Understanding Kubernetes Context and Current Context
A Kubernetes context encapsulates the connection details necessary for `kubectl` to interact with a specific Kubernetes cluster. It bundles the cluster’s API server address, credentials for authentication, and a default namespace. The `kubectl` command-line tool leverages these contexts to direct commands to the intended cluster and namespace. Properly configured contexts are crucial for managing multiple Kubernetes environments, such as development, staging, and production. It’s essential to differentiate between a context and the current context. The former is a stored set of access parameters, while the latter indicates which context `kubectl` is actively using. To avoid unintended actions, especially in production environments, one must accurately set and manage contexts. Users can leverage `kubectl check context` to ensure operations are directed to the right place. This simple command verifies that your connection is pointing to the intended Kubernetes environment.
The importance of correctly setting and managing contexts cannot be overstated. Using the wrong context can lead to deployments in the wrong environment, resulting in potentially disastrous consequences. For example, accidentally deploying a development application to a production cluster could disrupt live services and compromise data. Therefore, developers and operators should always double-check their current context before executing any `kubectl` commands. Think of a Kubernetes context as a profile. It is used to connect to a cluster, and the current context is the profile currently in use. A proactive approach to validating the current context is essential for maintaining the integrity and stability of Kubernetes deployments. This highlights the importance of a `kubectl check context` strategy.
Managing contexts effectively is critical for teams working with multiple Kubernetes clusters. It helps to ensure consistency and reduces the risk of human error. Tools like `kubectx` and `kubens` can simplify context switching, but understanding the underlying concepts remains essential. Regularly reviewing and updating context configurations is also a good practice, especially as clusters evolve or credentials change. By following these guidelines and practicing diligence, teams can confidently manage their Kubernetes environments and minimize the risk of costly mistakes. Using `kubectl check context` is not a one-time activity but an ongoing part of managing the environment. In summary, understanding and validating Kubernetes contexts are paramount for the safe and efficient operation of Kubernetes clusters, and `kubectl check context` is a key part of that validation.
How to Verify Your Kubernetes Context Using Kubectl
To verify your Kubernetes context, the `kubectl` command-line tool offers a straightforward method to display the currently active context. This is crucial for ensuring that subsequent `kubectl` commands are executed against the intended cluster and namespace. The command `kubectl config current-context` reveals the name of the context that `kubectl` is presently using.
To `kubectl check context`, execute the following command in your terminal:
kubectl config current-context
The expected output will be the name of the current context. For example:
my-cluster-dev
This indicates that all subsequent `kubectl` commands will be directed towards the cluster and namespace defined within the `my-cluster-dev` context. This is a vital step to `kubectl check context` and avoid unintended actions on production or other sensitive environments. If no context is configured, the command will return an empty string or an error message. This usually means that the Kubernetes configuration file (`~/.kube/config`) is missing or improperly set up. To resolve this, ensure that the `KUBECONFIG` environment variable is correctly pointing to a valid configuration file, or that the default configuration file exists and contains the necessary context information. In situations where you encounter an incorrect configuration file, carefully examine and correct its contents, paying close attention to the server address, credentials, and namespace definitions. Using `kubectl check context` is a primary task for any cluster operator.
Common errors include “No context is currently set” or an empty output. This typically indicates that the Kubernetes configuration file is either missing, corrupted, or does not contain any valid context definitions. Another potential issue is an incorrect path to the configuration file. `kubectl` relies on the `KUBECONFIG` environment variable to locate the configuration file. Ensure this variable is correctly set. If the path is correct and the file exists, verify that the file contains valid context configurations. The configuration file is usually located in the home directory under `.kube/config`. When troubleshooting, carefully examine the configuration file for any syntax errors or inconsistencies. Remember to `kubectl check context` before executing potentially harmful commands.
Exploring Available Kubernetes Contexts
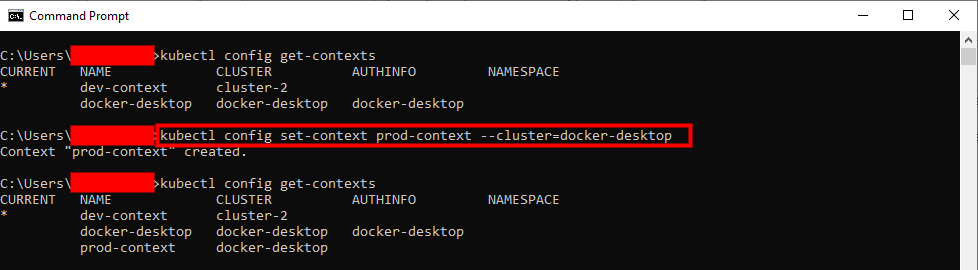
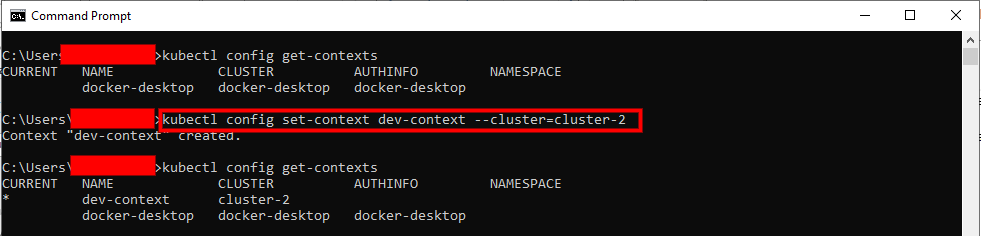
To effectively manage multiple Kubernetes clusters, understanding how to list available contexts is crucial. The `kubectl config get-contexts` command provides a comprehensive view of all configured contexts. This command allows users to see the names of the contexts, the associated clusters, the authentication information, and the default namespaces, enabling informed decisions about which context to use. Ensuring you `kubectl check context` regularly is essential for maintaining control over your deployments. The `kubectl check context` process starts with listing the contexts.
Executing `kubectl config get-contexts` in the terminal yields a table-like output. A code snippet of this command is:
kubectl config get-contextsThe output typically includes the following columns:
- NAME: The unique name assigned to the context. This is how you reference the context when switching between clusters.
- CLUSTER: The name of the Kubernetes cluster associated with this context. It points to the specific cluster endpoint.
- AUTHINFO: The authentication information used to authenticate with the cluster. This often refers to a user or service account.
- NAMESPACE: The default namespace used when interacting with the cluster using this context. This can be overridden with the `–namespace` flag.
Each row in the output represents a different Kubernetes context, providing a quick overview of your available connections. Understanding these columns is key to effectively managing your Kubernetes environments and being able to `kubectl check context` when needed.
The ability to list and understand available Kubernetes contexts is fundamental for anyone working with multiple clusters. By using `kubectl config get-contexts`, users can quickly identify and verify their configured contexts, preventing accidental deployments to the wrong environment. This command, combined with a clear understanding of the output columns, empowers users to `kubectl check context` for robust and error-free Kubernetes management. This ensures that you are always targeting the correct cluster and namespace, reducing the risk of misconfiguration and deployment errors. Regularly using this command will assist in preventing issues related to incorrect context usage. Remember to `kubectl check context` to keep deployments in order.
Validating Kubernetes Context: Checking Connection and Access
Simply having a context configured within your `kubectl` environment doesn’t automatically ensure a functional connection to the intended Kubernetes cluster. A context might exist in your configuration file, but the underlying connection details, such as credentials or network settings, could be outdated or incorrect. Therefore, it’s essential to actively validate that your `kubectl check context` setup is working as expected.
To effectively `kubectl check context`, initiate a basic command against the cluster using the configured context. A common and straightforward approach involves using `kubectl get pods`. This command attempts to retrieve a list of all pods running in the default namespace of the cluster defined by your current context. Execute this command in your terminal: `kubectl get pods`. If the context is correctly configured and your user has the necessary permissions, `kubectl` will display a table containing information about the pods. However, if issues exist, you’ll encounter errors. For instance, a “connection refused” error suggests a network problem or that the Kubernetes API server is unreachable. An “unauthorized” error indicates that your credentials lack the necessary permissions to perform the requested action. These errors highlight the importance to `kubectl check context` for a successful interaction.
Encountering errors while attempting to `kubectl check context` requires further investigation. Check your credentials for accuracy, especially if you are using tokens or client certificates. Verify network connectivity between your machine and the Kubernetes API server. Examine your RBAC (Role-Based Access Control) settings to ensure your user or service account has the appropriate roles and permissions to access the resources you’re trying to manage. Using `kubectl check context` regularly can proactively identify and resolve connectivity or authorization issues, ensuring smooth and secure interaction with your Kubernetes clusters. Regularly using `kubectl check context` saves time in the long run. Ensuring appropriate RBAC policies also improves `kubectl check context` process.
Advanced Kubernetes Context Verification Techniques
Beyond basic connectivity, validating a Kubernetes context involves ensuring adequate permissions for intended operations. Simply having a configured context doesn’t guarantee the ability to perform specific actions within the cluster. One powerful method for performing a kubectl check context involves leveraging the `kubectl auth can-i` command. This command assesses whether the current user, associated with the active context, possesses the necessary authorization to execute a particular action on a specific resource. For instance, running `kubectl auth can-i get pods` verifies if the user can retrieve pod information. A “yes” response confirms sufficient permissions, while a “no” indicates an RBAC (Role-Based Access Control) issue or lack of authorization.
RBAC issues are a common cause of context validation failures. These issues arise when the user associated with the context lacks the necessary roles or permissions to interact with the cluster’s resources. Examining the output of `kubectl auth can-i` can pinpoint the specific actions that are unauthorized, facilitating targeted RBAC policy adjustments. This command offers a granular approach to kubectl check context, enabling administrators to diagnose and resolve permission-related problems effectively. Another valuable tool for advanced context verification is the `kubectl cluster-info` command. This command retrieves comprehensive details about the targeted cluster, including its Kubernetes version, API endpoint, and other relevant information. Successful execution of this command confirms connectivity to the cluster’s API server and provides insights into the cluster’s configuration. Any errors encountered during the execution of `kubectl cluster-info` may indicate network connectivity problems or API server unavailability. Using `kubectl cluster-info` to kubectl check context ensures that the context is valid and points to a functional Kubernetes cluster.
By combining `kubectl auth can-i` and `kubectl cluster-info`, a comprehensive assessment of a Kubernetes context’s validity can be achieved. The `kubectl auth can-i` command verifies user permissions, while `kubectl cluster-info` confirms cluster connectivity and provides cluster details. Employing these techniques allows administrators to proactively identify and address potential issues, ensuring seamless interaction with Kubernetes clusters. Furthermore, these commands aid in debugging RBAC configurations and troubleshooting connectivity problems, making them invaluable tools for maintaining a healthy and secure Kubernetes environment. Always ensure to kubectl check context regularly to prevent unexpected deployment failures or access denials.
Tools and Utilities for Managing Kubernetes Contexts Effectively
Managing Kubernetes contexts efficiently is crucial for developers and operators working with multiple clusters or namespaces. While `kubectl` provides the fundamental commands for context management, several tools enhance productivity and minimize the risk of errors. These utilities offer more intuitive interfaces and streamlined workflows, making context switching and namespace management significantly easier. When you kubectl check context, these tools provide a faster, more user-friendly approach.
One popular tool is `kubectx`, which simplifies switching between Kubernetes contexts. Instead of typing lengthy `kubectl config use-context
These tools not only enhance speed but also improve accuracy. By reducing the amount of typing required, they minimize the potential for typos and configuration errors, this is very helpful to kubectl check context without issues. Furthermore, they often provide visual cues, such as customized shell prompts, to indicate the currently active context and namespace. This helps prevent accidental deployments to the wrong environment. For those looking to kubectl check context more efficiently, incorporating tools like `kubectx` and `kubens` into your workflow is highly recommended. You can find more information and installation instructions on their respective GitHub repositories. Using these tools, teams can kubectl check context and ensure their configurations are correct while streamlining their day-to-day operations.
Troubleshooting Common Kubernetes Context Issues
Several issues can arise when working with Kubernetes contexts. Connection problems, permission errors, and misconfigured contexts are among the most common. Effective troubleshooting is essential for maintaining a stable and accessible Kubernetes environment. When facing connection problems, the first step is to verify network connectivity to the Kubernetes API server. Firewalls or network policies might be blocking access. Ensure that the `kubectl` configuration file, typically located at `~/.kube/config`, is correctly configured with the right server address and credentials. Using `kubectl check context` involves ensuring that the defined cluster endpoint is reachable from your current network.
Permission errors often manifest as “unauthorized” or “forbidden” messages when attempting to execute `kubectl` commands. These errors indicate that the currently active context does not have the necessary RBAC (Role-Based Access Control) permissions to perform the requested action. To diagnose RBAC issues, examine the roles and role bindings associated with the service account or user defined in the context’s `AUTHINFO`. Use `kubectl auth can-i get pods` to check if the current user has permission to retrieve pods within the current context. If the context is misconfigured, `kubectl check context` may fail. This could be due to incorrect cluster details, invalid credentials, or corrupted configuration files. Manually inspect the `~/.kube/config` file for any discrepancies or errors. Consider recreating the context using the correct cluster information and credentials if necessary. Regularly validating contexts with `kubectl check context` helps to proactively identify and resolve configuration problems before they impact deployments or operations.
Debugging tips include using the `-v` flag with `kubectl` commands to increase verbosity and gain more insight into the API requests and responses. This can help pinpoint the exact cause of errors. Examine the Kubernetes API server logs for more detailed error messages and audit trails. These logs can provide valuable clues about authentication failures or authorization issues. Consider using tools like `kubectx` and `kubens` to simplify context switching and management, reducing the risk of accidentally executing commands in the wrong context. Remember to always validate your current context using `kubectl config current-context` before performing any critical operations. Properly configured and validated contexts are crucial for avoiding unintended consequences and maintaining the integrity of your Kubernetes deployments. Always `kubectl check context` before applying changes.
Best Practices for Long-Term Kubernetes Context Management
Effective Kubernetes context management is crucial for maintaining a secure and scalable infrastructure. Implementing robust strategies ensures smooth operations and prevents accidental deployments. Using descriptive context names is a foundational best practice. Names should clearly indicate the environment (e.g., `production`, `staging`, `development`) and the cluster’s purpose. This clarity helps prevent misconfiguration and reduces the risk of deploying to the wrong environment. Secure storage of context configurations is equally important. The `kubectl` configuration file (`~/.kube/config`) contains sensitive information, including credentials. Protecting this file from unauthorized access is paramount. Consider using encrypted storage solutions or implementing strict access controls to safeguard the configuration data. Regularly reviewing and updating contexts is also essential. Kubernetes clusters and access policies evolve over time. Regularly checking the validity of contexts and updating them as needed ensures continued connectivity and proper authorization. This proactive approach helps prevent connection errors and permission issues. To proactively validate your context, consider a regular `kubectl check context` verification as part of an automated script.
Proper Role-Based Access Control (RBAC) policies are fundamental to secure Kubernetes context management. RBAC controls who can access what resources within a cluster. Implementing granular RBAC policies ensures that users and applications only have the necessary permissions. This minimizes the risk of unauthorized actions and data breaches. Automation and Infrastructure-as-Code (IaC) are crucial for managing contexts in large-scale Kubernetes environments. Manual context management becomes cumbersome and error-prone as the number of clusters and namespaces grows. IaC tools like Terraform or Ansible allow you to define and manage contexts programmatically. This ensures consistency, repeatability, and simplifies the process of creating, updating, and deleting contexts. With IaC, you can easily `kubectl check context` via automated workflows on a scheduled daily cadence for example. Infrastructure as Code (IaC) with `kubectl check context` verification will help in large scale context deployments.
For a secure context management, employ best practices for securing the `kubectl` configuration file. Regularly rotate credentials used within your contexts, particularly if you suspect a compromise. Use short-lived tokens whenever possible to limit the potential impact of stolen credentials. Employ audit logging to track context usage and identify any suspicious activity. Monitoring context usage helps detect unauthorized access attempts or misconfigurations. Integrate `kubectl check context` commands into your monitoring dashboards to get a better understanding of the context status across all clusters. Also use tools like `kubectx` and `kubens` to easily switch between contexts and namespaces, but always confirm the current context before executing any critical commands. This helps prevent accidental deployments to the wrong environment and promotes a more secure and efficient workflow. Consistent and secure Kubernetes context management is crucial for maintaining a healthy and reliable Kubernetes environment, regular `kubectl check context` executions will aid in validating the connections.