How to Fortify Kubernetes Networks
Kubernetes network security is a critical aspect of maintaining a secure and reliable containerized environment. Default Kubernetes networking configurations are not inherently secure and can expose your cluster to various risks. These risks include unauthorized access, data breaches, and lateral movement within the cluster. The complexity of Kubernetes network environments, with their dynamic nature and numerous interconnected components, amplifies these challenges. Without proper security measures, a cluster can become vulnerable to attacks, leading to significant operational and financial consequences. Therefore, it is essential to understand and implement robust security practices tailored to the unique challenges of Kubernetes networking. This approach ensures that sensitive data remains protected and the integrity of your applications is maintained. The initial lack of security in standard Kubernetes setups underscores the need for proactive and well-defined strategies.
A significant challenge in Kubernetes environments is the inherent trust among pods within the same network. By default, pods can communicate freely, which can be exploited by attackers to move laterally. This lack of isolation increases the risk of a breach if one compromised pod grants access to other services. Furthermore, the dynamic nature of Kubernetes makes managing network security complicated. As pods are created and destroyed, security policies must adapt to maintain a consistent level of protection. The need for a robust system that monitors, identifies, and addresses network security issues is of the utmost importance. A clear understanding of potential threats and vulnerabilities is the first step in creating a secure Kubernetes deployment, with a specific focus on the intricacies of kubernetes network security.
To mitigate these risks, organizations must invest in establishing a strong Kubernetes network security posture. This includes implementing network segmentation, access controls, and traffic management policies. Also, regular security audits are essential to identify potential loopholes. A multi-layered security approach is important. This approach should include measures at the network level, application level, and infrastructure level. Ultimately, a well-secured Kubernetes environment requires diligent planning, the implementation of best practices, and ongoing monitoring to protect against evolving threats and ensure the continued integrity and availability of the system and maintaining a focus on kubernetes network security.
Understanding Kubernetes Network Fundamentals
Kubernetes network security is paramount for any successful deployment. Understanding its fundamental concepts is the first step. This includes how pods communicate both internally and externally. Pod networking allows containers within pods to interact seamlessly. It also manages their connections to the outside world. Services in Kubernetes provide stable endpoints for applications. These endpoints enable reliable access. They abstract away the complexities of pod IPs. They are crucial for a robust system. Network Policies control the traffic flow within a cluster. They act as a firewall, limiting access. Kubernetes employs several key network resources. The Container Network Interface (CNI) is one of them. CNI is responsible for setting up pod networking. It can be implemented by different providers. Service discovery helps pods locate other services easily. These resources are essential for managing a complex cluster. A solid grasp of these concepts is necessary to ensure kubernetes network security.
Pod networking is the core of kubernetes network security. It involves how pods establish and manage connections. This includes both pod-to-pod communication. It also includes pod-to-external world interactions. Kubernetes uses a flat network. This means every pod gets a unique IP. This allows for direct communication. Services use selectors to find pods providing a specific service. This ensures that requests are routed correctly. The Kubernetes network layer relies on CNI plugins. These plugins offer diverse networking options. Examples include Flannel, Calico, and Weave Net. Network Policies are crucial for security. They define rules to control traffic between pods. They use labels to target specific workloads. This adds a strong layer of kubernetes network security. They determine which pods can communicate with others. Understanding this flow is key to security implementation.
Deeper insights into kubernetes network security are gained by considering service discovery. It allows pods to locate and communicate with each other. They do this without knowing the actual IP address of each other. Kubernetes uses DNS to perform service discovery. This allows each service to have a stable DNS name. This name is used by pods to access the service. Load balancing is also an important part of networking. Kubernetes services provide this functionality. It distributes traffic across multiple pods. This ensures high availability and resilience of applications. The goal of these components is to provide secure and efficient communication. Managing these fundamental elements is important. This will help you create a secure cluster environment. These concepts form the foundation for all other network security measures. They must be fully understood for a secure kubernetes network.
Implementing Robust Network Policies
Kubernetes Network Policies are essential for enhancing kubernetes network security. They act as a firewall within your cluster. These policies control traffic flow between pods and namespaces. Network policies operate at Layer 3 and 4 of the OSI model. This allows for granular control over network communication. They provide a mechanism to specify how pods can communicate with each other. These policies also define how pods interact with external networks. Understanding network policies is crucial for securing your Kubernetes environment. They default to allowing all traffic, so explicit policies are needed. This means that without specific configurations, everything can communicate with everything else. This poses a significant security risk. It is important to implement policies that limit access. By default, all ingress and egress traffic is allowed for each pod. Network policies let you define specific rules for these types of traffic. These rules are essential for a strong kubernetes network security posture.
Defining a network policy involves several key aspects. These rules specify the allowed source and destination for traffic. This is done using selectors based on labels. For example, a policy can allow traffic only from pods within the same namespace. Another might allow specific pods to access a particular service. `matchLabels` are used to select the pods or namespaces on which the policy applies. It is key to understand how selectors and matchLabels work. Understanding the structure of network policies is fundamental to implement them correctly. Policies can also be configured to allow communication between different namespaces. For example, you can allow pods in a frontend namespace to talk to pods in a backend namespace. Ingress rules control what traffic can enter a pod or namespace. Egress rules control the traffic that can leave. A practical scenario might involve allowing only pods with the `app=frontend` label to access pods with `app=backend`. Another example could block all access to a database pod except from its specific backend services. These policies are essential to isolate environments and provide kubernetes network security.
Implementing Kubernetes Network Policies effectively is a crucial part of kubernetes network security. Network Policies should be thoroughly tested after their implementation. This is essential to ensure they function as expected. Start by implementing stricter default-deny policies. Then allow traffic by exception and do not start from the allowing everything concept. Use namespaces to further separate your resources. Be careful with overlapping rules. Review these policies frequently. Network policies do not apply retroactively. They only affect pods created after the policy is in place. By following these strategies, you can significantly improve your kubernetes network security. These policies, when properly implemented, can reduce the attack surface of your application. Use monitoring tools to ensure your policies are working correctly. Consistent monitoring can help identify any issues with your implementation. Properly configured network policies are essential for a secure Kubernetes environment. They must be continuously updated and improved for optimal security.
Leveraging Service Mesh for Enhanced Security
A service mesh represents a dedicated infrastructure layer designed to manage service-to-service communication within a Kubernetes cluster. It introduces a layer of abstraction that decouples application logic from networking concerns. Service meshes, such as Istio and Linkerd, offer a powerful approach to bolster kubernetes network security by providing features like mutual TLS (mTLS). mTLS ensures encrypted communication between services by verifying the identity of each party involved. This cryptographic authentication enhances security by preventing unauthorized access to internal APIs. Service meshes also facilitate sophisticated traffic management techniques, including canary deployments and circuit breaking, further improving overall cluster stability and security. Additionally, the observability features of a service mesh provide valuable insights into application behavior and network traffic, aiding in identifying security vulnerabilities.
The implementation of a service mesh significantly strengthens a kubernetes network security posture through its ability to enforce zero-trust security principles. Traditional network models rely on perimeter security, with less emphasis on internal traffic management. Zero-trust models assume that no user or device is inherently trustworthy and require verification for every access request. Service meshes operationalize this through mTLS and granular access controls, limiting lateral movement within the network if a pod becomes compromised. Moreover, service meshes enable fine-grained authorization and policy enforcement, allowing administrators to create flexible rules that restrict access based on service identities and roles. This dynamic control of traffic flow enables the implementation of robust kubernetes network security strategies which adapt to evolving threat landscapes, making it a vital component of modern cloud-native architectures.
Further, service meshes contribute to overall kubernetes network security by providing centralized management of security policies. This approach is advantageous because it avoids relying on individual applications to implement their own security mechanisms, which can often lead to inconsistencies and vulnerabilities. By using a service mesh, you gain a unified framework for controlling authentication, authorization, and encryption across all services within your Kubernetes cluster. This significantly reduces complexity and enhances the security posture of the entire network. Therefore, adopting a service mesh strategy represents a proactive approach towards improving overall network robustness and resilience against potential security incidents, making it a core part of modern kubernetes network security best practices.
Best Practices for Kubernetes Network Security Hardening
Securing a Kubernetes environment demands a proactive approach to safeguarding its network. Kubernetes network security isn’t just a feature; it’s a necessity for maintaining a robust infrastructure. Begin by strictly limiting external access points. Expose only necessary services to the outside world, avoiding broad connections that could be entryways for malicious actors. Regularly update Kubernetes and its related components. This practice mitigates vulnerabilities that attackers could exploit. The latest versions typically include crucial security patches.
Implement strong authentication and authorization mechanisms. Employ role-based access control (RBAC) to limit user privileges and enhance security. Network segmentation is essential; create different network zones for different applications. Doing this can confine the impact of a potential breach. Implement robust security scanning and auditing tools. These can detect vulnerabilities and abnormal behavior early. These practices are vital for effective kubernetes network security. Also, establish a robust process to manage secrets securely, such as API keys and passwords. Use Kubernetes Secrets or dedicated solutions like HashiCorp Vault to store and handle sensitive information securely.
Further enhancements include leveraging network policies to control communication between pods. The default setup often grants broad communication access, increasing risks, so implementing network policies to define explicit rules for allowing traffic is key. Enforce these rules to ensure that only necessary communication is permitted. Regularly audit your network configurations and logs for any suspicious activities or changes. This helps identify potential security incidents and understand them. Adopt a zero-trust approach where no component or communication is inherently trusted. Always verify and authorize each connection. This methodology helps prevent lateral movement inside the cluster and contributes to a strong kubernetes network security posture.
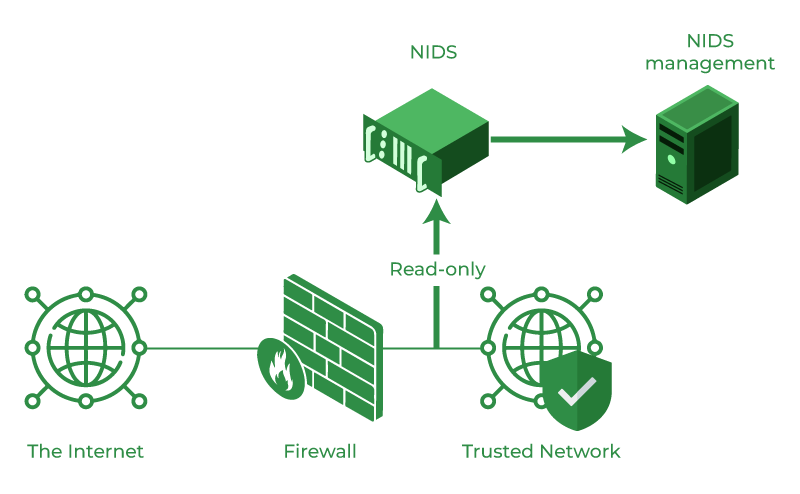
Practical Strategies for Network Intrusion Detection
Intrusion detection and response are vital aspects of maintaining robust kubernetes network security. Kubernetes environments, while powerful, are also susceptible to various network-based attacks. A reactive approach is not sufficient; a proactive stance that involves constant monitoring and analysis is needed. This involves implementing tools and strategies that detect, analyze, and respond to malicious activities targeting your cluster’s network. Effective intrusion detection helps maintain the integrity, availability, and confidentiality of your applications and data within your Kubernetes environment.
Network monitoring tools play a critical role in identifying suspicious activities. These tools track network traffic patterns, looking for anomalies that might indicate a security breach. Log analysis, another key strategy, involves examining logs generated by Kubernetes components and network infrastructure. These logs contain valuable insights into network activities, potential security threats, and system behavior. Alerting mechanisms should also be set up to notify security personnel when suspicious events occur, enabling swift response and mitigation. Specific open-source and commercial tools are available to aid in this process. For instance, tools like Falco and Suricata are often deployed to detect runtime anomalies in Kubernetes environments. Commercial solutions like Aqua Security and Twistlock offer advanced intrusion detection and threat analysis capabilities. These tools can be integrated to provide real-time detection and analysis, allowing for immediate response actions. This proactive approach enhances the overall kubernetes network security.
Integrating network monitoring and security tools is crucial for efficient intrusion detection. Tools should be selected based on the specific needs of the cluster and the types of threats anticipated. It’s advisable to implement a layered security approach by combining multiple detection tools to enhance the overall kubernetes network security. Regular analysis of logs and metrics is vital for identifying patterns and potential vulnerabilities. Implementing security baselines can assist in identifying deviations from standard behavior. This can help improve the detection of unusual activities within the cluster and helps enhance the overall security posture. Furthermore, automated responses can be configured to shut down or isolate infected components, minimizing the impact of a security incident. These comprehensive measures help maintain a secure and resilient Kubernetes network environment.
Choosing the Right Tools for Kubernetes Network Protection
Selecting the appropriate tools is crucial for robust kubernetes network security. This section provides a comparative overview of various solutions. These tools help to safeguard your Kubernetes network. We will explore both open-source projects and commercial offerings. Each option presents unique features and trade-offs. Understanding these differences is vital for informed decision-making. Consider your specific requirements when selecting tools for your environment. Open-source projects offer flexibility and community support. Commercial solutions provide advanced features and enterprise-level support. Let’s examine some prominent tools in each category.
Among open-source options, Cilium stands out with its eBPF-based networking. Cilium provides advanced network policy enforcement. It also offers visibility into network traffic. Calico is another popular choice, known for its simplicity and scalability. Calico provides robust network policy capabilities. It integrates with various CNI plugins. These open-source tools empower users with customization. They can adapt to diverse network requirements. However, they often require in-house expertise for deployment and management. They are constantly evolving in the world of kubernetes network security. Commercial solutions such as Aqua Security and Tigera provide comprehensive security platforms. These platforms integrate multiple security features. This includes network security and vulnerability management. These solutions often feature user-friendly interfaces. They provide enterprise-grade support. Commercial tools provide centralized management capabilities. They enhance the security posture of Kubernetes environments. They are well equipped for kubernetes network security. These offerings come at a cost but can reduce the burden on internal teams. Consider the ease of use and the total cost of ownership while choosing a tool.
When selecting tools for kubernetes network security, evaluate your specific requirements. Consider the size of your cluster and the complexity of your network. Assess your team’s expertise and budget. Explore trial versions or demos before making a commitment. Choosing the right tool ensures an adequate balance between security and usability. It enhances your overall security posture. It helps to mitigate the risks associated with Kubernetes networking. Carefully evaluate each tool’s feature set and community support. Also consider its ability to integrate into your existing infrastructure. The ideal tool will streamline management. It will simplify the complexities of securing your Kubernetes environment. Kubernetes network security needs careful evaluation of the best tools for it.
Monitoring and Auditing Your Kubernetes Network
Maintaining a secure Kubernetes environment requires continuous monitoring and auditing. These practices are crucial for detecting and responding to potential threats. Effective monitoring involves collecting network-related logs and metrics. These provide a detailed view of network activity within the cluster. Establishing security baselines is a vital first step. This allows for the identification of deviations that may indicate a security incident. Analyzing network traffic patterns helps in understanding normal behavior. This understanding enables the detection of anomalous activities. Implementing real-time alerting mechanisms is also essential. These mechanisms should notify security teams about potential breaches. Tools that collect and analyze network data can greatly assist in this process. These tools often provide configurable rules and alerts to help you stay ahead of emerging threats. By actively monitoring, one can quickly identify and mitigate risks. Monitoring contributes significantly to the overall security of the kubernetes network security.
Effective auditing of your Kubernetes network security also plays a key role. It helps in understanding the access control and network policy implementation. Auditing involves examining configurations and policies. It also entails reviewing the logs to verify compliance with security standards. This process will include reviewing network policies to ensure proper traffic filtering. Monitoring network configurations helps in detecting any unauthorized changes or misconfigurations. Regular audits should be conducted to ensure ongoing compliance. Audits help identify vulnerabilities or areas of potential improvement. This activity can provide a clear history of network activity. Security baselines are important when performing network auditing. By comparing current configurations against these baselines, anomalies can be quickly identified. Kubernetes network security is strengthened through the effective audit of implemented policies.
Visualization tools and dashboards offer better insights into network activity. They help in monitoring trends over time. Network monitoring tools provide real-time views of traffic patterns. These interfaces make it easier to spot anomalies and identify potential threats. Integrating logs and metrics in a centralized platform will help enhance incident response. Dashboards should also display key security indicators. This can include the number of policy violations and network traffic data. By implementing these strategies, organizations can maintain strong kubernetes network security. Regular monitoring and auditing ensure the protection of sensitive resources. The continuous analysis of logs and metrics will lead to a robust security posture.