Understanding Google Cloud Identities and Access Management
Google Cloud Platform (GCP) employs a robust Identity and Access Management (IAM) system to control who (identities) has access to what resources. These identities can be categorized into users, service accounts, and groups. Users represent individual people with direct access to the platform. Google Cloud groups allow the management of permissions for multiple users collectively. However, a core element in secure resource access is the google cloud platform service account, which provides a non-human identity for applications, workloads, or automated processes. These service accounts, unlike user accounts, do not represent specific individuals; instead, they act as an automated identity for accessing and manipulating resources in GCP. Central to granting any access is the concept of permissions, determining what actions an identity can perform on a given resource. This is governed by roles, collections of permissions that are attached to identities, which are defined following the principle of least privilege, ensuring that each identity has only the necessary permissions to carry out its specific function. It is of high importance to avoid granting excessive access, mitigating potential risks and security breaches within the cloud environment.
The principle of least privilege is of paramount importance when dealing with any identity, but particularly when using a google cloud platform service account. The focus must remain on granting only the required roles and permissions needed for the specific task or operation, minimizing the attack surface and potential damage from compromised credentials. This concept is fundamental to secure cloud resource access, preventing unauthorized actions and limiting the scope of any potential security incident. Furthermore, it ensures that applications and services only have access to the resources they genuinely need to function correctly, reducing the risk of data exposure and preventing escalation of privileges. Service accounts represent an indispensable part of any well-architected Google Cloud solution, providing automated entities with the capability to interact with the platform while maintaining strong security boundaries, which enables more efficient automation and application access control within the cloud.
As we delve deeper into the practicalities of GCP, it will be clear that service accounts are not just a best practice, but an essential aspect of establishing a secure and well-governed cloud environment. They provide the necessary automation needed for modern cloud applications while adhering to strict security controls. Moving forward, the discussion on service account management, including creation, security practices, use cases and advanced techniques, will build on this foundational understanding of identities and access management. Understanding the importance of the principle of least privilege and the role of the google cloud platform service account will set the stage for building secure, scalable and robust solutions.
What are GCP Service Accounts: A Detailed Breakdown
A Google Cloud Platform service account represents a special type of Google account that is designed for non-human users, such as applications, virtual machines, or other services that need to access Google Cloud resources. Unlike user accounts that are tied to individual people, Google Cloud Platform service accounts are designed for use by workloads, thus avoiding the need for human intervention to grant permissions and authenticate. They are particularly beneficial in scenarios requiring server-to-server communication, where applications running in a virtual machine need to interact with a database or when automation scripts need to access cloud storage. Using a Google Cloud Platform service account ensures that applications and automated processes can access cloud resources securely, without embedding and risking exposure of human credentials. This helps to provide a solid security approach that is both robust and manageable. The value of Google Cloud Platform service accounts lies in their ability to grant and control access to resources by using a least privilege approach, which enhances the overall security posture of the cloud deployment.
The purpose of a Google Cloud Platform service account is to provide a secure identity for applications and services, enabling them to programmatically interact with Google Cloud Platform. A Google Cloud Platform service account is not associated with a specific human user, which means the authentication is done by keys or certificates, enhancing security by removing the need for human-managed credentials. For example, a continuous integration/continuous deployment (CI/CD) pipeline can use a Google Cloud Platform service account to deploy application updates without requiring a person to enter credentials every time. Similarly, an application running on a Compute Engine virtual machine can use a Google Cloud Platform service account to access data from a Cloud Storage bucket, enhancing efficiency and safety. Using Google Cloud Platform service accounts in these scenarios is beneficial, because they are designed to minimize the risk of credential exposure, improving overall security. Service accounts are used widely for server-to-server authentication, automation processes, and CI/CD pipelines, providing a dependable way to manage access to your Google Cloud Platform environment.
Key Differences Between User Accounts and Google Cloud Service Principals
Understanding the distinctions between user accounts and Google Cloud Platform service accounts is crucial for maintaining robust security and enabling efficient automation within Google Cloud. User accounts represent individual human users, each with their unique login credentials. These credentials typically consist of an email address and a password, and sometimes involve multi-factor authentication for enhanced security. User accounts are primarily designed for interactive access to Google Cloud resources through the Google Cloud Console, command-line interfaces, or APIs. Conversely, a Google Cloud Platform service account is a non-human identity specifically designed for applications, services, and automated processes to access Google Cloud resources. Service accounts lack traditional login credentials; instead, they authenticate using private keys, which are often managed and rotated for enhanced security. This fundamental difference in authentication mechanisms has significant implications for how these two types of identities are employed within Google Cloud. Using a service account for application access avoids sharing user credentials, reducing the risk of credential compromise and unauthorized access.
The authentication methods for user accounts and Google Cloud Platform service accounts also differ significantly. User accounts rely on user-managed credentials, such as passwords or federated identities. These credentials can be compromised through phishing attacks or weak password practices. In contrast, Google Cloud service accounts utilize private key files or workload identity federation. These authentication methods are designed for automation and minimize the need for human interaction. The use of service accounts allows applications to authenticate programmatically without requiring direct user intervention. This distinction is paramount when considering best practices for automation and security. In addition, while user accounts might be granted broad permissions that cover their entire scope of work, service accounts can be granted granular permissions, ensuring the principle of least privilege is maintained. This approach limits the potential damage from a compromised service account because it would only be able to access the specific resources necessary for its designated purpose. By using IAM service accounts you avoid long-lived credentials on applications that could lead to security breaches.
The implications for security and automation are profound when we consider the differences between user and Google Cloud Platform service accounts. Sharing user credentials among applications or embedding them within code is a high-risk practice that should be avoided at all costs. It creates significant vulnerabilities and makes it challenging to track and manage access. Instead, Google Cloud Platform service accounts offer a safer and more manageable approach, where access is granted through dedicated credentials that can be easily rotated and audited. For this reason, using service accounts instead of user accounts for application access ensures a more secure and scalable environment that will avoid the common security risks present when using human accounts for non-human workloads. Employing service accounts aligns with the principle of least privilege, ensuring only the necessary permissions are granted for a specific application’s needs. By doing this, you improve overall security posture and streamline access management practices.
How to Create and Manage a Google Cloud Service Account
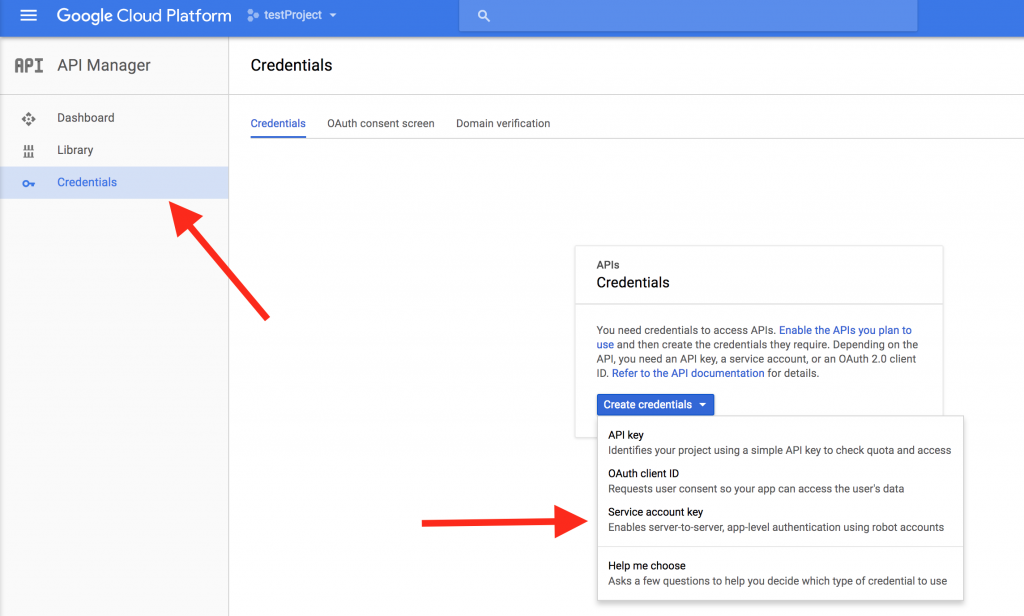
Creating a new google cloud platform service account is a straightforward process achievable through several methods, each catering to different user preferences and technical environments. The Google Cloud Console provides a user-friendly graphical interface, ideal for those who prefer visual interaction. To begin, navigate to the IAM & Admin section within the console, select ‘Service Accounts,’ and then click on ‘Create Service Account’. You will be prompted to provide a name and optional description for the google cloud platform service account, which helps in identifying its purpose later on. Once created, the service account will be assigned a unique email address. Permissions are then granted by assigning predefined or custom roles. The gcloud CLI offers a command-line alternative for developers who prefer scripting and automation. The command `gcloud iam service-accounts create` allows the creation of service accounts, setting the display name, and optional descriptions via command arguments. This method is particularly useful for integrating service account creation into deployment pipelines and automation scripts. Finally, the Google Cloud API enables programmatic creation and management of google cloud platform service accounts via HTTP requests. This is advantageous for complex infrastructures where automation and integration are critical.
Managing a google cloud platform service account securely is crucial. Permissions granted to a service account define which resources it can access and modify. It’s vital to adhere to the principle of least privilege, assigning only the minimum required roles to the service account. This approach limits potential damage in case of compromised credentials. After creating the service account, you can manage its keys. Service account keys are credentials used to authenticate as the service account, and they come in two types: JSON and P12 files. Downloading and storing service account keys securely is paramount. These keys should be treated with the same care as any other sensitive credentials. Key rotation is also vital, and it is considered best practice to create new keys periodically and disable or delete older keys after a short grace period. This reduces the risk associated with compromised keys. The google cloud console, gcloud CLI, and API all provide ways to rotate keys, add new ones, and disable them. Key rotation can also be automated through scripts to enhance security further. For sensitive environments, it’s preferable to use workload identity federation instead of service account keys whenever possible, as this eliminates the risks associated with long-lived credentials.
Best Practices for Securing Your GCP Service Accounts
Securing Google Cloud Platform service account is paramount to maintaining the integrity and confidentiality of your cloud resources. Improperly managed service accounts can introduce significant security vulnerabilities. One crucial practice is to adhere strictly to the principle of least privilege. This entails granting only the necessary roles and permissions required for a service account to perform its designated task. Avoid assigning broad, encompassing roles like ‘Owner’ whenever possible. Instead, meticulously select specific, granular roles that precisely match the service account’s operational requirements. This proactive approach minimizes the potential damage from a compromised service account. Another vital security measure involves diligent key management. Service account keys should be treated as highly sensitive information, akin to privileged user credentials. Securely store these keys, avoiding their direct embedding within application code or storage in public locations. Implementing key rotation policies is an essential practice, periodically generating new keys while invalidating the old ones, which limits the window of opportunity for malicious access. Comprehensive auditing of service account usage is equally important. Monitor all activities associated with service accounts to rapidly identify and respond to any suspicious behavior. This includes scrutinizing which resources a service account accesses and any modifications it makes. Enable detailed logging and alerts to detect unusual access patterns promptly. Regular audits of permissions help ensure that no service account has excessive or obsolete privileges.
Disabling unused Google Cloud Platform service account is a vital step in maintaining robust security posture. Idle accounts present unnecessary attack surfaces and should be deactivated when they are no longer needed to reduce the risk of compromised access. For external workloads that need to access Google Cloud resources, consider using workload identity federation. This innovative technique avoids the need to manage and store long-lived service account keys outside of the Google Cloud Platform environment, significantly boosting security. Workload identity federation allows applications running outside of Google Cloud, such as in your own data centers or other cloud providers, to access Google Cloud resources using short lived tokens. By utilizing it, you significantly minimize the risk associated with exposing or mishandling service account keys. This sophisticated approach enhances overall security by reducing the reliance on static credentials. Employing these best practices forms the foundation of a secure and resilient Google Cloud Platform environment. By actively managing service accounts with these practices, organizations can confidently deploy their applications and services while significantly reducing security risks.
In summary, effective security for google cloud platform service account involves a multi-faceted approach: least privilege, meticulous key management, regular auditing, timely disabling of unused accounts, and leveraging advanced solutions like workload identity federation. These measures minimize potential risks, ensure secure access to Google Cloud resources, and contribute to an overall stronger security framework. By implementing these best practices, organizations can operate with confidence and safeguard their cloud infrastructure.
Exploring Google Cloud Service Account Use Cases and Examples
Google Cloud Platform service accounts are instrumental in securing access to various Google Cloud resources, offering a robust solution for application-to-resource interactions. Consider, for instance, a scenario where a data analytics application needs to access data stored in Cloud Storage. Instead of using a user’s credentials, a dedicated Google Cloud Platform service account is created and granted the necessary permissions, such as the “Storage Object Viewer” role. This ensures the application only has the minimal access needed to read the required data, adhering to the principle of least privilege. Similarly, when a virtual machine running on Compute Engine requires access to a BigQuery dataset for processing, the virtual machine can be configured to use a specific Google Cloud Platform service account with the “BigQuery Data Viewer” role, allowing the machine to perform its task without granting excessive permissions. This precise control over resource access is a cornerstone of secure cloud operations. Another practical example involves a CI/CD pipeline deploying a web application. The pipeline can use a Google Cloud Platform service account with the “Cloud Build Editor” role to deploy code to App Engine or Cloud Run, ensuring only the deployment process has the ability to make changes to the deployed code. This is a safer way to manage deployments, rather than using developer credentials in automated pipelines. These examples showcase how service accounts help to build safe software.
The principle of least privilege is not just a theoretical recommendation; it’s a fundamental aspect of secure Google Cloud Platform service account management. Imagine a microservice-based architecture; each service can utilize a different Google Cloud Platform service account tailored to its specific needs. For instance, a payment processing service may require access to a database and a messaging queue while a user management service only needs access to user data storage. Granting each service only the essential permissions significantly reduces the potential impact of a security breach. If one service account is compromised, the attacker’s access is limited to the resources that account has permission to interact with, not the entire project. Another use case is creating a Google Cloud Platform service account for an application to publish messages to a Pub/Sub topic. The principle of least privilege dictates that the service account should have only the “Pub/Sub Publisher” role for that specific topic, and not broader permissions like the “Pub/Sub Admin” role. These granular permissions provide a strong layer of security, reducing the risk of unauthorized actions.
Real-world examples of Google Cloud Platform service account implementation extend to automation scripts and serverless functions as well. For example, a scheduled function that backs up Cloud SQL database data to Cloud Storage can use a dedicated Google Cloud Platform service account with “Cloud SQL Client” and “Storage Object Admin” roles only. This design prevents accidental deletion of the backup objects by other services or users. Another case is using service accounts to manage access to secrets managed in Secret Manager, giving only certain applications access to retrieve specific secrets. This avoids embedding credentials in code, which is a security risk. By implementing granular permissions and rotating keys regularly as needed, organizations achieve a more robust security posture, and Google Cloud Platform service accounts are the key element for implementing such policies. The careful use of service accounts, especially when combined with the principle of least privilege, makes a large difference in maintaining secure and well-managed cloud environments.
Troubleshooting Common Issues with Google Cloud Service Accounts
Encountering issues with Google Cloud Platform service accounts can be frustrating, but understanding common problems and their solutions is key to maintaining smooth operations. Authentication failures are a frequent hurdle, often stemming from incorrect service account key files or improper configuration of the environment variables required for authentication. When an application fails to authenticate, the first step should be verifying the service account key file path and ensuring that the `GOOGLE_APPLICATION_CREDENTIALS` environment variable is correctly set. Permission errors, another typical problem, arise when a service account lacks the necessary IAM roles to perform a specific action. To address this, it’s essential to review the granted roles against the required permissions needed for the task at hand. Utilizing the principle of least privilege, make sure to grant only the necessary roles and avoid over-permissioning. A detailed inspection of the error messages provided by the Google Cloud Platform API or logs is the recommended approach to identify the specific permission deficiencies. The Google Cloud Platform service account might also have key management mishaps, which are mainly related to key expirations, incorrect rotations, or unauthorized exposures. Always ensure that keys are properly rotated and that access to service account keys is strictly controlled and managed with secure storage practices.
Further troubleshooting of Google Cloud Platform service account issues involves leveraging the Google Cloud Platform audit logs. Audit logs provide valuable insights into the operations performed by service accounts, including any attempts to access resources and whether those attempts were successful or not. When facing permission errors, checking the audit logs can pinpoint exactly which permission was missing and which Google Cloud Platform service account was used to execute the action. This helps in addressing permission related issues to ensure the principle of least privilege is followed. Examining logs around authentication failures can also show what type of authentication was attempted and how it failed. This helps differentiate between key issues and environment variables misconfiguration. It is also useful to determine whether the service account is even being used as expected. Another common issue arises from incorrect configurations, especially when the service account is being used in different environments, like a local development environment and a production environment. Ensuring the configurations for each environment are correctly implemented and tested should be part of the best practices.
The efficient usage of Google Cloud Platform service account requires a strong focus on error analysis. When encountering errors, carefully review the full error message, which often includes specific details about the issue and potential fixes. These error messages, often cryptic, can provide the precise reason for a failure such as a missing scope for a specific Google Cloud API. For example, if you receive an error message about missing permission “storage.objects.get”, you will know exactly that the service account lacks access to retrieve objects in Google Cloud Storage. When you need help in troubleshooting, always begin with the error message and work your way back to the configuration and permission details. This step-by-step approach allows for a more organized and effective diagnosis of problems, minimizing downtime and improving the overall reliability of applications utilizing the Google Cloud Platform service account. By combining careful log analysis, error message interpretation and a solid understanding of Google Cloud Platform, most of the problems can be quickly diagnosed and resolved.
Advanced Techniques for Google Cloud Service Principal Management
Managing Google Cloud Platform service accounts effectively requires a move beyond basic creation and permission assignment, especially when dealing with complex environments. One such advanced technique is the implementation of Workload Identity Federation, designed to facilitate secure access to Google Cloud Platform resources from external environments without the need for long-lived service account keys. This is particularly useful for applications running in other cloud providers or on-premises, which need to interact with Google Cloud services. Workload Identity Federation allows your external workloads to assume the identity of a Google Cloud Platform service account using short-lived tokens, mitigating the risks associated with managing and distributing service account keys. By configuring a trust relationship between your identity provider and Google Cloud Platform, you achieve a more secure and manageable approach for cross-environment resource access. This avoids hardcoding or embedding credentials, enhances your overall security posture and reduces the risk of credential leaks or unauthorized access. The proper configuration of Workload Identity Federation needs a clear strategy to make sure proper access with the least privilege principle in mind. This method provides a very strong solution when dealing with services outside of the Google Cloud Platform.
Furthermore, consider the management of Google Cloud Platform service accounts across multiple projects within an organization. A centralized approach to service account governance is crucial for maintaining consistency and control. Employing resource hierarchy best practices allows for the logical grouping of projects and facilitates the efficient assignment of permissions. This includes understanding how to delegate service account management to specific teams or users through IAM roles, ensuring that only authorized individuals can create or modify service accounts. Moreover, when managing a large number of google cloud platform service accounts, it is essential to establish a consistent naming convention and labeling system to aid in the identification, governance, and auditing of these resources. Using organizational policies to enforce naming standards and required labels helps prevent the proliferation of service accounts that are difficult to track. You can also establish processes for periodic reviews of service accounts to ensure they are being used correctly, including monitoring their activities and removing or disabling unused ones. This combination of policy and periodic review contributes to robust governance and scalability when using google cloud platform service account. Adopting a well planned strategy for service account management will increase the security and scalability of your infrastructure.