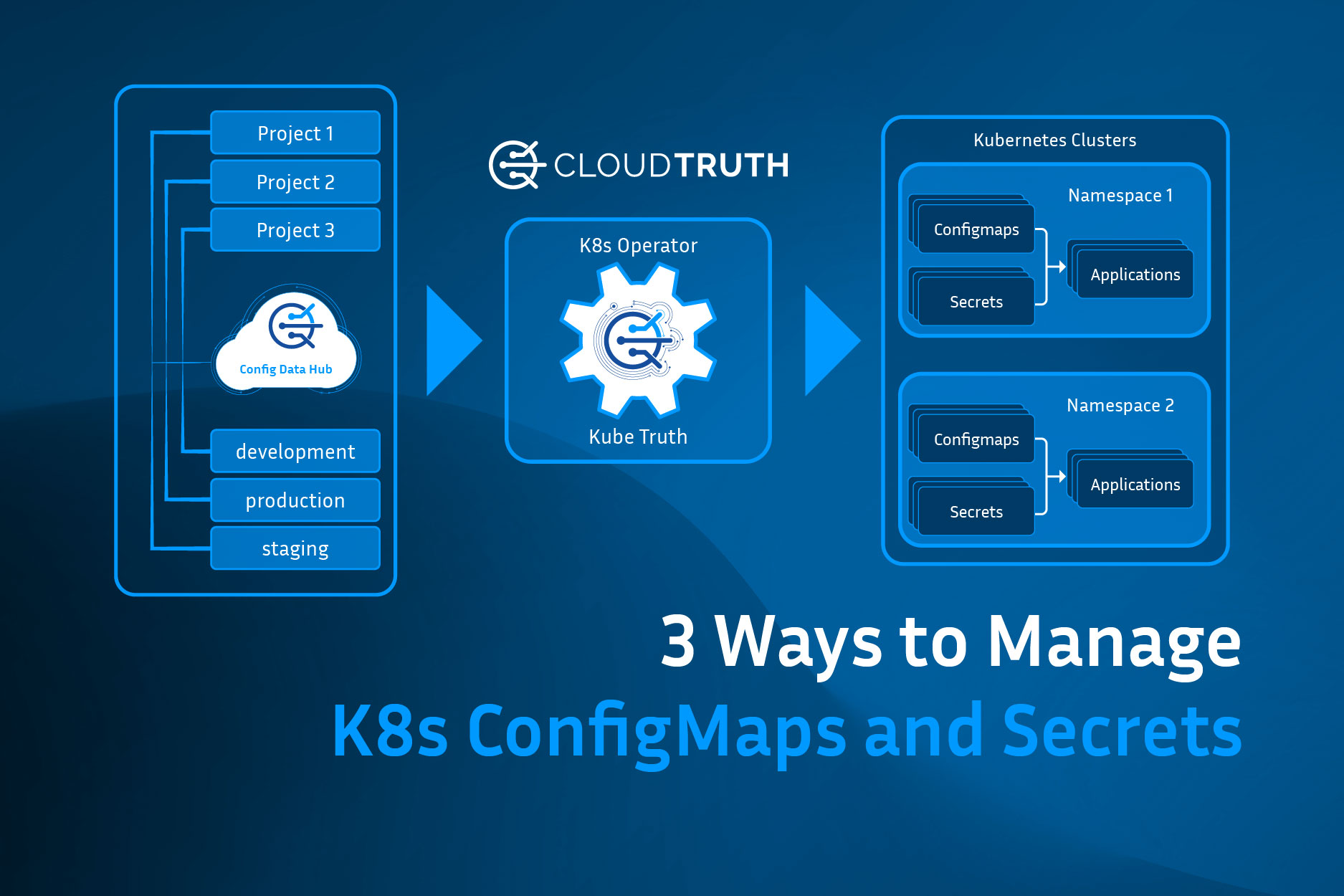
The Significance of Robust Secret Management in Kubernetes
Effective secret management is a critical aspect of securing Kubernetes environments. Mismanaging secrets can lead to severe security vulnerabilities and compliance issues, putting sensitive data and applications at risk. Proper secret management, on the other hand, offers numerous benefits, including enhanced security, regulatory compliance, and streamlined operations. By implementing a robust secret management strategy, organizations can ensure the confidentiality, integrity, and availability of their Kubernetes workloads.
Understanding Kubernetes Secrets: Concepts and Best Practices
Kubernetes secrets are objects that store sensitive information, such as passwords, tokens, and keys, in an encrypted format. Secrets are used to authenticate and authorize access to Kubernetes resources, ensuring that only authorized users and applications can access sensitive data. Secrets are typically stored in etcd, a distributed key-value store that is used by Kubernetes to manage cluster data.
Best practices for creating, managing, and securing Kubernetes secrets include:
- Using secret management tools, such as HashiCorp Vault, CyberArk, or Aqua Security, to create, manage, and distribute secrets.
- Rotating secrets regularly to minimize the risk of unauthorized access.
- Limiting access to secrets by using Kubernetes role-based access control (RBAC) and network policies.
- Encrypting secrets at rest and in transit to prevent interception and theft.
- Monitoring secret usage and auditing secret access to detect and respond to security incidents.
Reviewing Popular Kubernetes Secret Management Solutions
When it comes to managing Kubernetes secrets, there are several popular solutions available in the market. Here are some of the top tools to consider:
- HashiCorp Vault: HashiCorp Vault is a popular secret management tool that provides secure storage and retrieval of secrets. It supports dynamic secrets, which can be generated on-demand, and offers features such as lease management, secret versioning, and access control. HashiCorp Vault is available in both open-source and enterprise editions.
- CyberArk: CyberArk is a comprehensive privileged access management solution that includes secret management capabilities. It offers features such as secret rotation, access control, and auditing, and supports integration with Kubernetes and other container orchestration platforms. CyberArk is a commercial product with pricing based on the number of managed secrets and users.
- Aqua Security: Aqua Security is a container security platform that includes secret management capabilities. It offers features such as secret rotation, access control, and auditing, and supports integration with Kubernetes and other container orchestration platforms. Aqua Security is available in both open-source and enterprise editions.
When selecting a Kubernetes secret management solution, consider factors such as features, pricing, ease of use, and integration with existing tools and workflows. It’s also important to evaluate the security and compliance posture of the solution, and ensure that it meets regulatory requirements and industry best practices.
How to Implement a Secure Kubernetes Secret Management Strategy
Implementing a secure Kubernetes secret management strategy is essential for protecting sensitive data and ensuring regulatory compliance. Here’s a step-by-step guide to help you get started:
- Create secrets: Start by creating secrets for sensitive data, such as API keys, passwords, and certificates. You can create secrets using the Kubernetes command-line interface (CLI) or a secret management tool.
- Configure access controls: Implement access controls to limit who can access secrets. Use Kubernetes role-based access control (RBAC) to define roles and permissions for users and service accounts. You can also use network policies to restrict access to secrets based on IP addresses and other criteria.
- Integrate with secret management tools: Integrate Kubernetes with a secret management tool, such as HashiCorp Vault, CyberArk, or Aqua Security. This will enable you to securely store, manage, and distribute secrets across your Kubernetes environment.
- Monitor secret usage: Use Kubernetes audit logs and third-party security tools to monitor secret usage and detect anomalies. Set up alerts and notifications to notify you of suspicious activity or policy violations.
- Test and validate security: Regularly test and validate the security of your Kubernetes secret management system. Use tools such as penetration testing, vulnerability scanning, and compliance auditing to identify and remediate security issues.
By following these steps, you can implement a secure Kubernetes secret management strategy that protects sensitive data, ensures regulatory compliance, and streamlines operations.
Preventing Common Kubernetes Secret Management Pitfalls
Effective Kubernetes secret management requires careful planning and execution. Here are some common mistakes and pitfalls to avoid:
- Hardcoding secrets in configuration files: Hardcoding secrets in configuration files can expose sensitive data and make it difficult to manage and rotate secrets. Instead, use Kubernetes secrets or a secret management tool to store and manage secrets.
- Storing secrets in plaintext: Storing secrets in plaintext can make them vulnerable to theft and compromise. Use encryption and other security measures to protect secrets and ensure that only authorized users and applications can access them.
- Sharing secrets with unauthorized users: Sharing secrets with unauthorized users can lead to security breaches and compliance issues. Implement access controls and other security measures to limit who can access secrets and ensure that they are used only for authorized purposes.
- Neglecting to rotate secrets: Failing to rotate secrets regularly can make them vulnerable to compromise. Implement a regular schedule for rotating secrets and ensure that they are updated frequently to minimize the risk of security breaches.
- Ignoring audit logs and monitoring: Ignoring audit logs and monitoring can make it difficult to detect and respond to security incidents. Implement auditing and monitoring tools to track secret usage and detect anomalies and policy violations.
By avoiding these common pitfalls, you can implement a secure Kubernetes secret management strategy that protects sensitive data, ensures regulatory compliance, and streamlines operations.
Maintaining Compliance and Auditing Kubernetes Secrets
Maintaining compliance and auditing Kubernetes secrets is essential for ensuring regulatory compliance and detecting and responding to security incidents. Here are some best practices for maintaining compliance and auditing Kubernetes secrets:
- Implement auditing and monitoring tools: Implement auditing and monitoring tools, such as Kubernetes audit logs and third-party security tools, to track secret usage and detect anomalies and policy violations. Use these tools to generate reports and alerts for security incidents and compliance violations.
- Follow regulatory requirements and industry best practices: Follow regulatory requirements and industry best practices for Kubernetes secret management, such as the National Institute of Standards and Technology (NIST) Cybersecurity Framework and the Payment Card Industry Data Security Standard (PCI DSS). Ensure that your Kubernetes secret management strategy meets these requirements and best practices.
- Limit access to secrets: Limit access to secrets to only authorized users and applications. Implement access controls, such as role-based access control (RBAC) and network policies, to restrict who can access secrets and ensure that they are used only for authorized purposes.
- Rotate secrets regularly: Rotate secrets regularly to minimize the risk of security breaches. Implement a regular schedule for rotating secrets and ensure that they are updated frequently to minimize the risk of security breaches.
- Test and validate the security of the secret management system: Regularly test and validate the security of the secret management system to ensure that it meets regulatory requirements and industry best practices. Use tools such as penetration testing, vulnerability scanning, and compliance auditing to identify and remediate security issues.
By following these best practices, you can maintain compliance and auditing Kubernetes secrets, ensuring regulatory compliance and detecting and responding to security incidents.
The Future of Kubernetes Secret Management: Trends and Innovations
Effective Kubernetes secret management is essential for securing and streamlining enterprise workloads. As Kubernetes continues to evolve, new trends and innovations are emerging that can enhance the security and privacy of Kubernetes secrets. Here are some of the most exciting developments to watch:
- Confidential computing: Confidential computing is a technology that uses hardware-based encryption to protect data in use. This can help prevent unauthorized access to Kubernetes secrets, even if an attacker has gained access to the underlying infrastructure. Confidential computing is still in its early stages, but it has the potential to significantly enhance the security of Kubernetes secrets.
- Homomorphic encryption: Homomorphic encryption is a technology that allows computations to be performed on encrypted data without decrypting it first. This can help prevent unauthorized access to Kubernetes secrets, even if an attacker has gained access to the encryption keys. Homomorphic encryption is still in its early stages, but it has the potential to significantly enhance the privacy of Kubernetes secrets.
- Zero-trust security: Zero-trust security is a security model that assumes that all users and applications are untrusted by default. This can help prevent unauthorized access to Kubernetes secrets by requiring users and applications to authenticate and authorize themselves before accessing secrets. Zero-trust security is becoming increasingly popular in Kubernetes environments, as it can help prevent insider threats and other security breaches.
To prepare for the adoption of these trends and innovations in the enterprise, it’s essential to stay up-to-date with the latest developments in Kubernetes secret management. This can help you identify new opportunities to enhance the security and privacy of your Kubernetes secrets, and ensure that your Kubernetes environment is secure and compliant.
Conclusion: Securing Your Kubernetes Environment with Effective Secret Management
Effective Kubernetes secret management is essential for securing and streamlining enterprise workloads. By implementing a secure Kubernetes secret management strategy, you can enhance security, ensure regulatory compliance, and streamline operations. However, mismanaging secrets can lead to security vulnerabilities and compliance issues, putting your enterprise at risk.
To avoid these risks, it’s essential to understand the basics of Kubernetes secrets, including their purpose, structure, and storage locations. Best practices for creating, managing, and securing secrets include using secret management tools, rotating secrets regularly, and limiting access to secrets. By following these best practices, you can ensure that your Kubernetes secrets are secure and compliant.
When selecting a Kubernetes secret management tool, consider factors such as features, pricing, and ease of use. Popular Kubernetes secret management tools include HashiCorp Vault, CyberArk, and Aqua Security. Each tool has its own strengths and weaknesses, so it’s essential to choose the one that best meets your enterprise’s needs.
To prevent common Kubernetes secret management pitfalls, avoid hardcoding secrets in configuration files, storing secrets in plaintext, and sharing secrets with unauthorized users. Instead, use secret management tools, encrypt secrets, and limit access to secrets to only authorized users and applications.
Maintaining compliance and auditing Kubernetes secrets is also essential for ensuring regulatory compliance and detecting and responding to security incidents. Implement auditing and monitoring tools, such as Kubernetes audit logs and third-party security tools, to track secret usage and detect anomalies and policy violations.
Looking ahead, emerging trends and innovations, such as confidential computing, homomorphic encryption, and zero-trust security, have the potential to enhance the security and privacy of Kubernetes secrets. By staying up-to-date with the latest developments in Kubernetes secret management, you can identify new opportunities to enhance the security and privacy of your Kubernetes secrets, and ensure that your Kubernetes environment is secure and compliant.
In conclusion, effective Kubernetes secret management is essential for securing and streamlining enterprise workloads. By following best practices, selecting the right Kubernetes secret management tool, preventing common pitfalls, maintaining compliance, and staying up-to-date with the latest trends and innovations, you can ensure that your Kubernetes secrets are secure and compliant, and your enterprise is protected from security vulnerabilities and compliance issues.