What is IAM Google? An Overview of Google’s Identity and Access Management System
IAM Google, also known as Google Cloud Identity and Access Management, is a robust and unified solution for managing identity and access to resources within Google Cloud Platform (GCP). It plays a critical role in ensuring secure and scalable authentication and authorization services for various GCP components, enabling organizations to control who can access their data and applications and what actions they can perform.
At the heart of IAM Google are three main components: users, groups, and roles. Users represent individual identities that need access to GCP resources. Groups are collections of users who share similar access requirements, making it easier to manage permissions for multiple users simultaneously. Roles, on the other hand, define a set of permissions that determine what actions a user or group can perform on specific GCP resources.
IAM Google enables fine-grained access control, allowing organizations to precisely define and manage user permissions. This approach not only enhances security but also improves efficiency, as it simplifies the process of managing user access to various GCP resources.
As a key component of GCP, IAM Google is designed to integrate seamlessly with other GCP services, such as Compute Engine, Kubernetes Engine, and Cloud Storage. By leveraging IAM policies, organizations can effectively manage access to these resources and ensure that only authorized users can perform specific actions, further strengthening their security posture in the cloud.
Key Components of IAM Google: Users, Groups, and Roles
IAM Google comprises several essential components that facilitate secure and efficient identity and access management for Google Cloud Platform (GCP) resources. Users, groups, and roles are the primary building blocks of IAM Google, enabling fine-grained access control and simplified management of user permissions.
Users
Users in IAM Google represent individual identities that require access to GCP resources. These users can be human users, service accounts, or system-level identities. Each user has a unique email address that serves as their identifier within the GCP environment. Users can be granted permissions directly or as members of groups.
Groups
Groups in IAM Google are collections of users who share similar access requirements. Organizing users into groups simplifies the management of permissions, as it allows administrators to assign access controls to a group rather than individually to each user. When a user is added to or removed from a group, their access permissions are automatically updated based on the group’s policies.
Roles
Roles in IAM Google define a set of permissions that determine what actions a user or group can perform on specific GCP resources. IAM Google offers predefined roles that cover common use cases, such as project owners, editors, and viewers. Custom roles can also be created to meet specific organizational needs. By assigning roles to users or groups, administrators can ensure that users have the appropriate access levels to perform their tasks without compromising security.
Together, users, groups, and roles in IAM Google enable organizations to establish a scalable and secure identity and access management strategy. By leveraging these components, administrators can efficiently manage user permissions, ensuring that only authorized users can access and interact with GCP resources.
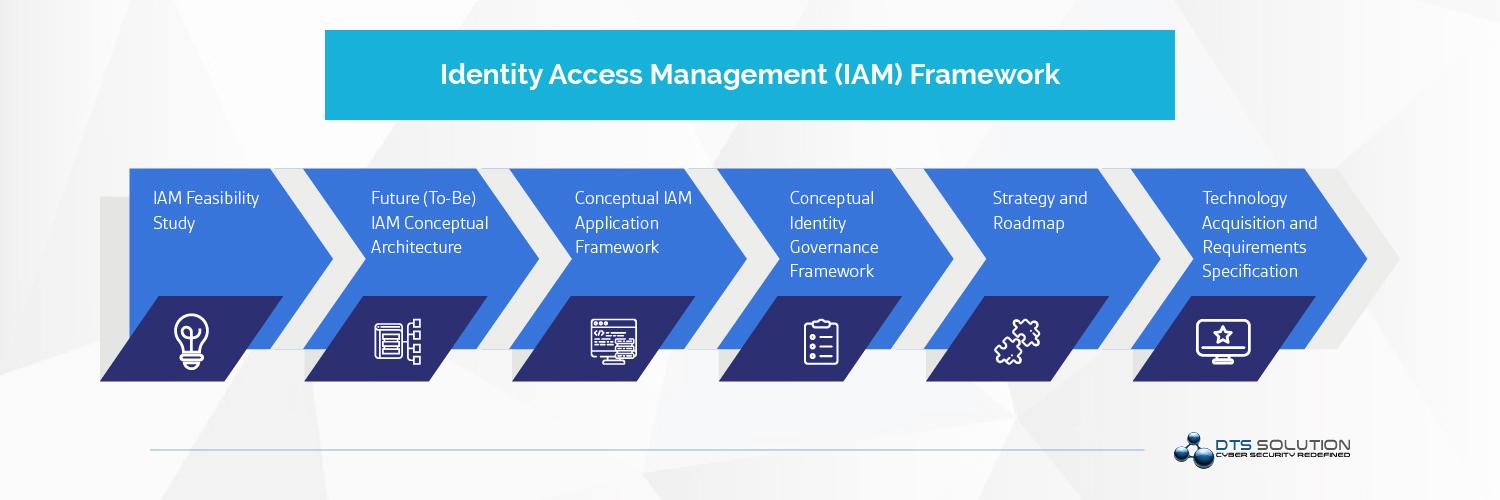
How to Set Up IAM Google: A Step-by-Step Guide
Setting up IAM Google for your Google Cloud Platform (GCP) project is a straightforward process. By following these steps, you can create users, groups, and roles, and assign permissions and policies to ensure secure and efficient access control for your GCP resources.
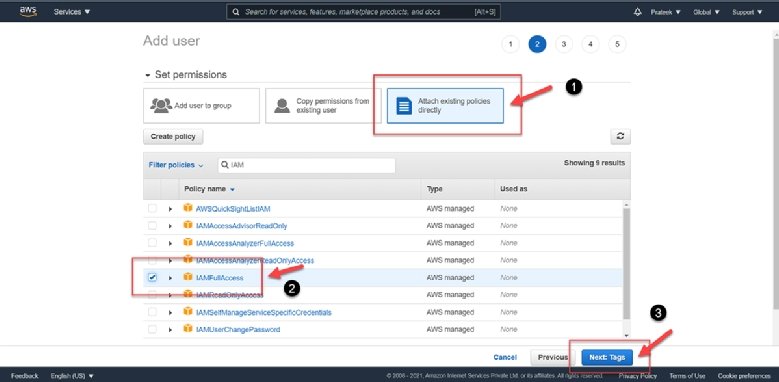
Step 1: Access the IAM Console
Log in to your GCP Console and navigate to the IAM page. Here, you can manage users, groups, roles, and permissions for your project.
Step 2: Create Users
To create a new user, click on the “Create” button in the Users section. Enter the user’s email address, display name, and optional description. Save the new user.
Step 3: Create Groups
In the Groups section, click “Create” and enter a name and description for the group. Add users to the group by typing their email addresses and clicking “Add.” Save the new group.
Step 4: Create Custom Roles (Optional)
If the predefined roles do not meet your needs, you can create custom roles. Navigate to the Roles section and click “Create Role.” Define the role’s permissions and save it. Custom roles can be granted to users or groups like predefined roles.
Step 5: Assign Roles to Users or Groups
To assign a role to a user or group, navigate to the IAM page and locate the user or group in the Members section. Click “Edit” and select the appropriate role from the dropdown menu. Save the updated role assignment.
Step 6: Create and Apply IAM Policies
IAM policies are collections of role assignments that determine who can access specific GCP resources. To create an IAM policy, click “Create Policy” on the IAM page and define the policy’s bindings (role assignments) and conditions (optional constraints). Save the new policy and apply it to your desired GCP resources.
By following these steps, you can effectively set up IAM Google for your GCP project, ensuring secure and efficient access control for your cloud resources.
Best Practices for Implementing IAM Google
Implementing IAM Google effectively within your Google Cloud Platform (GCP) environment requires careful planning and adherence to best practices. By following these expert tips, you can ensure secure, scalable, and efficient access control for your GCP resources.
1. Follow the Principle of Least Privilege
The principle of least privilege (PoLP) states that users and services should be granted the minimum levels of access necessary to perform their tasks. By adhering to PoLP, you can minimize the risk of unauthorized access and potential security breaches.
2. Use Predefined Roles When Possible
IAM Google offers a wide range of predefined roles that cover common use cases. Utilizing these roles simplifies the management of user permissions and reduces the likelihood of configuration errors.
3. Regularly Review Access Controls
Periodically review your IAM policies, roles, and permissions to ensure they remain up-to-date and aligned with your organization’s security requirements. Regular audits can help identify potential security risks and maintain a strong security posture.
4. Implement Role-Based Access Control (RBAC)
RBAC enables you to assign permissions to roles based on job functions or responsibilities. By implementing RBAC, you can ensure that users have the appropriate access levels to perform their tasks without compromising security.
5. Use Separation of Duties (SoD)
SoD involves dividing critical tasks among multiple users or roles, reducing the risk of fraud or errors. By implementing SoD, you can ensure that no single user has excessive control over critical GCP resources.
6. Leverage Conditional Access Policies
Conditional access policies allow you to enforce additional security measures, such as multi-factor authentication (MFA), based on specific conditions, such as user location or device. By leveraging conditional access policies, you can further strengthen your GCP security posture.
7. Document Your IAM Strategy
Documenting your IAM strategy helps ensure consistency and enables easier onboarding and offboarding of users. Maintaining clear and up-to-date documentation is essential for effective IAM management.
By following these best practices, you can optimize your implementation of IAM Google, ensuring secure and efficient access control for your GCP resources.
Integrating IAM Google with Other GCP Services
IAM Google is designed to integrate seamlessly with other Google Cloud Platform (GCP) services, enabling you to manage access to various resources effectively. By understanding how IAM Google interacts with services such as Compute Engine, Kubernetes Engine, and Cloud Storage, you can optimize your GCP security strategy.
IAM Google and Compute Engine
Compute Engine is a service that enables you to run virtual machines (VMs) on GCP. IAM Google policies can be applied to Compute Engine resources, such as VMs and disks, to control user access. By defining IAM roles and permissions for Compute Engine resources, you can ensure that only authorized users can create, modify, or delete VMs and their associated components.
IAM Google and Kubernetes Engine
Kubernetes Engine is a managed service that allows you to deploy, manage, and scale containerized applications on GCP. IAM Google policies can be used to control access to Kubernetes Engine resources, such as clusters, nodes, and pods. By defining IAM roles and permissions for Kubernetes Engine resources, you can ensure that only authorized users can manage and interact with your containerized applications.
IAM Google and Cloud Storage
Cloud Storage is a highly-scalable, durable object storage service on GCP. IAM Google policies can be applied to Cloud Storage buckets and objects to control user access. By defining IAM roles and permissions for Cloud Storage resources, you can ensure that only authorized users can manage, read, or write data stored in your Cloud Storage buckets and objects.
Leveraging IAM Policies for Effective Access Management
IAM policies are collections of role assignments that determine who can access specific GCP resources. By creating and applying IAM policies to your GCP resources, you can ensure that users have the appropriate access levels to perform their tasks without compromising security. IAM policies can be applied at various levels, such as the project, folder, or organization level, allowing you to establish a hierarchical access control structure that meets your organization’s needs.
By understanding how IAM Google integrates with other GCP services, you can effectively manage access to your GCP resources and maintain a strong security posture in the cloud.
Troubleshooting Common IAM Google Issues
Working with IAM Google can sometimes result in challenges and issues. Understanding common problems and their solutions can help you effectively manage access to your Google Cloud Platform (GCP) resources. Here, we discuss several common IAM Google issues and provide practical troubleshooting steps.
Issue 1: Incorrect Role Assignments
Symptom: Users are unable to perform necessary tasks due to insufficient permissions.
Solution: Review role assignments and ensure that users have the appropriate roles and permissions. Use the “gcloud iam roles describe” command to view role details and the “gcloud projects add-iam-policy-binding” command to assign roles to users.
Issue 2: Orphaned IAM Policies
Symptom: IAM policies are no longer associated with any resources, causing confusion and inefficiency.
Solution: Regularly review and remove orphaned IAM policies using the GCP Console, gcloud CLI, or API. Use the “gcloud iam policies list” command to view policies and the “gcloud iam policies delete” command to remove unnecessary policies.
Issue 3: Overly Permissive Roles
Symptom: Users have excessive permissions, increasing the risk of unintended actions or security breaches.
Solution: Adhere to the principle of least privilege and regularly review user roles and permissions. Remove unnecessary permissions and use predefined roles when possible. Utilize custom roles to tailor access levels to specific job functions or responsibilities.
Issue 4: Inconsistent Access Controls Across GCP Services
Symptom: Access controls for various GCP resources are managed independently, leading to inconsistencies and potential security risks.
Solution: Implement a unified access control strategy using IAM Google. Define IAM policies at the project, folder, or organization level to establish a consistent and hierarchical access control structure. Leverage IAM policies to manage access to Compute Engine, Kubernetes Engine, Cloud Storage, and other GCP services.
By understanding and addressing these common IAM Google issues, you can maintain a secure and efficient access control strategy for your GCP resources.
https://www.youtube.com/watch?v=n8LRki4sMQ8
Comparing IAM Google with Other Identity and Access Management Solutions
Google Cloud Platform’s (GCP) Identity and Access Management (IAM) system, also known as IAM Google, is a powerful and flexible solution for managing user identities and controlling access to GCP resources. To better understand IAM Google’s unique features and benefits, let’s compare it with other popular identity and access management solutions, such as AWS Identity and Access Management (IAM) and Microsoft Azure Active Directory.
IAM Google vs. AWS Identity and Access Management (IAM)
Both IAM Google and AWS IAM provide unified identity and access management solutions for their respective cloud platforms. However, IAM Google offers a more streamlined and user-friendly interface, making it easier for administrators to manage user permissions and access controls. Additionally, IAM Google supports more granular access control through the use of custom roles, allowing organizations to tailor access levels to specific job functions or responsibilities.
IAM Google vs. Microsoft Azure Active Directory
While Azure Active Directory is a comprehensive identity and access management solution for Microsoft’s cloud services and on-premises environments, IAM Google focuses solely on managing access to GCP resources. IAM Google’s integration with GCP services is seamless and straightforward, enabling organizations to establish a unified access control strategy for their GCP resources. Furthermore, IAM Google’s support for custom roles provides greater flexibility in defining access levels compared to Azure Active Directory’s predefined role-based access control model.
In summary, IAM Google offers unique features and benefits that set it apart from other identity and access management solutions. Its seamless integration with GCP services, user-friendly interface, and support for granular access control through custom roles make it an ideal choice for organizations looking to manage access to their GCP resources effectively and securely.
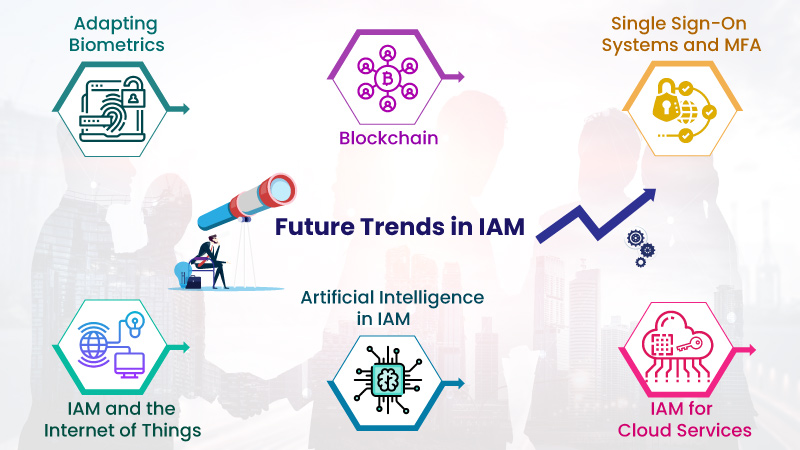
The Future of IAM Google: Emerging Trends and Innovations
Identity and access management (IAM) is a rapidly evolving field, with new trends and innovations constantly reshaping the landscape. As a leading IAM solution for Google Cloud Platform (GCP), IAM Google is well-positioned to meet the changing needs of GCP users and the broader cloud computing landscape. Here, we explore the future of IAM Google and discuss emerging trends and innovations in the field of identity and access management.
Trend 1: Zero Trust Security
Zero Trust Security is a security model that assumes no user or system is trustworthy by default. Instead, it requires continuous verification and authentication for every access request, regardless of the user’s location or device. IAM Google is likely to adopt this model, offering enhanced security features and ensuring that only authenticated and authorized users can access GCP resources.
Trend 2: Machine Learning and AI
Machine learning (ML) and artificial intelligence (AI) are becoming increasingly important in identity and access management, enabling organizations to analyze user behavior and detect potential security threats. IAM Google is likely to incorporate ML and AI technologies, allowing for more intelligent and adaptive access control decisions based on user behavior and risk levels.
Trend 3: Identity as a Service (IDaaS)
Identity as a Service (IDaaS) is a cloud-based identity and access management solution that offers centralized authentication, authorization, and user management services. IAM Google is likely to evolve into a more comprehensive IDaaS solution, providing organizations with a unified identity and access management platform for their GCP and on-premises resources.
Trend 4: Improved User Experience
As IAM solutions become more complex, user experience (UX) is becoming increasingly important. IAM Google is likely to focus on improving UX, offering intuitive and user-friendly interfaces for managing user identities and controlling access to GCP resources. This will enable organizations to effectively manage access controls without requiring extensive IAM expertise.
In conclusion, IAM Google is well-positioned to meet the changing needs of GCP users and the broader cloud computing landscape. By adopting trends such as Zero Trust Security, Machine Learning and AI, Identity as a Service (IDaaS), and improved User Experience, IAM Google will continue to provide secure, scalable, and efficient authentication and authorization services for various GCP resources.