Understanding the Challenges of Kubernetes Service Connectivity
Connecting Kubernetes services, particularly in distributed environments, presents significant complexities. Network configuration is crucial, but often requires meticulous planning, especially in the context of a kubernetes service connection in azure devops. Security concerns, including access control and firewalls, are paramount. Ensuring secure communication between the cluster and external systems, like Azure DevOps, is vital. Effective service discovery within the cluster and between the cluster and Azure DevOps is also essential for seamless operation. Robust and reliable solutions are necessary to guarantee smooth CI/CD pipelines and application deployments. Troubleshooting difficulties with kubernetes service connection in azure devops quickly is often vital for successful integration.
Difficulties arise from the distributed nature of Kubernetes. Coordinating communication between pods and services across nodes requires sophisticated mechanisms. Security vulnerabilities can arise if communication protocols aren’t properly secured. Maintaining high availability and reliability in a distributed environment poses constant challenges. These complexities underscore the need for a thorough understanding of both Kubernetes and Azure DevOps integration methodologies for seamless application deployments.
Issues with network latency, inconsistent DNS resolution, and authentication problems can hinder the smooth operation of deployments. Ensuring secure communication channels between Kubernetes services and Azure DevOps is crucial to prevent unauthorized access and data breaches. Effective troubleshooting and configuration management strategies are essential to overcome these hurdles and maintain smooth operation. A thorough understanding of how Azure DevOps interacts with the kubernetes service connection is critical to avoid unforeseen issues.
Azure DevOps Integration Options for Kubernetes Clusters
Integrating Kubernetes services with Azure DevOps offers numerous advantages for streamlining CI/CD pipelines and application deployments. A well-planned integration allows for the automation of complex tasks and ensures consistent, reliable deployments to the Kubernetes cluster. Several strategies support this integration, each with unique strengths. Azure Kubernetes Service (AKS) is a popular option, providing a managed Kubernetes environment within Azure. Leveraging Azure DevOps pipelines for deployment enables automation of tasks like building, testing, and deploying applications to the AKS cluster. This simplifies the overall process of deploying and managing applications on Kubernetes. The secure kubernetes service connection in azure devops enhances the overall efficiency and security of the process.
Another key aspect of this integration involves Azure Container Registry (ACR). ACR acts as a central repository for storing container images. Integrating ACR with Azure DevOps pipelines allows for seamless automated image building and deployment. This efficient storage and management of container images streamline the deployment process, further enhancing the overall efficiency of managing kubernetes services within Azure devops. By leveraging the strengths of Azure DevOps and AKS, businesses can improve the management of applications in the cloud. This integrated solution for kubernetes service connection in azure devops ensures secure and reliable delivery of software to production environments.
Moreover, the integrated use of Azure services like Azure Active Directory and Azure Key Vault enables enhanced security practices. These services provide robust identity management and secrets management solutions, which are critical for safeguarding sensitive information within the cloud infrastructure. Integrating these elements into the comprehensive kubernetes service connection in azure devops creates a robust, secure, and scalable solution for deploying and managing applications in a Kubernetes environment.
How to Establish Secure Connections Using Azure DevOps Pipelines and AKS
Establishing secure connections between Kubernetes services and Azure DevOps pipelines within an AKS cluster is crucial for robust CI/CD pipelines. This section details securing the Kubernetes service connection in Azure DevOps using best practices. Implementing robust security measures is vital for safeguarding sensitive data and preventing unauthorized access to the Kubernetes cluster. Secure communication channels are fundamental for maintaining data integrity throughout the pipeline’s deployment stages. This involves creating a secure Kubernetes service connection to enable seamless communication between your Kubernetes cluster and Azure DevOps.
A crucial initial step involves configuring service principals within Azure Active Directory. These service principals act as identities for the Kubernetes cluster, enabling authentication with Azure DevOps. Properly managing permissions using Role-Based Access Control (RBAC) is essential. Assign precise permissions to the service principal to limit access to only necessary resources within the AKS cluster. This method minimizes attack surface and keeps the Kubernetes service connection secure in Azure DevOps. Securely store sensitive credentials, such as service principal secrets. Utilizing Azure Key Vault is highly recommended to safeguard these secrets. This approach prevents exposure of credentials within code and promotes secure access management for the Kubernetes service connection in Azure DevOps. Ensure these secrets are referenced securely within the Azure DevOps YAML pipeline definition, which helps manage the Kubernetes service connection securely. Implementing these practices for managing credentials in the YAML pipeline is essential.
The use of Azure CLI commands aids in configuring and managing these settings. Use appropriate Azure CLI commands to create and configure the service principal. In the Azure DevOps pipeline, the YAML definition should reference the service principal for authentication and secure access to the AKS cluster. This seamless approach provides a strong foundation for managing the Kubernetes service connection in Azure DevOps, ensuring the integrity of your deployments. Follow these steps carefully to create a reliable pipeline for deploying to Kubernetes. This practice ensures all deployments are completed successfully and accurately. Adhering to these guidelines contributes to a well-structured and manageable workflow for your Kubernetes service connection in Azure DevOps.
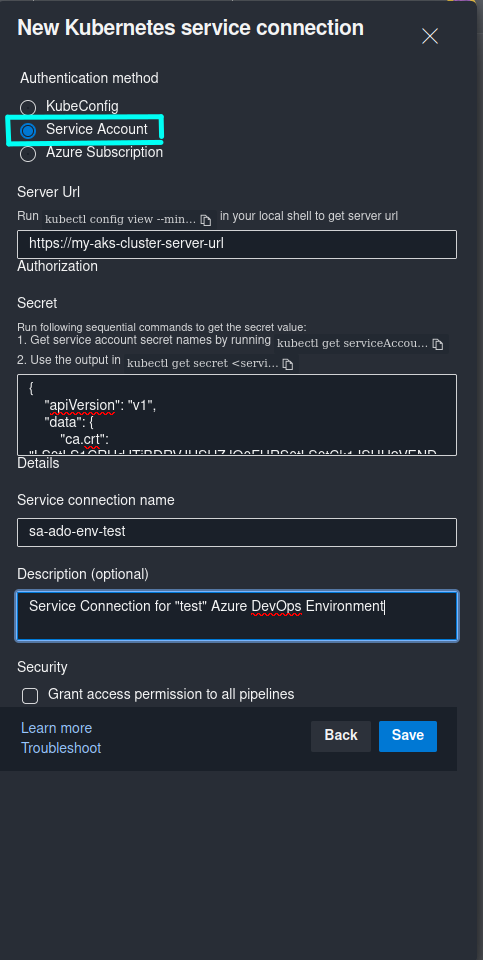
Leveraging Service Accounts for Seamless Authentication
Securely authenticating Kubernetes services with Azure DevOps is crucial for a smooth CI/CD pipeline. Service accounts in Kubernetes offer a robust method for authentication. This approach simplifies the process of granting access to Azure DevOps resources, vital for a successful kubernetes service connection in azure devops. Creating and managing service accounts within the Kubernetes cluster streamlines the authentication process.
The process involves creating a service account within the Kubernetes cluster. Assign appropriate roles and permissions to this account, enabling the necessary interactions with Azure DevOps resources. Storing the service account credentials securely is essential. Kubernetes secrets provide a secure mechanism for handling sensitive information, such as tokens or credentials. Storing these credentials within secrets mitigates security risks associated with hardcoding sensitive data into Kubernetes deployments. Effectively managing service accounts is pivotal for a successful kubernetes service connection in azure devops. The method of using service accounts offers several advantages. It simplifies authentication and reduces the risk of exposing sensitive credentials. Moreover, this approach aligns with best practices for securing sensitive data. However, proper configuration and management of service accounts within Kubernetes is paramount. Incorrect configurations might lead to authentication failures, impacting the deployment pipeline. Consider comparing this approach to other authentication methods to fully understand its advantages.
Comparing service accounts to other authentication methods reveals significant benefits. Service accounts streamline the process of granting specific permissions to Kubernetes components. They facilitate secure interactions with Azure DevOps services, critical for a successful kubernetes service connection in azure devops. This method offers a more controlled access management system. Proper configuration of service accounts contributes to enhanced security and operational reliability. Regular audits ensure consistent configurations, maintaining robust security practices, and contribute to a more secure deployment strategy. Carefully configuring service account permissions in Kubernetes ensures smooth integration with Azure DevOps, supporting a reliable and efficient CI/CD pipeline for Kubernetes services.
Networking Considerations: Ingress, Load Balancers, and Virtual Networks
Ensuring seamless communication between a Kubernetes cluster and Azure DevOps necessitates meticulous network planning. Proper configuration of virtual networks, load balancers, and ingress controllers is crucial for a robust kubernetes service connection in azure devops. Virtual networks define the boundaries for network traffic. Properly configured subnets isolate specific applications and services within the network.
Kubernetes ingress controllers act as gateways, directing external traffic to the appropriate services within the cluster. These controllers often integrate with Azure Load Balancers, distributing traffic across multiple instances of a deployed application. Configuring load balancers for efficient traffic distribution is essential for handling increasing application demands. Network policies provide a granular level of control over traffic flow within the Kubernetes cluster, further enhancing security and improving performance. Implementing network policies reduces unnecessary traffic and limits access to resources, enhancing security.
Careful consideration of network security is critical for a kubernetes service connection in azure devops. Using virtual networks, subnets, and network policies creates a secure communication channel between the AKS cluster and the Azure DevOps infrastructure. Proper configuration of firewalls ensures that unauthorized access is blocked. Network monitoring tools can provide insights into potential bottlenecks and anomalies in the network. Careful monitoring and prompt responses to issues can help avoid downtime and service disruptions.
Troubleshooting Common Connectivity Problems in Kubernetes Service Connection in Azure DevOps
Establishing a robust kubernetes service connection in Azure DevOps often involves navigating various connectivity challenges. DNS resolution failures frequently disrupt communication. Incorrectly configured DNS settings within the AKS cluster or Azure DevOps environment can prevent services from resolving hostnames. Verify DNS server configurations and ensure proper propagation of DNS records. Check the connectivity between the AKS cluster and Azure DevOps using tools like ping and nslookup to pinpoint network connectivity problems. Examine firewall rules on both the AKS cluster and Azure DevOps infrastructure. Ensure that necessary ports are open to facilitate communication between the services. Troubleshooting these issues requires careful examination of network configurations and security settings.
Authentication and authorization errors are common hurdles in securing kubernetes service connection in Azure DevOps. Incorrectly configured service principals or service accounts can lead to authentication failures. Double-check the permissions assigned to the service principal used by the Azure DevOps pipeline to access the Kubernetes cluster. Verify that the service account within the Kubernetes cluster possesses the necessary roles and permissions to perform required actions. Examine the logs for detailed error messages that pinpoint authentication issues. If using RBAC, ensure roles are correctly assigned to allow Azure DevOps to interact with Kubernetes resources. Consider using a dedicated service account for each pipeline to limit the scope of its permissions and enhance security. This granular approach minimizes the risk of credential compromise and improves security posture.
Authorization errors may occur if the Azure DevOps pipeline lacks the necessary permissions to interact with specific Kubernetes resources. Ensure that the service principal or service account has sufficient privileges to deploy and manage applications. This involves configuring appropriate RBAC roles to grant the necessary access. Kubernetes network policies play a critical role in controlling communication between pods and namespaces. Misconfigured policies may block traffic between services, leading to connectivity problems. Review and adjust network policies to allow traffic flow between the applications and the relevant Kubernetes components. Use tools like kubectl to examine the network policies and troubleshoot potential issues. Remember, comprehensive logging and monitoring of your kubernetes service connection in Azure DevOps is essential for early detection and resolution of these issues.
Advanced Techniques: Leveraging Kubernetes Secrets and ConfigMaps for Secure Kubernetes Service Connection in Azure DevOps
Managing sensitive data is critical for any application, especially when dealing with a kubernetes service connection in Azure DevOps. Kubernetes Secrets provide a secure way to store and manage confidential information like passwords, API keys, and certificates. These secrets are encrypted at rest and in transit, protecting them from unauthorized access. Within an Azure DevOps pipeline, you can access these secrets using dedicated pipeline variables, ensuring your application receives the necessary credentials without exposing them in your pipeline definition. This approach enhances the security of your kubernetes service connection in Azure DevOps, preventing accidental exposure or breaches.
ConfigMaps, on the other hand, are used to store non-sensitive configuration data such as database connection strings, application settings, or environment variables. Unlike Secrets, ConfigMaps are not encrypted, making them suitable for information that doesn’t require the same level of security. Integrating ConfigMaps into your Azure DevOps pipelines allows you to manage and deploy application configurations efficiently and consistently across different environments. By leveraging ConfigMaps, you can easily adjust application settings without modifying the application’s source code, streamlining the deployment process for your kubernetes service connection in Azure DevOps. This combination of Secrets and ConfigMaps offers a robust solution for managing both sensitive and non-sensitive data within your Kubernetes cluster, enhancing security and operational efficiency. Proper configuration management greatly improves the reliability of your kubernetes service connection in Azure DevOps.
To effectively utilize Secrets and ConfigMaps in your Azure DevOps pipeline for a secure kubernetes service connection in Azure DevOps, you must define them within your Kubernetes manifests. These manifests will then be applied during your deployment process via your Azure DevOps pipeline. The pipeline can be configured to access these Secrets and ConfigMaps using dedicated variables, substituting the values into your application’s configuration files or environment variables during deployment. This method guarantees that sensitive information is never directly stored within the pipeline configuration, enhancing the security of your entire deployment process. Remember to carefully control access to these Secrets and ConfigMaps using Kubernetes Role-Based Access Control (RBAC) to prevent unauthorized access and maintain the integrity of your kubernetes service connection in Azure DevOps. By employing these techniques, you can significantly improve the security and maintainability of your Kubernetes deployments within the Azure DevOps ecosystem.
Monitoring and Logging Your Kubernetes Service Connections
Effective monitoring and logging are crucial for maintaining the health and stability of your kubernetes service connection in azure devops. Proactive monitoring allows for early detection of issues, minimizing downtime and ensuring seamless CI/CD pipelines. Azure Monitor provides comprehensive tools for collecting and analyzing logs and metrics from your AKS cluster and Azure DevOps pipelines. Integrate Azure Monitor with your AKS cluster to track resource utilization, pod health, and network performance. This integration provides real-time visibility into your kubernetes service connection in azure devops, allowing for quick identification and resolution of performance bottlenecks or connectivity problems. Utilize the rich visualization capabilities of Azure Monitor to create custom dashboards that display key metrics relevant to your application deployment process. Regularly review these dashboards to maintain optimal performance of your kubernetes service connection in azure devops.
Kubernetes itself offers robust logging capabilities. Configure logging drivers to collect logs from your applications and Kubernetes components. Integrate these logs with Azure Monitor Log Analytics to centralize log management and perform advanced analysis. Correlation of logs from various sources – applications, AKS, and Azure DevOps pipelines – provides a holistic view of your system’s behavior, aiding in faster troubleshooting. Efficient log analysis tools enable you to search, filter, and aggregate logs based on various criteria. This allows you to identify patterns, track down errors efficiently, and gain deep insights into the health of your kubernetes service connection in azure devops. Implementing a robust logging strategy helps prevent unexpected outages and ensures continuous performance. Regularly review your logs to detect any anomalies that might indicate upcoming problems.
Beyond basic monitoring, consider implementing advanced techniques such as custom metrics and alerts. These allow you to monitor specific aspects of your kubernetes service connection in azure devops that are crucial for your application’s functionality. Set up alerts to notify your team immediately when critical metrics exceed thresholds, ensuring rapid response to potential issues. Azure Monitor supports various alert mechanisms such as email, SMS, and webhooks. Choose the methods best suited to your team’s workflow and response requirements. This proactive approach to monitoring helps prevent minor issues from escalating into major outages, guaranteeing the reliability of your kubernetes service connection in azure devops. Continuous monitoring and refined alerting strategies ensure the smooth operation of your applications, enhancing the overall user experience.