What is Identity and Access Management (IAM) in AWS?
Identity and Access Management (IAM) in AWS is a service that helps manage user identities and secure access to AWS resources. IAM enables organizations to create and manage AWS users and groups, and use permissions to allow and deny access to AWS resources. By using IAM, organizations can ensure secure access to AWS services and resources, and maintain compliance with regulations and industry standards. The benefits of using IAM include enabling secure access to AWS services and resources, reducing the risk of unauthorized access, and ensuring compliance with regulations and industry standards.
Key Components of IAM in AWS
IAM in AWS includes several key components that work together to provide secure access to AWS resources. These components include users, groups, roles, and permissions. Users are the identities that access AWS resources. Groups are collections of users who share the same permissions. Roles are AWS identities with specific permissions. Permissions define what actions are allowed or denied for a user, group, or role.
Users, groups, and roles are created and managed in the IAM console. Permissions can be assigned to users, groups, or roles using policies. Policies are JSON documents that define what actions are allowed or denied for a user, group, or role. Policies can be attached to users, groups, or roles, and can be managed using the IAM console or AWS CLI.
IAM in AWS also includes features such as access keys and multi-factor authentication. Access keys are used to authenticate API requests, and multi-factor authentication provides an additional layer of security by requiring a second form of authentication. By using these key components and features, organizations can ensure secure access to AWS resources and maintain compliance with regulations and industry standards.
How to Use IAM in AWS: A Step-by-Step Guide
To use IAM in AWS, follow these steps:
-
Sign in to the AWS Management Console.
-
Navigate to the IAM console.
-
Create users, groups, and roles as needed.
-
Assign permissions to users, groups, and roles using policies.
-
Create access keys for users who need to make API requests.
-
Enable multi-factor authentication for added security.
-
Regularly review and update IAM policies to ensure they are up-to-date and reflect the principle of least privilege.
Here are some screenshots and examples to illustrate each step:
Step 1: Sign in to the AWS Management Console

Step 2: Navigate to the IAM console

Step 3: Create users, groups, and roles as needed

Step 4: Assign permissions to users, groups, and roles using policies

Step 5: Create access keys for users who need to make API requests

Step 6: Enable multi-factor authentication for added security

Step 7: Regularly review and update IAM policies to ensure they are up-to-date and reflect the principle of least privilege

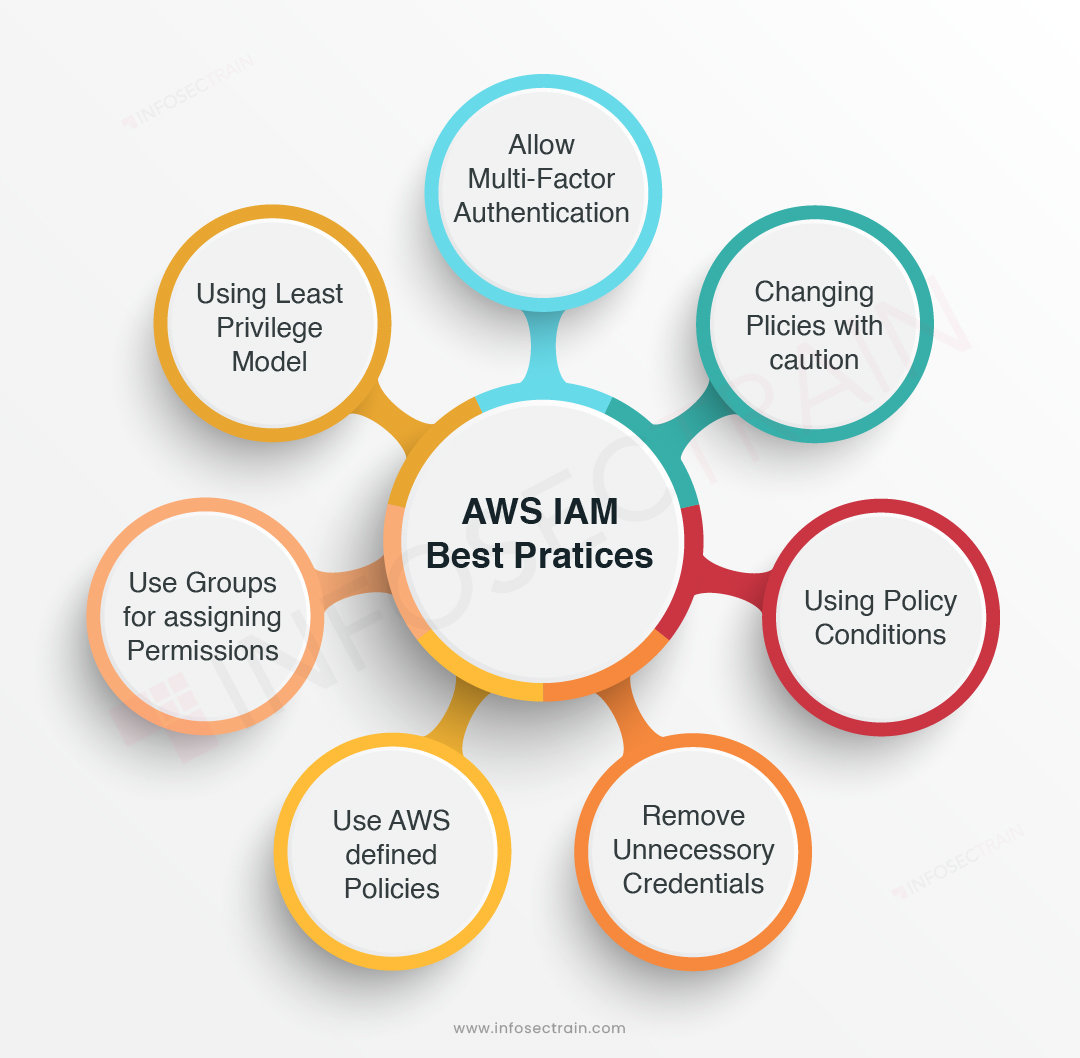
Best Practices for Implementing IAM in AWS
Implementing IAM in AWS requires careful planning and execution to ensure secure access to AWS resources. Here are some best practices to follow:
-
Use access keys and multi-factor authentication: Access keys are long-term credentials that allow API access to AWS services. It’s important to rotate access keys regularly and use multi-factor authentication to add an extra layer of security.
-
Follow the principle of least privilege: Assign the minimum permissions necessary for users, groups, and roles to perform their tasks. This reduces the risk of unauthorized access and data breaches.
-
Regularly review and update IAM policies: IAM policies define what actions are allowed or denied for a user, group, or role. Regularly reviewing and updating IAM policies ensures they are up-to-date and reflect the principle of least privilege.
-
Use IAM roles for applications: IAM roles allow applications to assume temporary credentials to access AWS resources. This is more secure than hard-coding credentials into applications.
-
Use service controls policies (SCPs) for fine-grained access control: SCPs provide central control over permissions for multiple AWS accounts and prevent unauthorized access to AWS services.
-
Enable IAM password policy: IAM password policy allows you to enforce password requirements, such as length, complexity, and expiration, for IAM users.
-
Use IAM conditions to restrict access: IAM conditions allow you to restrict access to AWS resources based on specific conditions, such as IP address, time of day, or SSL certificate.
-
Monitor IAM activity: Use AWS CloudTrail and Amazon CloudWatch to monitor IAM activity and detect any suspicious behavior.
By following these best practices, you can ensure secure access to AWS resources and maintain compliance with regulations and industry standards.
Real-World Examples of IAM in AWS
IAM is a powerful tool for managing user identities and access to AWS resources. Here are some real-world examples of how IAM is used in AWS:
-
Managing access to Amazon S3 buckets: IAM allows you to manage access to Amazon S3 buckets by creating IAM users and groups with specific permissions. For example, you can create an IAM group for developers and grant them read/write access to specific S3 buckets. This ensures that only authorized users can access the S3 buckets, reducing the risk of data breaches.
-
Secure access to Amazon EC2 instances: IAM allows you to manage access to Amazon EC2 instances by creating IAM roles with specific permissions. For example, you can create an IAM role for an application and grant it permissions to access specific EC2 instances. This ensures that the application has the necessary permissions to access the EC2 instances, without the need for hard-coded credentials.
-
Compliance with regulations and industry standards: IAM allows you to meet compliance requirements by creating IAM policies that enforce password requirements, multi-factor authentication, and least privilege access. For example, you can create an IAM policy that requires users to change their passwords every 90 days and use multi-factor authentication. This ensures that your organization is compliant with regulations and industry standards, such as HIPAA and PCI DSS.
-
Centralized access control: IAM allows you to centrally manage access to AWS resources across multiple accounts. For example, you can use IAM roles to delegate access to specific AWS resources in different accounts. This ensures that users have the necessary permissions to access the resources, without the need for multiple sets of credentials.
These are just a few examples of how IAM is used in AWS. By implementing IAM best practices and regularly reviewing and updating IAM policies, you can ensure secure access to AWS resources and maintain compliance with regulations and industry standards.
Comparing IAM Solutions in AWS: Free vs. Paid
AWS offers two solutions for managing identities and access in your AWS environment: AWS Identity and Access Management (IAM) and AWS Identity and Access Management Access Analyzer. Both solutions provide secure access to AWS resources, but they have different features and limitations. In this article, we will compare the two solutions to help you decide which one is right for your organization.
AWS Identity and Access Management (IAM)
IAM is a free service that allows you to manage access to AWS services and resources. With IAM, you can create and manage AWS users and groups, and use permissions to allow and deny access to AWS resources. IAM also allows you to create and manage roles, which are AWS identities with specific permissions. IAM provides the following features:
-
User management: Create and manage IAM users and groups, and set permissions to allow or deny access to AWS resources.
-
Role management: Create and manage IAM roles, which are AWS identities with specific permissions. Roles can be assumed by IAM users, AWS services, or federated users.
-
Permission management: Use IAM policies to allow or deny access to AWS resources. IAM policies are JSON documents that define permissions in a hierarchical structure.
-
Access key management: Create and manage access keys for IAM users. Access keys are used to authenticate API requests and access the AWS Management Console.
-
Multi-factor authentication (MFA): Enforce MFA for IAM users to provide an additional layer of security.
AWS Identity and Access Management Access Analyzer
Access Analyzer is a paid service that helps you identify potential security risks in your IAM policies. Access Analyzer analyzes your IAM policies and identifies permissions that allow access from outside your AWS account. Access Analyzer provides the following features:
-
IAM policy analysis: Analyze IAM policies and identify permissions that allow access from outside your AWS account.
-
Resource sharing analysis: Analyze resource sharing permissions and identify potential security risks.
-
Security recommendations: Receive security recommendations based on the analysis of your IAM policies and resource sharing permissions.
-
Integration with AWS Security Hub: Integrate Access Analyzer with AWS Security Hub to centrally manage security findings across your AWS environment.
Comparison
Both IAM and Access Analyzer provide secure access to AWS resources, but they have different features and limitations. IAM is a free service that allows you to manage access to AWS services and resources, while Access Analyzer is a paid service that helps you identify potential security risks in your IAM policies. Here is a comparison of the two solutions:
| Feature | IAM | Access Analyzer |
|---|---|---|
| User management | Yes | No |
| Role management | Yes | No |
| Permission management | Yes | Yes |
| Access key management | Yes | No |
| MFA | Yes | No |
| IAM policy analysis | No | Yes |
| Resource sharing analysis | No | Yes |
| Security recommendations | No | Yes |
| Integration with AWS Security Hub | No | Yes |
In summary, IAM is a free service that allows you to manage access to AWS services and resources, while Access Analyzer is a paid service that helps you identify potential security risks in your IAM policies. If you need to manage users and roles, or use access keys and MFA, then IAM is the right solution for you. If you need to analyze IAM policies and resource sharing permissions, and receive security recommendations, then Access Analyzer is the right solution for you.
Troubleshooting Common IAM Issues in AWS
Identity and Access Management (IAM) in AWS is a powerful tool for managing user identities and access to AWS resources. However, it can be complex to set up and manage, and there are several common issues that users may encounter. In this article, we will discuss some of the most common IAM issues in AWS and provide tips and tricks for troubleshooting them.
Access Denied Errors
Access denied errors are one of the most common IAM issues in AWS. These errors occur when a user tries to access a resource, but doesn’t have the necessary permissions. To troubleshoot access denied errors, follow these steps:
-
Check the IAM policy: Check the IAM policy for the user to ensure that they have the necessary permissions to access the resource.
-
Check the resource policy: Check the resource policy to ensure that it allows access from the user’s AWS account.
-
Check the service control policy: Check the service control policy to ensure that it allows access to the resource.
-
Check for conflicts: Check for conflicts between the IAM policy, resource policy, and service control policy.
Managing Permissions
Managing permissions can be complex in IAM, especially when dealing with large numbers of users and resources. To simplify permission management, follow these best practices:
-
Use groups: Use IAM groups to manage permissions for multiple users. This makes it easier to assign and manage permissions for large numbers of users.
-
Use least privilege: Follow the principle of least privilege and only assign the minimum permissions necessary for users to perform their tasks.
-
Use permission boundaries: Use permission boundaries to limit the permissions that a user or group can be granted.
Debugging IAM Policies
Debugging IAM policies can be challenging, especially when dealing with complex policies. To debug IAM policies, follow these steps:
-
Simplify the policy: Simplify the policy by removing unnecessary statements and conditions.
-
Test the policy: Test the policy using the IAM policy simulator to ensure that it behaves as expected.
-
Check for errors: Check for errors in the policy syntax and format.
Conclusion
Identity and Access Management (IAM) in AWS is a powerful tool for managing user identities and access to AWS resources. However, it can be complex to set up and manage, and there are several common issues that users may encounter. By following the tips and tricks outlined in this article, you can troubleshoot common IAM issues in AWS and ensure secure access to your AWS resources.
Future Trends in Identity and Access Management (IAM) in AWS
Identity and Access Management (IAM) in AWS is an essential service for managing user identities and access to AWS resources. As cloud computing continues to evolve, IAM in AWS is also expected to undergo significant changes. In this article, we will discuss some of the future trends in IAM in AWS, such as the adoption of zero trust security models, the use of machine learning and artificial intelligence for access control, and the integration of IAM with other AWS services.
Adoption of Zero Trust Security Models
Zero trust security models are becoming increasingly popular as they provide a more secure way of managing access to resources. In a zero trust model, access is granted based on the identity of the user, regardless of their location or device. This approach helps prevent unauthorized access and reduces the risk of data breaches. In the future, we can expect to see more organizations adopting zero trust security models in AWS, which will require IAM to evolve to support this new approach.
Use of Machine Learning and Artificial Intelligence for Access Control
Machine learning and artificial intelligence are being increasingly used in access control to provide more intelligent and dynamic access decisions. These technologies can analyze user behavior and identify patterns that indicate potential security threats. In the future, we can expect to see more organizations using machine learning and artificial intelligence in IAM in AWS to improve access control and enhance security.
Integration of IAM with Other AWS Services
IAM in AWS is already integrated with many AWS services, but we can expect to see even more integration in the future. This integration will enable organizations to manage access to multiple services from a single IAM platform, simplifying access management and improving security. For example, IAM could be integrated with AWS Security Hub to provide a centralized view of security alerts and events across multiple AWS services.
Conclusion
Identity and Access Management (IAM) in AWS is an essential service for managing user identities and access to AWS resources. As cloud computing continues to evolve, IAM in AWS is also expected to undergo significant changes. By adopting zero trust security models, using machine learning and artificial intelligence for access control, and integrating IAM with other AWS services, organizations can improve access management and enhance security in the future.