Unraveling the Process: An Overview of Connecting to an EKS Cluster
Connecting to an Elastic Kubernetes Service (EKS) cluster is an essential skill for managing and deploying applications in a containerized environment. This comprehensive guide will walk you through the process of how to connect to an EKS cluster, providing valuable insights and best practices along the way. EKS, a managed Kubernetes service by Amazon Web Services (AWS), simplifies the deployment, scaling, and management of containerized applications.
Prerequisites: Setting the Stage for a Successful Connection
Before connecting to an EKS cluster, you need to set up several tools and configurations. First, install and configure the AWS Command Line Interface (CLI), which allows you to interact with AWS services through the command line. The AWS CLI is essential for creating and managing EKS clusters and other AWS resources.
Next, install and configure kubectl, the Kubernetes command-line tool. Kubectl enables you to run commands against Kubernetes clusters, such as deploying applications, managing resources, and troubleshooting issues. Lastly, install and configure eksctl, a simple CLI tool for creating clusters on EKS.
These tools play a crucial role in how to connect to an EKS cluster. The AWS CLI facilitates cluster creation and management, while kubectl and eksctl provide the means to interact with and configure your cluster. Ensuring these tools are correctly installed and configured is vital for a smooth connection process.
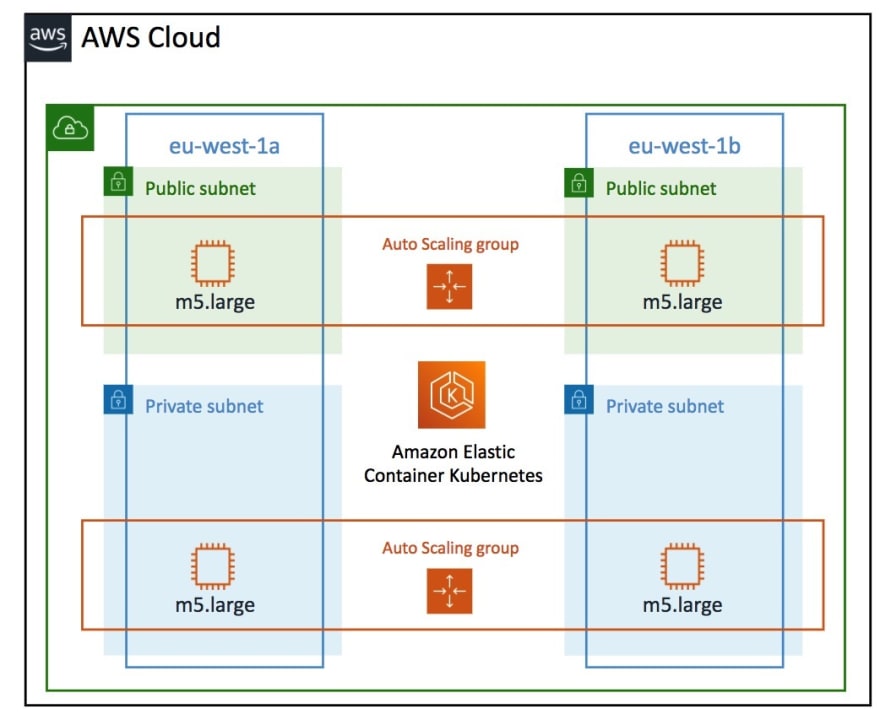
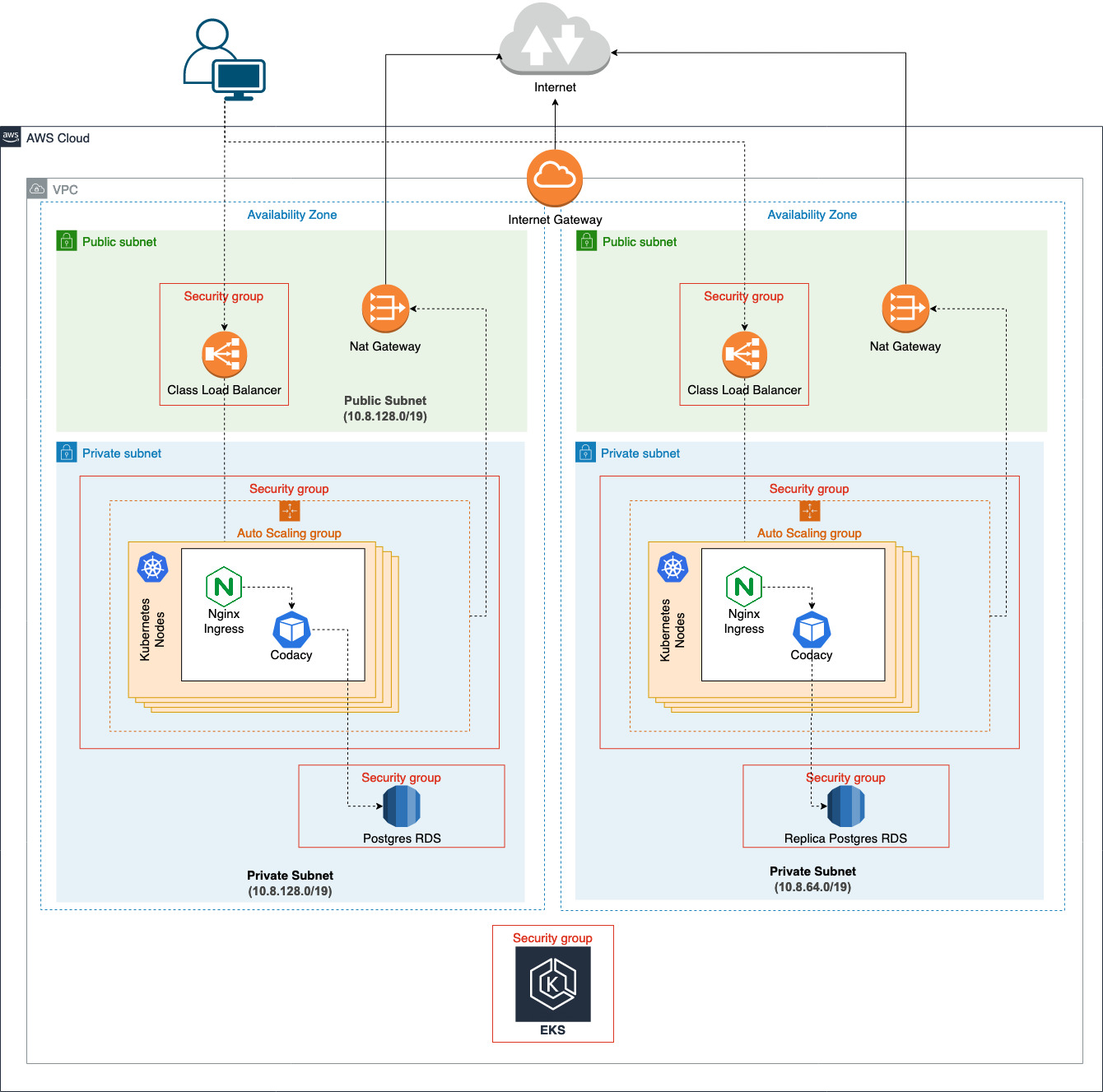
Creating an EKS Cluster: The Foundation of Your Connection
To establish a connection to an EKS cluster, you first need to create a cluster using eksctl. This powerful CLI tool simplifies the process of creating, updating, and managing EKS clusters. Start by installing eksctl on your local machine, ensuring it’s properly configured with your AWS credentials.
Next, configure your EKS cluster settings, including the cluster name, region, and node groups. Node groups consist of worker nodes, which are EC2 instances that run your Kubernetes workloads. Determine the number and type of worker nodes based on your application requirements and resource needs. Properly configuring your cluster settings and worker nodes is crucial for a secure connection.
Once your configuration is complete, create the EKS cluster using the following command:
eksctl create cluster -f cluster-config.yaml Replace “cluster-config.yaml” with the path to your configuration file. eksctl will create the EKS cluster and all required resources, such as the Kubernetes API server, worker nodes, and networking components. After the creation process is complete, you’ll have a fully functional EKS cluster ready for connection and management.
Authenticating Your Access: Configuring kubectl for Your EKS Cluster
To interact with your EKS cluster, you must configure kubectl with the correct authentication settings. This process involves using kubeconfig files and the aws-iam-authenticator, which enables secure communication between kubectl and your EKS cluster.
A kubeconfig file is a collection of API endpoint, user, and authentication information that allows kubectl to communicate with a Kubernetes cluster. By default, kubectl looks for a kubeconfig file at ~/.kube/config. When working with an EKS cluster, you need to update this file with the correct settings for your cluster.
To update your kubeconfig file, follow these steps:
- Retrieve the AWS credentials and endpoint for your EKS cluster using the AWS CLI:
aws eks update-kubeconfig --name - Verify that the aws-iam-authenticator is correctly installed and configured. This tool is required for authenticating kubectl commands with an EKS cluster.
After completing these steps, your kubectl configuration should be properly authenticated with your EKS cluster. You can now manage Kubernetes resources, deploy applications, and interact with your cluster using kubectl commands.
Maintaining a secure connection is essential when working with an EKS cluster. Always ensure that your kubeconfig file and aws-iam-authenticator are up-to-date and configured correctly. Regularly review access management policies and monitor your cluster for suspicious activity to protect your data and resources.
Establishing the Connection: Using kubectl to Interact with Your EKS Cluster
After configuring kubectl, you can now connect to your EKS cluster and manage Kubernetes resources. To ensure a secure connection, follow these best practices:
- Use encrypted communication channels, such as HTTPS, when interacting with your EKS cluster.
- Limit the number of users with access to your kubeconfig file and kubectl commands.
- Regularly review and update access management policies for your EKS cluster.
To connect to your EKS cluster using kubectl, simply run the following command:
kubectl get svc This command retrieves a list of services running on your EKS cluster. You can also use kubectl to deploy applications, manage pods, and interact with various Kubernetes resources.
For example, to deploy a simple Nginx application on your EKS cluster, create a deployment configuration file named “nginx-deployment.yaml” with the following content:
apiVersion: apps/v1 kind: Deployment metadata: name: nginx-deployment spec: selector: matchLabels: app: nginx replicas: 3 template: metadata: labels: app: nginx spec: containers: - name: nginx image: nginx:1.14.2 ports: - containerPort: 80 Then, apply this configuration using the following command:
kubectl apply -f nginx-deployment.yaml This command creates a new Nginx deployment with three replicas on your EKS cluster. By understanding how to use kubectl effectively, you can efficiently manage your Kubernetes resources and ensure a secure connection to your EKS cluster.
Troubleshooting Connections: Identifying and Resolving Common Issues
When connecting to an EKS cluster, you may encounter various challenges and errors. Here are some common issues and their solutions:
Error: Unable to locate credentials
This error occurs when the AWS CLI cannot find your AWS credentials. To resolve this issue, ensure that your AWS credentials are correctly configured and accessible to the AWS CLI. You can configure your AWS credentials using the aws configure command or by setting environment variables.
Error: You must be logged in to the server (Unauthorized)
This error is typically caused by incorrect kubectl configuration or insufficient permissions. Double-check your kubeconfig file and ensure that it contains the correct settings for your EKS cluster. Additionally, verify that your IAM role or user has the necessary permissions to interact with the EKS cluster.
Error: the server doesn’t have a resource type “pods”
This error indicates that kubectl is not correctly configured to communicate with your EKS cluster. Ensure that your kubeconfig file is up-to-date and correctly configured. You can update your kubeconfig file using the aws eks update-kubeconfig command.
If you encounter issues that are not covered in this guide, consult the official AWS documentation or seek help from the Kubernetes and AWS communities. Remember that maintaining a secure connection to your EKS cluster is essential, so always follow best practices for access management, updates, and monitoring.
Maintaining Security: Best Practices for EKS Cluster Connections
Security is a top priority when connecting to an EKS cluster. To ensure a secure connection, follow these best practices:
Proper Access Management
Limit access to your EKS cluster by implementing strict IAM policies and roles. Only grant the minimum necessary permissions to users and services. Regularly review and update these policies to ensure they remain relevant and secure.
Regular Updates
Keep your EKS cluster, worker nodes, and tools up-to-date with the latest patches and updates. This ensures that you benefit from the latest security features and fixes, reducing the risk of vulnerabilities and exploits.
Monitoring
Monitor your EKS cluster and its connections for suspicious activity. Use tools like CloudTrail, CloudWatch, and Prometheus to monitor API calls, cluster events, and resource usage. Regularly review logs and alerts to detect and respond to potential security threats.
Use of Encryption
Encrypt all communication channels between your local machine and the EKS cluster using HTTPS and other encryption technologies. This helps protect sensitive data from unauthorized access and eavesdropping.
Secure kubectl Configuration
Ensure that your kubectl configuration is secure and up-to-date. Regularly review and update your kubeconfig file, and limit access to this file to only those who require it.
By following these best practices, you can maintain a secure connection to your EKS cluster and protect your data and resources from potential threats.
Exploring Further: Advanced EKS Cluster Connection Techniques
Once you have mastered the basics of connecting to an EKS cluster, consider exploring advanced techniques to enhance your skills and productivity. Here are a few techniques to get you started:
VPC Peering
VPC peering enables you to connect two VPCs in the same or different regions, allowing resources in both VPCs to communicate with each other as if they were in the same network. By using VPC peering, you can establish a secure and private connection between your EKS cluster and other resources in your VPC.
Private Link Endpoints
Private link endpoints enable you to securely access AWS services, such as EKS, from your own VPC without exposing traffic to the public internet. By using private link endpoints, you can reduce the attack surface and improve the security of your EKS cluster connections.
Third-Party Tools
Various third-party tools and services can help you manage and connect to your EKS cluster more efficiently. These tools offer features such as visualization, monitoring, and automation, making it easier to manage your cluster and its resources.
By exploring these advanced techniques, you can enhance your skills and productivity when connecting to an EKS cluster. Always remember to follow best practices for security, access management, and monitoring to ensure the protection of your cluster and data.