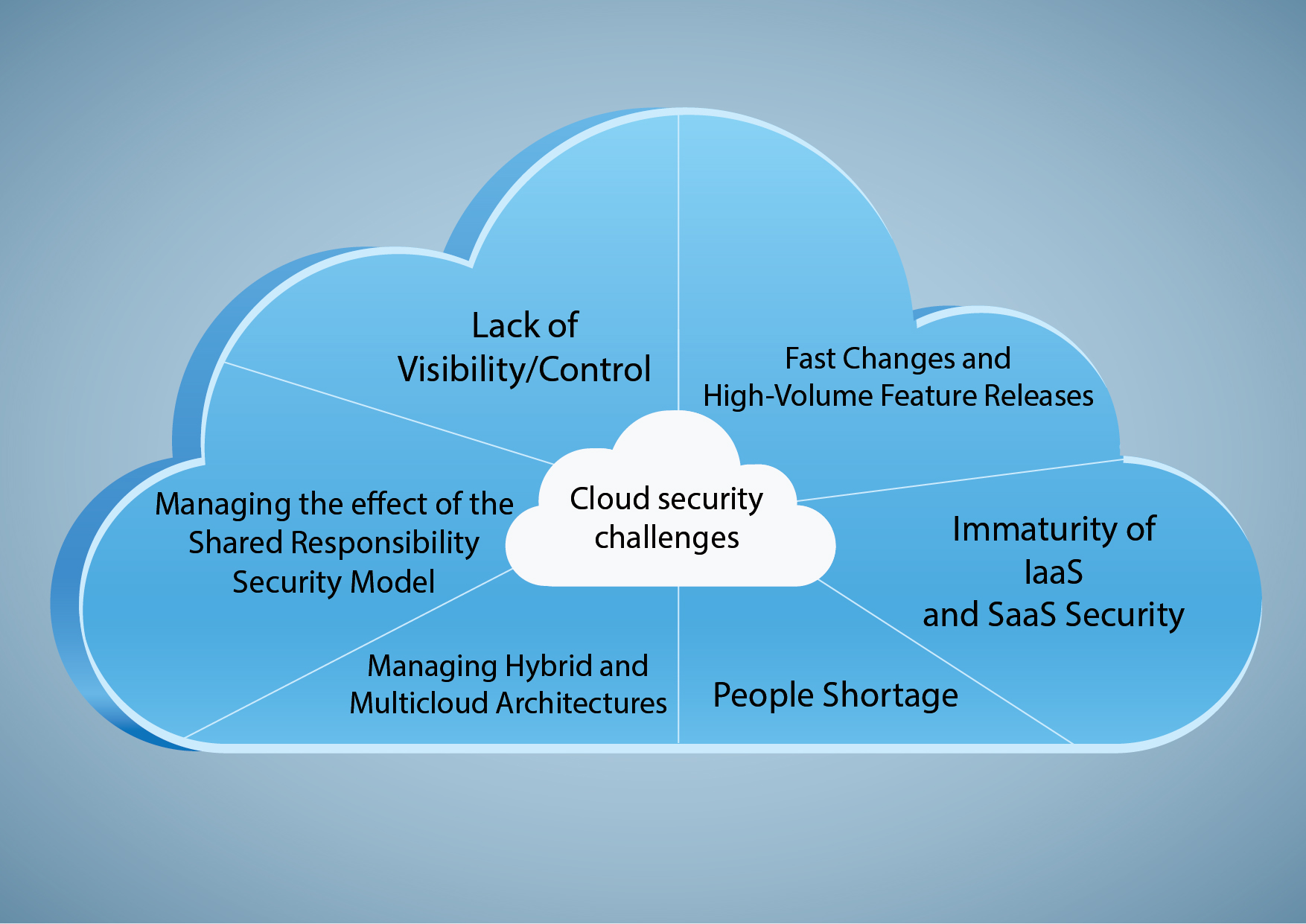
Understanding Google Cloud Security and Compliance
Google Cloud security and compliance are critical considerations for businesses and organizations that use cloud services. Google Cloud offers a range of security features and compliance certifications to help protect data and meet regulatory requirements. By understanding these features and certifications, organizations can leverage the benefits of Google Cloud, such as scalability, reliability, and data protection.
Google Cloud security is a comprehensive approach that includes various components such as Identity and Access Management (IAM), Security Key Enforcement, and Data Loss Prevention (DLP). IAM allows organizations to control who has access to their data and resources, while Security Key Enforcement provides an additional layer of security by requiring users to provide a second form of authentication. DLP helps organizations protect sensitive data by automatically detecting and encrypting it.
Google Cloud compliance framework includes various certifications and standards such as SOC 1, SOC 2, ISO 27001, and HIPAA. These certifications ensure that Google Cloud meets various industry and regulatory requirements, such as financial reporting, data privacy, and healthcare regulations. By using Google Cloud, organizations can demonstrate their commitment to data protection and regulatory compliance.
Key Components of Google Cloud Security
Google Cloud security is a comprehensive approach that includes various components to help protect data and resources. Here are some of the key components of Google Cloud security:
Identity and Access Management (IAM)
IAM allows organizations to control who has access to their data and resources. With IAM, organizations can create and manage user roles and permissions, set up access controls, and monitor user activity. For example, an organization can use IAM to grant a user access to a specific project or resource, or to restrict a user’s access to read-only.
Security Key Enforcement
Security Key Enforcement provides an additional layer of security by requiring users to provide a second form of authentication. With Security Key Enforcement, users must provide a physical security key, such as a YubiKey, in addition to their username and password. This helps prevent unauthorized access to data and resources, even if a user’s password is compromised.
Data Loss Prevention (DLP)
DLP helps organizations protect sensitive data by automatically detecting and encrypting it. With DLP, organizations can set up policies to detect and protect sensitive data, such as credit card numbers or social security numbers. DLP can also help organizations comply with data privacy regulations, such as GDPR or HIPAA.
Network Security
Google Cloud provides various network security features, such as firewalls, Virtual Private Cloud (VPC), and Cloud Load Balancing. These features help protect data and resources from external threats, such as DDoS attacks or malicious traffic.
Encryption
Google Cloud offers encryption at rest and in transit for data and resources. With encryption, organizations can protect their data from unauthorized access, even if the data is intercepted or stolen. Google Cloud also offers customer-managed encryption keys, which allow organizations to have full control over their encryption keys.
Google Cloud Compliance Framework
Google Cloud offers a robust compliance framework that includes various certifications and standards to help businesses and organizations meet regulatory requirements. Here are some of the key certifications and standards included in the Google Cloud compliance framework:
SOC 1, SOC 2, and SOC 3
SOC 1, SOC 2, and SOC 3 are reports that assess the controls relevant to security, availability, and confidentiality of a service organization’s system. Google Cloud has received SOC 1, SOC 2, and SOC 3 reports, which demonstrate its commitment to security, availability, and confidentiality.
ISO 27001
ISO 27001 is an international standard that outlines the requirements for establishing, implementing, maintaining, and continually improving an information security management system (ISMS). Google Cloud has received ISO 27001 certification, which demonstrates its commitment to information security management.
HIPAA
HIPAA is a US law that establishes national standards to protect individuals’ medical records and personal health information. Google Cloud has signed a Business Associate Agreement (BAA) with its customers, which demonstrates its commitment to HIPAA compliance.
PCI DSS
PCI DSS is a set of security standards designed to ensure that all companies that accept, process, store, or transmit credit card information maintain a secure environment. Google Cloud has received PCI DSS certification, which demonstrates its commitment to payment card data security.
GDPR
GDPR is a regulation that requires businesses to protect the personal data and privacy of EU citizens. Google Cloud has implemented various features and tools to help businesses comply with GDPR, such as data processing agreements, data protection impact assessments, and data subject requests.
How to Implement Google Cloud Security and Compliance
Implementing Google Cloud security and compliance can seem like a daunting task, but with the right approach, it can be done efficiently and effectively. Here are some steps to help you get started:
Enable Multi-Factor Authentication
Multi-factor authentication (MFA) adds an extra layer of security to user accounts by requiring a second form of authentication in addition to a password. Google Cloud offers MFA for user accounts, which can help prevent unauthorized access to your data and resources.
Set Up Access Controls
Access controls allow you to specify who can access your data and resources and what actions they can perform. Google Cloud offers various access control mechanisms, such as Identity and Access Management (IAM) and Access Context Manager, which can help you manage access to your resources.
Monitor Activity Logs
Monitoring activity logs can help you detect and respond to security threats and compliance violations. Google Cloud offers various logging and monitoring tools, such as Cloud Audit Logs and Cloud Logging, which can help you track user activity and detect anomalies.
Implement Encryption
Encryption can help protect your data from unauthorized access, even if it is intercepted or stolen. Google Cloud offers encryption at rest and in transit for data and resources. You can also use customer-managed encryption keys to have full control over your encryption keys.
Regularly Review and Update Your Security Policies
Regularly reviewing and updating your security policies can help you stay up-to-date with the latest threats and compliance requirements. Make sure to review your access controls, activity logs, and encryption policies regularly and update them as needed.
Real-World Examples of Google Cloud Security and Compliance
Many businesses and organizations have successfully implemented Google Cloud security and compliance, experiencing numerous benefits such as improved data protection, reduced costs, and increased efficiency. Here are some real-world examples:
Example 1: Financial Services Company
A financial services company used Google Cloud to migrate its sensitive data and applications to the cloud. By implementing Identity and Access Management (IAM) and encryption, the company was able to ensure that only authorized personnel could access its data. Additionally, the company used Cloud Audit Logs to monitor user activity and detect any potential security threats.
Example 2: Healthcare Provider
A healthcare provider used Google Cloud to store and process electronic health records (EHRs) for its patients. By implementing HIPAA compliance and access controls, the provider was able to ensure that patient data was protected and only accessible to authorized personnel. Additionally, the provider used Data Loss Prevention (DLP) to prevent any accidental or intentional disclosure of sensitive patient information.
Example 3: Retail Company
A retail company used Google Cloud to store and process customer data and transactions. By implementing multi-factor authentication and encryption, the company was able to ensure that customer data was protected from unauthorized access. Additionally, the company used Cloud Logging to monitor user activity and detect any potential security threats.
Challenges and Solutions for Google Cloud Security and Compliance
Implementing Google Cloud security and compliance can be a complex process, and businesses and organizations may face several challenges. Here are some common issues and solutions:
Data Breaches
Data breaches can result in significant financial and reputational damage. To prevent data breaches, businesses and organizations should implement encryption, access controls, and multi-factor authentication. Regularly monitoring activity logs can also help detect any potential security threats and respond to them promptly.
Insider Threats
Insider threats can come from current or former employees, contractors, or business partners who have authorized access to data and resources. To mitigate insider threats, businesses and organizations should implement access controls, monitor user activity, and provide regular security training to employees.
Regulatory Changes
Regulatory requirements for data protection and privacy are constantly evolving. To stay up-to-date with regulatory changes, businesses and organizations should regularly review and update their security policies and procedures. Google Cloud offers several compliance tools and resources to help businesses and organizations meet regulatory requirements.
Future Trends in Google Cloud Security and Compliance
Google Cloud security and compliance are constantly evolving to meet the changing needs of businesses and organizations. Here are some future trends to watch:
Artificial Intelligence (AI) and Machine Learning (ML)
AI and ML can help improve data protection and regulatory compliance by automatically detecting and responding to security threats. Google Cloud offers several AI and ML tools and services, such as Cloud AI and Cloud ML Engine, that can help businesses and organizations enhance their security and compliance posture.
Blockchain
Blockchain technology can help improve data integrity and transparency, making it an ideal solution for regulatory compliance. Google Cloud offers several blockchain services, such as Cloud Blockchain and Cloud Identity-Aware Proxy, that can help businesses and organizations leverage blockchain technology for security and compliance purposes.
Zero Trust Security Model
The zero trust security model assumes that any user or system could potentially be compromised, and therefore, verifies every request as though it originates from an open network. Google Cloud offers several zero trust security solutions, such as BeyondCorp and Cloud Identity, that can help businesses and organizations enhance their security and compliance posture.
Conclusion: The Importance of Google Cloud Security and Compliance
Google Cloud security and compliance are critical for businesses and organizations that want to leverage the benefits of cloud computing while protecting their data and meeting regulatory requirements. By understanding the key components of Google Cloud security, such as Identity and Access Management (IAM), Security Key Enforcement, and Data Loss Prevention (DLP), and implementing the Google Cloud compliance framework, which includes various certifications and standards such as SOC 1, SOC 2, ISO 27001, and HIPAA, businesses and organizations can ensure their data is protected and compliant.
Implementing Google Cloud security and compliance best practices can help businesses and organizations prevent data breaches, detect insider threats, and stay up-to-date with regulatory changes. By following a step-by-step guide, such as enabling multi-factor authentication, setting up access controls, and monitoring activity logs, businesses and organizations can enhance their security and compliance posture.
Real-world examples of businesses and organizations that have successfully implemented Google Cloud security and compliance demonstrate the benefits of improved data protection, reduced costs, and increased efficiency. By staying up-to-date with future trends in Google Cloud security and compliance, such as artificial intelligence, machine learning, and blockchain, businesses and organizations can continue to enhance their security and compliance posture and stay ahead of potential threats.
In conclusion, Google Cloud security and compliance are essential for businesses and organizations that want to leverage the benefits of cloud computing while protecting their data and meeting regulatory requirements. By implementing best practices, staying up-to-date with future trends, and following a step-by-step guide, businesses and organizations can ensure their data is secure and compliant, providing peace of mind and enabling them to focus on their core operations.