Understanding Kubernetes Deployment Volume ConfigMaps
ConfigMaps in Kubernetes are powerful objects designed to manage and store non-confidential data used by containerized applications. Specifically, Kubernetes Deployment Volume ConfigMaps focus on handling configurations and settings, allowing for a more organized and efficient management of containerized applications. The primary purpose of ConfigMaps is to decouple configuration artifacts from image content, ensuring that container images remain small, portable, and focused on the application logic. By using ConfigMaps, developers can manage application configurations separately, making it easier to maintain, update, and distribute them across different environments.
Kubernetes Deployment Volume ConfigMaps offer several benefits, including:
- Encouraging a clean separation of concerns between application code and configurations.
- Simplifying the management of environment-specific configurations.
- Facilitating the distribution of configuration updates without requiring new container image builds.
- Improving security by keeping sensitive data out of ConfigMaps and using Kubernetes Secrets instead.
- Enabling the use of various volume types and mounting options to provide containers with access to configuration data.
As a crucial component of Kubernetes deployments, understanding and utilizing ConfigMaps effectively can significantly improve the maintainability, scalability, and resilience of containerized applications.
Creating a ConfigMap in Kubernetes
To create a ConfigMap in Kubernetes, you can use various methods, including the command line, YAML files, or literals. This section will discuss each method in detail, allowing you to choose the one that best suits your needs.
Method 1: Using the Command Line
To create a ConfigMap using the command line, you can use the kubectl create configmap command followed by the name of the ConfigMap and the source data. For example:
kubectl create configmap my-configmap --from-literal=KEY1=VALUE1 --from-literal=KEY2=VALUE2 This command creates a ConfigMap named my-configmap with two key-value pairs: KEY1=VALUE1 and KEY2=VALUE2.
Method 2: Using YAML Files
Alternatively, you can create a ConfigMap using a YAML file. To do this, create a file named configmap.yaml with the following content:
apiVersion: v1 kind: ConfigMap metadata: name: my-configmap data: KEY1: VALUE1 KEY2: VALUE2 Then, apply the YAML file using the kubectl apply -f command:
kubectl apply -f configmap.yaml This command creates a ConfigMap named my-configmap with two key-value pairs: KEY1=VALUE1 and KEY2=VALUE2.
Method 3: Using Literals
Finally, you can create a ConfigMap using literals directly in the kubectl create configmap command. For example:
kubectl create configmap my-configmap --from-file=path/to/config/file This command creates a ConfigMap named my-configmap from the contents of the file located at path/to/config/file.
By understanding these methods, you can create ConfigMaps in Kubernetes and manage your containerized applications’ configurations and settings more effectively.
Mounting ConfigMaps to Pod Volumes
Mounting ConfigMaps to Pod volumes enables containers to access configuration data, allowing for a more organized and efficient management of containerized applications. This section will explain how to mount ConfigMaps to Pod volumes and discuss different volume types and mounting options.
Volume Types
Kubernetes supports various volume types, including emptyDir, hostPath, and persistentVolumes. When mounting ConfigMaps to Pod volumes, you can use the volumes and volumeMounts sections in the Pod’s YAML definition to specify the volume type and mount the ConfigMap data.
Mounting ConfigMaps to Volumes
To mount a ConfigMap to a volume, you need to define the volume and volumeMounts in the Pod’s YAML definition. Here’s an example:
apiVersion: v1 kind: Pod metadata: name: my-pod spec: containers: - name: my-container image: my-image volumeMounts: - name: config-volume mountPath: /etc/config volumes: - name: config-volume configMap: name: my-configmap In this example, the ConfigMap named my-configmap is mounted to the volume config-volume, and the data is accessible at /etc/config within the container.
Mounting Options
Kubernetes offers several mounting options, such as readOnly and subPath, which can be used to fine-tune the access and management of ConfigMaps in Pod volumes.
Read-Only Mounts
To mount a ConfigMap as read-only, add the readOnly: true option to the volumeMounts section:
volumeMounts: - name: config-volume mountPath: /etc/config readOnly: true This configuration ensures that the container cannot modify the ConfigMap data.
SubPath Mounts
The subPath option allows you to mount a specific subset of the ConfigMap data to a container. For example:
volumeMounts: - name: config-volume mountPath: /etc/config/specific-config subPath: specific-config.yaml In this example, only the specific-config.yaml data from the ConfigMap is mounted to the container at the /etc/config/specific-config path.
By mastering the art of mounting ConfigMaps to Pod volumes, you can provide containers with seamless access to configuration data, improving the maintainability and scalability of your containerized applications.
Updating and Managing ConfigMaps in a Live Kubernetes Environment
When working with ConfigMaps in a live Kubernetes environment, it’s crucial to follow best practices for updating, managing, and handling versioning, rollbacks, and concurrent updates. This section will discuss these best practices and provide guidance on maintaining ConfigMaps effectively.
Versioning ConfigMaps
To ensure proper tracking of changes, version your ConfigMaps by appending a version number or timestamp to their names. This approach simplifies rollbacks and makes it easier to identify the active configuration.
Performing Rollbacks
To roll back to a previous version of a ConfigMap, simply rename the current ConfigMap and restore the desired version using its original name. This method ensures minimal downtime and allows for easy version switching.
Handling Concurrent Updates
When multiple users or automated processes update ConfigMaps concurrently, conflicts may arise. To prevent such issues, implement a locking mechanism or use a version control system to manage ConfigMaps, ensuring that only one user can modify a ConfigMap at a time.
Monitoring ConfigMaps
Monitoring ConfigMaps is essential for maintaining a stable Kubernetes environment. Utilize monitoring tools and alerts to track changes, detect anomalies, and receive notifications when ConfigMaps are updated or modified.
Auditing ConfigMaps
Auditing ConfigMaps helps identify potential security threats and configuration drift. Implement audit logs and periodically review them to ensure that ConfigMaps are up-to-date and secure.
By following these best practices, you can effectively update and manage ConfigMaps in a live Kubernetes environment, ensuring a smooth and efficient configuration management experience.
Using ConfigMaps for Environment-Specific Configurations
ConfigMaps can be effectively utilized for managing environment-specific configurations, such as development, staging, and production. By separating configuration data from container images, you can maintain a clean separation of concerns and handle sensitive data securely.
Managing Environment-Specific ConfigMaps
Create separate ConfigMaps for each environment, using unique names and labels to differentiate them. For example, you can create a ConfigMap named my-configmap-dev, my-configmap-staging, and my-configmap-prod for development, staging, and production environments, respectively.
Handling Sensitive Data Securely
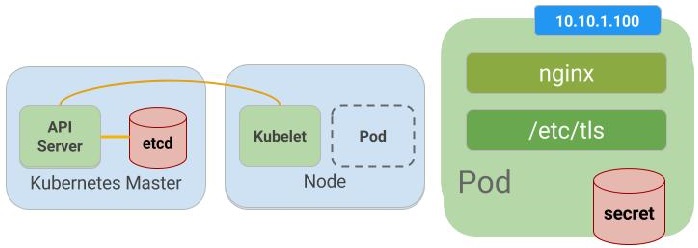
When dealing with sensitive data, such as API keys, database credentials, or encryption keys, avoid storing them directly in ConfigMaps. Instead, use Kubernetes Secrets to manage sensitive information securely. Secrets are encrypted at rest and in transit, ensuring that your sensitive data remains protected.
Configuring Environment-Specific Settings
To configure environment-specific settings, create a ConfigMap for each environment and include the necessary configuration data. For instance, you can define different log levels, API endpoints, or database connections for each environment.
Deploying Environment-Specific ConfigMaps
When deploying applications to different environments, ensure that the correct ConfigMap is mounted to the corresponding Pod. Utilize Kubernetes labels and selectors to match Pods with the appropriate ConfigMaps based on the environment.
Rotating and Updating ConfigMaps
Regularly rotate and update ConfigMaps to maintain a secure and up-to-date environment. Implement versioning, rollbacks, and concurrent updates best practices to ensure a smooth configuration management experience.
By leveraging ConfigMaps for environment-specific configurations, you can maintain a clean separation of concerns, handle sensitive data securely, and ensure a consistent and efficient configuration management process across different environments.
Comparing ConfigMaps with Secrets and Other Kubernetes Objects
ConfigMaps, Secrets, ConfigMap volumes, and environment variables are essential Kubernetes objects for managing containerized applications’ configurations and settings. Understanding the differences between these objects can help users make informed decisions about when to use each object.
ConfigMaps vs. Secrets
ConfigMaps and Secrets both store configuration data, but they differ in how they handle sensitive information. ConfigMaps are designed for storing non-sensitive data, while Secrets are used for managing sensitive data, such as API keys, passwords, or certificates. Secrets are encrypted at rest and in transit, providing an additional layer of security compared to ConfigMaps.
ConfigMaps vs. ConfigMap Volumes
ConfigMaps and ConfigMap volumes serve similar purposes but differ in their implementation. ConfigMaps store configuration data, while ConfigMap volumes allow containers to access the data stored in ConfigMaps. ConfigMap volumes are particularly useful when dealing with shared or read-only data that needs to be accessible by multiple containers within a Pod.
ConfigMaps vs. Environment Variables
ConfigMaps and environment variables can both be used to provide configuration data to containers. However, environment variables have some limitations compared to ConfigMaps. Environment variables are less flexible, harder to manage at scale, and may expose sensitive data if not handled securely. ConfigMaps offer a more organized and secure approach to managing configuration data.
When to Use Each Object
Use ConfigMaps for managing non-sensitive configuration data, such as application settings, log levels, or endpoints. Utilize Secrets for sensitive data, like API keys, passwords, or certificates. Leverage ConfigMap volumes when sharing or providing read-only data to multiple containers within a Pod. Finally, consider using environment variables for simple, standalone applications that require minimal configuration data.
By understanding the differences between ConfigMaps, Secrets, ConfigMap volumes, and environment variables, you can make informed decisions about when to use each Kubernetes object, ensuring a secure and efficient configuration management experience.
Real-World Examples of ConfigMaps in Action
ConfigMaps are widely used in production environments to manage containerized applications’ configurations and settings. This section highlights real-world examples of ConfigMaps in action, demonstrating their versatility and effectiveness.
Example 1: Managing Application Settings
ConfigMaps can be used to manage application settings, such as log levels, endpoints, or timeouts. For instance, a ConfigMap can store configuration data for a web application, allowing administrators to modify settings without rebuilding the container image.
Example 2: Environment-Specific Configurations
ConfigMaps can be employed to manage environment-specific configurations, such as development, staging, and production environments. By creating separate ConfigMaps for each environment, you can ensure that applications use the correct configuration data based on their deployment context.
Example 3: Database Connection Details
ConfigMaps can store database connection details, such as hostnames, port numbers, usernames, and passwords. By leveraging ConfigMaps, you can centralize database connection information and simplify the process of updating or rotating credentials.
Example 4: Customizing Container Startup Commands
ConfigMaps can be used to customize container startup commands, allowing you to specify command-line arguments or environment variables for your applications. This approach enables you to tailor container behavior based on specific deployment requirements or conditions.
Example 5: Sharing Data Between Containers
ConfigMaps can be mounted as volumes, allowing containers within a Pod to share data or configuration information. This technique is particularly useful when multiple containers need to access the same configuration data or when you want to maintain a consistent data sharing mechanism across your applications.
These real-world examples demonstrate the versatility and effectiveness of ConfigMaps in managing containerized applications’ configurations and settings. By incorporating ConfigMaps into your Kubernetes deployment strategy, you can simplify configuration management, enhance security, and improve the overall maintainability of your applications.
Troubleshooting ConfigMaps in Kubernetes
Working with ConfigMaps in Kubernetes can sometimes present challenges. This section discusses common issues and provides troubleshooting tips and best practices to help users resolve these issues efficiently.
Issue 1: ConfigMap Data Not Accessible
If a container cannot access the data from a ConfigMap, ensure that the ConfigMap is correctly mounted to the Pod volume and that the container has the necessary permissions to read the data. Check the Pod’s YAML definition for any misconfigurations and verify the volume and volumeMounts sections.
Issue 2: ConfigMap Data Not Updated
If a ConfigMap’s data is not being updated in a container, ensure that the container is restarted after the ConfigMap is updated. Containers may cache ConfigMap data, and a restart is often required to apply the latest changes.
Issue 3: Concurrent ConfigMap Updates
When multiple users or automated processes update ConfigMaps concurrently, conflicts may arise. Implement a locking mechanism or use a version control system to manage ConfigMaps, ensuring that only one user can modify a ConfigMap at a time.
Issue 4: Sensitive Data Exposure
Avoid storing sensitive data directly in ConfigMaps. Instead, use Kubernetes Secrets to manage sensitive information securely. Secrets are encrypted at rest and in transit, providing an additional layer of security compared to ConfigMaps.
Issue 5: Managing ConfigMaps Across Clusters
Managing ConfigMaps across multiple Kubernetes clusters can be challenging. Consider using tools like Helm, Kustomize, or Kubeval to manage ConfigMaps consistently and efficiently across different environments.
By understanding these common issues and challenges when working with ConfigMaps in Kubernetes, you can proactively address potential problems and ensure a smooth configuration management experience.