Understanding Kubernetes Dashboard Access Tokens
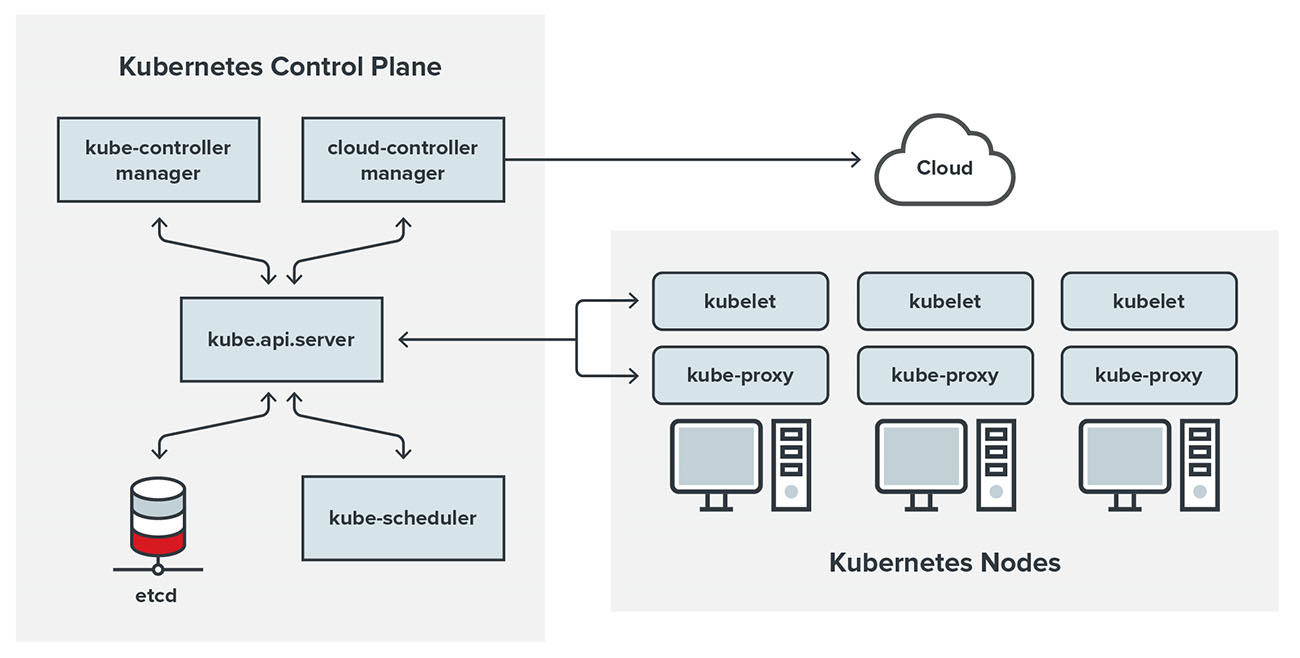
Kubernetes dashboard access tokens are crucial components in granting secure access to the Kubernetes dashboard. These tokens serve as a type of authentication key, allowing users to interact with the dashboard and manage Kubernetes resources securely. By understanding the purpose and importance of these tokens, users can ensure the safety and integrity of their Kubernetes clusters.
Access tokens are an essential part of Kubernetes’ identity and access management (IAM) system. They provide a secure and flexible way to authenticate users and grant them access to specific resources within a Kubernetes cluster. By creating and utilizing access tokens, users can manage and monitor their clusters with confidence, knowing that their actions are authenticated and authorized.
In this comprehensive guide, we will explore the process of creating and utilizing Kubernetes dashboard access tokens. We will discuss best practices for managing and renewing tokens, troubleshoot common issues, and compare alternative methods for securing access to the Kubernetes dashboard. By the end of this article, you will have a solid understanding of the power and flexibility of Kubernetes dashboard access tokens.
Generating a New Access Token for the Kubernetes Dashboard
To create a new access token for the Kubernetes dashboard, follow these steps:
- Access your Kubernetes cluster using the command line. You can use a tool like kubectl or Rancher to connect to your cluster.
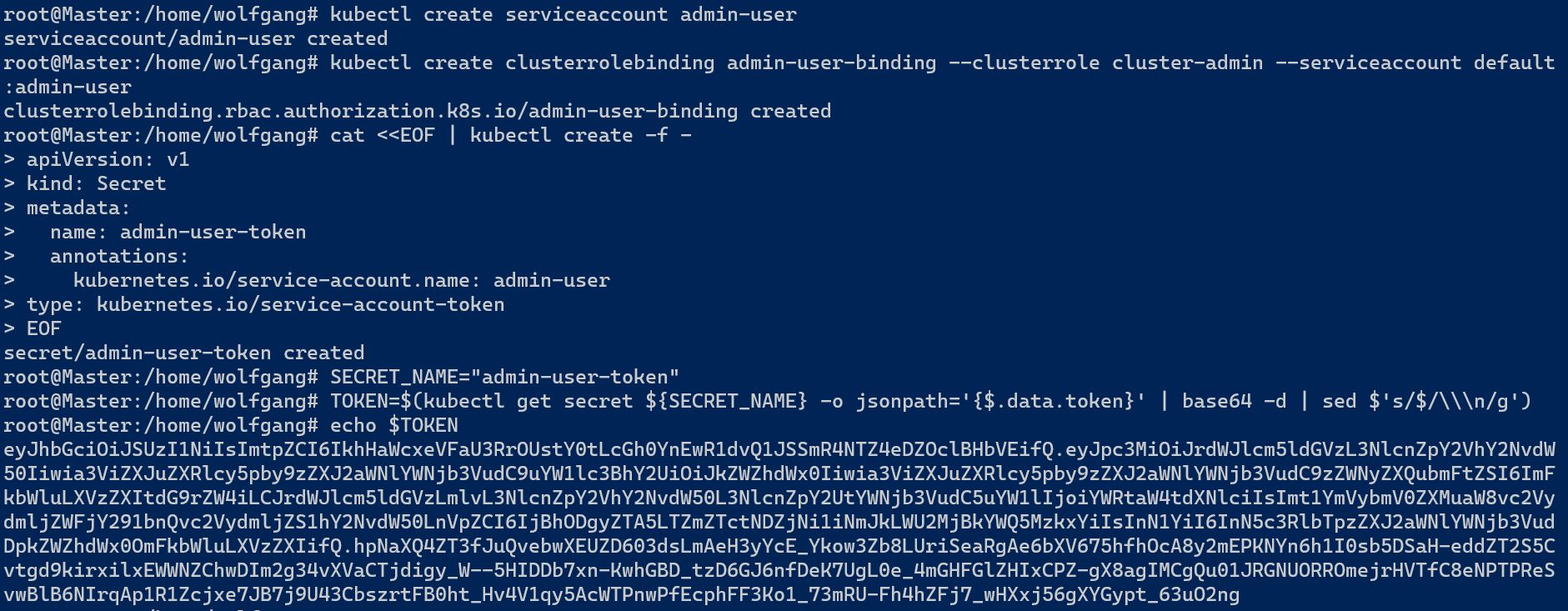
- Once connected, run the following command to create a new service account:
kubectl create serviceaccount dashboard-admin - Next, create a ClusterRoleBinding to grant the service account full access to the Kubernetes API:
kubectl create clusterrolebinding dashboard-admin \ --clusterrole=cluster-admin \ --serviceaccount=default:dashboard-admin - Retrieve the secret associated with the service account using the following command:
kubectl get secret $(kubectl get serviceaccount dashboard-admin -o jsonpath='{.secrets[0].name}') -o jsonpath='{.data.token}' | base64 --decode The output of this command is your new access token. Save this token in a secure location, as you will need it to authenticate to the Kubernetes dashboard.
Note that the command above uses the kubectl command-line tool to create a new service account and bind it to the cluster-admin role. This provides the service account with full access to the Kubernetes API. The command then retrieves the secret associated with the service account, which contains the access token. By decoding the token from the secret, you obtain a new access token that can be used to authenticate to the Kubernetes dashboard.
Applying the Generated Token to Access the Kubernetes Dashboard
To apply the generated token and access the Kubernetes dashboard, follow these steps:
- First, ensure that the Kubernetes dashboard is installed and running in your cluster. If you haven’t installed the dashboard yet, you can follow the official Rancher documentation to install it.
- Once the dashboard is installed, you need to proxy the dashboard to your local machine using kubectl. Run the following command:
kubectl proxy - In a new terminal window, navigate to the Kubernetes dashboard URL:
http://localhost:8001/api/v1/namespaces/kubernetes-dashboard/services/https:kubernetes-dashboard:/proxy/ - You will be prompted to log in to the dashboard. Select “Token” as the authentication method, and enter the token you generated in the previous section. Click “Sign In” to access the Kubernetes dashboard.
By following these steps, you can apply the generated token to access the Kubernetes dashboard. The token serves as your authentication credentials, allowing you to interact with the dashboard and manage Kubernetes resources securely.
Note that the command above uses the kubectl command-line tool to proxy the Kubernetes dashboard to your local machine. This allows you to access the dashboard securely using your generated token. By navigating to the dashboard URL and selecting “Token” as the authentication method, you can enter your token and access the dashboard securely.
Managing and Renewing Access Tokens
Managing and renewing access tokens is an essential part of securing your Kubernetes cluster. By following best practices, you can ensure that your tokens are up-to-date and that your cluster remains secure.
Viewing Existing Tokens
To view existing tokens, you can use the following command:
kubectl get secrets -n kubernetes-dashboard This command lists all the secrets in the kubernetes-dashboard namespace. Look for secrets with a type of kubernetes.io/service-account-token. These secrets contain the access tokens for the Kubernetes dashboard.
Setting Expiration Periods
To set an expiration period for your access tokens, you can use the following command:
kubectl patch serviceaccount dashboard-admin -p '{"secrets": [{"name": "dashboard-admin-token-xxxxx", "annotations": {"kubernetes.io/service-account-token-ttl": "2h"}}]}' This command sets the expiration
Troubleshooting Common Issues with Kubernetes Dashboard Access Tokens
Creating and using Kubernetes dashboard access tokens can sometimes result in issues, such as authentication errors or token expiration. In this section, we’ll discuss common problems and provide solutions to help you troubleshoot them.
Authentication Errors
If you encounter authentication errors when attempting to access the Kubernetes dashboard, double-check that you have entered the correct token. You can also verify that the token has not expired by checking its expiration date in the Kubernetes API server logs.
If the token is still valid, ensure that the Kubernetes dashboard is configured to use the correct authentication method. You can check the dashboard’s authentication configuration by running the following command:
kubectl get configmap kubernetes-dashboard -n kubernetes-dashboard -o yaml Look for the “auth.conf” section and verify that the “tokenFile” and “tokenKey” are correctly configured.
Token Expiration
If your access token has expired, you can generate a new one using the steps outlined in Context 2. To avoid token expiration issues, consider setting an expiration period for your access tokens, as discussed in Context 4.
If you are experiencing issues with token expiration, ensure that your Kubernetes API server is configured to use the correct token expiration period. You can check the API server’s token expiration configuration by running the following command:
kubectl get configmap kube-apiserver -n kube-system -o yaml Look for the “service-account-signing-key-file” and “service-account-key-file” sections and verify that the “token-ttl” is correctly configured.
By following these troubleshooting steps, you can quickly identify and resolve common issues with Kubernetes dashboard access tokens.
Alternatives to Kubernetes Dashboard Access Tokens
While Kubernetes dashboard access tokens are a popular and effective way to secure access to the Kubernetes dashboard, there are alternative methods available. In this section, we’ll explore some of these alternatives and compare them to access tokens.
Kubernetes Service Accounts
Kubernetes service accounts are a built-in method for granting access to the Kubernetes API. Service accounts are associated with a set of credentials, such as a token or a certificate, that can be used to authenticate to the API. Service accounts can be assigned roles and role bindings, which define the permissions and resources that the account can access.
Compared to access tokens, service accounts offer a more fine-grained level of access control. However, service accounts can be more complex to manage, especially in large clusters with many services and users. Additionally, service accounts do not provide the same level of user-friendly interface as the Kubernetes dashboard.
Third-Party Authentication Providers
Third-party authentication providers, such as OAuth or LDAP, can be integrated with the Kubernetes dashboard to provide an alternative method for authenticating users. These providers offer a centralized authentication system that can be used across multiple applications and services.
Compared to access tokens, third-party authentication providers offer a more scalable and flexible solution for managing user access. However, integrating these providers can be complex and may require additional configuration and maintenance. Additionally, third-party authentication providers may introduce additional security risks, such as password breaches or phishing attacks.
Choosing the Right Method
When choosing a method for securing access to the Kubernetes dashboard, consider the following factors:
- Ease of use: How easy is it for users to authenticate and access the dashboard?
- Access control: How fine-grained is the level of access control? Can you easily assign roles and permissions to users and services?
- Scalability: How well does the method scale as your cluster grows in size and complexity?
- Security: How secure is the method? What steps can you take to mitigate security risks and ensure the safety and integrity of your cluster?
Ultimately, the right method for securing access to the Kubernetes dashboard will depend on your specific use case and requirements. Consider your options carefully and choose the method that best meets your needs.
Best Practices for Securing Kubernetes Clusters with Access Tokens
Access tokens are a powerful and flexible method for securing access to the Kubernetes dashboard. However, it’s important to follow best practices to ensure the safety and integrity of your Kubernetes clusters.
Network Policies
Network policies are a built-in method for controlling network traffic in Kubernetes. By defining network policies, you can restrict access to the Kubernetes API and dashboard to specific IP addresses or ranges. This can help prevent unauthorized access and reduce the risk of security breaches.
RBAC
Role-Based Access Control (RBAC) is a method for controlling access to Kubernetes resources based on user roles. By defining roles and role bindings, you can restrict access to specific resources and operations. This can help ensure that users only have the access they need to perform their tasks, reducing the risk of accidental or malicious changes to your cluster.
Token Expiration
Setting an expiration period for access tokens can help ensure that tokens are regularly updated and monitored for security purposes. By setting an expiration period, you can reduce the risk of token theft or misuse. Additionally, regularly renewing access tokens can help ensure that your cluster remains secure and up-to-date.
Monitoring and Auditing
Monitoring and auditing access to the Kubernetes dashboard and API can help you detect and respond to security incidents. By monitoring access logs and auditing user activity, you can identify suspicious behavior and take action to prevent security breaches. Additionally, monitoring can help you identify and address performance issues, ensuring that your cluster remains responsive and reliable.
Secure Communication
Secure communication is essential for protecting access to the Kubernetes dashboard and API. By using secure communication protocols, such as HTTPS or TLS, you can encrypt data in transit and prevent eavesdropping or tampering. Additionally, secure communication can help ensure the integrity and confidentiality of your cluster data.
Summary
Access tokens are a powerful and flexible method for securing access to the Kubernetes dashboard. By following best practices, such as network policies, RBAC, token expiration, monitoring and auditing, and secure communication, you can ensure the safety and integrity of your Kubernetes clusters. By regularly updating and monitoring access tokens, you can reduce the risk of security breaches and ensure that your cluster remains secure and up-to-date.
Conclusion: The Power and Flexibility of Kubernetes Dashboard Access Tokens
Access tokens are a powerful and flexible method for securing access to the Kubernetes dashboard. By generating and applying access tokens, you can grant secure access to the dashboard while minimizing the risk of security breaches. In this guide, we have covered the process of creating and utilizing Kubernetes dashboard access tokens, as well as best practices for managing and securing them.
Throughout this guide, we have mentioned the keyword “kubernetes dashboard create token” to help improve SEO and ensure that this content is easily discoverable by users searching for information on this topic. By following the steps and best practices outlined in this guide, you can take full advantage of the power and flexibility of Kubernetes dashboard access tokens.
As with any security measure, it’s important to use access tokens responsibly and with caution. Regularly monitoring and updating access tokens can help ensure the safety and integrity of your Kubernetes clusters. By following best practices for securing Kubernetes clusters using access tokens, including network policies, RBAC, and other security measures, you can reduce the risk of security breaches and ensure that your cluster remains secure and up-to-date.
We hope that this guide has been helpful in explaining the process of creating and utilizing Kubernetes dashboard access tokens. By experimenting with access tokens and exploring their capabilities, you can enhance the security and management of your Kubernetes clusters.