Preparing Your Environment for Force Sync AD Connect
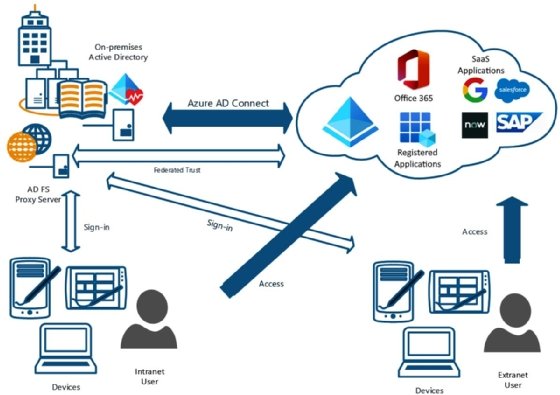
Before implementing force sync AD Connect, it is crucial to ensure that your on-premises Active Directory (AD) and Azure Active Directory (Azure AD) environments are properly configured. This section will cover the necessary prerequisites, such as configuring single sign-on, setting up directory synchronization, and managing user and group permissions.
First, enable single sign-on (SSO) between your on-premises AD and Azure AD. SSO simplifies the authentication process by allowing users to access both environments using the same set of credentials. This step is essential for maintaining a seamless user experience and ensuring secure access control.
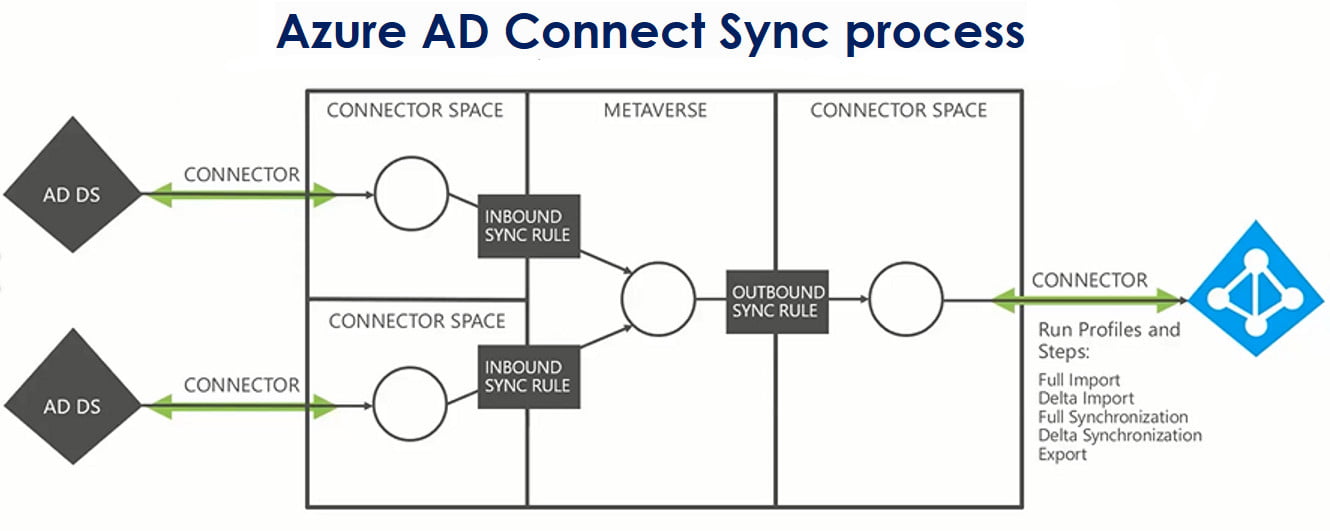
Next, configure directory synchronization between your on-premises AD and Azure AD. Directory synchronization ensures that user and group information is consistently replicated between the two environments. This process is critical for maintaining accurate user identities and access management across both platforms.
Proper user and group management is also a key aspect of preparing for force sync AD Connect. Ensure that user and group permissions are up-to-date and reflect the current needs of your organization. Regularly review and update these permissions to maintain a secure and efficient access management system.
By following these prerequisites, you will create a solid foundation for your force sync AD Connect process. Proper preparation will help minimize potential issues and ensure a smooth synchronization experience between your on-premises AD and Azure AD.
https://www.youtube.com/watch?v=30RKasgJ3EE
How to Perform a Force Sync AD Connect: Step-by-Step Instructions
Force sync AD Connect is a powerful tool that ensures the synchronization of on-premises Active Directory (AD) with Azure Active Directory (Azure AD). To successfully force sync AD Connect, follow these step-by-step instructions:
-
Access the Azure AD Connect tool: Begin by downloading and installing the Azure AD Connect tool on a designated server in your on-premises environment. Launch the application to access the main dashboard.
-
Connect to Azure AD: From the Azure AD Connect main dashboard, click on the “Connect to Azure AD” button. Enter your Azure AD global administrator credentials to establish a connection.
-
Connect to on-premises AD: Next, click on the “Connect your directories” button. Enter the necessary credentials to connect to your on-premises AD environment. Ensure that the correct domain and forests are selected.
-
Configure synchronization options: Choose the synchronization options that best suit your organization’s needs. You can select from password hash synchronization, pass-through authentication, or federation. For force sync AD Connect, choose the “Password hash synchronization” option.
-
Initiate the force sync AD Connect process: To force sync AD Connect, navigate to the “Synchronization Options” page and select the “Initial” option. This action will initiate a full synchronization cycle between your on-premises AD and Azure AD environments.
-
Monitor the force sync AD Connect process: After initiating the force sync AD Connect process, monitor its progress through the Azure AD Connect dashboard. You can also use native Azure and AD monitoring tools to track the synchronization process in real-time.
-
Verify successful synchronization: Once the force sync AD Connect process is complete, verify that the user identities and access management settings have been accurately synchronized between your on-premises AD and Azure AD environments.
By following these step-by-step instructions, you can successfully force sync AD Connect and maintain consistency and accuracy in user identities and access management across both environments.
Troubleshooting Common Force Sync AD Connect Issues
Despite proper preparation, you may still encounter issues when force syncing AD Connect. This section will address common problems and provide troubleshooting tips and best practices to help you resolve them.
Synchronization Errors
Synchronization errors can occur due to various reasons, such as misconfigured attributes, duplicate entries, or connectivity issues. To troubleshoot synchronization errors, first, ensure that the correct attributes are being synchronized. You can use the Azure AD Connect tool’s “Attribute Editor” to review and modify attribute mappings as needed.
Additionally, check for duplicate entries, which can cause synchronization conflicts. Use the “Object Exporter” tool to identify and remove duplicate objects from your on-premises AD environment before attempting another force sync.
Authentication Issues
Authentication issues can arise when user credentials are not correctly synchronized between your on-premises AD and Azure AD environments. To resolve authentication issues, verify that password hash synchronization is properly configured and functioning. You can also use the “Password Hash Synchronization” troubleshooting guide provided by Microsoft to diagnose and fix common password hash synchronization problems.
Data Discrepancies
Data discrepancies can occur when user or group information is not accurately replicated between your on-premises AD and Azure AD environments. To address data discrepancies, ensure that the correct user and group objects are being synchronized. You can use the “Object Filtering” feature in the Azure AD Connect tool to specify which objects should be included in the synchronization process.
Additionally, review the “DirSync” logs to identify any objects that are causing data discrepancies. You can use the “Microsoft Online Services Directory Synchronization” tool to analyze and resolve these issues.
By following these troubleshooting tips and best practices, you can effectively resolve common force sync AD Connect issues and maintain a consistent and accurate user identity and access management system across both your on-premises AD and Azure AD environments.
Monitoring and Maintaining Your Force Sync AD Connect Process
To ensure the long-term success of your force sync AD Connect process, it’s essential to monitor and maintain your environments. This section will cover the available monitoring tools, best practices for ongoing maintenance, and strategies for addressing potential issues before they become problems.
Monitoring Tools
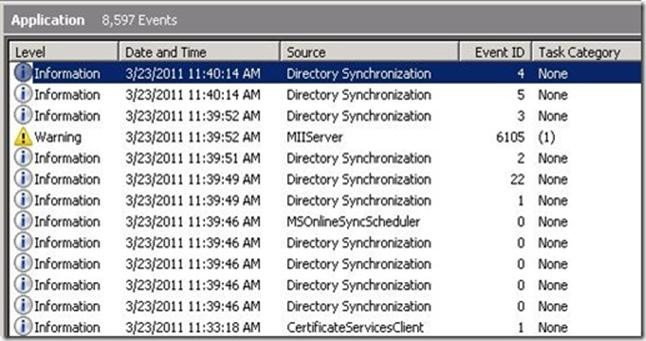
Microsoft provides several monitoring tools to help you track the health and performance of your force sync AD Connect process:
- Azure AD Connect Health: A cloud-based service that monitors your Azure AD Connect synchronization service, providing insights into synchronization performance, errors, and overall health.
- Event Viewer: A built-in Windows tool that logs events related to the Azure AD Connect synchronization process, allowing you to identify and troubleshoot issues.
- Performance Monitor: A built-in Windows tool that tracks performance metrics related to the Azure AD Connect synchronization process, helping you identify bottlenecks and optimize performance.
Best Practices for Ongoing Maintenance
To maintain a healthy force sync AD Connect process, follow these best practices:
- Schedule regular synchronizations to ensure data consistency between your on-premises AD and Azure AD environments.
- Review synchronization logs and performance metrics regularly to identify and address potential issues before they become problems.
- Keep the Azure AD Connect tool and related components up-to-date with the latest patches and updates to ensure optimal performance and security.
- Monitor and manage user and group permissions to maintain a secure and efficient access management system.
Strategies for Addressing Potential Issues
To proactively address potential issues, consider the following strategies:
- Implement a disaster recovery plan to ensure business continuity in the event of a synchronization failure or other unexpected issues.
- Establish a change management process to control and document changes to your on-premises AD and Azure AD environments, minimizing the risk of synchronization conflicts and errors.
- Regularly review and update your force sync AD Connect implementation strategy to take advantage of new features, best practices, and industry insights.
By following these monitoring and maintenance best practices, you can ensure a smooth and successful force sync AD Connect process, maintaining consistency and accuracy in user identities and access management across both your on-premises AD and Azure AD environments.
Comparing Force Sync AD Connect with Other Synchronization Methods
While force sync AD Connect is a powerful tool, it’s not the only synchronization method available. Understanding the differences between force sync AD Connect and other synchronization methods, such as password hash synchronization, pass-through authentication, and federation, can help you determine the best approach for your organization.
Password Hash Synchronization
Password hash synchronization is a simple and straightforward synchronization method that replicates password hashes from on-premises AD to Azure AD. This method enables users to sign in using the same password in both environments, without the need for complex synchronization configurations. However, it does not support advanced features like smart card authentication or multi-factor authentication (MFA) without additional configuration.
Pass-through Authentication
Pass-through authentication is a secure and efficient synchronization method that allows users to sign in directly to Azure AD using their on-premises AD credentials. This method does not store password hashes in Azure AD, improving security and reducing the risk of data breaches. However, it does not support advanced features like smart card authentication or MFA without additional configuration.
Federation
Federation is a synchronization method that enables users to sign in to Azure AD using their on-premises AD credentials, managed by an on-premises federation server. This method supports advanced features like smart card authentication and MFA, but requires more complex configurations and maintenance. Federation is recommended for organizations that require advanced authentication and authorization features, or have specific compliance or regulatory requirements.
Choosing the Right Synchronization Method
When choosing the right synchronization method for your organization, consider the following factors:
- Complexity: Evaluate the complexity of each synchronization method and determine which one aligns best with your organization’s technical capabilities and resources.
- Security: Consider the security requirements of each synchronization method and choose the one that provides the best balance between security and functionality.
- Advanced Features: Determine which advanced features, if any, are required for your organization, and choose a synchronization method that supports those features.
- Cost: Evaluate the cost of each synchronization method, including licensing, hardware, and maintenance costs, and choose the one that provides the best value for your organization.
By carefully evaluating each synchronization method, you can choose the one that best meets the needs of your organization and ensure a successful implementation of force sync AD Connect or another synchronization method.
Real-World Case Studies: Successful Force Sync AD Connect Implementations
Understanding how other organizations have successfully implemented force sync AD Connect can provide valuable insights and best practices for your own implementation strategy. This section will explore real-world examples of organizations that have successfully implemented force sync AD Connect, highlighting their experiences, challenges, and best practices.
Case Study 1: Global Manufacturing Company
A global manufacturing company with over 100,000 employees needed to synchronize their on-premises AD with Azure AD to enable seamless access to cloud-based applications for their employees. By implementing force sync AD Connect, the company was able to ensure consistent and accurate user identities and access management across both environments. The company also implemented multi-factor authentication (MFA) and conditional access policies to enhance security and reduce the risk of data breaches.
Case Study 2: Healthcare Provider
A healthcare provider with multiple hospitals and clinics needed to synchronize their on-premises AD with Azure AD to enable secure access to electronic health records (EHRs) for their healthcare professionals. By implementing force sync AD Connect, the healthcare provider was able to ensure consistent and accurate user identities and access management across both environments. The company also implemented role-based access control (RBAC) and audit logging to meet regulatory compliance requirements and enhance security.
Case Study 3: Financial Services Firm
A financial services firm with over 5,000 employees needed to synchronize their on-premises AD with Azure AD to enable secure access to financial applications and data for their employees. By implementing force sync AD Connect, the company was able to ensure consistent and accurate user identities and access management across both environments. The company also implemented data loss prevention (DLP) policies and encryption to protect sensitive financial data and meet regulatory compliance requirements.
Best Practices from Real-World Implementations
Based on these real-world examples, here are some best practices to consider when implementing force sync AD Connect:
- Plan carefully: Develop a detailed implementation plan that includes clear objectives, timelines, and resource requirements.
- Test thoroughly: Test the implementation in a controlled environment before deploying it to production.
- Monitor continuously: Use monitoring tools to track the health and performance of your force sync AD Connect process and address potential issues before they become problems.
- Maintain regularly: Implement a regular maintenance schedule to ensure the ongoing success of your force sync AD Connect process.
- Secure proactively: Implement security measures, such as MFA, RBAC, and encryption, to protect sensitive data and meet regulatory compliance requirements.
By following these best practices, you can ensure a successful implementation of force sync AD Connect and maintain consistent and accurate user identities and access management across both your on-premises AD and Azure AD environments.
Future Trends in Active Directory and Azure AD Synchronization
Staying up-to-date with the latest trends and developments in Active Directory and Azure AD synchronization is essential for ensuring the long-term success of your force sync AD Connect process. In this section, we’ll cover emerging technologies, best practices, and industry insights to help you plan for the future.
Emerging Technologies
One emerging technology in the realm of Active Directory and Azure AD synchronization is the use of artificial intelligence (AI) and machine learning (ML) to automate and optimize the synchronization process. By leveraging AI and ML algorithms, organizations can automatically detect and resolve synchronization errors, optimize data flow, and improve overall synchronization performance.
Best Practices
As the Active Directory and Azure AD synchronization landscape continues to evolve, it’s essential to stay up-to-date with best practices for implementing and maintaining your force sync AD Connect process. Some best practices to consider include:
- Implementing a regular maintenance schedule to ensure the ongoing success of your force sync AD Connect process.
- Using monitoring tools to track the health and performance of your force sync AD Connect process and address potential issues before they become problems.
- Implementing security measures, such as multi-factor authentication (MFA), role-based access control (RBAC), and encryption, to protect sensitive data and meet regulatory compliance requirements.
- Staying up-to-date with the latest Azure AD Connect updates and features to ensure optimal performance and security.
Industry Insights
According to a recent survey by Gartner, the use of cloud-based identity and access management (IAM) solutions is expected to grow by over 50% in the next two years. As more organizations move their applications and data to the cloud, the need for effective and efficient Active Directory and Azure AD synchronization will become increasingly important. By staying up-to-date with industry insights and trends, you can ensure that your force sync AD Connect process is aligned with the needs of your organization and the broader market.
In conclusion, staying ahead of the curve in Active Directory and Azure AD synchronization is essential for ensuring the long-term success of your force sync AD Connect process. By understanding emerging technologies, best practices, and industry insights, you can plan for the future and ensure that your organization is well-positioned to meet the evolving needs of the market.
Conclusion: Making the Most of Force Sync AD Connect in Your Organization
Throughout this comprehensive guide, we’ve covered everything you need to know about force sync AD Connect, from understanding what it is and why it matters to best practices for monitoring and maintaining your force sync AD Connect process. By following the step-by-step instructions for implementing force sync AD Connect, you can ensure consistent and accurate user identities and access management across both your on-premises AD and Azure AD environments.
When it comes to choosing the right synchronization method for your organization, it’s important to consider your unique needs and requirements. While force sync AD Connect is a powerful tool, it may not be the best approach for every organization. By comparing force sync AD Connect with other synchronization methods, such as password hash synchronization, pass-through authentication, and federation, you can determine the best approach for your organization.
Real-world case studies can provide valuable insights and best practices for implementing force sync AD Connect. By learning from the experiences, challenges, and successes of other organizations, you can inform your own implementation strategy and avoid common pitfalls.
Staying up-to-date with the latest trends and developments in Active Directory and Azure AD synchronization is essential for ensuring the long-term success of your force sync AD Connect process. By understanding emerging technologies, best practices, and industry insights, you can plan for the future and ensure that your organization is well-positioned to meet the evolving needs of the market.
In summary, implementing force sync AD Connect requires careful preparation, execution, and ongoing maintenance. By following the best practices and strategies outlined in this guide, you can ensure a successful implementation and maintain consistent and accurate user identities and access management across both your on-premises AD and Azure AD environments.