Understanding Docker Vulnerabilities: An In-Depth Analysis
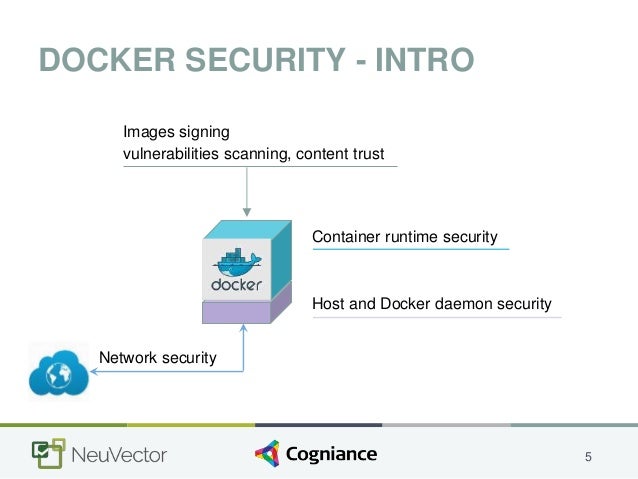
Docker has revolutionized the software development industry by enabling developers to create, deploy, and run applications in containers. This containerization technology offers numerous benefits, such as resource efficiency, portability, and faster deployment. However, like any other software, Docker is susceptible to vulnerabilities that can impact system security. Addressing Docker vulnerabilities is crucial to maintaining a secure and stable environment for application development and deployment.
Common Docker Vulnerabilities and Exploits
Docker vulnerabilities can manifest in various ways, posing significant risks to system security if left unaddressed. Some common Docker vulnerabilities include insecure image configurations, privilege escalation, and network exposures. These vulnerabilities can be exploited by malicious actors, leading to unauthorized access, data breaches, and system disruptions.
Insecure image configurations can lead to Docker vulnerabilities when developers create images with unnecessary or outdated software packages, hardcoded credentials, or unpatched bugs. These image vulnerabilities can provide an entry point for attackers, allowing them to gain unauthorized access to the host system or other containers.
Privilege escalation is another common Docker vulnerability, which occurs when an attacker exploits misconfigured user privileges to gain higher-level access to the system. For instance, if a container runs with root privileges, an attacker who successfully compromises the container can escalate their privileges to control the host system.
Network exposures can also contribute to Docker vulnerabilities, especially when containers are not properly isolated from the host network or from other containers. Improper network configurations can enable attackers to move laterally within the system, access sensitive data, or disrupt services.
Exploiting these Docker vulnerabilities can have severe consequences, ranging from data breaches and financial losses to damaged reputations and legal liabilities. It is essential to proactively address these vulnerabilities to maintain a secure and stable environment for application development and deployment.
How to Mitigate Docker Vulnerabilities: Best Practices and Recommendations
To effectively address Docker vulnerabilities, it is essential to implement best practices and recommendations for securing your Docker environment. These strategies focus on securing image configurations, managing user privileges, and implementing network security measures.
Securing Image Configurations
To mitigate Docker vulnerabilities related to image configurations, follow these best practices:
- Minimize the number of base images used to build your applications.
- Regularly update and patch your base images and other dependencies.
- Remove unnecessary packages, files, and credentials from your images.
- Use multi-stage builds to separate build-time and runtime environments.
- Leverage tools like Docker Content Trust and Notary to ensure the integrity of your images.
Managing User Privileges
To prevent privilege escalation and other Docker vulnerabilities, follow these recommendations:
- Avoid running containers as the root user whenever possible.
- Define and manage user privileges within your containers using user namespaces or user directives in Dockerfiles.
- Regularly review and update your container’s privilege settings.
- Implement least privilege principles for your containers and host system.
Implementing Network Security Measures
To address network exposures and other Docker vulnerabilities, consider these network security measures:
- Isolate containers using Docker’s built-in network features, such as user-defined networks and network policies.
- Limit container-to-container and container-to-host network communication.
- Use firewalls, network segmentation, and access control lists to restrict network access.
- Monitor and analyze network traffic for signs of suspicious activity.
By following these best practices and recommendations, you can significantly reduce the risk of Docker vulnerabilities and maintain a secure environment for your applications.
Real-World Examples of Docker Vulnerabilities and Breaches
Analyzing real-world examples of Docker vulnerabilities and breaches helps emphasize the importance of addressing these issues and encourages a security-focused approach in software development. By understanding the causes and consequences of these incidents, organizations can learn valuable lessons and implement best practices to protect their systems.
Case Study 1: Insecure Image Configurations
In 2019, a popular open-source project was found to have an insecure image configuration, exposing sensitive data and allowing unauthorized access to its containers. The project’s Dockerfile contained hardcoded credentials and unnecessary packages, making it an easy target for attackers. The consequences included data breaches and potential system disruptions, leading to a loss of user trust and reputational damage.
Case Study 2: Privilege Escalation
A well-known container orchestration platform experienced a privilege escalation vulnerability in 2018, which allowed attackers to gain root access to the host system. The vulnerability stemmed from a misconfiguration in the platform’s Docker daemon settings, enabling unauthorized users to execute arbitrary commands with elevated privileges. This incident resulted in unauthorized access to sensitive data and potential system disruptions, highlighting the risks associated with improper privilege management.
Lessons Learned
These real-world examples of Docker vulnerabilities and breaches underscore the importance of addressing Docker security. Key lessons learned include:
- The significance of securing image configurations to prevent data breaches and unauthorized access.
- The need for proper privilege management to prevent privilege escalation and unauthorized access to the host system.
- The potential consequences of Docker vulnerabilities, such as data breaches, financial losses, and reputational damage.
- The value of continuous learning and monitoring to maintain system security and stay updated on emerging threats and best practices.
Docker Security Tools and Solutions
To address Docker vulnerabilities and enhance system security, various tools and solutions are available. These tools offer features such as vulnerability scanning, intrusion detection, and runtime protection. Understanding their benefits and limitations can help you choose the most suitable options for your environment.
Docker Security Scanning Tools
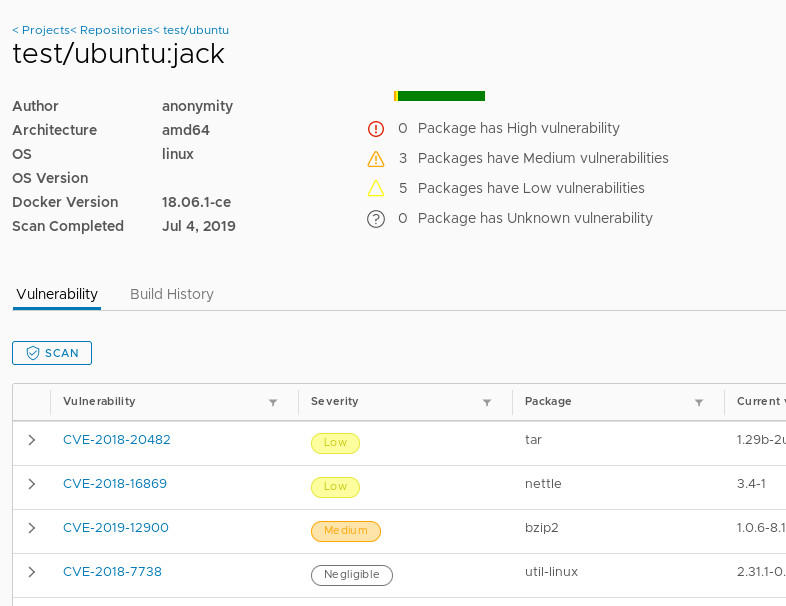
Security scanning tools, like Docker Hub’s vulnerability scanning or third-party solutions like Anchore Engine and Clair, can help identify vulnerabilities in your Docker images. These tools analyze image layers, comparing them against known vulnerabilities in various software packages. By integrating these tools into your CI/CD pipeline, you can automatically scan images before deployment, ensuring a more secure environment.
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS)
IDS and IPS solutions, such as Project Calico and Twistlock, monitor network traffic and container behavior for signs of suspicious activity. These tools can detect and prevent unauthorized access, privilege escalation, and other Docker vulnerabilities. However, they may require additional configuration and management efforts.
Runtime Protection and Monitoring Tools
Runtime protection and monitoring tools, like Aqua Security and Sysdig Secure, provide real-time visibility into container behavior and enforce security policies. These tools can detect and respond to threats, anomalies, and policy violations, ensuring a more secure environment. However, they may introduce performance overhead and require careful tuning to balance security and performance.
Choosing the Right Tools
When selecting Docker security tools and solutions, consider the following factors:
- Integration with your existing infrastructure and tools.
- Ease of use and management.
- Performance overhead and resource requirements.
- Cost and licensing models.
- Community support and documentation.
By carefully evaluating these factors, you can choose the most suitable Docker security tools and solutions for your environment, effectively addressing Docker vulnerabilities and enhancing system security.
The Future of Docker Security: Trends and Challenges
As Docker and containerization technology continue to evolve, new trends and challenges in Docker security will emerge. Staying informed about these developments and implementing proactive measures can help organizations maintain a secure software development environment.
Emerging Trends
Some of the emerging trends in Docker security include:
- Integration of security into container lifecycle management tools.
- Adoption of DevSecOps practices, embedding security into development workflows.
- Increased use of Kubernetes and other container orchestration platforms, requiring specialized security solutions.
- Development of multi-cloud and hybrid cloud strategies, introducing new security considerations and challenges.
Challenges
Alongside these trends, organizations may face several challenges in addressing Docker vulnerabilities, such as:
- Keeping up with the rapidly changing threat landscape and the continuous release of new vulnerabilities.
- Balancing security and agility in fast-paced development environments.
- Addressing the complexity of multi-container and multi-host environments.
- Ensuring compliance with regulatory requirements and industry standards.
Potential Solutions and Research Areas
To address these trends and challenges, organizations can explore potential solutions and research areas, including:
- Automating security testing and vulnerability scanning throughout the container lifecycle.
- Investing in security training and awareness programs for development teams.
- Collaborating with the security community to share best practices and threat intelligence.
- Exploring emerging technologies, such as machine learning and artificial intelligence, to enhance Docker security and threat detection capabilities.
By staying informed about the future of Docker security, organizations can proactively address emerging trends and challenges, ensuring a secure and resilient software development environment.
How to Stay Updated on Docker Vulnerabilities: Resources and Alerts
Staying informed about Docker vulnerabilities and security best practices is crucial for maintaining a secure software development environment. By leveraging various resources and alerts, organizations can ensure continuous learning and monitoring, enabling them to proactively address potential security threats.
Official Docker Security Documentation
Docker provides extensive documentation on security best practices and guidelines. Regularly reviewing and following these recommendations can help organizations keep their Docker environments secure. The official Docker documentation covers topics such as image security, network security, and user privileges.
Docker Security Announcements and Advisories
Subscribing to Docker security announcements and advisories ensures that organizations receive timely updates on newly discovered vulnerabilities and patches. Docker provides security advisories through their official blog, GitHub repository, and security mailing list.
Third-Party Security Resources
Various third-party resources offer valuable insights into Docker vulnerabilities and security best practices. Examples include container security blogs, newsletters, and forums, such as Aqua Security’s Container Security Blog, Sysdig’s Falco project, and the CNCF (Cloud Native Computing Foundation) security working group.
Security Conferences and Webinars
Attending security conferences and webinars focused on containerization technology provides opportunities to learn about the latest trends, threats, and solutions related to Docker security. Events such as DockerCon, KubeCon, and various online webinars offer valuable insights and networking opportunities for security professionals.
Security Training and Certification Programs
Investing in security training and certification programs helps organizations build a security-focused team capable of addressing Docker vulnerabilities effectively. Programs like the Certified Kubernetes Security Specialist (CKS) and the Certified Container Security Professional (CCSP) provide in-depth knowledge and hands-on experience in container security.
By leveraging these resources and alerts, organizations can maintain a proactive approach to Docker security, ensuring a secure and resilient software development environment.
Conclusion: The Importance of Proactive Docker Security
Docker vulnerabilities pose a significant risk to system security, potentially leading to unauthorized access, data breaches, and disrupted services. By adopting a proactive approach to Docker security, organizations can minimize these risks and maintain a secure software development environment.
Addressing Docker Vulnerabilities
To effectively address Docker vulnerabilities, organizations should:
- Stay informed about common Docker vulnerabilities and exploits.
- Implement best practices and recommendations to mitigate these vulnerabilities.
- Leverage Docker security tools and solutions to enhance system security.
- Monitor and learn from real-world examples of Docker vulnerabilities and breaches.
The Value of Proactive Security Measures
Implementing proactive security measures offers several benefits, such as:
- Minimizing the risk of unauthorized access and data breaches.
- Maintaining system availability and reliability.
- Preserving organizational reputation and trust.
- Complying with regulatory requirements and industry standards.
Encouraging a Security-Focused Approach
A security-focused approach in software development should be encouraged, emphasizing the importance of:
- Continuous learning and monitoring to stay updated on Docker vulnerabilities and security best practices.
- Collaboration between development, operations, and security teams to ensure a cohesive security strategy.
- Integrating security into the entire container lifecycle, from development to deployment and maintenance.
By prioritizing proactive Docker security, organizations can protect their systems and data, ensuring a secure and resilient software development environment.