Securing Kubernetes Deployments with Network Policies
Kubernetes Network Policies are a fundamental tool for securing Kubernetes deployments, especially in complex microservices architectures. A Kubernetes network policy examples defines how pods are allowed to communicate with each other and with other network endpoints. Without network policies, all pods within a Kubernetes cluster can freely communicate, creating a flat network that expands the attack surface. This open communication can pose significant security risks, as a compromised pod can potentially access sensitive data or disrupt other services. Kubernetes network policy examples can restrict lateral movement.
Network policies operate on the principle of “default deny.” This means that, by default, all traffic is blocked unless explicitly allowed by a network policy. This approach minimizes the attack surface and provides a granular level of control over network traffic. Kubernetes network policy examples are essential for implementing a zero-trust security model within your cluster.
Implementing Kubernetes network policy examples allows you to segment your applications, isolate critical services, and enforce strict access controls. By defining precise rules about which pods can communicate with each other, you can significantly reduce the risk of unauthorized access and data breaches. These policies act as a firewall at the pod level, providing an additional layer of security on top of other Kubernetes security measures, greatly enhancing the overall security posture of your Kubernetes environment. Kubernetes network policy examples are key for a secure cluster.
Understanding the Fundamentals of Kubernetes Network Policy Definition
A Kubernetes Network Policy is defined using a YAML manifest, similar to other Kubernetes resources. Understanding its basic structure is crucial before implementing more complex scenarios. The manifest specifies the policy’s target pods and the allowed traffic rules. Key fields within the manifest control how the policy operates. These fields include `podSelector`, `ingress`, `egress`, `policyTypes`, and `namespaceSelector`. A simple example can illustrate these core concepts, providing a foundation for understanding more advanced kubernetes network policy examples.
The `podSelector` field is fundamental. It uses labels to select the pods to which the policy applies. The `ingress` section defines rules for inbound traffic. These rules specify which sources are allowed to connect to the selected pods. The `egress` section, conversely, controls outbound traffic. It determines where the selected pods are allowed to initiate connections. `policyTypes` specifies whether the policy applies to ingress, egress, or both. Finally, `namespaceSelector` allows policies to target pods within specific namespaces. This field is usually combined with `podSelector` to narrow down the scope. Properly configuring these fields ensures the kubernetes network policy examples function as intended.
Consider a basic example: A network policy that allows only pods with the label “app=web” within the same namespace to connect to pods with the label “app=database”. The `podSelector` would target “app=database”. The `ingress` section would specify a rule allowing traffic from pods with the label “app=web”. This rule could utilize `matchLabels` to define the label selector. This simple example highlights the basic components of a Kubernetes Network Policy. Furthermore, it shows how these elements combine to control network traffic. Building upon this foundation is key to mastering more sophisticated kubernetes network policy examples and securing your Kubernetes deployments. By understanding how to define these policies, users can effectively implement a “default deny” approach, significantly reducing the attack surface of their applications. Carefully crafted policies are essential for robust security, leading to well-protected environments.
Restricting Ingress Traffic to Specific Pods Using Network Policies
Kubernetes Network Policies are essential for securing Kubernetes deployments. These policies allow for fine-grained control over network traffic. They define how pods communicate with each other and with external networks. This section demonstrates how to restrict inbound (ingress) traffic to specific pods. These kubernetes network policy examples will focus on controlling access based on labels, ensuring only authorized traffic reaches your applications.
To restrict ingress traffic, the `podSelector` field is used to select the target pods. The `ingress` field defines the rules for allowed traffic. Kubernetes network policy examples include allowing traffic only from pods within the same namespace. This is achieved by using a `podSelector` that matches labels of pods in the same namespace. To allow traffic from pods in different namespaces, use the `namespaceSelector` along with a `podSelector`. The `namespaceSelector` selects the namespaces from which traffic is allowed. The `podSelector` further narrows down the allowed pods within those namespaces. These selectors utilize `matchLabels` and `matchExpressions`. `matchLabels` provide a simple way to match pods with specific labels. `matchExpressions` offer more complex matching logic, allowing for conditions like “label exists” or “label value is in a set”.
Consider a scenario where you want to allow traffic to your backend pods only from your frontend pods. First, label your backend pods with `app: backend`. Then, create a network policy with a `podSelector` that targets pods with the `app: backend` label. Within the `ingress` rule, use a `namespaceSelector` to select the namespace where your frontend pods reside. Use a `podSelector` with `matchLabels: app: frontend` to only allow traffic from pods with that label. This ensures that only the frontend pods can communicate with the backend pods, enhancing security. These kubernetes network policy examples are a good starting point for setting up effective policies. You can also restrict based on IP blocks. Use the `ipBlock` field inside ingress and egress rules to define which CIDR blocks are allowed or denied access.
Limiting Egress Traffic from Pods to External Services
Kubernetes network policy examples include controlling outbound (egress) traffic. Network policies define how pods can communicate with the outside world. This involves restricting access to specific external services. Egress policies protect your cluster from malicious outbound connections. They also help comply with security regulations. This section demonstrates how to implement these policies effectively. It shows restricting access using CIDR blocks or IP addresses.
The `to` field within the egress rule specifies the destination. It can define a CIDR block, limiting traffic to a specific IP range. For example, to restrict access to a database with IP address `192.168.1.10`, use `to: – ipBlock: cidr: 192.168.1.10/32`. The `ports` field further refines the policy. It specifies which ports are allowed for egress traffic. An example is restricting HTTP traffic (port 80) to an external API. The configuration would include `ports: – protocol: TCP port: 80`. Combine `to` and `ports` for granular control. Kubernetes network policy examples need precise configuration. This avoids unintended consequences.
Practical scenarios highlight the importance of egress policies. Consider restricting access to a specific external API. Create a policy allowing only HTTPS (port 443) traffic to the API’s IP range. Another scenario involves databases. Limit access only to the database port (e.g., 5432 for PostgreSQL). Careful planning is crucial when creating policies. Incorrect policies can disrupt application functionality. Kubernetes network policy examples provide essential security. They minimize the risk of data exfiltration and unauthorized access. Properly configured egress policies significantly enhance cluster security. They restrict the blast radius of potential breaches. Implementing these policies constitutes a critical security measure. This is important for any Kubernetes deployment. They are one of the effective kubernetes network policy examples for better security.
Creating Namespace-Wide Network Policies for Broad Security Control
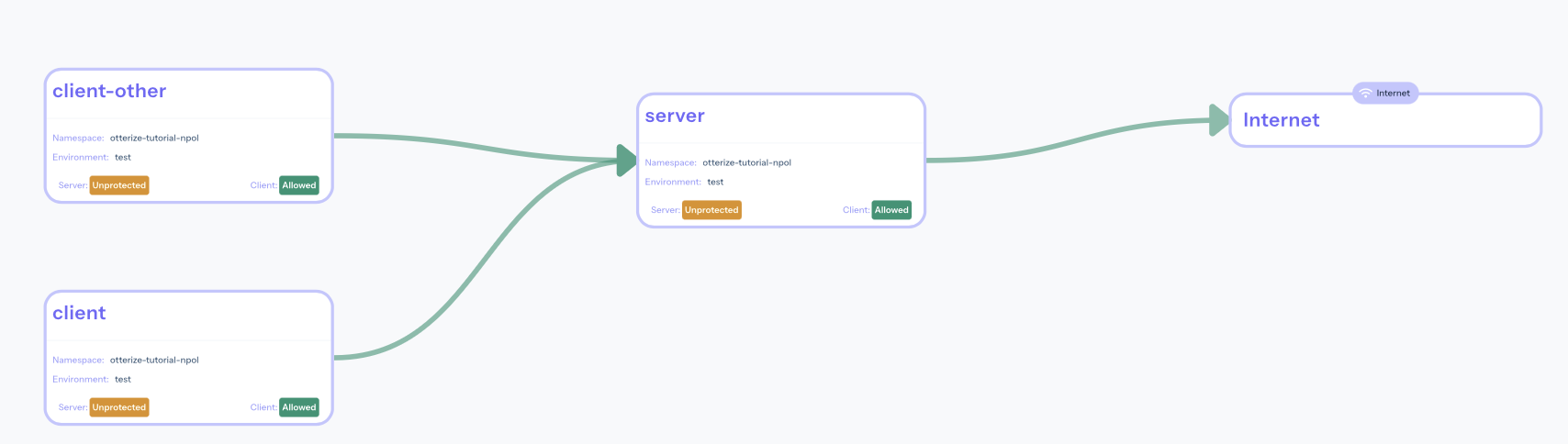
Namespace-wide Kubernetes network policy examples offer a powerful mechanism for enforcing security across an entire namespace in a Kubernetes cluster. These policies provide a broad security control layer, impacting all pods within the designated namespace, unless explicitly overridden by more specific policies. This approach is particularly useful for implementing a “default deny” posture, where all traffic is blocked by default, and only explicitly allowed connections are permitted. This drastically reduces the attack surface and improves the overall security profile of the applications running within that namespace. The use of `namespaceSelector` in network policies enables administrators to target all pods within a namespace regardless of their individual labels, providing a comprehensive security baseline. This ensures that new deployments within the namespace automatically inherit these security restrictions.
To create a namespace-wide policy, the `podSelector` field can be left empty in the network policy definition. When `podSelector` is omitted, the policy applies to all pods within the namespace where the network policy is deployed. Combining `namespaceSelector` with an empty `podSelector` is a common strategy for enforcing baseline security rules across multiple namespaces. For instance, a `namespaceSelector` can target development namespaces to restrict all egress traffic to external services, while allowing inter-pod communication within those namespaces. Kubernetes network policy examples that leverage `namespaceSelector` are crucial for implementing security best practices in multi-tenant environments, where different teams or applications share the same Kubernetes cluster. These policies allow administrators to isolate workloads and prevent unauthorized access between namespaces, reducing the risk of security breaches and data leakage.
Consider a scenario where you want to implement a default deny policy for all ingress traffic within the `development` namespace. You would create a network policy with an empty `podSelector` and an `ingress` section that denies all traffic. Subsequently, you can create more specific policies that selectively allow ingress traffic to certain pods within the `development` namespace based on labels. This layered approach provides granular control over network traffic, allowing you to balance security and functionality. Similarly, for egress traffic, a namespace-wide policy can restrict all outbound connections except those explicitly permitted by other policies. Such Kubernetes network policy examples ensure that even if a pod is compromised, its ability to communicate with external resources or other pods in different namespaces is severely limited, containing the potential damage. By strategically employing namespace-wide policies, organizations can establish a strong foundation for Kubernetes security, protecting their applications and data from unauthorized access and malicious attacks.
Implementing Network Policies with Calico and Other Network Plugins
Kubernetes network policy examples demonstrate that the actual enforcement of network policies is handled by the Container Network Interface (CNI) plugin in use within the Kubernetes cluster. Different CNI plugins implement network policies in varying ways, each with its own strengths and considerations. Understanding how your chosen CNI handles network policies is crucial for effective security implementation. This section briefly discusses a few popular CNI plugins and their network policy implementations.
Calico is a widely used CNI that provides rich network policy features. Calico implements network policies using its own virtual router, offering highly scalable and performant network security. It supports both Kubernetes network policies and its own extended policy model, providing advanced features like global network policies and tiered policies for more granular control. Kubernetes network policy examples using Calico often involve complex scenarios due to Calico’s flexibility. Cilium is another popular CNI that leverages eBPF (extended Berkeley Packet Filter) for network policy enforcement. eBPF allows Cilium to implement network policies at the kernel level, offering high performance and low overhead. Cilium also provides advanced features like HTTP-aware network policies, allowing you to control traffic based on HTTP headers. Antrea is a Kubernetes networking solution based on Open vSwitch. It implements Kubernetes network policies using OpenFlow rules, offering a balance of performance and flexibility. Antrea supports features like Traceflow, which helps you visualize network traffic and troubleshoot network policy issues. When selecting a CNI, consider your specific security requirements and the features offered by each CNI. For detailed information on implementing network policies with each CNI, refer to their respective documentation.
Keep in mind that the behavior and available features of network policies can vary depending on the CNI plugin being used. Always consult the documentation for your specific CNI to understand its capabilities and limitations. Kubernetes network policy examples are available for most popular CNIs to help get you started. For Calico, refer to the official Calico documentation; for Cilium, consult the Cilium documentation; and for Antrea, refer to the Antrea documentation. These resources provide detailed information on configuring and troubleshooting network policies within each environment. Choosing the right CNI and understanding its network policy implementation are key to securing your Kubernetes deployments.
Troubleshooting Common Kubernetes Network Policy Issues
Troubleshooting kubernetes network policy examples implementations can be challenging. Identifying the root cause requires a systematic approach. A common pitfall involves misconfigured label selectors. Ensure the labels in your `podSelector`, `namespaceSelector`, `ingress`, and `egress` rules accurately match the labels applied to your pods and namespaces. Double-check for typos or inconsistencies in label names and values. Overlapping policies can also create unexpected behavior. When multiple policies apply to the same pod, their effects are combined, potentially leading to unintended consequences. Carefully review all policies that affect a specific pod to understand their combined impact. Issues with the Container Network Interface (CNI) plugin can also hinder network policy enforcement.
CNI plugins like Calico, Cilium, and Antrea are responsible for implementing network policies. If the CNI is not configured correctly or is experiencing issues, network policies may not function as expected. Consult the CNI’s documentation for troubleshooting steps. Utilize `kubectl describe networkpolicy
Address resolution problems and DNS errors are other potential causes. Verify pods can resolve DNS names correctly, especially when using external services. Inspect kube-dns or CoreDNS logs for DNS resolution failures. Remember the “default deny” principle when implementing kubernetes network policy examples. Start with restrictive policies that block all traffic and then selectively allow specific connections. This approach makes it easier to identify and address network policy issues. Misconfigured kubernetes network policy examples can severely hinder application functionality, so methodical testing is essential. Remember to test thoroughly after applying any changes. Use tools like `tcpdump` inside containers to capture network traffic and analyze packet flows. This provides detailed insights into network communication and helps pinpoint the exact point where traffic is being blocked. Effective troubleshooting involves a combination of careful policy inspection, connectivity testing, and log analysis. Following these steps will help resolve most kubernetes network policy examples related problems, and ensure a secure and functional environment. Remember to consult official Kubernetes documentation and your CNI provider’s documentation for specific guidance.
Advanced Network Policy Strategies: Combining Policies for Granular Control
Kubernetes network policy examples often showcase single, isolated policies. However, real-world deployments benefit from combining multiple policies to achieve granular security control. This layering approach enables administrators to define a baseline security posture and then refine it with more specific rules. Implementing multiple kubernetes network policy examples will improve the security on several layers.
One powerful strategy involves starting with a default-deny policy. This policy, applied at the namespace level, blocks all ingress and egress traffic by default. Subsequent policies then selectively allow traffic based on specific criteria. For example, a default-deny policy might block all ingress, while another policy allows ingress from pods with the label `app=monitoring`. A third policy might allow egress to specific external services, such as a database. Combining these policies ensures that only explicitly permitted traffic flows, minimizing the attack surface. This provides a layered security, and is one of the most useful kubernetes network policy examples. The order in which these policies are applied is also important. Kubernetes applies network policies in a non-deterministic order, so relying on strict order of precedence is not recommended. Instead, design policies to be additive, with each policy contributing to the overall security posture. Overlapping policies can create unexpected behavior, making it crucial to carefully plan and test policy combinations.
Consider a scenario where you want to isolate a sensitive application. First, apply a namespace-wide default-deny policy. Next, create a policy that allows ingress traffic only from specific frontend pods, identified by labels. Finally, implement a policy that restricts egress traffic to only the necessary external services or databases. This layered approach provides robust security, ensuring that the sensitive application is protected from unauthorized access. Troubleshooting combined policies requires careful examination of each policy’s rules and their interactions. Use tools like `kubectl describe networkpolicy` to inspect the policies and test connectivity to verify their effectiveness. Kubernetes network policy examples like these help ensure deployments are secure.