Microsoft Azure Entra: A Powerful Identity and Access Management Solution
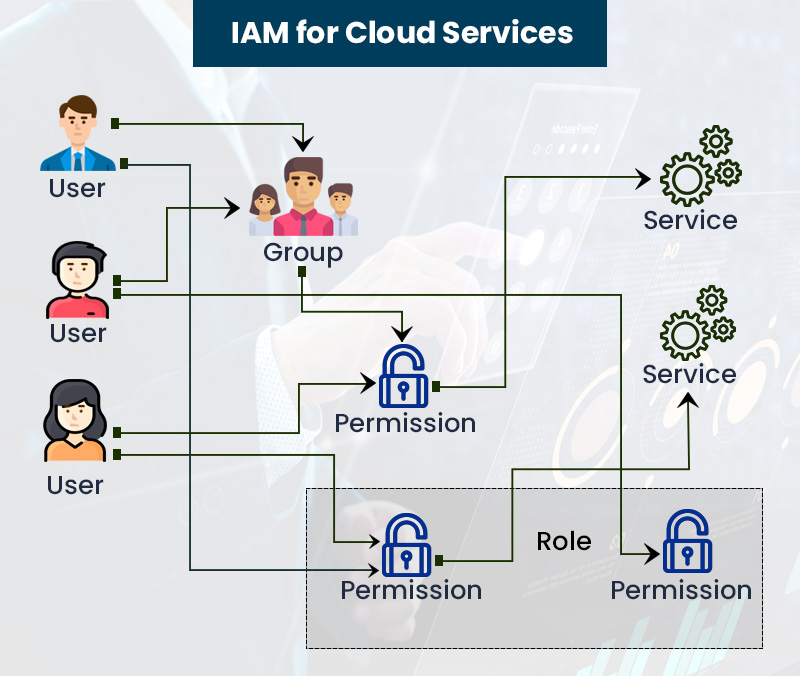
Microsoft Azure Entra is an advanced identity and access management (IAM) solution designed for modern cloud-based environments. Its primary role is to simplify identity management, enhance security, and improve user experience. With Azure Entra, organizations can manage access to various resources, applications, and services more efficiently and securely. The solution is built on a foundation of robust components, such as Azure Active Directory, Azure AD Connect, and Azure AD Identity Protection, which work together to provide a comprehensive IAM strategy.
Key Capabilities and Components of Microsoft Azure Entra
Microsoft Azure Entra is a versatile IAM solution that comprises several key components, each contributing to a comprehensive identity and access management strategy. The primary components include Azure Active Directory (Azure AD), Azure AD Connect, and Azure AD Identity Protection. These components work together to provide a seamless and secure user experience while simplifying identity management for organizations.
Azure Active Directory (Azure AD)
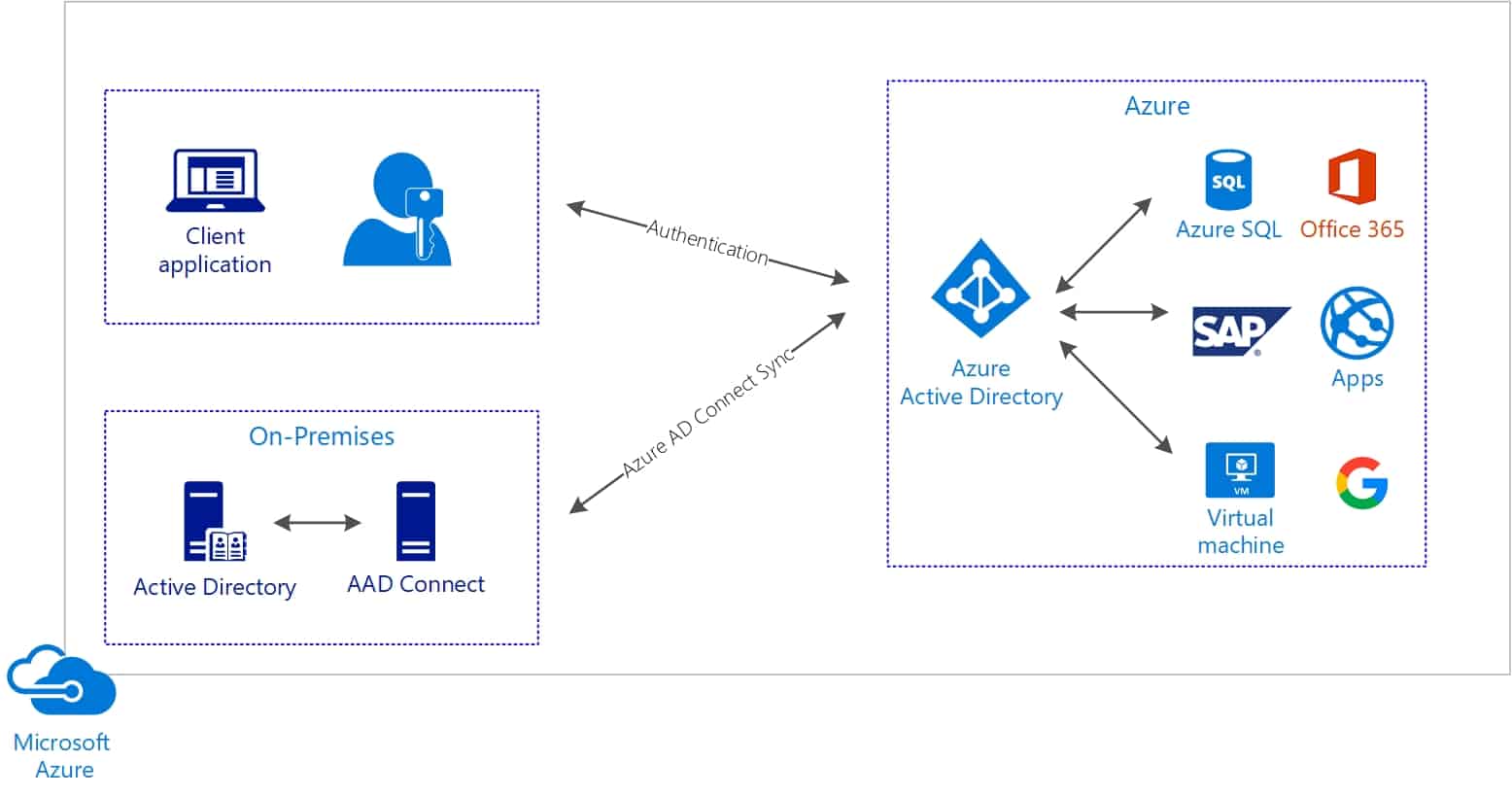
Azure AD is a cloud-based directory and identity management service that combines core directory services, advanced identity governance, and application access management. It simplifies identity management by providing a single identity platform for both on-premises and cloud applications, enabling users to sign in and access resources with a single set of credentials. Azure AD also offers features such as group management, self-service password reset, and conditional access, enhancing security and user experience.
Azure AD Connect
Azure AD Connect is a tool that enables organizations to connect their on-premises Active Directory (AD) to Azure AD, allowing for seamless identity synchronization between the two environments. By synchronizing user and group accounts, organizations can provide a consistent identity experience across both on-premises and cloud-based resources. Azure AD Connect also supports features such as password hash synchronization, pass-through authentication, and federation, ensuring secure and flexible authentication options for users.
Azure AD Identity Protection
Azure AD Identity Protection is a cloud-based service that helps organizations detect, investigate, and respond to identity-based risks in real-time. By leveraging machine learning and large-scale telemetry, Identity Protection identifies suspicious activities, such as sign-ins from unfamiliar locations or impossible travel, and calculates user risk levels. Organizations can then configure policies to automatically respond to detected risks, further enhancing security and minimizing the potential for unauthorized access and data breaches.
How to Implement Microsoft Azure Entra in Your Organization
Implementing Microsoft Azure Entra in your organization involves several steps, from prerequisites and planning to configuration and deployment. By following best practices and real-world examples, you can ensure a smooth and successful implementation process.
Prerequisites and Planning
Before implementing Azure Entra, ensure that you have a clear understanding of your organization’s identity and access management requirements. Identify the applications, services, and resources that will be integrated with Azure Entra, and assess the current on-premises identity infrastructure. Additionally, consider factors such as user base, geographical distribution, and compliance requirements.
Configuration and Deployment
Once you have completed the planning phase, proceed with configuring and deploying Azure Entra. This process typically involves the following steps:
- Setting up Azure AD: Create and configure an Azure AD tenant, and connect it to your on-premises AD using Azure AD Connect.
- Configuring single sign-on (SSO): Implement SSO for cloud applications and services, allowing users to sign in with a single set of credentials.
- Implementing multi-factor authentication (MFA): Enhance security by requiring users to provide a second form of authentication when signing in from unfamiliar locations or devices.
- Setting up conditional access policies: Define and enforce access policies based on user risk levels, location, and device compliance.
- Monitoring and optimizing: Continuously monitor Azure Entra for potential issues and fine-tune configurations to maintain a secure and efficient identity and access management system.
Real-World Examples and Best Practices
When implementing Azure Entra, consider the following best practices:
- Start small: Begin by integrating a few pilot applications and gradually expand the scope of integration to minimize risks and ensure a smooth deployment process.
- Leverage automation: Use Azure AD Connect’s automation features to simplify the configuration and deployment process.
- Train users and administrators: Provide training and resources to help users and administrators understand and utilize Azure Entra’s features effectively.
- Monitor and optimize: Continuously monitor Azure Entra for potential issues and fine-tune configurations to maintain a secure and efficient identity and access management system.
Securing Your Organization with Azure Entra’s Advanced Features
Microsoft Azure Entra offers advanced security features that can help organizations protect themselves from unauthorized access and data breaches. By leveraging these features, you can enhance your organization’s security posture and ensure a more secure identity and access management strategy.
Conditional Access
Conditional access is a powerful feature that enables organizations to define and enforce access policies based on user risk levels, location, and device compliance. By setting up conditional access policies, you can ensure that only authorized users can access specific resources, minimizing the risk of unauthorized access and data breaches.
Multi-Factor Authentication (MFA)
MFA is a security mechanism that requires users to provide a second form of authentication when signing in from unfamiliar locations or devices. By implementing MFA, you can add an extra layer of security to your identity and access management strategy, ensuring that even if a user’s credentials are compromised, attackers cannot easily gain access to sensitive resources.
Privileged Identity Management
Privileged identity management (PIM) is a feature that allows organizations to manage, control, and monitor access to sensitive resources. By assigning just-in-time (JIT) and just-enough-access (JEA) privileges, you can minimize the risk of privilege abuse and ensure that users only have the access they need, when they need it. PIM also provides visibility into user activities, enabling organizations to detect and respond to potential security threats more effectively.
Real-World Examples and Best Practices
When implementing Azure Entra’s advanced security features, consider the following best practices:
- Start with a risk assessment: Evaluate your organization’s risk levels and prioritize the implementation of advanced security features based on your specific needs and requirements.
- Implement MFA for all users: Require MFA for all users, especially those with administrative privileges, to minimize the risk of unauthorized access and data breaches.
- Monitor and optimize: Continuously monitor Azure Entra for potential security threats and fine-tune configurations to maintain a secure and efficient identity and access management system.
- Train users and administrators: Provide training and resources to help users and administrators understand and utilize Azure Entra’s advanced security features effectively.
Integrating Azure Entra with Other Microsoft Services and Third-Party Applications
Microsoft Azure Entra is designed to integrate seamlessly with other Microsoft services and popular third-party applications, enabling organizations to create a cohesive and secure digital ecosystem. By integrating Azure Entra with various services and applications, you can enhance productivity, streamline workflows, and improve user experience.
Integration with Microsoft Services
Azure Entra can be integrated with various Microsoft services, such as Microsoft 365, Dynamics 365, and Power Platform. By integrating Azure Entra with these services, you can provide a consistent and secure identity and access management experience across your organization’s Microsoft applications and services.
- Microsoft 365: Simplify identity management for Microsoft 365 applications by integrating Azure Entra with Microsoft 365. This integration enables users to sign in with a single set of credentials, improving user experience and enhancing security.
- Dynamics 365: Integrate Azure Entra with Dynamics 365 to manage user access to Dynamics 365 applications and services. By doing so, you can ensure that only authorized users can access sensitive Dynamics 365 resources, minimizing the risk of unauthorized access and data breaches.
- Power Platform: Connect Azure Entra with Power Platform to manage user access to Power Platform applications and services. This integration enables you to control user access, improve security, and enhance user experience across Power Platform applications.
Integration with Third-Party Applications
Azure Entra can also be integrated with popular third-party applications, such as Salesforce, Google Workspace, and Dropbox. By integrating Azure Entra with these applications, you can provide a consistent and secure identity and access management experience across your organization’s diverse application landscape.
- Salesforce: Integrate Azure Entra with Salesforce to manage user access to Salesforce applications and services. This integration enables you to control user access, improve security, and enhance user experience across Salesforce applications.
- Google Workspace: Connect Azure Entra with Google Workspace to manage user access to Google Workspace applications and services. By doing so, you can ensure that only authorized users can access sensitive Google Workspace resources, minimizing the risk of unauthorized access and data breaches.
- Dropbox: Integrate Azure Entra with Dropbox to manage user access to Dropbox applications and services. This integration enables you to control user access, improve security, and enhance user experience across Dropbox applications.
Real-World Examples and Best Practices
When integrating Azure Entra with other Microsoft services and third-party applications, consider the following best practices:
- Plan ahead: Before integrating Azure Entra with other services and applications, ensure that you have a clear understanding of your organization’s requirements and objectives. Plan the integration process carefully to minimize risks and ensure a smooth deployment process.
- Leverage automation: Use Azure Entra’s automation features to simplify the integration process and minimize the risk of errors and inconsistencies.
- Monitor and optimize: Continuously monitor Azure Entra for potential issues and fine-tune configurations to maintain a secure and efficient identity and access management system.
- Train users and administrators: Provide training and resources to help users and administrators understand and utilize Azure Entra’s integration features effectively.
Comparing Azure Entra with Other Identity and Access Management Solutions
When choosing an identity and access management solution, it’s essential to compare various options and evaluate their unique selling points, features, pricing, and scalability. In this context, let’s compare Microsoft Azure Entra with other popular identity and access management solutions, such as Okta, OneLogin, and Duo Security.
Azure Entra vs. Okta
Both Azure Entra and Okta offer robust identity and access management features, but they differ in terms of pricing, integration capabilities, and target audience. Azure Entra is a more comprehensive solution that includes Azure Active Directory, Azure AD Connect, and Azure AD Identity Protection, while Okta focuses primarily on identity and access management for cloud applications.
- Pricing: Azure Entra offers more flexible pricing options, with different tiers for various features and services. Okta’s pricing is more straightforward but may not provide as much flexibility for organizations with specific requirements.
- Integration: Azure Entra offers seamless integration with other Microsoft services, such as Microsoft 365, Dynamics 365, and Power Platform. Okta, on the other hand, focuses on integration with cloud applications and may not provide as many integration options for on-premises applications and services.
- Target audience: Azure Entra is a more comprehensive solution that caters to organizations with both cloud and on-premises environments. Okta is more suitable for organizations that primarily use cloud applications and services.
Azure Entra vs. OneLogin
Like Okta, OneLogin focuses primarily on identity and access management for cloud applications. However, OneLogin offers more flexible pricing options and a more user-friendly interface than Okta.
- Pricing: OneLogin offers more flexible pricing options than Okta, with different tiers for various features and services. Azure Entra also provides flexible pricing options, making it easier for organizations to choose the right solution for their needs.
- Integration: OneLogin offers integration with various cloud applications and services, but it may not provide as many integration options for on-premises applications and services as Azure Entra.
- Target audience: OneLogin is more suitable for organizations that primarily use cloud applications and services, while Azure Entra caters to organizations with both cloud and on-premises environments.
Azure Entra vs. Duo Security
Duo Security is a popular multi-factor authentication solution that can be integrated with various identity and access management solutions, including Azure Entra. While Duo Security offers robust multi-factor authentication features, it may not provide as many identity and access management features as Azure Entra.
- Pricing: Duo Security offers flexible pricing options, with different tiers for various features and services. Azure Entra also provides flexible pricing options, making it easier for organizations to choose the right solution for their needs.
- Integration: Duo Security can be integrated with various identity and access management solutions, including Azure Entra. However, Azure Entra offers more comprehensive identity and access management features than Duo Security alone.
- Target audience: Duo Security is a multi-factor authentication solution that can be integrated with various identity and access management solutions. Azure Entra is a more comprehensive solution that caters to organizations with both cloud and on-premises environments.
Real-World Examples and Best Practices
When comparing Azure Entra with other identity and access management solutions, consider the following best practices:
- Evaluate your organization’s requirements: Before choosing an identity and access management solution, ensure that you have a clear understanding of your organization’s requirements and objectives. Evaluate each solution’s features, pricing, and scalability to determine which one is the best fit for your organization.
- Test each solution: Before making a final decision, test each solution in a controlled environment to evaluate its performance, ease of use, and integration capabilities.
- Consider the total cost of ownership: When evaluating pricing options, consider the total cost of ownership, including licensing fees, maintenance costs, and integration costs.
- Train users and administrators: Provide training and resources to help users and administrators understand and utilize each solution’s features effectively.
Monitoring and Optimizing Microsoft Azure Entra for Long-Term Success
Monitoring and optimizing your Azure Entra implementation is crucial to ensuring long-term success and maintaining a secure and efficient identity and access management system. By tracking usage, identifying potential issues, and fine-tuning configurations, you can continuously improve your Azure Entra deployment and adapt to changing business needs and requirements.
Tracking Usage
Tracking usage is essential to understanding how your organization is utilizing Azure Entra. By monitoring usage patterns, you can identify which features and services are being used the most, which ones are underutilized, and which ones may require additional training or support. Additionally, tracking usage can help you identify potential bottlenecks, optimize resource allocation, and plan for future growth.
Identifying Potential Issues
Monitoring Azure Entra for potential issues is crucial to maintaining a secure and efficient identity and access management system. By proactively identifying and addressing potential issues, you can minimize downtime, reduce the risk of data breaches, and ensure a positive user experience. Some potential issues to monitor include authentication failures, configuration changes, and security alerts.
Fine-Tuning Configurations
Fine-tuning configurations is an essential part of optimizing Azure Entra for long-term success. By continuously evaluating and adjusting configurations, you can ensure that your identity and access management system is aligned with your organization’s changing needs and requirements. Some areas to focus on when fine-tuning configurations include user access, group policies, and conditional access rules.
Tools and Techniques
There are various tools and techniques available for monitoring and optimizing Azure Entra. Some of these include Azure Monitor, Azure Advisor, and Azure Policy. Additionally, Azure Entra provides built-in monitoring and reporting features, such as Azure Active Directory’s sign-in and audit logs, that can be used to track usage, identify potential issues, and fine-tune configurations.
Real-World Examples and Best Practices
When monitoring and optimizing Azure Entra, consider the following best practices:
- Establish a monitoring and optimization plan: Before implementing Azure Entra, establish a monitoring and optimization plan that outlines your organization’s goals, objectives, and key performance indicators (KPIs). This plan should include a schedule for monitoring usage, identifying potential issues, and fine-tuning configurations.
- Use Azure Monitor and Azure Advisor: Azure Monitor and Azure Advisor can be used to monitor Azure Entra for potential issues, optimize resource allocation, and identify areas for improvement. Additionally, Azure Policy can be used to enforce compliance with organizational standards and best practices.
- Regularly review sign-in and audit logs: Regularly reviewing Azure Active Directory’s sign-in and audit logs can help you identify potential security threats, authentication failures, and configuration changes. Additionally, these logs can be used to track usage and optimize configurations.
- Provide training and support: Provide training and support to users and administrators to ensure that they understand how to use Azure Entra effectively. Additionally, provide resources and documentation to help users and administrators troubleshoot issues and optimize configurations.
Future Trends and Innovations in Identity and Access Management with Microsoft Azure Entra
As the digital landscape continues to evolve, so do the challenges and opportunities in identity and access management. Microsoft Azure Entra is well-positioned to adapt and innovate in this ever-evolving landscape, offering cutting-edge features and capabilities that address the needs of modern organizations.
Passwordless Authentication
Passwordless authentication is an emerging trend in identity and access management, offering a more secure and convenient alternative to traditional password-based authentication. Azure Entra supports passwordless authentication through features such as Microsoft Authenticator and FIDO2 security keys, enabling users to authenticate using biometric factors such as fingerprints or facial recognition.
Biometric-Based Verification
Biometric-based verification is another trend that is gaining popularity in identity and access management. Azure Entra supports biometric-based verification through features such as Azure Active Directory verifiable credentials, enabling users to prove their identity using cryptographically verifiable attributes such as driver’s licenses or passports.
AI-Driven Risk Assessment
AI-driven risk assessment is a powerful tool in identity and access management, enabling organizations to detect and respond to potential security threats in real-time. Azure Entra supports AI-driven risk assessment through features such as Azure AD Identity Protection, which uses machine learning algorithms to detect suspicious activities and anomalies.
Real-World Examples and Best Practices
When exploring the future trends and innovations in identity and access management with Azure Entra, consider the following best practices:
- Stay up-to-date with the latest features and capabilities: Azure Entra is constantly evolving, with new features and capabilities being added regularly. Stay up-to-date with the latest developments and consider how they can be leveraged to enhance your identity and access management strategy.
- Pilot new features and capabilities in a controlled environment: Before deploying new features and capabilities in a production environment, pilot them in a controlled environment to evaluate their performance, ease of use, and impact on your organization.
- Collaborate with Microsoft and other industry leaders: Collaborate with Microsoft and other industry leaders to stay informed about the latest trends and innovations in identity and access management. Participate in Microsoft’s partner programs and engage with Microsoft’s technical experts to gain insights and best practices.
- Invest in training and education: Invest in training and education to ensure that your users and administrators are up-to-date with the latest features and capabilities of Azure Entra. Provide resources and documentation to help users and administrators troubleshoot issues and optimize configurations.