The Role of Docker Image Scanning Tools in Container Security
Docker image scanning tools play a pivotal role in maintaining container security, addressing vulnerabilities, and ensuring compliance with industry standards. As organizations increasingly adopt containerization technologies, the need for robust and efficient image scanning solutions becomes paramount. These tools help identify potential security threats, such as software vulnerabilities, malware, and insecure configurations, in Docker images before they are deployed in production environments.
Continuous monitoring and automation are essential aspects of an effective Docker image scanning strategy. By continuously scanning Docker images throughout the development lifecycle, organizations can proactively detect and remediate security issues, minimizing the risk of breaches and ensuring regulatory compliance. Automation enables security teams to scale their efforts, reducing the manual labor required to assess and secure Docker images.
How to Select the Right Docker Image Scanning Tool
When choosing a Docker image scanning tool, organizations must consider several factors to ensure they select the most suitable solution for their needs. Accuracy, scalability, integration, ease of use, and support are essential aspects to evaluate.
First, accuracy is crucial to ensure that the scanning tool can reliably detect vulnerabilities and other security issues in Docker images. Opt for tools that utilize up-to-date vulnerability databases and offer high precision in their scan results.
Scalability is another key factor, particularly for organizations with large container ecosystems. Select a Docker image scanning tool that can efficiently handle numerous images and maintain performance as your container environment grows.
Integration with existing tools and workflows is vital for seamless adoption. Ensure that the chosen tool can integrate with your CI/CD pipeline, container registry, and other relevant systems.
Ease of use is also an important consideration, as a user-friendly interface and intuitive workflow can reduce the learning curve and enable faster adoption.
Lastly, consider the vendor’s support and maintenance offerings to ensure that the tool will continue to meet your organization’s needs as containerization technologies evolve.
Top Docker Image Scanning Tools in the Market
In the rapidly evolving landscape of containerization technologies, several Docker image scanning tools have emerged as leading solutions. This review highlights the key features, strengths, and weaknesses of Anchore Engine, Clair, Docker Hub Security Scanning, Snyk, and Aqua Security.
Anchore Engine
Anchore Engine is an open-source Docker image scanning tool that offers vulnerability assessment, compliance checking, and policy management. Its modular architecture and extensive API support make it highly customizable and easy to integrate into existing workflows. However, it may require more technical expertise to set up and manage compared to other solutions.
Clair
Clair is another open-source Docker image scanning tool, developed by CoreOS (now owned by Red Hat). Clair specializes in vulnerability detection, leveraging a comprehensive vulnerability database to provide accurate and up-to-date scan results. While it offers powerful features, Clair may have a steeper learning curve and require more technical know-how to use effectively.
Docker Hub Security Scanning
Docker Hub Security Scanning, provided by Docker, is a user-friendly Docker image scanning tool integrated into the Docker Hub platform. It offers vulnerability detection and provides actionable recommendations for remediation. While it is easy to use and requires minimal setup, Docker Hub Security Scanning may not offer the same level of customization and control as other solutions.
Snyk
Snyk is a container security platform that includes Docker image scanning capabilities. It offers vulnerability detection, license compliance, and dependency management. Snyk’s user-friendly interface and seamless integration with popular development tools make it an attractive option for organizations looking for an easy-to-use and comprehensive solution. However, it may not be as extensible or customizable as some open-source alternatives.
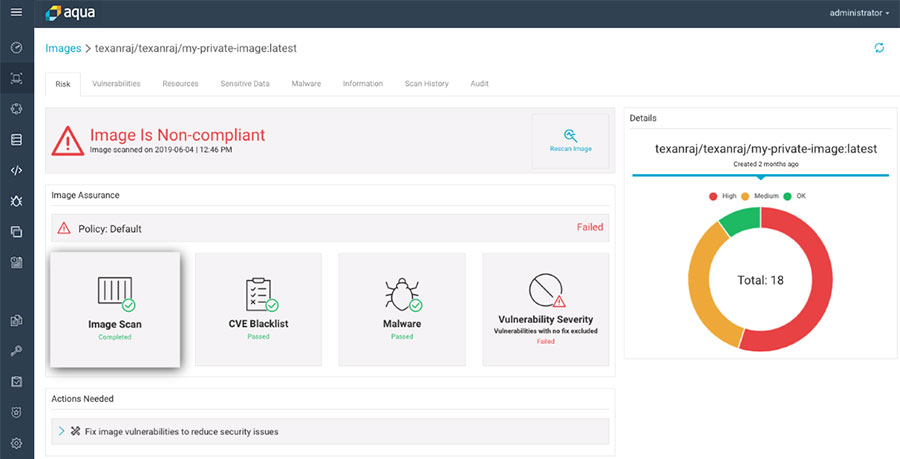
Aqua Security
Aqua Security is a comprehensive container security platform that includes Docker image scanning, runtime protection, and network security features. Its image scanning capabilities offer vulnerability detection, compliance checking, and malware scanning. Aqua Security’s robust feature set and enterprise-focused support make it an ideal solution for large organizations with complex container environments. However, it may be overkill for smaller teams or projects.
Comparing Docker Image Scanning Tools: A Feature-by-Feature Analysis
When evaluating Docker image scanning tools, it’s essential to compare their features and capabilities to determine which solution best fits your organization’s needs. This comparison focuses on vulnerability detection, compliance monitoring, user interface, and pricing.
Vulnerability Detection
Vulnerability detection is a critical feature of Docker image scanning tools. Anchore Engine, Clair, Docker Hub Security Scanning, Snyk, and Aqua Security all provide vulnerability detection capabilities. However, their detection accuracy, coverage, and update frequency may vary. It’s essential to consider these factors when comparing these tools.
Compliance Monitoring
Compliance monitoring is another important aspect of Docker image scanning. Some tools, like Anchore Engine and Aqua Security, offer comprehensive compliance checking features, ensuring that your Docker images adhere to various industry standards and best practices. Others may have limited or no compliance monitoring capabilities.
User Interface
A user-friendly interface can significantly impact the adoption and effectiveness of a Docker image scanning tool. Snyk and Docker Hub Security Scanning are known for their intuitive and easy-to-use interfaces, making them accessible to users with varying levels of technical expertise. In contrast, tools like Clair and Anchore Engine may require more technical know-how to navigate and use effectively.
Pricing
Pricing is a crucial factor for many organizations. Anchore Engine and Clair are open-source tools, making them cost-effective options. Docker Hub Security Scanning is free for up to 100 image scans per month, while Snyk and Aqua Security offer various pricing tiers based on usage and features. Consider your budget and the value provided by each tool when comparing pricing options.
Real-World Use Cases: Success Stories and Lessons Learned
Implementing Docker image scanning tools in real-world scenarios can provide valuable insights into their benefits, challenges, and best practices. This section highlights successful use cases and the lessons learned from organizations that have adopted these tools.
Case Study 1: Large Enterprise Adoption
A multinational corporation implemented Anchore Engine to secure its Docker images across various development teams. By integrating Anchore Engine into their CI/CD pipeline, they achieved continuous monitoring and vulnerability remediation, significantly reducing the risk of security breaches. The key lesson learned was the importance of clear communication and training for development teams to ensure proper tool usage and understanding of security policies.
Case Study 2: Mid-Sized Company Transformation
A mid-sized software development company adopted Snyk to enhance its container security posture. By leveraging Snyk’s user-friendly interface and seamless integration with their existing tools, the company improved vulnerability detection and remediation, leading to increased customer trust. The primary lesson learned was the value of automation in reducing manual security efforts and minimizing the potential for human error.
Case Study 3: Compliance-Driven Implementation
A financial institution implemented Aqua Security to ensure compliance with strict industry regulations. By utilizing Aqua Security’s comprehensive compliance checking features, the organization met regulatory requirements and improved its overall security posture. The key takeaway was the need for thorough planning and coordination between security and compliance teams to achieve desired outcomes.
Integrating Docker Image Scanning Tools with DevOps Workflows
Seamlessly integrating Docker image scanning tools into DevOps workflows is essential for maintaining a secure and efficient development pipeline. By automating the scanning process and incorporating continuous monitoring, organizations can proactively address vulnerabilities and ensure compliance. This section outlines strategies for integrating Docker image scanning tools into DevOps workflows, emphasizing the importance of automation, continuous monitoring, and feedback loops.
Automation
Automating Docker image scanning is crucial for maintaining a secure development pipeline. By integrating scanning tools into your CI/CD pipeline, you can automatically scan images at various stages, such as build, pre-deployment, and deployment. Automation ensures that vulnerabilities are detected and addressed early in the development process, reducing the risk of security breaches and minimizing manual effort.
Continuous Monitoring
Continuous monitoring involves regularly scanning Docker images for vulnerabilities and configuration issues. By continuously monitoring your images, you can quickly detect and remediate security threats, ensuring that your container environment remains secure. Implementing real-time alerting and notifications can help security teams respond to potential threats promptly.
Feedback Loops
Establishing feedback loops between development, security, and operations teams is essential for addressing vulnerabilities and improving the overall security posture. By sharing scan results, recommendations, and best practices, teams can collaborate to resolve security issues and enhance the development pipeline’s security. Implementing tools that support integration with issue tracking systems, such as Jira or GitHub Issues, can help facilitate feedback loops and streamline communication.
Best Practices for Docker Image Scanning and Security
Implementing Docker image scanning tools is an essential step in maintaining container security, but following best practices is equally important. This section outlines strategies for vulnerability prioritization, patch management, and incident response, ensuring that your organization maximizes the benefits of Docker image scanning tools.
Vulnerability Prioritization
With potentially hundreds or thousands of vulnerabilities detected in Docker images, prioritizing remediation efforts is crucial. Focus on high-severity vulnerabilities affecting widely used base images or popular packages. Additionally, consider the context of your application and the likelihood of exploitation when prioritizing vulnerabilities. Tools like Snyk and Anchore Engine provide built-in vulnerability prioritization features, helping security teams focus on the most critical issues.
Patch Management
Regularly updating and patching Docker images is essential for maintaining security. Implement a patch management strategy that includes monitoring for new vulnerabilities, testing patches in staging environments, and deploying patches to production as soon as possible. Automating the patching process can help reduce manual effort and minimize the risk of human error.
Incident Response
Despite best efforts, security incidents may still occur. Develop an incident response plan that outlines the steps to take when a security issue is detected. This plan should include identifying the affected images, isolating them from the production environment, and applying appropriate remediation measures. Regularly review and update your incident response plan to ensure it remains effective and up-to-date.
Future Trends in Docker Image Scanning and Security
As containerization technology continues to evolve, so do the challenges and solutions related to Docker image scanning and security. This section discusses emerging trends in Docker image scanning and security, such as AI-powered threat intelligence, container runtime protection, and Kubernetes security.
AI-Powered Threat Intelligence
Artificial intelligence (AI) and machine learning (ML) are increasingly being applied to threat intelligence, enabling Docker image scanning tools to more accurately predict and identify potential vulnerabilities. AI-powered threat intelligence can help security teams stay ahead of emerging threats by providing real-time, dynamic analysis of Docker images and container environments.
Container Runtime Protection
Container runtime protection involves monitoring and securing containers during runtime, ensuring that any security issues are detected and addressed as they arise. Tools like Aqua Security and Twistlock offer container runtime protection capabilities, providing features such as behavioral analytics, anomaly detection, and automated response.
Kubernetes Security
As Kubernetes becomes the de facto standard for container orchestration, securing Kubernetes clusters and workloads becomes increasingly important. Docker image scanning tools must evolve to support Kubernetes security, providing features such as role-based access control (RBAC), network segmentation, and secret management. Tools like Falco and Kyverno offer Kubernetes-specific security features, helping organizations secure their container environments end-to-end.