Protecting Energy Infrastructure from Cyber Threats
Safeguarding the Energy Sector with Effective Incident Response
The energy sector is a critical component of modern society, providing power to homes, businesses, and industries. However, this critical infrastructure is increasingly vulnerable to cyber threats, which can have devastating consequences. A robust incident response plan is essential to prevent or mitigate the impact of these attacks, ensuring the continuity of energy supply and minimizing the risk of disruptions. Incident response for energy system security is a top priority, as the potential consequences of a successful cyber attack can be severe, including power outages, equipment damage, and even physical harm. Effective incident response requires a proactive approach, with a well-planned strategy in place to detect, respond to, and recover from security incidents. By adopting a comprehensive incident response plan, energy organizations can minimize the risk of cyber attacks, protect their systems and data, and ensure the reliability of their services.
Understanding Energy System Vulnerabilities
Energy systems are complex networks comprising various IT and OT (operational technology) infrastructure, making them vulnerable to cyber attacks. These vulnerabilities can be exploited by attackers to disrupt or compromise energy system operations. The potential consequences of such attacks can be severe, including power outages, equipment damage, and even safety risks to humans. Incident response for energy system security requires a deep understanding of these vulnerabilities to develop effective mitigation strategies.
Common energy system vulnerabilities include outdated software, unpatched systems, and weak network security. Network architecture and system design can also create vulnerabilities, such as the connection of IT and OT systems or the use of shared networks for both administrative and control functions. Additionally, insider threats and social engineering tactics can be used by attackers to gain unauthorized access to energy systems. Identifying and addressing these vulnerabilities is critical to preventing or mitigating the impact of cyber attacks on energy systems.
Increased connectivity and the adoption of IoT devices in energy systems have expanded the attack surface, creating more vulnerabilities that can be exploited. Furthermore, the lack of standardization and the use of legacy equipment can make it challenging to implement robust security measures, making incident response for energy system security even more critical.
Threat intelligence and vulnerability assessments can help energy organizations identify potential threats and weaknesses in their systems. Conducting regular security audits and penetration testing can also help identify vulnerabilities and improve incident response preparedness. By understanding the potential vulnerabilities in their systems, energy organizations can proactively develop strategies to prevent or mitigate cyber attacks, ensuring the security and continuity of their operations.
How to Develop a Comprehensive Incident Response Plan for Energy Systems
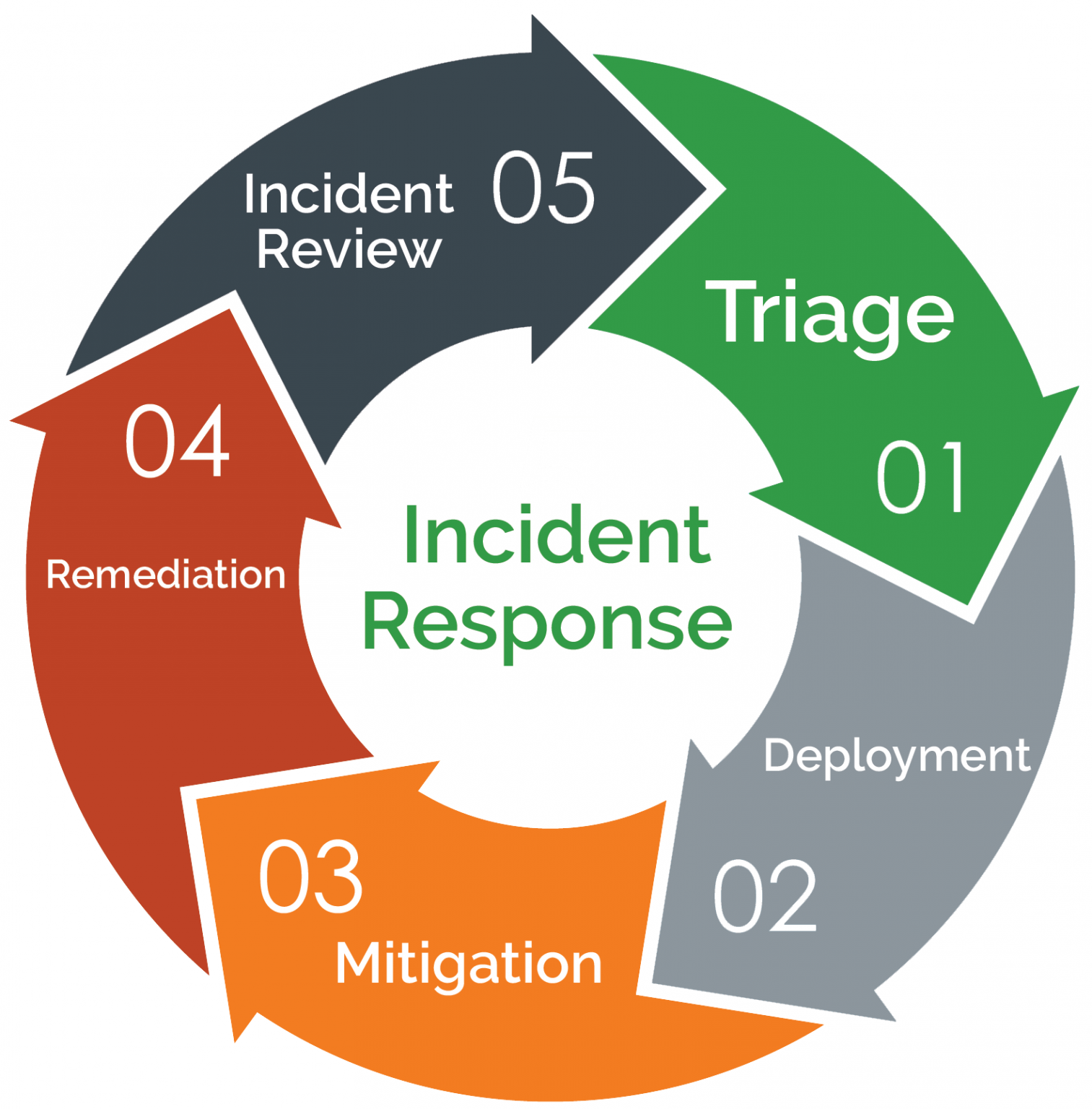
Developing a comprehensive incident response plan for energy systems requires a structured approach to ensure that all aspects of energy system security are addressed. The plan should be tailored to the organization’s specific needs and based on industry best practices and standards. The following steps provide a general framework for developing an effective incident response plan for energy system security.
Step 1: Identify and Classify Incident Response Roles and Responsibilities. Clearly define the roles and responsibilities of the incident response team, including the incident response manager, security analysts, IT staff, and other stakeholders. This ensures that each team member knows their specific duties and responsibilities in the event of a cyber attack.
Step 2: Conduct a Threat Analysis. Identify potential threats to the energy system, including cyber attacks, physical attacks, and natural disasters. Analyze the likelihood and potential impact of each threat to prioritize the organization’s defense efforts.
Step 3: Develop Incident Detection and Reporting Procedures. Establish procedures for detecting and reporting cyber attacks and other security incidents. This may include the use of intrusion detection systems, security information and event management (SIEM) systems, and other monitoring tools.
Step 4: Create Incident Response Strategies. Develop incident response strategies for each type of threat identified in the threat analysis. For example, in the event of a data breach, the incident response strategy may involve isolating affected systems, conducting a forensic analysis, and notifying regulatory authorities.
Step 5: Establish Communication Protocols. Develop communication protocols for incident response, including contact information, notification procedures, and reporting requirements. This ensures that all stakeholders, including regulatory authorities, law enforcement, and affected customers, are informed in a timely and effective manner.
Step 6: Test and Train Incident Response Plan. Regularly test and train the incident response plan to ensure that it is effective and that all team members are familiar with their roles and responsibilities. This may include conducting tabletop exercises, simulations, and other training activities.
Step 7: Review and Update the Incident Response Plan. Regularly review and update the incident response plan to ensure that it remains effective and aligned with industry best practices and standards. This may include reviewing lessons learned from actual incidents and incorporating new security technologies and threat intelligence.
By following these steps, energy organizations can develop a comprehensive incident response plan that provides effective incident response for energy system security, enhancing the overall security posture of the organization and minimizing the risk of cyber attacks.
Incident response for energy system security requires a proactive approach, combining a deep understanding of energy system vulnerabilities with expert knowledge of cyber security strategies and technologies. By incorporating incident response for energy system security into their overall security program, organizations can reduce the risk of successful cyber attacks and minimize the impact of security incidents.
Incident Response Strategies for Energy System Security
An effective incident response plan for energy systems should include a range of strategies to contain, eradicate, recover from, and learn from security incidents. These strategies are critical in minimizing the impact of cyber attacks on energy systems and ensuring the continuity of essential services. Incident response for energy system security requires a structured approach that enables rapid detection, analysis, and response to security incidents. The following incident response strategies are essential for energy system security:
Containment strategies involve isolating affected systems or networks to prevent the spread of malware or unauthorized access. This can include disconnecting from the internet, disabling affected systems, or creating a virtual isolation network. Containment is a critical step in preventing the escalation of a security incident and minimizing its impact on energy system operations. For example, in the event of a ransomware attack, containment strategies can prevent the malware from spreading to other systems and encrypting more data.
Eradication strategies involve removing malware, unauthorized access, or other security threats from affected systems or networks. This can include patching vulnerabilities, installing security updates, or conducting forensic analysis to identify and remove malware. Eradication is essential in restoring the security and integrity of affected systems and preventing future security incidents. In the energy sector, eradication strategies must be carefully planned and executed to minimize disruptions to critical infrastructure.
Recovery strategies involve restoring affected systems or networks to their pre-incident state. This can include rebuilding systems, restoring data from backups, or conducting system testing to ensure the security and integrity of systems. Recovery strategies must be carefully planned and executed to minimize disruptions to energy system operations and ensure the continuity of essential services. For example, in the event of a power grid disruption, recovery strategies can involve quickly restoring power generation and transmission systems to minimize the impact on customers.
Post-incident activities involve reviewing and analyzing security incidents to identify areas for improvement and implementing new security measures to prevent similar incidents in the future. This can include conducting post-incident reviews, updating incident response plans, and conducting security awareness training for employees. Post-incident activities are critical in identifying vulnerabilities, improving incident response strategies, and ensuring the long-term security and integrity of energy systems.
By incorporating these incident response strategies into an incident response plan, energy organizations can enhance their ability to detect, respond to, and recover from security incidents. Incident response for energy system security requires a proactive and structured approach that enables rapid detection, analysis, and response to security incidents. By adopting a proactive and structured approach, energy organizations can minimize the impact of cyber attacks on energy systems and ensure the continuity of essential services.
In incident response for energy system security, it is essential to prioritize a proactive approach that enables rapid detection, analysis, and response to security incidents. By incorporating strategies for containment, eradication, recovery, and post-incident activities into an incident response plan, energy organizations can enhance their ability to minimize the impact of security incidents and ensure the long-term security and integrity of energy systems.
The Role of Automation in Energy System Incident Response
A well-designed automation system plays a critical role in enhancing the efficiency of incident response for energy system security. Security information and event management (SIEM) systems are essential tools in this regard, as they provide real-time monitoring and analysis of security-related data from various sources. This enables swift detection and notification of potential security incidents, allowing for prompt action to prevent or mitigate their impact. Additionally, incident response platforms can help automate the response process, streamlining activities such as threat analysis, incident classification, and response strategy execution.
The integration of automation technologies is crucial for the effective implementation of incident response for energy system security. For instance, machine learning algorithms can be used to analyze patterns in security-related data, facilitating the identification of potential security threats. Moreover, automation tools can help incident responders to filter out false positives, reduce alert fatigue, and focus on high-priority incidents that require immediate attention.
Automation also enables the implementation of a proactive incident response approach. By leveraging predictive analytics and machine learning, energy organizations can identify potential security threats before they materialize, allowing for preventive measures to be taken. This proactive approach can significantly enhance the overall resilience of energy systems, reducing the risk of security incidents and their potential consequences.
When implementing automation tools for incident response, energy organizations must ensure that these tools are integrated with existing security systems and processes. This integration is essential for ensuring seamless collaboration between different stakeholders and facilitating the efficient execution of incident response strategies. Furthermore, automation tools should be regularly updated and fine-tuned to keep pace with evolving security threats and technologies.
Effective automation can also help address the skill gap in incident response for energy system security. By automating routine tasks and providing real-time guidance, automation tools can enable less experienced incident responders to respond effectively to security incidents. This, in turn, can enhance the overall efficiency of incident response efforts, reducing the mean time to detect (MTTD) and mean time to respond (MTTR) to security incidents.
Ultimately, the integration of automation technologies is essential for effective incident response for energy system security. By leveraging automation tools and technologies, energy organizations can enhance the efficiency of their incident response efforts, reduce the risk of security incidents, and ensure the continued reliability and resilience of their energy systems.
Collaboration and Communication in Energy System Incident Response
Effective collaboration and communication are crucial components of a robust incident response plan for energy system security. The seamless sharing of information and coordination between stakeholders can significantly impact the efficiency of response efforts, ultimately minimizing the consequences of cyber attacks on energy systems. A comprehensive incident response strategy must include clear communication protocols to ensure that all relevant parties are informed and involved throughout the incident response process.
The importance of communication in incident response for energy system security cannot be overstated. Energy systems often involve complex networks of organizations, including operators, contractors, and regulatory agencies. A clear understanding of roles, responsibilities, and communication channels is vital to ensure that response efforts are well-coordinated and effective. The National Institute of Standards and Technology (NIST) emphasizes the importance of communication in its Cybersecurity Framework, highlighting the need for communication protocols to support incident response.
Several best practices can support effective collaboration and communication in incident response for energy system security. Organizations should define clear communication protocols, including established channels for reporting incidents, regular updates, and post-incident reviews. Regular training exercises can help ensure that stakeholders are familiar with these protocols and are prepared to respond effectively in the event of a cyber attack.
Technology can also support collaboration and communication in incident response efforts. Security information and event management (SIEM) systems, incident response platforms, and other technologies can facilitate real-time communication and information sharing between stakeholders. These tools can help streamline incident response processes, reduce the risk of miscommunication, and support more efficient response efforts.
Additionally, incident response plans for energy systems should account for compliance with relevant regulations and standards. For example, the North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection (CIP) standards require energy organizations to establish incident response plans that include clear communication protocols. Compliance with these standards is critical to ensure that energy organizations are well-prepared to respond to cyber threats.
Ultimately, effective collaboration and communication are critical components of incident response for energy system security. By establishing clear communication protocols, leveraging technology, and ensuring compliance with relevant regulations, energy organizations can minimize the risk of cyber attacks and protect the reliability and security of energy systems.
Energy System Incident Response: Best Practices and Standards
Developing an effective incident response plan for energy system security requires adhering to industry best practices and standards. These guidelines and regulations help ensure that energy organizations are adequately prepared to respond to and mitigate the impact of cyber attacks. The National Institute of Standards and Technology (NIST) provides a framework for incident response that includes several key components, including incident response planning, incident detection, and incident response strategies. By following this framework, energy organizations can develop a robust incident response plan that aligns with industry best practices and standards.
In addition to NIST, other industry organizations and regulatory bodies, such as the Federal Energy Regulatory Commission (FERC) and the North American Electric Reliability Corporation (NERC), provide guidelines and standards for incident response in the energy sector. These guidelines emphasize the importance of incident response planning, communication, and coordination between stakeholders. For example, NERC’s Critical Infrastructure Protection (CIP) standards require energy organizations to have an incident response plan in place that includes procedures for identifying, assessing, and responding to cyber threats.
Incident response for energy system security also involves compliance with industry regulations and standards, such as the Payment Card Industry Data Security Standard (PCI DSS) and the International Organization for Standardization (ISO) 27001 standard. These regulations and standards help ensure that energy organizations have adequate controls in place to prevent and respond to cyber attacks. By complying with these regulations and standards, energy organizations can demonstrate their commitment to incident response and cybersecurity.
Furthermore, industry best practices and standards for incident response in the energy sector emphasize the importance of continuous improvement and regular testing of incident response plans. This includes conducting regular tabletop exercises, training and awareness programs for employees, and reviewing and updating incident response plans to ensure they remain effective and relevant. By following these best practices and standards, energy organizations can develop a robust incident response plan that is tailored to their specific needs and requirements.
By adhering to industry best practices and standards for incident response, energy organizations can ensure that they are adequately prepared to respond to and mitigate the impact of cyber attacks. This includes developing a robust incident response plan, communicating and coordinating with stakeholders, and continuously improving and testing incident response plans. By taking a proactive and comprehensive approach to incident response, energy organizations can help protect the security and reliability of the energy system.
Continuous Improvement in Energy System Incident Response
Implementing a comprehensive incident response plan for energy system security is not a one-time task, but rather an ongoing process that requires continuous improvement. To ensure the effectiveness of incident response strategies, regular testing, training, and evaluation of incident response plans are crucial. This allows energy system operators to identify areas for improvement, update their response plans, and maintain compliance with industry regulations and standards. Continuous improvement in incident response for energy system security involves several key activities, including regular training exercises, tabletop simulations, and real-world scenario testing. These activities help to identify vulnerabilities, test response strategies, and ensure that incident response teams are prepared to respond to potential threats.
Regular testing and training also help to ensure that incident response plans are aligned with the latest industry guidelines and standards, such as those provided by the North American Electric Reliability Corporation (NERC) and the International Electrotechnical Commission (IEC). Additionally, continuous improvement involves monitoring and analyzing incident response activities, identifying areas for improvement, and implementing changes to incident response plans as needed. By prioritizing continuous improvement, energy system operators can ensure that their incident response strategies remain effective and up-to-date, ultimately protecting their energy systems from cyber threats and maintaining the reliability and security of the energy infrastructure.
Another key aspect of continuous improvement in incident response for energy system security is the use of incident response metrics and key performance indicators (KPIs). These metrics help to measure the effectiveness of incident response strategies and identify areas for improvement. Common incident response metrics include mean time to detect (MTTD), mean time to respond (MTTR), and mean time to recover (MTTR). By tracking and analyzing these metrics, energy system operators can refine their incident response strategies and optimize their response times.
Ultimately, continuous improvement in incident response for energy system security is critical for protecting the energy infrastructure from cyber threats. By prioritizing regular testing, training, and evaluation, energy system operators can ensure that their incident response strategies remain effective and up-to-date, ultimately safeguarding the reliability and security of the energy system. This emphasis on continuous improvement underscores the importance of Incident response for energy system security as an ongoing process that requires regular attention and refinement to stay ahead of evolving threats.