Identity and Access Management (IAM) on AWS: An Overview
Identity and Access Management (IAM) on Amazon Web Services (AWS) is a critical component in ensuring secure access to AWS resources. IAM enables you to manage users, groups, roles, and permissions, forming the backbone of your security strategy on AWS. By controlling access, IAM helps maintain the confidentiality, integrity, and availability of your data and services.
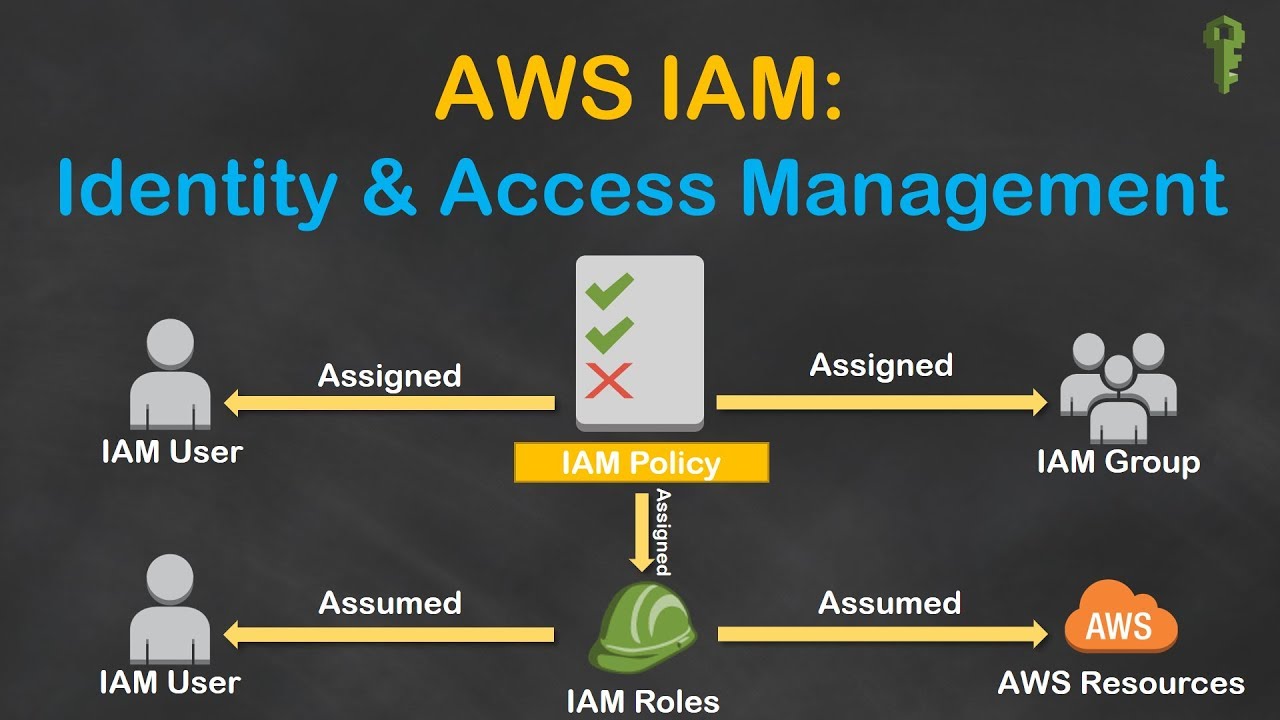
The main components of IAM include users, groups, roles, and permissions. Users represent individual identities that can be assigned specific access rights. Groups simplify the management of permissions for multiple users by allowing you to assign the same permissions to multiple users simultaneously. Roles are AWS identities with specific permissions, which can be assumed by IAM users, AWS services, or federated users from external identity providers. Permissions define what actions are allowed or denied for each user, group, or role, and are typically defined using policies.
Designing a Robust IAM Strategy on AWS
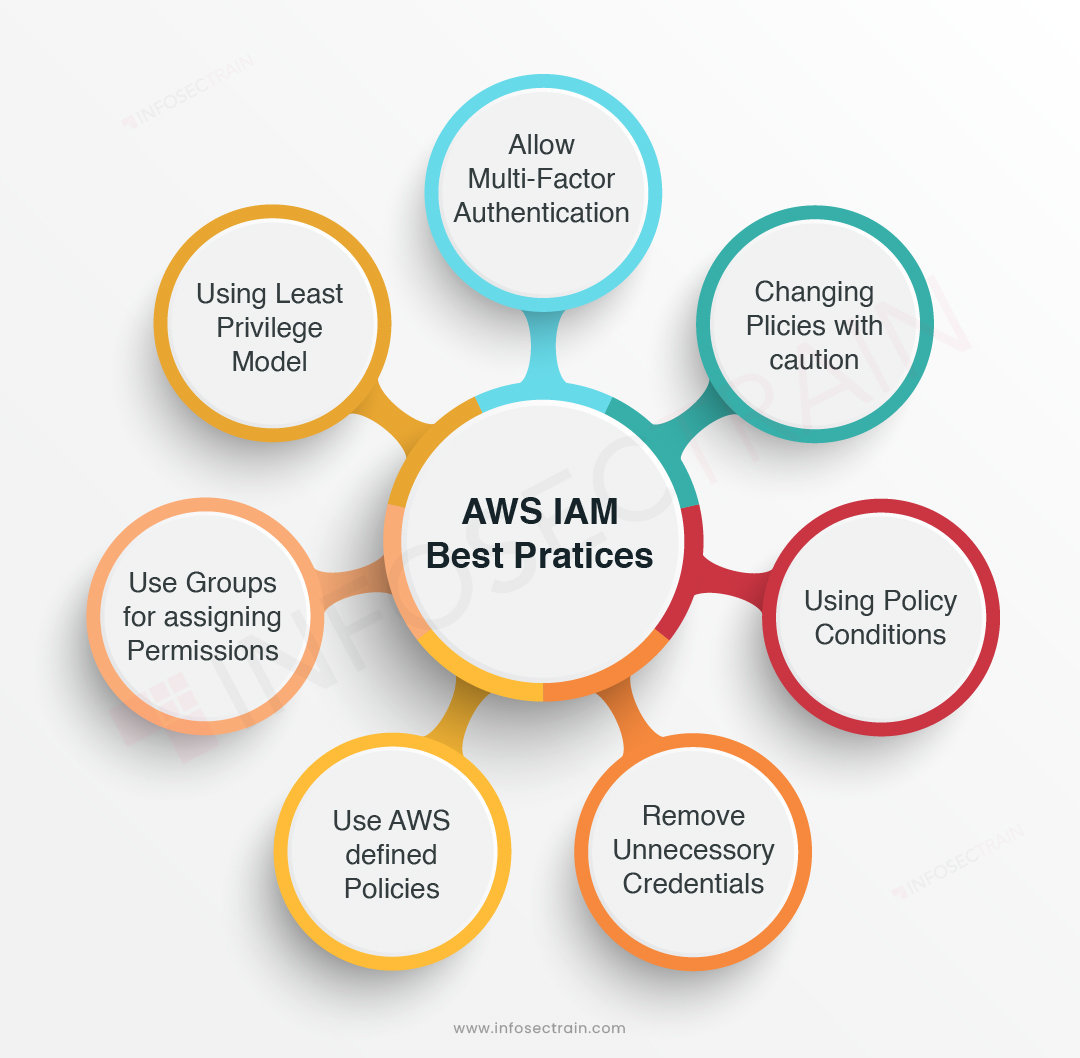
A well-designed Identity and Access Management (IAM) strategy on AWS is crucial for maintaining security and compliance. By following best practices and implementing key elements, you can create a robust IAM framework that ensures secure access to your AWS resources. The primary components of a robust IAM strategy include the principles of least privilege, separation of duties, and regular reviews.
The principle of least privilege means granting users, groups, or roles only the permissions necessary to perform their tasks. This approach minimizes the risk of unauthorized access or actions that could compromise your AWS resources. By adhering to this principle, you can maintain a secure environment while enabling users to perform their duties effectively.
Separation of duties is another essential element of a robust IAM strategy. By dividing tasks and responsibilities among multiple users or roles, you reduce the risk of errors, misconfigurations, or malicious activities. Separation of duties ensures that no single user has complete control over critical functions, limiting the potential for security breaches and data loss.
Regular reviews are vital for maintaining a secure IAM environment. Periodically examining and updating your IAM policies, users, groups, and roles helps ensure that your security posture remains up-to-date and aligned with your organization’s needs. Regular reviews also help identify and address potential security risks, misconfigurations, or outdated access levels.
To implement a robust IAM strategy on AWS, follow these best practices:
- Assign permissions using groups and roles instead of individual users.
- Regularly review and update IAM policies and permissions.
- Monitor and audit IAM activities using AWS services like AWS CloudTrail and AWS Config.
- Use Multi-Factor Authentication (MFA) for added security.
- Implement least privilege and separation of duties principles.
- Leverage IAM roles for applications and services to access AWS resources.
Implementing IAM Users, Groups, and Roles
IAM users, groups, and roles are essential components for managing secure access to your AWS resources. Understanding how to create, manage, and assign permissions to these entities is crucial for maintaining a robust IAM strategy.
IAM Users
IAM users represent individual identities that can be assigned specific access rights. To create an IAM user, follow these steps:
- Sign in to the AWS Management Console as an AWS account root user or an IAM user with the necessary permissions.
- In the navigation pane, choose Services and then select IAM.
- In the navigation pane, choose Users and then click the Add user button.
- Enter a user name, select the type of access (programmatic or AWS Management Console), and then click Next.
- Define the permissions for the user by adding them to groups, attaching policies directly, or using permission boundaries. Click Next.
- Review the user settings and click Create user.
Best practices for managing IAM users include:
- Creating individual IAM users instead of sharing AWS account credentials.
- Assigning the least privilege necessary for each user.
- Regularly reviewing and updating user permissions.
- Using access keys wisely and rotating them periodically.
IAM Groups
IAM groups simplify the management of permissions for multiple users by allowing you to assign the same permissions to multiple users simultaneously. To create an IAM group, follow these steps:
- Sign in to the AWS Management Console as an AWS account root user or an IAM user with the necessary permissions.
- In the navigation pane, choose Services and then select IAM.
- In the navigation pane, choose Groups and then click the Create New Group button.
- Enter a group name, add a description (optional), and then click Next Step.
- Select the policies to attach to the group and then click Next Step.
- Review the group settings and click Create Group.
IAM Roles
IAM roles are AWS identities with specific permissions that can be assumed by IAM users, AWS services, or federated users from external identity providers. To create an IAM role, follow these steps:
- Sign in to the AWS Management Console as an AWS account root user or an IAM user with the necessary permissions.
- In the navigation pane, choose Services and then select IAM.
- In the navigation pane, choose Roles and then click the Create New Role button.
- Select the type of trusted entity (AWS service, IAM user, or federated user) and then click Next Step.
- Attach the necessary policies and then click Next Step.
- Review the role settings and click Create Role.
Best practices for managing IAM roles include:
- Defining the role’s permissions using the principle of least privilege.
- Regularly reviewing and updating role permissions.
- Using roles to delegate access to AWS services or external users.
How to Use Multi-Factor Authentication (MFA) for Enhanced Security
Multi-Factor Authentication (MFA) is a security mechanism that requires users to provide two or more verification factors to gain access to a system or resource. Implementing MFA on AWS adds an extra layer of protection, preventing unauthorized access even if a user’s password is compromised. This section explains how to enable and use MFA on AWS and highlights its benefits.
Benefits of Multi-Factor Authentication
MFA offers several benefits, including:
- Increased security: MFA makes it more difficult for attackers to gain unauthorized access to your AWS resources.
- Reduced risk of account takeover: By requiring additional verification factors, MFA reduces the likelihood of successful phishing attacks and account takeovers.
- Compliance with regulations: Many regulatory frameworks require the use of MFA to protect sensitive data and systems.
Enabling Multi-Factor Authentication on AWS
To enable MFA for an IAM user, follow these steps:
- Sign in to the AWS Management Console as an IAM user with the necessary permissions or as the AWS account root user.
- In the navigation pane, choose Services and then select IAM.
- In the navigation pane, choose Users and then select the user you want to enable MFA for.
- Under Security Credentials, choose the Assigned MFA device option.
- Click the Manage MFA device button.
- Follow the on-screen instructions to configure your MFA device (e.g., virtual MFA app or hardware key).
Using Multi-Factor Authentication with AWS Services
Once MFA is enabled for an IAM user, you can require MFA for specific AWS services, such as the AWS Management Console, AWS CLI, or AWS SDKs. To enforce MFA for the AWS Management Console, follow these steps:
- Sign in to the AWS Management Console as an IAM user with the necessary permissions or as the AWS account root user.
- In the navigation pane, choose Services and then select IAM.
- In the navigation pane, choose Users and then select the user you want to enforce MFA for.
- Under Security Credentials, choose the Assigned MFA device option.
- Click the Edit button next to AWS Management Console sign-in URL.
- Select the Require MFA option and then click Save changes.
By following these steps, you can enhance the security of your AWS resources and protect your organization from unauthorized access. Remember to regularly review and update your MFA settings to ensure they remain aligned with your security and compliance objectives.
Identity and Access Management Best Practices on AWS
Implementing best practices for Identity and Access Management (IAM) on AWS is crucial for maintaining security and compliance. This section summarizes the best practices for IAM on AWS, including regular reviews, using access keys wisely, and leveraging IAM policies and roles. By following these practices, you can ensure secure access to your AWS resources and protect your organization from unauthorized access.
Regularly Review IAM Policies and Users
Regularly reviewing IAM policies, groups, roles, and users helps ensure that your security posture remains up-to-date and aligned with your organization’s needs. Schedule periodic audits to:
- Remove unnecessary access rights and permissions.
- Update permissions to reflect changes in job responsibilities or system configurations.
- Deactivate or delete inactive or unnecessary users.
Use Access Keys Wisely
Access keys are long-term security credentials that allow programs and scripts to access AWS services. To minimize the risk of unauthorized access, follow these best practices:
- Rotate access keys periodically.
- Delete access keys that are no longer needed.
- Limit the use of access keys to specific users and applications that require programmatic access.
Leverage IAM Policies and Roles
IAM policies and roles are powerful tools for controlling access to AWS resources. To maximize their potential, follow these best practices:
- Assign permissions using the principle of least privilege.
- Use IAM roles to delegate access to AWS services or external users.
- Leverage IAM policies to enforce security and compliance requirements.
Monitor and Audit IAM Activities
Monitoring and auditing IAM activities is essential for detecting and responding to security incidents. Use AWS services such as AWS CloudTrail, AWS Config, and AWS Security Hub to:
- Track IAM events and changes.
- Generate alerts and notifications for suspicious or unauthorized activities.
- Integrate IAM data with your organization’s security information and event management (SIEM) systems.
By following these best practices, you can ensure a secure and compliant IAM strategy on AWS. Regularly reviewing and updating your IAM policies, using access keys wisely, and leveraging IAM policies and roles can help protect your organization from unauthorized access and maintain a strong security posture.
Understanding AWS Security Services
AWS offers a range of security services designed to enhance security and compliance within your AWS environment. This section introduces AWS Security Hub, AWS GuardDuty, and AWS Shield and explains their role in IAM and access management. By understanding these services and how to integrate them with IAM, you can strengthen your security posture and better protect your AWS resources.
AWS Security Hub
AWS Security Hub is a security management service that provides a comprehensive view of your security and compliance status across your AWS accounts. By consolidating findings from AWS services such as Amazon GuardDuty, Amazon Inspector, Amazon Macie, and AWS IAM Access Analyzer, Security Hub simplifies security management and enables you to prioritize and respond to security issues more effectively.
AWS GuardDuty
AWS GuardDuty is a threat detection service that continuously monitors for malicious activity and unauthorized behavior to protect your AWS accounts and resources. GuardDuty analyzes and processes data from AWS CloudTrail, Amazon VPC Flow Logs, and DNS logs to detect threats like escalation of privileges, unusual data access, and communication with known malicious IPs. By integrating GuardDuty with IAM, you can enhance your security posture and respond to potential threats more effectively.
AWS Shield
AWS Shield is a managed Distributed Denial of Service (DDoS) protection service that safeguards your web applications running on AWS. Shield provides always-on detection and automatic inline mitigations to minimize application downtime and latency. By integrating AWS Shield with IAM, you can control access to Shield features and protect your web applications from DDoS attacks more effectively.
Integrating AWS Security Services with IAM
To integrate AWS Security Hub, AWS GuardDuty, and AWS Shield with IAM, follow these steps:
- Create IAM policies that grant the necessary permissions to access each service.
- Attach the policies to IAM users, groups, or roles as required.
- Configure each service to use the IAM policies and roles for access control and permission management.
By integrating AWS Security Hub, AWS GuardDuty, and AWS Shield with IAM, you can strengthen your security posture, enhance threat detection, and better protect your AWS resources. Regularly reviewing and updating your IAM policies and permissions ensures that your security services remain aligned with your organization’s needs and security objectives.
Implementing Access Control Policies and Permissions in IAM
Access control policies and permissions are essential components of Identity and Access Management (IAM) on AWS. They define who can access which resources and under what conditions. Understanding how to create, manage, and implement policies and permissions is crucial for maintaining a secure AWS environment. This section discusses the process of creating and managing access control policies and permissions in IAM, as well as the importance of using conditions and policy variables.
The Structure of IAM Policies
IAM policies are JSON documents that consist of one or more policy statements. Each statement includes an effect (Allow or Deny), a list of AWS resources, and a list of actions or operations that can be performed on those resources. IAM policies can be attached to IAM users, groups, or roles, allowing you to control access to AWS services and resources.
Creating and Managing Access Control Policies
To create and manage access control policies in IAM, follow these steps:
- Sign in to the AWS Management Console and navigate to the IAM service.
- In the navigation pane, choose Policies and then click the Create policy button.
- Choose either the JSON or the visual editor to define your policy. The JSON editor allows you to write the policy directly in JSON format, while the visual editor provides a user-friendly interface for creating policies.
- Define the policy statements, including the effect, resources, and actions. You can also specify conditions and policy variables to further refine the policy.
- Review the policy and click Create policy to save it.
Using Conditions and Policy Variables
Conditions and policy variables allow you to create more granular and dynamic policies. Conditions specify when a policy should take effect based on specific contexts, such as the IP address, time of day, or authenticated user. Policy variables, on the other hand, enable you to reference specific values, such as the user’s ARN or the resource’s region, in your policies.
Best Practices for Managing Access Control Policies
To ensure effective access control and minimize the risk of unauthorized access, follow these best practices:
- Assign permissions using the principle of least privilege.
- Regularly review and update your policies to reflect changes in job responsibilities or system configurations.
- Use conditions and policy variables to create more granular and dynamic policies.
- Test your policies in a controlled environment before deploying them to production.
By understanding the structure of IAM policies, learning how to create and manage policies and permissions, and employing best practices, you can effectively control access to your AWS resources and maintain a secure AWS environment.
Troubleshooting Common IAM Issues on AWS
Identity and Access Management (IAM) on AWS is a powerful tool for controlling access to your resources, but it can sometimes be challenging to manage, especially when issues arise. This section addresses common IAM issues on AWS, such as permission errors, and provides troubleshooting steps and best practices for resolving them. Emphasizing the importance of documentation and communication when dealing with IAM-related issues can help ensure a secure and compliant AWS environment.
Common IAM Issues
Some common IAM issues include permission errors, unintended resource access, and difficulties managing IAM entities. These issues can lead to unauthorized access, data breaches, or service disruptions. To minimize the impact of these issues, it’s essential to understand how to troubleshoot and resolve them effectively.
Troubleshooting Permission Errors
Permission errors typically occur when a user, group, or role doesn’t have the necessary permissions to perform an action on a resource. To troubleshoot permission errors, follow these steps:
- Review the error message to identify the resource and action causing the error.
- Check the IAM policy attached to the user, group, or role to ensure it includes the required permissions.
- Verify that the resource ARN is correctly specified in the policy.
- Confirm that the policy is attached to the correct IAM entity.
- If the issue persists, consider using AWS Trusted Advisor or AWS IAM Access Analyzer to identify potential policy issues.
Best Practices for Resolving IAM Issues
To minimize IAM-related issues and ensure a secure and compliant AWS environment, follow these best practices:
- Document IAM policies, permissions, and access levels to maintain a clear understanding of who has access to what resources.
- Regularly review IAM policies and permissions to ensure they remain up-to-date and reflect current job responsibilities and system configurations.
- Use IAM roles for applications and services that require access to AWS resources, rather than sharing long-term access keys.
- Implement Multi-Factor Authentication (MFA) for added security and to prevent unauthorized access.
- Monitor and audit IAM activities using AWS services such as AWS CloudTrail, AWS Config, and AWS Security Hub.
By understanding common IAM issues, following best practices for troubleshooting and resolving them, and emphasizing the importance of documentation and communication, you can maintain a secure and compliant AWS environment and minimize the risk of unauthorized access or data breaches.