components:
Scalability Options
Azure Key Vault provides scalability options to meet the needs of organizations with large volumes of keys and secrets. Here are some scalability options to consider:
When choosing a pricing plan for Azure Key Vault, consider the following factors:
By choosing the right pricing plan and scalability options, you can ensure that Azure Key Vault meets the needs of your organization and provides a secure and cost-effective solution for key management.
Overcoming Challenges and Limitations of Azure Key Vault
While Azure Key Vault is a powerful and feature-rich key management service, it does have some limitations and challenges that organizations should be aware of. Here are some common challenges and limitations of Azure Key Vault and how to overcome them:
Vendor Lock-In
One of the challenges of using Azure Key Vault is the risk of vendor lock-in. Once you have stored your keys and secrets in Azure Key Vault, it can be difficult to migrate to another key management service. To mitigate this risk, consider using open standards and APIs, such as the Key Management Interoperability Protocol (KMIP) and the Cryptography API: Next Generation (CNG), to ensure interoperability with other key management services.
Data Residency
Another challenge of using Azure Key Vault is data residency. Depending on your organization’s regulations and compliance requirements, you may need to store your keys and secrets in a specific geographic location. To address this issue, Azure Key Vault provides geo-replication and regional availability options to ensure that your keys and secrets are stored in the location that meets your requirements.
Integration with Legacy Systems
Integrating Azure Key Vault with legacy systems can be a challenge, especially if those systems do not support modern key management protocols and APIs. To overcome this issue, consider using a key management gateway or bridge that can translate between legacy protocols and APIs and the Key Vault REST API.
Limited HSM Capacity
Azure Key Vault Managed HSMs have a limited capacity, which may not be sufficient for organizations with large volumes of keys and secrets. To address this issue, consider using Azure Key Vault’s bring-your-own-key (BYOK) feature, which allows you to import your own HSMs into Azure Key Vault.
Cost
The cost of using Azure Key Vault can add up quickly, especially if you have large volumes of keys and secrets or if you perform a high number of operations. To manage costs, consider using Azure Key Vault’s cost management features, such as usage quotas and alerts, to monitor and control your usage.
By understanding and addressing these challenges and limitations, organizations can effectively use Azure Key Vault to secure their keys and secrets and simplify key management. Additionally, by following best practices and staying up-to-date with the latest features and updates, organizations can ensure that they are getting the most value and security out of Azure Key Vault.