Understanding the Power of Infrastructure as Code (IaC)
Infrastructure as Code (IaC) is revolutionizing how infrastructure is managed, offering a paradigm shift from manual processes to automated, code-driven approaches. IaC automation enables the definition and management of infrastructure through descriptive code, rather than physical hardware configuration or interactive configuration tools. This approach delivers significant advantages over traditional methods, addressing many challenges inherent in manual infrastructure management. Manual processes are often time-consuming, error-prone, and struggle to keep pace with the demands of modern, scalable systems. IaC automation mitigates these risks by providing a repeatable, consistent, and auditable method for provisioning, configuring, and managing infrastructure. The benefits are multifaceted, including increased efficiency, reduced human error, improved scalability, and enhanced collaboration among team members. Through IaC automation, organizations can significantly reduce the time and resources required to deploy and manage infrastructure, allowing IT teams to focus on higher-value tasks.
The core principle of IaC lies in its ability to treat infrastructure as software. This allows for version control, testing, and continuous integration, mirroring software development best practices. By defining infrastructure in code, organizations gain the ability to automate the entire infrastructure lifecycle, from initial provisioning to ongoing maintenance and updates. This automation reduces the risk of human error during configuration, a common source of system instability and security vulnerabilities. IaC automation also promotes consistency across environments, ensuring that development, testing, and production environments are identical, minimizing discrepancies that can lead to deployment issues. The ability to readily replicate entire environments is also beneficial for disaster recovery and business continuity planning. Popular IaC tools, such as Terraform, Ansible, Chef, and Puppet, provide various functionalities and approaches to achieve this automation. Each tool offers its own strengths and is best suited for specific use cases, allowing organizations to select the tool best aligned with their infrastructure and team expertise. The adoption of IaC automation represents a significant step towards more agile, efficient, and reliable IT operations.
The rise of cloud computing has further amplified the need for IaC automation. Cloud environments often require rapid provisioning and scaling, capabilities that are difficult to achieve efficiently through manual processes. IaC automation excels in dynamic cloud environments, providing the agility and scalability needed to meet evolving business demands. Moreover, IaC automation complements DevOps practices, enabling faster release cycles and improved collaboration between development and operations teams. By incorporating IaC into a broader DevOps strategy, organizations can unlock significant improvements in their software delivery pipeline, leading to faster time-to-market and greater customer satisfaction. The benefits of implementing IaC automation extend far beyond simply automating infrastructure management; it contributes to a more streamlined, efficient, and resilient IT ecosystem. Adopting IaC automation is not just a trend; it’s a necessity for organizations striving for operational excellence in today’s dynamic IT landscape.
Choosing the Right IaC Tool for Your Needs
Selecting the optimal IaC tool hinges on several crucial factors. Terraform, renowned for its declarative approach and broad cloud provider support, excels in managing complex, multi-cloud infrastructures. Its extensive community and rich ecosystem of providers simplify integration with diverse services. However, its declarative nature might present a steeper learning curve for beginners compared to more imperative solutions. Ansible, on the other hand, employs an agentless, imperative approach, making it easier to learn and use, particularly for simpler deployments or ad-hoc tasks. Its agentless architecture reduces overhead, enhancing efficiency for certain workflows. The strength of Ansible lies in its simplicity and suitability for configuration management tasks within existing infrastructure. Yet, Ansible’s capabilities might be perceived as less robust than Terraform for managing large-scale, complex deployments. Chef and Puppet, both known for their focus on configuration management, are powerful options for enterprises needing robust, centralized control over their IT infrastructure. These tools are particularly adept at managing existing infrastructure and offer sophisticated features for automation and orchestration of large IT environments. However, they often come with higher learning curves and more complex setups compared to Ansible or Terraform, potentially increasing initial implementation costs. The choice of IaC tool for efficient iac automation should align with the project’s scope, complexity, team expertise, and existing infrastructure. A small-scale project might benefit from Ansible’s simplicity, while a large multi-cloud deployment may be better suited for Terraform’s power and flexibility.
Consider a scenario where a company needs to deploy a new web application across multiple AWS regions. Terraform’s ability to define the entire infrastructure as code, ensuring consistency across regions, would be invaluable. Alternatively, imagine a team needing to configure a few servers with specific software packages. Ansible’s simpler, imperative approach might be faster and more efficient. For a large enterprise with established IT infrastructure and a need for robust configuration management, Chef or Puppet could provide the centralized control and sophisticated features required. This iac automation necessitates careful consideration of each tool’s strengths and weaknesses within the context of the specific requirements of your organization. The selection process should involve a thorough evaluation of the project’s demands, team capabilities and the long-term goals related to maintaining and scaling the IaC infrastructure. Choosing the right tool is crucial to successfully implementing iac automation.
Effective iac automation demands a deep understanding of the diverse tools available and their individual strengths. While Terraform’s declarative approach and broad compatibility make it suitable for complex projects, Ansible provides a simpler alternative for smaller deployments. Chef and Puppet cater to large enterprises needing robust configuration management. The decision of which iac automation tool to utilize should be driven by a careful assessment of factors including project scale, team proficiency, and long-term scalability considerations. This thorough analysis will ensure selection of the most appropriate tool for optimal results and efficient infrastructure management.
How to Automate Your Infrastructure with Terraform: A Step-by-Step Guide
Terraform, a popular IaC automation tool, simplifies infrastructure provisioning. This guide demonstrates deploying a simple virtual machine (VM) using Terraform. First, install Terraform; instructions are readily available online for various operating systems. Next, create a directory for your project and initialize it using the command `terraform init`. This downloads the necessary providers, ensuring compatibility with your chosen cloud platform. The core of Terraform’s automation lies in its configuration files, typically written in HashiCorp Configuration Language (HCL). These files define the desired infrastructure state, acting as a blueprint for the automation process. For our VM, the HCL file would specify details such as the instance type, operating system image, and network configuration. This declarative approach, a key tenet of IaC automation, contrasts sharply with the manual, imperative approach of traditional infrastructure management. Remember that robust IaC automation relies on version control—commit your Terraform code to a repository like Git for tracking changes and collaboration.
To deploy the VM, utilize the `terraform plan` command. This simulates the infrastructure changes, showcasing the actions Terraform will undertake without actually modifying the underlying infrastructure. This crucial step allows reviewing the proposed changes before execution, minimizing unintended consequences. Once satisfied, execute `terraform apply` to deploy the infrastructure as defined in the HCL configuration. Terraform manages the entire process, including resource creation and configuration. Observe that the output provides details of the newly created VM, such as its public IP address. This streamlined approach is a significant advancement over the complex, error-prone manual methods. Effective IaC automation, particularly with Terraform, hinges on modularity. Consider creating reusable modules for common infrastructure components, promoting efficiency and consistency across projects. This best practice simplifies complex infrastructure deployments, reducing the chance of human errors and accelerating the deployment process. Remember to manage state files carefully; these files store the current infrastructure state, essential for maintaining consistency and enabling Terraform to manage changes efficiently. The correct management of state files is crucial for the success of any IaC automation project.
After deployment, managing and updating your infrastructure becomes similarly streamlined. Modify the HCL file to reflect desired changes (e.g., increasing the VM’s memory) and rerun `terraform plan` and `terraform apply`. Terraform intelligently identifies the necessary changes and applies them efficiently. This iterative process, facilitated by the power of IaC automation, drastically reduces downtime and streamlines the maintenance cycle. Terraform’s ability to handle infrastructure updates without disrupting running services underscores its strength as a core component of robust IaC automation. Error handling is another critical aspect of successful IaC automation. While Terraform’s extensive error messages usually provide adequate guidance, incorporating robust error handling into the HCL configuration is a best practice that safeguards against unexpected issues and enhances the overall reliability of your automated infrastructure. This ensures that potential issues are identified and addressed proactively, minimizing disruptions and promoting stability. Furthermore, integrating Terraform with CI/CD pipelines fully automates infrastructure deployments and updates, leading to faster release cycles and higher quality infrastructure management. This synergy between IaC automation and CI/CD is a cornerstone of modern DevOps practices.
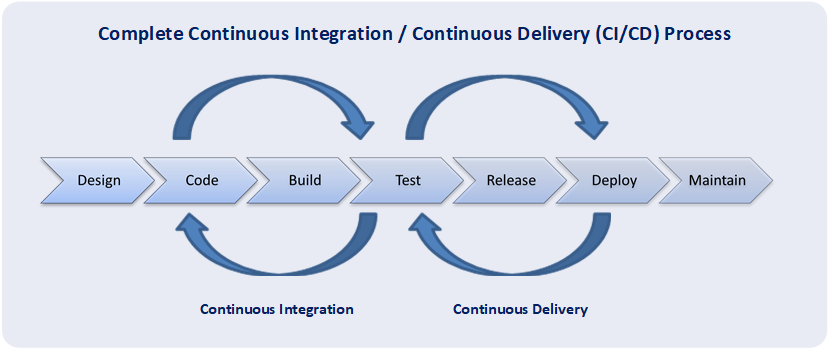
Implementing Continuous Integration/Continuous Delivery (CI/CD) with IaC
Continuous Integration/Continuous Delivery (CI/CD) pipelines significantly enhance the benefits of IaC automation. By integrating IaC with CI/CD, organizations can automate not only infrastructure provisioning but also the entire software delivery lifecycle. This involves automating testing, deployment, and updates, leading to faster release cycles and increased reliability. The core concept is to treat infrastructure as code, managed and versioned alongside application code, allowing for consistent and repeatable deployments across various environments. This approach minimizes human error and ensures that infrastructure remains consistent with the application’s requirements. Successful iac automation within a CI/CD pipeline streamlines the entire process, enabling developers to focus on building and deploying applications rather than managing infrastructure manually. The integration of IaC and CI/CD promotes a DevOps culture, fostering collaboration and improving communication between development and operations teams.
A typical CI/CD pipeline with IaC might start with developers committing IaC code to a version control system like Git. This triggers an automated build process, where the IaC code is validated, tested, and then deployed to a staging environment. Automated testing in this context includes verifying that the provisioned infrastructure conforms to predefined specifications and that the application functions correctly within that environment. Once the staging environment tests are successful, the same IaC code is deployed to the production environment. This automated process significantly reduces deployment time and risk, minimizing the chance of errors and ensuring consistent infrastructure across all environments. The power of iac automation shines in this context as the entire process can be repeated reliably and consistently for new features, bug fixes, or infrastructure upgrades. Properly implemented, this level of automation reduces downtime and increases the speed of delivering value to end-users.
Moreover, integrating IaC into a CI/CD pipeline enables automated rollbacks in case of deployment failures. If an issue arises in the production environment, the pipeline can be reversed to a previous known-good state, quickly mitigating the impact of any errors. This capability is crucial for maintaining system stability and reducing the potential for service disruptions. By implementing robust monitoring and logging throughout the CI/CD pipeline, organizations gain valuable insights into the performance and health of their infrastructure, allowing for proactive identification and resolution of potential problems. This proactive approach minimizes downtime and maximizes the efficiency of the iac automation strategy. Effective monitoring also enables the collection of data that can inform future infrastructure improvements, leading to a continuously evolving and optimized infrastructure landscape.
Securing Your IaC Infrastructure
Infrastructure as code (IaC) automation offers significant advantages, but security remains paramount. Protecting IaC code and the infrastructure it manages requires a multi-layered approach. Implementing robust access control is crucial; this involves limiting who can access and modify IaC code and the associated infrastructure. Leveraging role-based access control (RBAC) within your chosen IaC tool and cloud provider is highly recommended. Regular security audits and penetration testing should be part of a comprehensive security strategy for IaC automation, ensuring vulnerabilities are identified and addressed promptly. Employing secrets management tools to store sensitive information, like API keys and passwords, outside the IaC codebase itself is a critical step, preventing accidental exposure.
Version control, typically through Git or similar systems, plays a vital role in IaC security. It allows for tracking changes, collaboration, and rollback capabilities in case of errors or security breaches. IaC automation, when coupled with version control, significantly enhances security by providing an audit trail of all modifications. Furthermore, integrating security scanning tools into your CI/CD pipeline allows for automated vulnerability checks before deployment. This proactive approach helps identify and remediate security flaws early in the development lifecycle, mitigating potential risks. The importance of IaC automation for security cannot be overstated; adopting best practices will create a more secure infrastructure.
Another critical aspect of securing IaC automation is the use of infrastructure-as-code (IaC) scanning tools. These tools automatically analyze IaC code for potential security vulnerabilities and misconfigurations, such as insecure network settings or improperly configured access controls. Regularly scanning your IaC code with these tools provides an early warning system for potential security issues, allowing for prompt remediation and reducing the risk of exploitation. Properly managing dependencies and ensuring all software components are up-to-date and patched contributes to a more secure IaC system. Regularly updating IaC tools and the underlying infrastructure strengthens overall security posture. Remember, a robust security approach for IaC automation is an ongoing process that demands continuous vigilance and adaptation.
Managing IaC Configuration and Version Control for Enhanced IaC Automation
Effective configuration management and version control are paramount for successful IaC automation. Without a robust system in place, managing infrastructure becomes complex and error-prone, negating many of the benefits of automation. Utilizing a version control system like Git is essential for tracking changes, collaborating effectively, and enabling easy rollbacks in case of issues. Git’s branching capabilities are particularly useful for managing different environments—development, testing, staging, and production—each with its own configuration files. This allows developers to work on changes independently without affecting the stability of live systems. The ability to revert to previous versions in case of a faulty deployment is a crucial aspect of risk mitigation within IaC automation.
Implementing a structured approach to configuration management further enhances IaC automation. This typically involves creating reusable modules and templates to avoid repetitive coding and ensure consistency across environments. These modules can encapsulate common infrastructure components, such as virtual machines, networks, and databases, simplifying the process of building and managing complex systems. Properly documenting these modules is critical for maintainability and understanding their functionality. By using a consistent naming convention and a clear structure for configuration files, teams can more easily collaborate and maintain the IaC codebase, leading to better overall IaC automation practices. This organized approach also makes it easier to audit and manage configurations, reducing the risk of errors and ensuring compliance with security policies.
Beyond basic version control, strategies for managing environment-specific configurations are crucial for effective IaC automation. Techniques such as environment variables, configuration files, or dedicated code branches for different environments ensure that sensitive information, such as passwords and API keys, are not directly embedded in the IaC code. Instead, these credentials can be securely managed using dedicated secret management tools, enhancing security and reducing the risk of exposure. Moreover, employing a robust infrastructure-as-code strategy allows for the automation of the entire lifecycle, from initial deployment to ongoing maintenance and updates. This streamlined process, facilitated by efficient configuration management and version control, significantly reduces manual intervention and improves the reliability of the automated infrastructure. This continuous improvement cycle, driven by the use of IaC automation, results in a more efficient, secure, and scalable system.
Monitoring and Maintaining Your Automated Infrastructure
Effective monitoring is crucial for any infrastructure, and IaC automation enhances this process by providing a centralized view of your resources. Tools like Datadog, Prometheus, and Grafana offer robust monitoring capabilities, allowing for real-time tracking of resource utilization, such as CPU, memory, and network bandwidth. These tools integrate seamlessly with IaC, enabling automated alerts based on predefined thresholds. By leveraging these monitoring tools, organizations gain proactive insights into the health of their infrastructure, facilitating timely interventions before minor issues escalate into major outages. This proactive approach to monitoring is a key advantage of IaC automation, ensuring systems remain operational and efficient. Automated dashboards can visualize key performance indicators (KPIs), making it easy to identify trends and potential problems early on. This allows for more efficient resource allocation and prevents unexpected downtime.
Maintaining your automated infrastructure goes beyond simple monitoring; it involves a continuous process of refinement and improvement. Regular security audits are vital to identify vulnerabilities and ensure compliance with security standards. IaC automation facilitates these audits by providing a clear and auditable trail of infrastructure changes. This contrasts sharply with manual infrastructure management, where tracking changes can be challenging and error-prone. Furthermore, the ability to roll back changes quickly and easily, a key feature of IaC, minimizes the impact of potential errors during maintenance. By incorporating comprehensive logging and version control into the IaC process, organizations gain greater control over their infrastructure, simplifying troubleshooting and incident response. Regular reviews of the IaC code itself should also be part of the maintenance routine, ensuring code quality and identifying areas for improvement. This iterative process of monitoring, analysis, and refinement is fundamental to the success of any IaC automation strategy.
Implementing proactive maintenance measures further enhances the reliability and efficiency of your IaC automation. Scheduled tasks for software updates, security patching, and performance optimization can be automated through IaC, reducing the manual effort involved in these essential maintenance procedures. This scheduled automation ensures your infrastructure remains secure and up-to-date. Moreover, the ability to easily clone and replicate infrastructure components within your IaC framework simplifies disaster recovery planning. This ensures business continuity in case of unexpected failures or outages. By consistently implementing proactive maintenance and leveraging the inherent capabilities of IaC automation, organizations can achieve significantly higher levels of uptime, efficiency, and security in their IT infrastructure. Continuous improvement and monitoring are vital components of a successful and robust IaC automation implementation.
Advanced IaC Techniques and Best Practices for Enhanced IaC Automation
To truly harness the power of IaC automation, organizations should explore advanced techniques that optimize efficiency and scalability. Modularization, a cornerstone of effective IaC, allows for the creation of reusable components. These modules encapsulate infrastructure elements, promoting consistency and reducing redundancy across deployments. By breaking down complex infrastructure into smaller, manageable modules, teams can simplify development, testing, and maintenance. This approach significantly streamlines the IaC automation process, making it easier to manage and update infrastructure across various environments. Furthermore, effective IaC automation leverages version control systems like Git, enabling collaborative development, trackable changes, and the ability to revert to previous states if necessary. This is crucial for maintaining a secure and reliable infrastructure. Implementing robust testing strategies, such as unit and integration testing of IaC modules, is essential to ensure the reliability and stability of automated deployments. Regular security audits and penetration testing are also vital for identifying and addressing vulnerabilities within the IaC codebase. Proper access control, utilizing role-based access control (RBAC) models, is key to secure IaC automation and protect sensitive infrastructure information.
Cloud providers, such as AWS, Azure, and GCP, offer powerful tools and services that seamlessly integrate with IaC. Leveraging these platform-specific services can enhance automation capabilities. For example, using managed services for databases, networking, or storage can simplify infrastructure management and reduce operational overhead. This synergy between IaC and cloud platforms extends the benefits of automation throughout the entire infrastructure lifecycle. Infrastructure-as-a-Service (IaaS) platforms are instrumental in achieving efficient IaC automation. These platforms provide on-demand access to computing resources, allowing for dynamic scaling and flexible provisioning based on real-time needs. By combining IaC with IaaS, organizations can create highly resilient and scalable infrastructure that adapts to changing demands. Proper planning and design are crucial for successful IaC implementation. Adopting a modular approach, employing a well-defined naming convention, and adhering to coding best practices contributes to maintainable and scalable IaC code. Regular code reviews ensure quality and identify potential issues early in the development cycle. Comprehensive documentation is essential for facilitating collaboration and knowledge sharing amongst team members.
Successfully scaling IaC implementations requires a proactive approach to maintenance and updates. Regularly reviewing and updating IaC code to reflect changes in infrastructure requirements or security best practices is paramount. This ensures the IaC automation remains aligned with organizational needs and prevents potential vulnerabilities from being exploited. Implementing a robust monitoring and logging system is critical for identifying potential issues and ensuring the health and stability of the automated infrastructure. This provides valuable insights into system performance, resource utilization, and potential areas for optimization. Continuous monitoring allows for proactive intervention, preventing potential outages or performance degradation. By combining advanced techniques, integrating with cloud platforms and IaaS, and implementing best practices, organizations can significantly enhance their IaC automation strategies, leading to more robust, scalable, and secure infrastructure management. The adoption of IaC automation offers a significant competitive advantage, allowing for rapid deployment of new services and efficient management of existing systems.