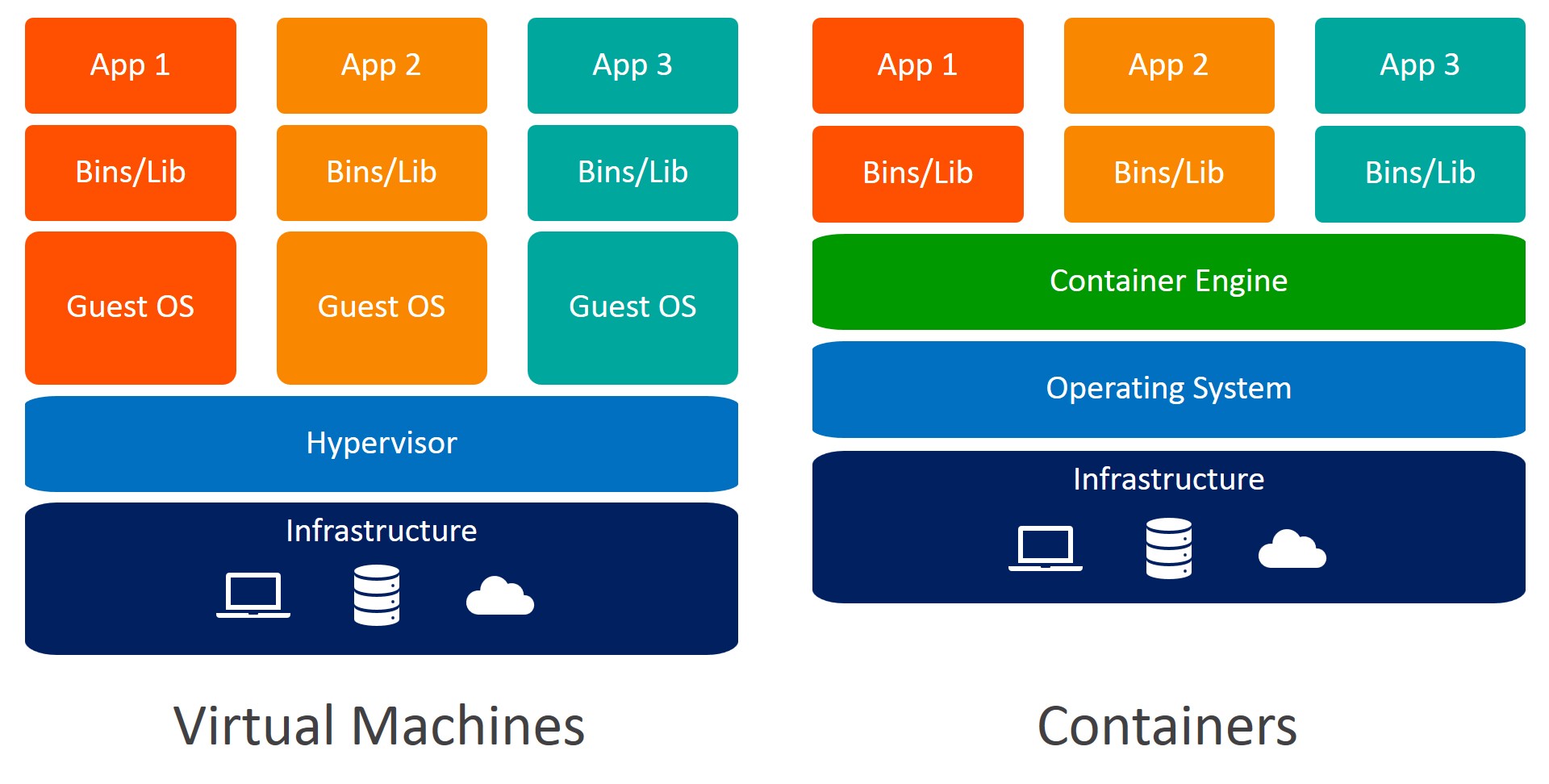
Understanding Kubernetes ConfigMaps: A Key Component in Container Orchestration
Kubernetes ConfigMaps are a powerful tool for managing configuration data in a Kubernetes cluster. ConfigMaps allow you to store and manage non-sensitive, application-specific data such as environment variables, application properties, and command-line arguments. By separating configuration data from container images, ConfigMaps make it easier to manage and update applications without having to rebuild and redeploy container images.
ConfigMaps are particularly useful in a microservices architecture, where applications are composed of multiple, loosely coupled services. In such an environment, ConfigMaps can help you manage the configuration data for each service independently, allowing you to make changes to one service without affecting others. This can lead to more agile and flexible development and deployment processes.
Moreover, Kubernetes ConfigMaps provide a way to decouple configuration data from the application code, which can help improve security and compliance. By storing configuration data outside of the container image, you can reduce the risk of exposing sensitive data in the event of a security breach. Additionally, ConfigMaps can help you comply with regulatory requirements such as data privacy and protection.
In summary, Kubernetes ConfigMaps are a key component in container orchestration, providing a flexible and secure way to manage configuration data for containerized applications. By using ConfigMaps, you can improve your development and deployment processes, enhance security and compliance, and make it easier to manage and update your applications.
How to Create and Manage Kubernetes ConfigMaps: A Practical Guide
Kubernetes ConfigMaps are a powerful tool for managing configuration data in a Kubernetes cluster. To get started with ConfigMaps, you need to create and manage them effectively. Here’s a step-by-step guide on how to do it:
-
Create a ConfigMap using the `kubectl` command-line interface. For example, the following command creates a ConfigMap named `my-config` from a file named `config.properties`:
kubectl create configmap my-config --from-file=config.properties -
Alternatively, you can create a ConfigMap using a YAML file. Here’s an example of a YAML file that creates a ConfigMap named `my-config` with two key-value pairs:
apiVersion: v1 kind: ConfigMap metadata: name: my-config data: key1: value1 key2: value2 -
List all ConfigMaps in your Kubernetes cluster using the following command:
kubectl get configmaps -
Describe a ConfigMap using the following command:
kubectl describe configmaps my-config -
Update a ConfigMap using the `kubectl` command-line interface or a YAML file. For example, the following command updates the `my-config` ConfigMap with a new key-value pair:
kubectl create configmap my-config --from-file=config.properties --dry-run=client -o yaml | kubectl apply -f - -
Delete a ConfigMap using the following command:
kubectl delete configmaps my-config
When creating and managing ConfigMaps, it’s essential to follow best practices. Here are some tips:
-
Use labels and annotations to organize and manage ConfigMaps easily.
-
Version ConfigMaps to enable rollbacks and track changes over time.
-
Use ConfigMaps in conjunction with other Kubernetes resources like Secrets and Deployments to manage application configuration effectively.
-
Monitor ConfigMap usage to ensure that they are up-to-date and secure.
In conclusion, Kubernetes ConfigMaps are a powerful tool for managing configuration data in a Kubernetes cluster. By following the step-by-step guide and best practices outlined in this article, you can create and manage ConfigMaps effectively, making it easier to manage and update your containerized applications.
Best Practices for Using Kubernetes ConfigMaps: Tips for Effective Configuration Management
Kubernetes ConfigMaps are a powerful tool for managing configuration data in a Kubernetes cluster. To get the most out of ConfigMaps, it’s essential to follow best practices. Here are some tips for effective configuration management:
-
Use labels and annotations: Labels and annotations are a powerful way to organize and manage ConfigMaps in a Kubernetes cluster. By using labels and annotations, you can easily filter and search for ConfigMaps based on specific criteria. For example, you could label ConfigMaps based on the environment they are used in (e.g., development, staging, production) or the application they are associated with.
-
Version ConfigMaps: Versioning ConfigMaps is essential for tracking changes over time and enabling rollbacks. By versioning ConfigMaps, you can easily revert to a previous version if a new version causes issues. You can version ConfigMaps manually by creating new ConfigMaps for each change or automatically using a tool like Helm.
-
Use ConfigMaps in conjunction with other Kubernetes resources: ConfigMaps are just one of many resources in a Kubernetes cluster. To manage application configuration effectively, you need to use ConfigMaps in conjunction with other resources like Secrets and Deployments. For example, you could use a ConfigMap to manage non-sensitive configuration data and a Secret to manage sensitive data like passwords and API keys.
-
Monitor ConfigMap usage: Monitoring ConfigMap usage is essential for ensuring that they are up-to-date and secure. By monitoring ConfigMap usage, you can quickly identify any issues and take action to resolve them. You can monitor ConfigMaps using tools like Prometheus, Grafana, or Kubernetes Dashboard.
In conclusion, Kubernetes ConfigMaps are a powerful tool for managing configuration data in a Kubernetes cluster. By following best practices like using labels and annotations, versioning ConfigMaps, using ConfigMaps in conjunction with other Kubernetes resources, and monitoring ConfigMap usage, you can manage application configuration effectively and ensure that your applications run smoothly.
Real-World Examples of Kubernetes ConfigMaps: Success Stories and Lessons Learned
Kubernetes ConfigMaps have become a popular choice for managing configuration data in containerized applications. Companies and organizations across various industries have adopted ConfigMaps to streamline their development and deployment processes. Here are some real-world examples of how businesses are using ConfigMaps and the lessons they have learned along the way.
Example 1: Managing Microservices Configurations
A leading e-commerce company used Kubernetes ConfigMaps to manage the configurations of its microservices-based architecture. By using ConfigMaps, the company was able to separate configuration data from container images, making it easier to manage and update applications. The company also used labels and annotations to organize ConfigMaps based on the environment and application, enabling developers to quickly locate and modify configurations.
Example 2: Centralizing Configuration Management
A financial services company used Kubernetes ConfigMaps to centralize its configuration management across multiple environments. By using ConfigMaps, the company was able to reduce the complexity of managing configuration data across different teams and environments. The company also used versioning to track changes and enable rollbacks, ensuring that configurations were up-to-date and secure.
Example 3: Automating Configuration Management
A software development company used Kubernetes ConfigMaps to automate its configuration management process. By using ConfigMaps in conjunction with other Kubernetes resources like Deployments and Secrets, the company was able to create a fully automated deployment pipeline. The company also used tools like Helm to version ConfigMaps, enabling developers to quickly roll back changes if necessary.
Lessons Learned
These real-world examples highlight some best practices for using Kubernetes ConfigMaps effectively. Here are some lessons learned from these examples:
-
Use labels and annotations to organize ConfigMaps based on the environment and application.
-
Version ConfigMaps to track changes and enable rollbacks.
-
Use ConfigMaps in conjunction with other Kubernetes resources to automate deployment pipelines.
-
Monitor ConfigMap usage to ensure that they are up-to-date and secure.
In conclusion, Kubernetes ConfigMaps have become a popular choice for managing configuration data in containerized applications. By learning from real-world examples and best practices, you can effectively use ConfigMaps to streamline your development and deployment processes.
Comparing Kubernetes ConfigMaps to Other Configuration Management Solutions: Pros and Cons
Kubernetes ConfigMaps are a powerful tool for managing configuration data in containerized applications. However, they are not the only solution available. Here, we will compare ConfigMaps to other configuration management solutions, such as environment variables, command-line arguments, and configuration files, and discuss the advantages and disadvantages of each approach.
Environment Variables
Environment variables are a common way to manage configuration data in applications. They are simple to use and easy to set up. However, they have some limitations compared to ConfigMaps.
-
Environment variables are not versioned, making it difficult to track changes and enable rollbacks.
-
Environment variables can be difficult to manage in a microservices architecture, where applications are composed of many small, loosely coupled services.
-
Environment variables can be leaked, exposing sensitive data to unauthorized users.
Command-Line Arguments
Command-line arguments are another way to manage configuration data in applications. They are flexible and can be easily changed at runtime. However, they have some limitations compared to ConfigMaps.
-
Command-line arguments can be difficult to manage in a distributed system, where applications are running on multiple nodes.
-
Command-line arguments can be easily exposed, making it difficult to keep data secure.
-
Command-line arguments can be verbose and difficult to read, making it hard to debug issues.
Configuration Files
Configuration files are a common way to manage configuration data in applications. They are flexible and can be easily changed without rebuilding the application. However, they have some limitations compared to ConfigMaps.
-
Configuration files can be difficult to manage in a distributed system, where applications are running on multiple nodes.
-
Configuration files can be easily exposed, making it difficult to keep data secure.
-
Configuration files can be verbose and difficult to read, making it hard to debug issues.
When to Use ConfigMaps
ConfigMaps are best suited for managing configuration data in containerized applications, particularly in a microservices architecture. They offer several advantages over other configuration management solutions, such as versioning, ease of management, and security. Here are some scenarios where ConfigMaps are the best choice:
-
When managing configuration data for multiple microservices.
-
When managing configuration data that changes frequently.
-
When managing sensitive data that needs to be kept secure.
In conclusion, Kubernetes ConfigMaps are a powerful tool for managing configuration data in containerized applications. While there are other configuration management solutions available, ConfigMaps offer several advantages, such as versioning, ease of management, and security. By understanding the pros and cons of each approach, you can make an informed decision about when to use ConfigMaps and when to use other solutions.
Security Considerations for Kubernetes ConfigMaps: Keeping Your Data Safe
While Kubernetes ConfigMaps offer many benefits for managing configuration data in containerized applications, it’s important to consider security when using them. Here are some best practices for keeping your data safe when using ConfigMaps in Kubernetes.
Encrypt Sensitive Data
If you’re storing sensitive data in ConfigMaps, it’s important to encrypt that data to prevent unauthorized access. Kubernetes supports encryption at rest and in transit, which can help keep your data secure. You can also use third-party tools, such as HashiCorp Vault, to manage secrets and encryption keys.
Limit Access to ConfigMaps
It’s important to limit access to ConfigMaps to only those users who need it. You can use Kubernetes role-based access control (RBAC) to control who can access ConfigMaps and what actions they can perform. You can also use network policies to restrict access to ConfigMaps based on IP address or other criteria.
Monitor ConfigMap Usage
Monitoring ConfigMap usage is essential for detecting and responding to security threats. You can use Kubernetes audit logs to track changes to ConfigMaps and other resources. You can also use third-party tools, such as Prometheus and Grafana, to monitor ConfigMap usage and alert you to any anomalies.
Avoid Storing Sensitive Data in ConfigMaps
While ConfigMaps are a convenient way to manage configuration data, it’s best to avoid storing sensitive data in them whenever possible. Instead, consider using Kubernetes Secrets to manage sensitive data, such as passwords and API keys. Secrets are encrypted by default and offer more robust security features than ConfigMaps.
Best Practices for Secure ConfigMaps
-
Encrypt sensitive data.
-
Limit access to ConfigMaps.
-
Monitor ConfigMap usage.
-
Avoid storing sensitive data in ConfigMaps.
-
Use Kubernetes RBAC and network policies to control access to ConfigMaps.
-
Regularly review and update ConfigMap permissions and access controls.
In conclusion, Kubernetes ConfigMaps offer many benefits for managing configuration data in containerized applications. However, it’s important to consider security when using ConfigMaps. By following best practices, such as encrypting sensitive data, limiting access to ConfigMaps, and monitoring ConfigMap usage, you can keep your data safe and avoid common security risks.
Trends and Future Developments in Kubernetes ConfigMaps: What to Expect
Kubernetes ConfigMaps have become an essential tool for managing configuration data in containerized applications. As the container orchestration landscape continues to evolve, we can expect to see new features and capabilities in ConfigMaps that will make them even more powerful and flexible. Here are some trends and future developments to watch for in Kubernetes ConfigMaps.
Integration with Other Kubernetes Resources
As Kubernetes continues to evolve, we can expect to see closer integration between ConfigMaps and other Kubernetes resources, such as Deployments, StatefulSets, and DaemonSets. This integration will make it easier to manage configuration data across different resources and ensure that applications are configured correctly.
Emerging Best Practices
As more companies and organizations adopt Kubernetes ConfigMaps, we can expect to see emerging best practices for using ConfigMaps effectively. These best practices may include using ConfigMaps in conjunction with other configuration management solutions, such as environment variables and command-line arguments, and using labels and annotations to organize ConfigMaps more effectively.
New Features and Capabilities
Kubernetes ConfigMaps are constantly evolving, and we can expect to see new features and capabilities added in future releases. For example, Kubernetes 1.21 added support for ConfigMap volumes, which allow you to mount ConfigMaps as volumes in Pods. This feature makes it easier to share configuration data between containers in a Pod and ensures that applications have access to the latest configuration data.
Staying Up-to-Date with the Latest Developments
To stay up-to-date with the latest developments in Kubernetes ConfigMaps, it’s essential to follow the Kubernetes community and participate in discussions and events. You can also use tools, such as Kubernetes SIG Config and Owners, to track changes and provide feedback on new features and capabilities.
Best Practices for Staying Up-to-Date
-
Follow the Kubernetes community and participate in discussions and events.
-
Use tools, such as Kubernetes SIG Config and Owners, to track changes and provide feedback on new features and capabilities.
-
Experiment with new features and capabilities in a testing or development environment before deploying them in production.
-
Regularly review and update your ConfigMap usage to ensure that you’re using the latest best practices and features.
In conclusion, Kubernetes ConfigMaps are a powerful tool for managing configuration data in containerized applications. By staying up-to-date with the latest trends and future developments, you can ensure that you’re using ConfigMaps effectively and taking advantage of the latest features and capabilities. By following best practices, such as integrating ConfigMaps with other Kubernetes resources and participating in the Kubernetes community, you can stay ahead of the curve and make the most of Kubernetes ConfigMaps for your containerized applications.
Conclusion: Making the Most of Kubernetes ConfigMaps for Your Containerized Applications
Kubernetes ConfigMaps are a powerful tool for managing configuration data in containerized applications. By separating configuration from container images, you can make it easier to manage and update applications, reduce image size, and improve security. In this article, we’ve covered everything you need to know to get started with Kubernetes ConfigMaps, from creating and managing ConfigMaps to best practices for using them effectively.
To recap, we’ve discussed the following topics:
-
Understanding Kubernetes ConfigMaps and their importance in container orchestration.
-
Creating and managing ConfigMaps using the `kubectl` command-line interface and YAML files.
-
Best practices for using ConfigMaps, such as using labels and annotations, versioning ConfigMaps, and using ConfigMaps with other Kubernetes resources like Secrets and Deployments.
-
Real-world examples of companies and organizations using Kubernetes ConfigMaps to manage their containerized applications.
-
Comparing Kubernetes ConfigMaps to other configuration management solutions, such as environment variables, command-line arguments, and configuration files.
-
Security considerations for using Kubernetes ConfigMaps, such as encrypting sensitive data, limiting access to ConfigMaps, and monitoring ConfigMap usage.
-
Trends and future developments in Kubernetes ConfigMaps, such as new features and capabilities, integration with other Kubernetes resources, and emerging best practices.
To make the most of Kubernetes ConfigMaps for your containerized applications, follow these actionable steps:
-
Separate configuration data from container images to make it easier to manage and update applications.
-
Use Kubernetes ConfigMaps to store and manage configuration data in a Kubernetes cluster.
-
Follow best practices for using ConfigMaps, such as using labels and annotations, versioning ConfigMaps, and using ConfigMaps with other Kubernetes resources like Secrets and Deployments.
-
Encrypt sensitive data, limit access to ConfigMaps, and monitor ConfigMap usage to ensure data security.
-
Stay up-to-date with the latest trends and future developments in Kubernetes ConfigMaps to ensure that you’re using them effectively.
For further learning and exploration, consider the following resources:
By following best practices and staying up-to-date with the latest developments in Kubernetes ConfigMaps, you can ensure that you’re using them effectively to manage your containerized applications. With the power of Kubernetes ConfigMaps, you can simplify configuration management, reduce image size, and improve security for your containerized applications.