What is K8s NetworkPolicy and Why is it Important?
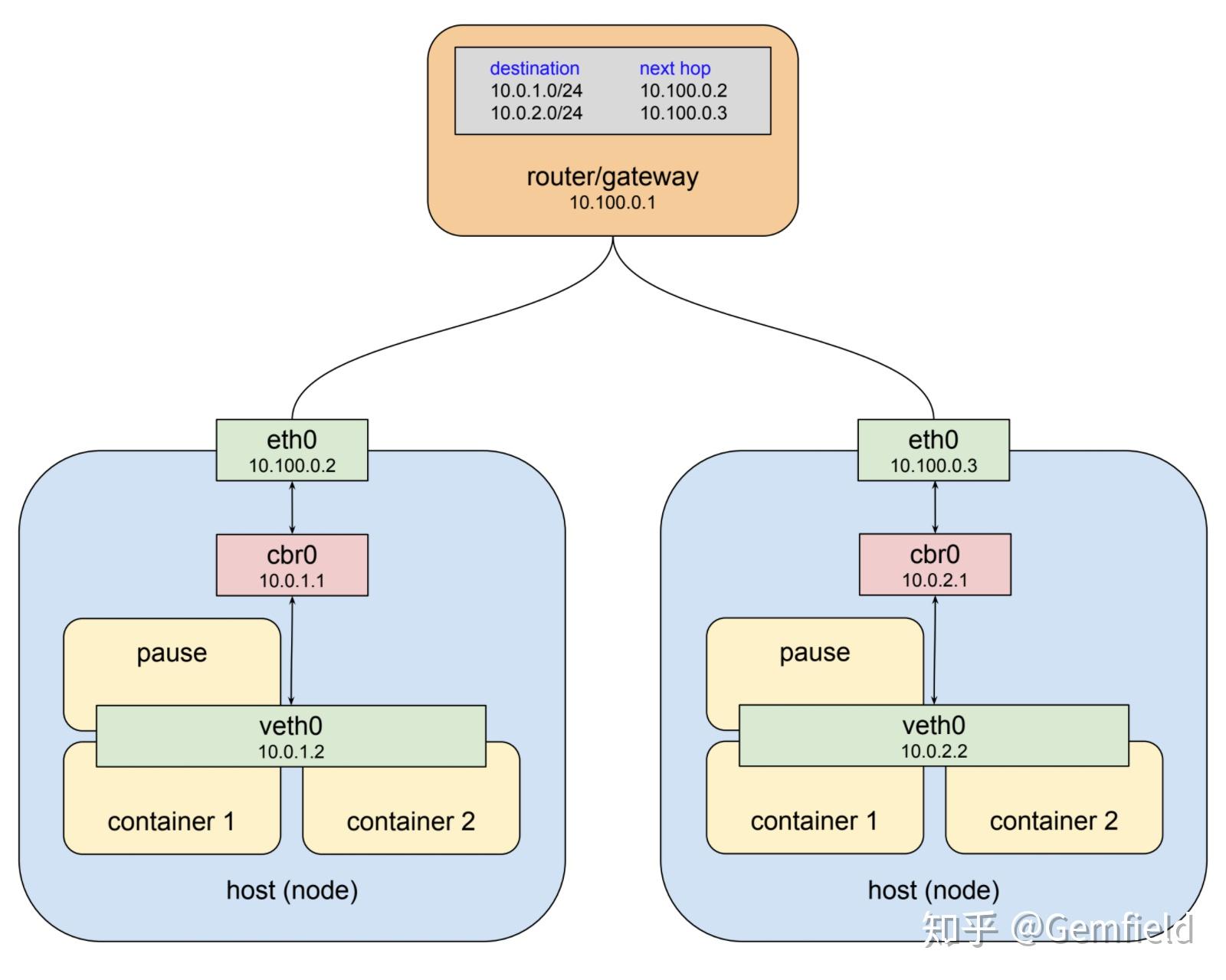
K8s NetworkPolicy is a feature in Kubernetes that allows for the management and securing of network traffic within a cluster. By defining policies, users can control how pods communicate with each other and the outside world, improving security, network segmentation, and traffic control. The importance of K8s NetworkPolicy lies in its ability to provide a more secure and efficient network infrastructure for Kubernetes clusters. With the increasing use of microservices and containerized applications, the need for effective network management and security has become more critical than ever. K8s NetworkPolicy enables users to define and enforce network policies that align with their specific security and compliance requirements.
By implementing K8s NetworkPolicy, users can prevent unauthorized access to their applications and data, reduce the risk of data breaches, and improve overall network performance. Additionally, K8s NetworkPolicy can help organizations meet regulatory compliance requirements, such as HIPAA and PCI-DSS, by providing a way to control and monitor network traffic.
In summary, K8s NetworkPolicy is an essential feature for securing and managing network traffic within a Kubernetes cluster. By understanding its key components and implementing best practices, users can improve their network security, segmentation, and traffic control, leading to a more efficient and secure infrastructure.
Key Components of a K8s NetworkPolicy
K8s NetworkPolicy is a powerful feature that enables users to control and manage network traffic within a Kubernetes cluster. To create effective NetworkPolicies, it is essential to understand the key components that make up a policy. These components include podSelector, policyTypes, and ingress/egress rules. PodSelector is a label selector that matches pods to which the NetworkPolicy applies. By using label selectors, users can define policies that apply to specific pods or groups of pods. For example, a user could create a NetworkPolicy that applies only to pods with the label “tier=frontend”.
PolicyTypes is an optional field that specifies the types of traffic to be evaluated by the NetworkPolicy. The available policy types are Ingress and Egress, which control incoming and outgoing traffic, respectively. By default, both Ingress and Egress traffic are evaluated.
Ingress and Egress rules define the traffic that is allowed or denied by the NetworkPolicy. These rules consist of a series of port, protocol, and source/destination IP address pairs. For example, a user could create an Ingress rule that allows traffic from a specific IP address on port 80.
Here is an example of a simple K8s NetworkPolicy that allows traffic from a specific IP address on port 80:
yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-traffic-from-ip
spec:
podSelector:
matchLabels:
app: my-app
ingress:
– from:
– ipBlock:
cidr: 10.0.0.0/24
ports:
– protocol: TCP
port: 80
In this example, the NetworkPolicy applies to pods with the label “app=my-app” and allows traffic from the IP address range 10.0.0.0/24 on port 80.
When designing K8s NetworkPolicy, it is essential to follow best practices to ensure effective network security and traffic management. These practices include segmenting traffic, creating allowlists and blocklists, and monitoring and auditing NetworkPolicy for security and compliance purposes.
In summary, K8s NetworkPolicy is a powerful feature that enables users to control and manage network traffic within a Kubernetes cluster. By understanding the key components of a NetworkPolicy, including podSelector, policyTypes, and ingress/egress rules, users can create effective policies that improve network security and traffic management.
How to Implement K8s NetworkPolicy in Your Cluster
Implementing K8s NetworkPolicy in your Kubernetes cluster can help improve network security and traffic management. Here are the steps required to implement K8s NetworkPolicy:
Select a network plugin: Before implementing K8s NetworkPolicy, you need to select a network plugin that supports NetworkPolicy. Popular network plugins that support NetworkPolicy include Calico, Cilium, and Flannel.
Configure NetworkPolicy resources: Once you have selected a network plugin, you need to configure NetworkPolicy resources. NetworkPolicy resources define the rules that control network traffic within your cluster. Here is an example of a simple NetworkPolicy resource that allows traffic from a specific IP address on port 80:
yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-traffic-from-ip
spec:
podSelector:
matchLabels:
app: my-app
ingress:
– from:
– ipBlock:
cidr: 10.0.0.0/24
ports:
– protocol: TCP
port: 80
Test the policies: After configuring NetworkPolicy resources, you need to test the policies to ensure they are working as expected. You can use tools like kubectl to test the policies by creating test pods and checking the network traffic.
Monitor the policies: Once the policies are implemented and tested, you need to monitor them for security and compliance purposes. You can use tools like Prometheus and Grafana to monitor the NetworkPolicy resources and alert you to any issues.
When implementing K8s NetworkPolicy, it is essential to follow best practices to ensure effective network security and traffic management. These practices include segmenting traffic, creating allowlists and blocklists, and monitoring and auditing NetworkPolicy for security and compliance purposes.
In summary, implementing K8s NetworkPolicy in your Kubernetes cluster can help improve network security and traffic management. By selecting a network plugin, configuring NetworkPolicy resources, testing the policies, and monitoring them for security and compliance purposes, you can ensure effective network security and traffic management within your cluster.
Best Practices for Designing K8s NetworkPolicy
Designing effective K8s NetworkPolicy is crucial for securing and managing network traffic within a Kubernetes cluster. Here are some best practices to follow when designing K8s NetworkPolicy:
Segment traffic: Segmenting traffic is essential for improving network security and reducing the attack surface. You can segment traffic by creating separate NetworkPolicy resources for different applications, services, or tiers within your cluster.
Create allowlists and blocklists: Allowlists and blocklists are essential for controlling network traffic. Allowlists specify the sources or destinations that are allowed to communicate with a pod, while blocklists specify the sources or destinations that are blocked.
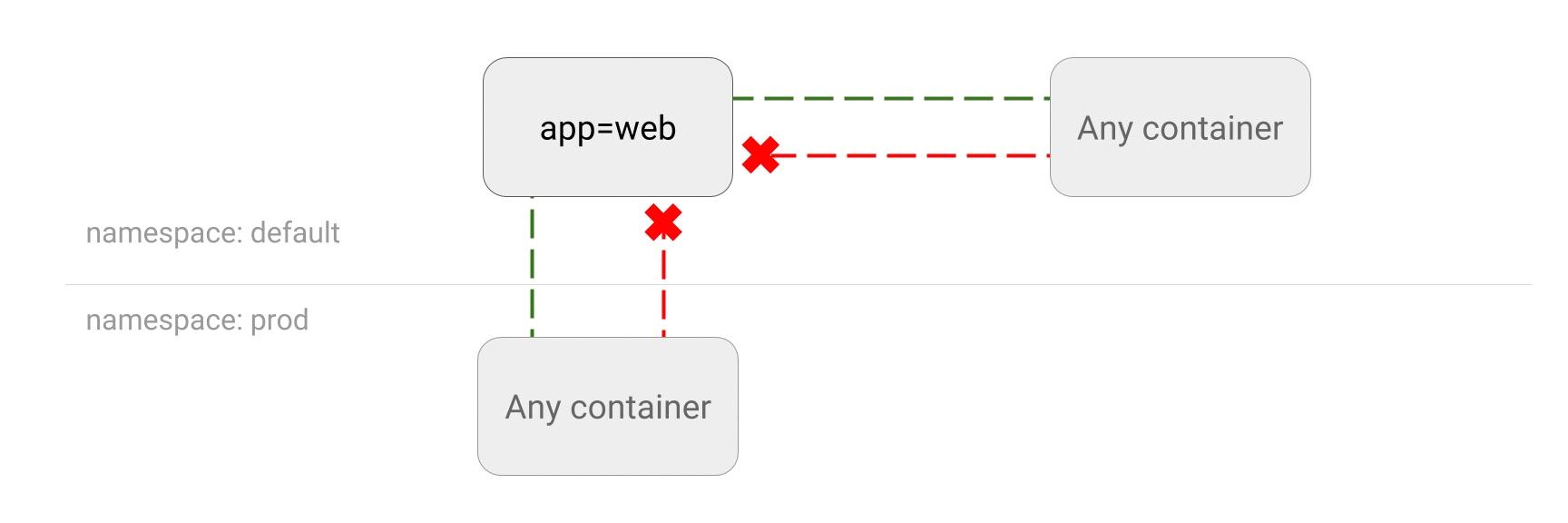
Use namespaces: Namespaces are a way to divide a cluster into virtual clusters. You can use namespaces to isolate different applications, services, or teams within your cluster. When designing K8s NetworkPolicy, you can apply policies to specific namespaces to control network traffic.
Monitor and audit NetworkPolicy: Monitoring and auditing NetworkPolicy is essential for ensuring security and compliance. You can use tools like Prometheus and Grafana to monitor NetworkPolicy resources and alert you to any issues.
Test policies: Testing policies is crucial for ensuring that they are working as expected. You can use tools like kubectl to test the policies by creating test pods and checking the network traffic.
Use labels: Labels are a way to organize and select objects in Kubernetes. When designing K8s NetworkPolicy, you can use labels to select pods or namespaces to which the policy applies.
Use policy types: Policy types are a way to specify the types of traffic to be evaluated by the NetworkPolicy. The available policy types are Ingress and Egress, which control incoming and outgoing traffic, respectively.
Use ingress and egress rules: Ingress and egress rules define the traffic that is allowed or denied by the NetworkPolicy. These rules consist of a series of port, protocol, and source/destination IP address pairs.
In summary, designing effective K8s NetworkPolicy requires following best practices such as segmenting traffic, creating allowlists and blocklists, using namespaces, monitoring and auditing NetworkPolicy, testing policies, using labels, policy types, and ingress and egress rules. By following these best practices, you can ensure effective network security and traffic management within your cluster.
Real-World Examples of K8s NetworkPolicy
K8s NetworkPolicy is a powerful tool for securing and managing network traffic within a Kubernetes cluster. Here are some real-world examples of how organizations have used K8s NetworkPolicy to improve their network security and traffic management:
Example 1: Segmenting Traffic for a Multi-Tier Application
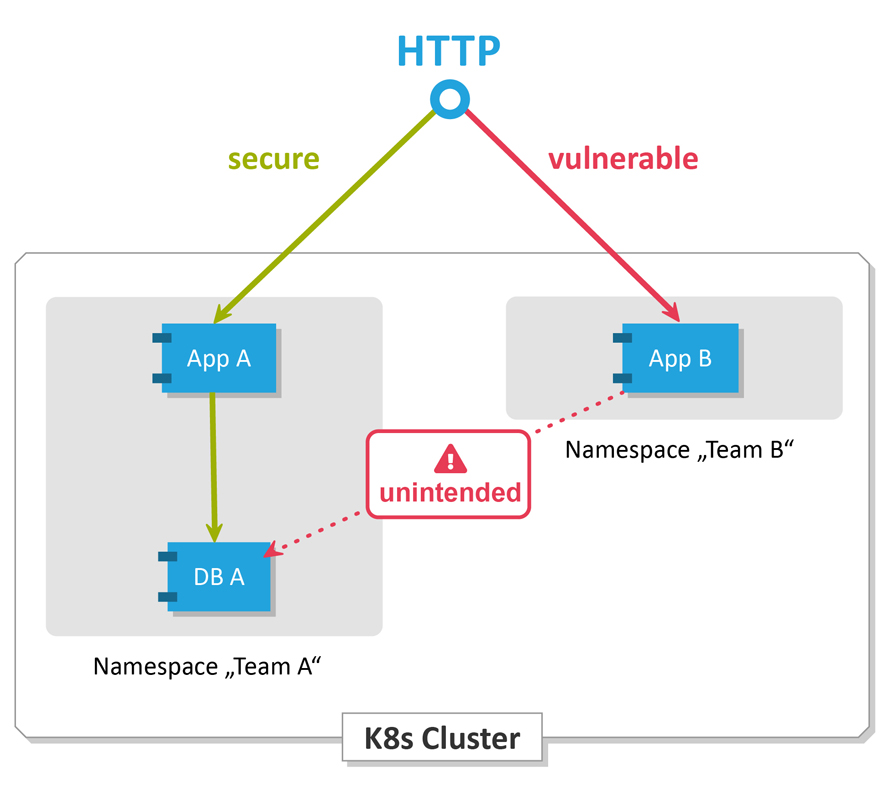
A financial services company wanted to segment traffic for a multi-tier application running in a Kubernetes cluster. They created separate NetworkPolicy resources for the frontend, backend, and database tiers of the application. The policies allowed traffic only between the tiers that needed to communicate with each other, reducing the attack surface and improving security.
Example 2: Allowing Traffic from Specific IP Addresses
A healthcare organization wanted to allow traffic only from specific IP addresses to a Kubernetes cluster running sensitive workloads. They created NetworkPolicy resources that allowed traffic only from the specified IP addresses, improving security and meeting compliance requirements.
Example 3: Blocking Traffic from Specific IP Addresses
A retail company wanted to block traffic from specific IP addresses that were known to be sources of malicious traffic. They created NetworkPolicy resources that blocked traffic from the specified IP addresses, improving security and reducing the risk of attacks.
Example 4: Allowing Traffic Only During Specific Hours
A manufacturing company wanted to allow traffic only during specific hours to a Kubernetes cluster running non-critical workloads. They created NetworkPolicy resources that allowed traffic only during the specified hours, reducing the risk of attacks and improving security.
Example 5: Auditing NetworkPolicy for Compliance
A government agency wanted to audit NetworkPolicy resources for compliance with security policies. They used tools like Prometheus and Grafana to monitor NetworkPolicy resources and alert them to any issues, ensuring compliance with security policies and improving security.
In summary, K8s NetworkPolicy is a powerful tool for securing and managing network traffic within a Kubernetes cluster. Real-world examples of K8s NetworkPolicy include segmenting traffic for a multi-tier application, allowing traffic from specific IP addresses, blocking traffic from specific IP addresses, allowing traffic only during specific hours, and auditing NetworkPolicy for compliance. By using K8s NetworkPolicy, organizations can improve their network security and traffic management, and meet compliance requirements.
Common Mistakes to Avoid When Implementing K8s NetworkPolicy
Implementing K8s NetworkPolicy can be complex, and there are several common mistakes that organizations should avoid. Here are some common mistakes to avoid when implementing K8s NetworkPolicy:
Mistake 1: Misconfiguring Policies
Misconfiguring NetworkPolicy resources is a common mistake that can lead to security vulnerabilities and network issues. To avoid this mistake, it is essential to double-check the configuration of NetworkPolicy resources and test them thoroughly before deploying them to production.
Mistake 2: Failing to Test Policies
Failing to test NetworkPolicy resources before deploying them to production is a common mistake that can lead to unexpected issues. To avoid this mistake, it is essential to test NetworkPolicy resources thoroughly in a staging environment before deploying them to production.
Mistake 3: Neglecting to Monitor Policies for Changes
Neglecting to monitor NetworkPolicy resources for changes is a common mistake that can lead to security vulnerabilities and network issues. To avoid this mistake, it is essential to monitor NetworkPolicy resources for changes and ensure that they are up-to-date with the latest security policies and requirements.
Mistake 4: Overcomplicating Policies
Overcomplicating NetworkPolicy resources is a common mistake that can lead to confusion and errors. To avoid this mistake, it is essential to keep NetworkPolicy resources simple and easy to understand, focusing on the most critical security and network requirements.
Mistake 5: Failing to Consider the Impact of Policy Changes
Failing to consider the impact of NetworkPolicy changes is a common mistake that can lead to unexpected issues. To avoid this mistake, it is essential to carefully consider the impact of NetworkPolicy changes and test them thoroughly before deploying them to production.
In summary, implementing K8s NetworkPolicy can be complex, and there are several common mistakes that organizations should avoid. These mistakes include misconfiguring policies, failing to test policies, neglecting to monitor policies for changes, overcomplicating policies, and failing to consider the impact of policy changes. By avoiding these mistakes and following best practices, organizations can ensure that NetworkPolicy is implemented effectively and provides the desired network security and traffic management benefits.
Integrating K8s NetworkPolicy with Other Kubernetes Security Tools
K8s NetworkPolicy is a powerful tool for securing and managing network traffic within a Kubernetes cluster, but it is not the only security tool available. Here are some ways to integrate K8s NetworkPolicy with other Kubernetes security tools to improve network security and traffic management:
Network Plugins
Network plugins are software components that enable network communication between pods in a Kubernetes cluster. K8s NetworkPolicy can be integrated with network plugins to provide additional network security features. For example, Calico is a popular network plugin that provides network security policies, network segmentation, and network visibility. By integrating K8s NetworkPolicy with Calico, organizations can create more granular network security policies and improve network visibility.
Network Policies
Network policies are a Kubernetes feature that enables organizations to define network traffic rules for pods. K8s NetworkPolicy can be integrated with network policies to provide more advanced network security features. For example, organizations can use network policies to define network traffic rules based on labels, namespaces, and pod selectors. By integrating K8s NetworkPolicy with network policies, organizations can create more granular network security policies and improve network segmentation.
Security Contexts
Security contexts are a Kubernetes feature that enables organizations to define security settings for pods. K8s NetworkPolicy can be integrated with security contexts to provide more advanced network security features. For example, organizations can use security contexts to define security settings for pods, such as user IDs, group IDs, and capabilities. By integrating K8s NetworkPolicy with security contexts, organizations can create more granular network security policies and improve network security.
Best Practices for Integrating K8s NetworkPolicy with Other Kubernetes Security Tools
Here are some best practices for integrating K8s NetworkPolicy with other Kubernetes security tools:
- Understand the capabilities and limitations of each security tool.
- Define clear network security policies and procedures.
- Test and validate network security policies and procedures regularly.
- Monitor network security policies and procedures for changes and anomalies.
- Implement a disaster recovery and incident response plan.
In summary, integrating K8s NetworkPolicy with other Kubernetes security tools, such as network plugins, network policies, and security contexts, can improve network security and traffic management. By following best practices for integrating K8s NetworkPolicy with other Kubernetes security tools, organizations can create more granular network security policies and improve network segmentation, visibility, and security.
The Future of K8s NetworkPolicy: Trends and Developments
K8s NetworkPolicy is an essential tool for securing and managing network traffic within a Kubernetes cluster, and it is constantly evolving to meet the changing needs of organizations. Here are some trends and developments to watch for in the future of K8s NetworkPolicy:
Increased Adoption of K8s NetworkPolicy
As Kubernetes becomes more popular, the adoption of K8s NetworkPolicy is also expected to increase. This is because K8s NetworkPolicy provides a powerful and flexible way to secure and manage network traffic within a Kubernetes cluster. As more organizations adopt Kubernetes, they are likely to turn to K8s NetworkPolicy to help them secure their clusters and improve their network traffic management.
Improved Integration with Other Security Tools
K8s NetworkPolicy is already integrated with other Kubernetes security tools, such as network plugins, network policies, and security contexts. However, there is still room for improvement in this area. In the future, we can expect to see better integration between K8s NetworkPolicy and other security tools, making it easier for organizations to create comprehensive network security policies and procedures.
More Granular Network Security Policies
As Kubernetes becomes more complex, there is a growing need for more granular network security policies. In the future, we can expect to see K8s NetworkPolicy evolve to meet this need, providing organizations with the ability to create more detailed and specific network security policies. This will enable organizations to better secure their clusters and improve their network traffic management.
Improved Network Visibility
Network visibility is a critical component of network security. In the future, we can expect to see K8s NetworkPolicy evolve to provide better network visibility, making it easier for organizations to monitor their clusters and detect potential security threats. This will enable organizations to respond more quickly to security threats and improve their overall network security.
Best Practices for Preparing for the Future of K8s NetworkPolicy
Here are some best practices for preparing for the future of K8s NetworkPolicy:
- Stay up-to-date with the latest trends and developments in K8s NetworkPolicy.
- Regularly review and update your network security policies and procedures.
- Test and validate your network security policies and procedures regularly.
- Monitor your clusters for changes and anomalies.
- Implement a disaster recovery and incident response plan.
In summary, the future of K8s NetworkPolicy is bright, with trends and developments such as increased adoption, improved integration with other security tools, more granular network security policies, and improved network visibility. By staying up-to-date with these trends and developments and following best practices, organizations can ensure that they are well-prepared for the future of K8s NetworkPolicy and can continue to secure and manage their network traffic effectively.