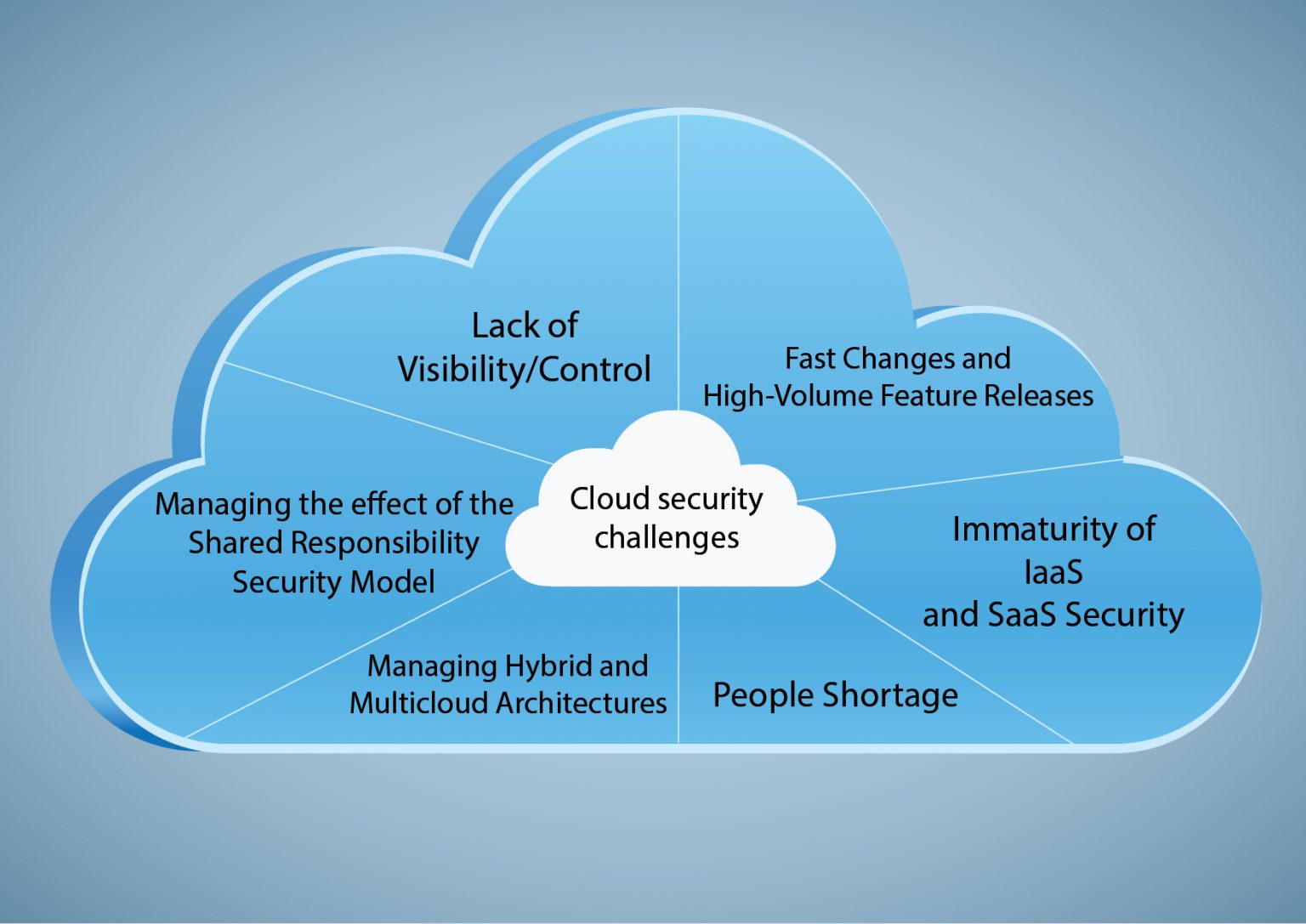
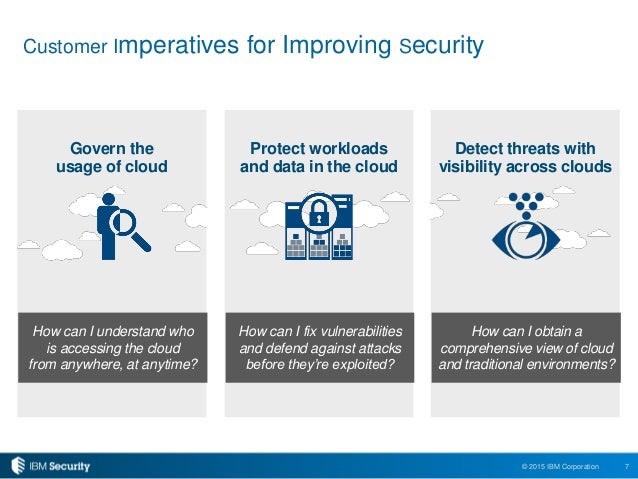
Understanding IBM Cloud Security and Compliance
In today’s digital age, organizations are increasingly moving their operations to the cloud to take advantage of its flexibility, scalability, and cost-effectiveness. However, this shift also introduces new security and compliance challenges that must be addressed to protect sensitive data and maintain regulatory compliance. This is where IBM Cloud Security and Compliance comes in.
IBM Cloud Security and Compliance is a comprehensive set of solutions designed to help organizations secure their cloud infrastructure, applications, and data. It includes key components such as data encryption, identity and access management, and security monitoring, which work together to provide a robust security posture in the cloud environment.
Data encryption is a critical component of IBM Cloud Security and Compliance, ensuring that data is protected both at rest and in transit. With encryption, even if data is intercepted or accessed without authorization, it remains unreadable and useless to attackers. IBM Cloud Security and Compliance supports a variety of encryption algorithms and standards, including AES, RSA, and SSL/TLS, to provide maximum flexibility and security.
Identity and access management is another essential component of IBM Cloud Security and Compliance. It enables organizations to manage user identities and access to cloud resources, ensuring that only authorized users have access to sensitive data and applications. IBM Cloud Security and Compliance supports a variety of identity and access management solutions, including IBM Cloud Identity, which provides a centralized identity and access management platform for cloud and on-premises environments.
Security monitoring is the third critical component of IBM Cloud Security and Compliance. It enables organizations to detect and respond to security threats in real-time, minimizing the risk of data breaches and other security incidents. IBM Cloud Security and Compliance supports a variety of security monitoring solutions, including IBM Cloud Security Advisor and IBM Cloud Security Hub, which provide real-time visibility into security events and alerts, enabling organizations to take swift and effective action to mitigate security threats.
IBM Cloud Security and Compliance Solutions
IBM Cloud Security and Compliance offers a range of solutions to help organizations secure their cloud infrastructure, applications, and data, and maintain compliance with industry regulations and standards. Here are some of the key solutions:
IBM Cloud Security Advisor
IBM Cloud Security Advisor is a cloud-native security platform that provides real-time visibility into security threats and vulnerabilities in an organization’s cloud environment. It uses machine learning and artificial intelligence to analyze security events and alerts, enabling organizations to detect and respond to security threats quickly and effectively. IBM Cloud Security Advisor supports a variety of security standards and frameworks, including PCI-DSS, HIPAA, and GDPR, making it an ideal solution for organizations in regulated industries.
IBM Cloud Security Hub
IBM Cloud Security Hub is a centralized platform that provides a single view of an organization’s cloud security posture. It enables security teams to manage security policies, configure security settings, and monitor security events and alerts across multiple cloud environments. IBM Cloud Security Hub supports a variety of security standards and frameworks, including CIS, NIST, and ISO 27001, making it an ideal solution for organizations that operate in complex and diverse cloud environments.
IBM Cloud Identity
IBM Cloud Identity is a cloud-based identity and access management platform that enables organizations to manage user identities and access to cloud resources securely. It supports a variety of authentication methods, including multi-factor authentication, social login, and passwordless authentication, making it an ideal solution for organizations that need to support a wide range of user identities and access requirements.
IBM Cloud Key Protect
IBM Cloud Key Protect is a cloud-based key management service that enables organizations to manage encryption keys and protect sensitive data in the cloud. It supports a variety of encryption algorithms and standards, including AES, RSA, and ECC, making it an ideal solution for organizations that need to secure sensitive data in the cloud.
IBM Cloud Security Group
IBM Cloud Security Group is a cloud-based network security service that enables organizations to secure their cloud infrastructure and applications. It supports a variety of security policies and configurations, including security groups, network ACLs, and VPNs, making it an ideal solution for organizations that need to secure their cloud infrastructure and applications.
How to Implement IBM Cloud Security and Compliance
Implementing IBM Cloud Security and Compliance in an organization’s cloud environment requires careful planning and execution. Here are some best practices to follow:
Step 1: Assess Your Security and Compliance Needs
The first step in implementing IBM Cloud Security and Compliance is to assess your organization’s security and compliance needs. Identify the types of data you need to protect, the regulatory requirements you must comply with, and the potential security threats you face. This assessment will help you determine the specific IBM Cloud Security and Compliance solutions you need to implement.
Step 2: Configure Security Settings
Once you have identified the IBM Cloud Security and Compliance solutions you need, the next step is to configure security settings. This includes setting up data encryption, configuring identity and access management policies, and setting up security monitoring. IBM Cloud Security and Compliance provides a range of tools and features to help you configure security settings quickly and easily.
Step 3: Manage User Identities and Access
Managing user identities and access is a critical component of IBM Cloud Security and Compliance. Use IBM Cloud Identity to manage user identities and access to cloud resources. Implement multi-factor authentication, role-based access control, and other best practices to ensure that only authorized users have access to sensitive data and applications.
Step 4: Monitor Security Events and Alerts
Security monitoring is essential to detect and respond to security threats quickly and effectively. Use IBM Cloud Security Advisor and IBM Cloud Security Hub to monitor security events and alerts in real-time. Configure security policies and alerts to notify you of potential security threats, and have a plan in place to respond to security incidents quickly and effectively.
Step 5: Regular Security Assessments
Regular security assessments are essential to maintain IBM Cloud Security and Compliance in the long term. Use IBM Cloud Security and Compliance tools to perform regular security assessments, identify potential vulnerabilities, and take corrective action. Train users on security best practices and conduct regular phishing and social engineering tests to ensure that users are aware of potential security threats and how to respond to them.
Step 6: Incident Response Planning
Incident response planning is critical to responding to security incidents quickly and effectively. Have a plan in place to respond to security incidents, including identifying the incident response team, defining incident response procedures, and testing the incident response plan regularly.
Real-World Examples of IBM Cloud Security and Compliance
Implementing IBM Cloud Security and Compliance can be a complex process, but many organizations have successfully implemented these solutions in their cloud environments. Here are some real-world examples of organizations that have implemented IBM Cloud Security and Compliance:
Example 1: Financial Services Organization
A financial services organization needed to secure sensitive customer data and maintain regulatory compliance in a complex cloud environment. The organization implemented IBM Cloud Security and Compliance solutions, including IBM Cloud Security Advisor and IBM Cloud Security Hub, to monitor security events and alerts in real-time. The organization also used IBM Cloud Identity to manage user identities and access to cloud resources. As a result, the organization was able to maintain regulatory compliance and improve its security posture, reducing the risk of data breaches and other security incidents.
Example 2: Healthcare Organization
A healthcare organization needed to secure sensitive patient data and maintain compliance with healthcare regulations, such as HIPAA. The organization implemented IBM Cloud Security and Compliance solutions, including IBM Cloud Key Protect, to encrypt patient data and protect it from unauthorized access. The organization also used IBM Cloud Identity to manage user identities and access to cloud resources. As a result, the organization was able to maintain compliance with healthcare regulations and improve its security posture, reducing the risk of data breaches and other security incidents.
Example 3: Retail Organization
A retail organization needed to secure sensitive customer data and maintain compliance with payment card industry (PCI) regulations. The organization implemented IBM Cloud Security and Compliance solutions, including IBM Cloud Security Advisor and IBM Cloud Security Hub, to monitor security events and alerts in real-time. The organization also used IBM Cloud Identity to manage user identities and access to cloud resources. As a result, the organization was able to maintain compliance with PCI regulations and improve its security posture, reducing the risk of data breaches and other security incidents.
Challenges and Solutions
Implementing IBM Cloud Security and Compliance can be challenging, especially in complex cloud environments. Some of the challenges organizations may face include configuring security settings, managing user identities and access, and monitoring security events and alerts. However, with the right approach and tools, organizations can overcome these challenges and achieve their security and compliance goals. Some solutions to these challenges include:
- Configuring security settings: Use IBM Cloud Security and Compliance tools to configure security settings quickly and easily. Follow best practices for data encryption, identity and access management, and security monitoring.
- Managing user identities and access: Use IBM Cloud Identity to manage user identities and access to cloud resources. Implement multi-factor authentication, role-based access control, and other best practices to ensure that only authorized users have access to sensitive data and applications.
- Monitoring security events and alerts: Use IBM Cloud Security Advisor and IBM Cloud Security Hub to monitor security events and alerts in real-time. Configure security policies and alerts to notify you of potential security threats, and have a plan in place to respond to security incidents quickly and effectively.
Best Practices for Maintaining IBM Cloud Security and Compliance
Implementing IBM Cloud Security and Compliance is just the beginning. To ensure long-term success, organizations must follow best practices for maintaining these solutions. Here are some best practices for maintaining IBM Cloud Security and Compliance:
Best Practice 1: Regular Security Assessments
Regular security assessments are essential for maintaining IBM Cloud Security and Compliance. Use IBM Cloud Security and Compliance tools to perform regular security assessments, identify potential vulnerabilities, and take corrective action. Schedule regular security assessments, such as quarterly or annually, to ensure that your cloud environment remains secure and compliant.
Best Practice 2: User Training
User training is essential for maintaining IBM Cloud Security and Compliance. Train users on security best practices, such as creating strong passwords, recognizing phishing emails, and reporting security incidents. Provide regular training sessions, such as monthly or quarterly, to ensure that users are aware of potential security threats and how to respond to them.
Best Practice 3: Incident Response Planning
Incident response planning is critical for maintaining IBM Cloud Security and Compliance. Have a plan in place to respond to security incidents quickly and effectively. Define incident response procedures, identify the incident response team, and test the incident response plan regularly. Ensure that all users are aware of the incident response plan and know how to report security incidents.
Best Practice 4: Regular Software Updates
Regular software updates are essential for maintaining IBM Cloud Security and Compliance. Ensure that all cloud infrastructure, applications, and software are up-to-date with the latest security patches and updates. Schedule regular software updates, such as monthly or quarterly, to ensure that your cloud environment remains secure and compliant.
Best Practice 5: Access Management
Access management is critical for maintaining IBM Cloud Security and Compliance. Implement multi-factor authentication, role-based access control, and other best practices to ensure that only authorized users have access to sensitive data and applications. Regularly review user access rights and remove access for users who no longer require it.
Best Practice 6: Data Backup and Disaster Recovery
Data backup and disaster recovery are essential for maintaining IBM Cloud Security and Compliance. Implement data backup and disaster recovery solutions to ensure that your data is protected and recoverable in the event of a security incident or disaster. Test your data backup and disaster recovery solutions regularly to ensure that they are working correctly.
IBM Cloud Security and Compliance vs. Competitors
When it comes to cloud security and compliance, organizations have a variety of solutions to choose from. However, IBM Cloud Security and Compliance stands out from the competition for several reasons. Here are some unique features and benefits of IBM Cloud Security and Compliance, and why organizations should consider it for their cloud security and compliance needs.
Advanced Security Monitoring
IBM Cloud Security and Compliance offers advanced security monitoring capabilities that enable organizations to detect and respond to security threats quickly and effectively. With real-time security event monitoring, threat intelligence, and automated threat response, IBM Cloud Security and Compliance provides organizations with the visibility and control they need to secure their cloud environments.
Regulatory Compliance
IBM Cloud Security and Compliance helps organizations maintain compliance with industry regulations and standards, such as HIPAA, PCI-DSS, and GDPR. With pre-built compliance templates, automated compliance reporting, and real-time compliance monitoring, IBM Cloud Security and Compliance simplifies compliance management and reduces the burden on IT teams.
Data Encryption and Protection
IBM Cloud Security and Compliance offers advanced data encryption and protection capabilities that enable organizations to secure their data in transit and at rest. With encryption key management, data masking, and data loss prevention, IBM Cloud Security and Compliance provides organizations with the tools they need to protect their sensitive data and prevent data breaches.
Identity and Access Management
IBM Cloud Security and Compliance offers advanced identity and access management capabilities that enable organizations to manage user identities and access to cloud resources. With multi-factor authentication, role-based access control, and single sign-on, IBM Cloud Security and Compliance provides organizations with the tools they need to prevent unauthorized access and protect their cloud resources.
Integration and Customization
IBM Cloud Security and Compliance offers integration and customization capabilities that enable organizations to tailor the solution to their specific security and compliance needs. With API integration, customizable dashboards, and third-party integrations, IBM Cloud Security and Compliance provides organizations with the flexibility they need to secure their cloud environments.
Why IBM Cloud Security and Compliance?
IBM Cloud Security and Compliance offers a comprehensive and proactive approach to cloud security and compliance. With advanced security monitoring, regulatory compliance, data encryption and protection, identity and access management, and integration and customization capabilities, IBM Cloud Security and Compliance provides organizations with the tools they need to secure their cloud environments and protect their sensitive data. By choosing IBM Cloud Security and Compliance, organizations can ensure their cloud environments are secure, compliant, and protected from ever-evolving security threats.
Future Trends in IBM Cloud Security and Compliance
As cloud computing continues to evolve, so too will the challenges and opportunities surrounding IBM Cloud Security and Compliance. Here are some future trends and developments to keep an eye on in the world of IBM Cloud Security and Compliance.
Artificial Intelligence and Machine Learning
Artificial intelligence (AI) and machine learning (ML) are becoming increasingly important in the world of IBM Cloud Security and Compliance. These technologies can help organizations automate threat detection and response, identify vulnerabilities, and predict potential security risks. By leveraging AI and ML, organizations can improve their security posture and respond to threats more quickly and effectively.
Zero Trust Security Models
Zero trust security models are becoming more prevalent in the world of IBM Cloud Security and Compliance. These models assume that all traffic is untrusted and require verification before granting access to resources. By implementing zero trust security models, organizations can reduce the risk of data breaches and improve their overall security posture.
Compliance Automation
Compliance automation is becoming more important in the world of IBM Cloud Security and Compliance. With compliance automation, organizations can reduce the burden of manual compliance tasks and improve their overall compliance posture. By automating compliance tasks, organizations can ensure that they are maintaining compliance with industry regulations and standards, and free up resources to focus on other critical security tasks.
Multi-Cloud Security
Multi-cloud security is becoming more critical in the world of IBM Cloud Security and Compliance. As organizations adopt multiple cloud platforms, they need to ensure that their security and compliance posture is consistent across all platforms. By implementing multi-cloud security strategies, organizations can ensure that their data and applications are secure, regardless of where they are hosted.
Supply Chain Security
Supply chain security is becoming more important in the world of IBM Cloud Security and Compliance. With the increasing complexity of supply chains, organizations need to ensure that their security and compliance posture extends beyond their own infrastructure. By implementing supply chain security strategies, organizations can ensure that their data and applications are secure throughout the entire supply chain.
Why IBM Cloud Security and Compliance?
IBM Cloud Security and Compliance is well-positioned to help organizations navigate these future trends and developments. With advanced security monitoring, regulatory compliance, data encryption and protection, identity and access management, and integration and customization capabilities, IBM Cloud Security and Compliance provides organizations with the tools they need to secure their cloud environments and protect their sensitive data. By choosing IBM Cloud Security and Compliance, organizations can ensure their cloud environments are secure, compliant, and prepared for the future.
Conclusion: The Importance of IBM Cloud Security and Compliance
In today’s digital age, organizations are increasingly moving their operations to the cloud, making IBM Cloud Security and Compliance a critical component of any cloud strategy. With the growing number of cyber threats and the increasing importance of regulatory compliance, organizations must take a comprehensive and proactive approach to cloud security and compliance.
IBM Cloud Security and Compliance offers a range of solutions to help organizations secure their cloud infrastructure, applications, and data, and maintain compliance with industry regulations and standards. From real-time security monitoring and data encryption to identity and access management and compliance automation, IBM Cloud Security and Compliance provides organizations with the tools they need to protect their sensitive data and maintain compliance in the cloud environment.
By following best practices for implementing and maintaining IBM Cloud Security and Compliance, organizations can ensure their cloud environments are secure, compliant, and prepared for the future. With the increasing use of artificial intelligence and machine learning for security monitoring and the growing importance of zero trust security models, IBM Cloud Security and Compliance is well-positioned to help organizations navigate the evolving landscape of cloud security and compliance.
In conclusion, IBM Cloud Security and Compliance is essential for organizations operating in the cloud environment. By prioritizing cloud security and compliance, organizations can protect their sensitive data, maintain regulatory compliance, and ensure the long-term success of their cloud strategies. With IBM Cloud Security and Compliance, organizations can have confidence in their cloud environments and focus on what matters most: delivering value to their customers and stakeholders.