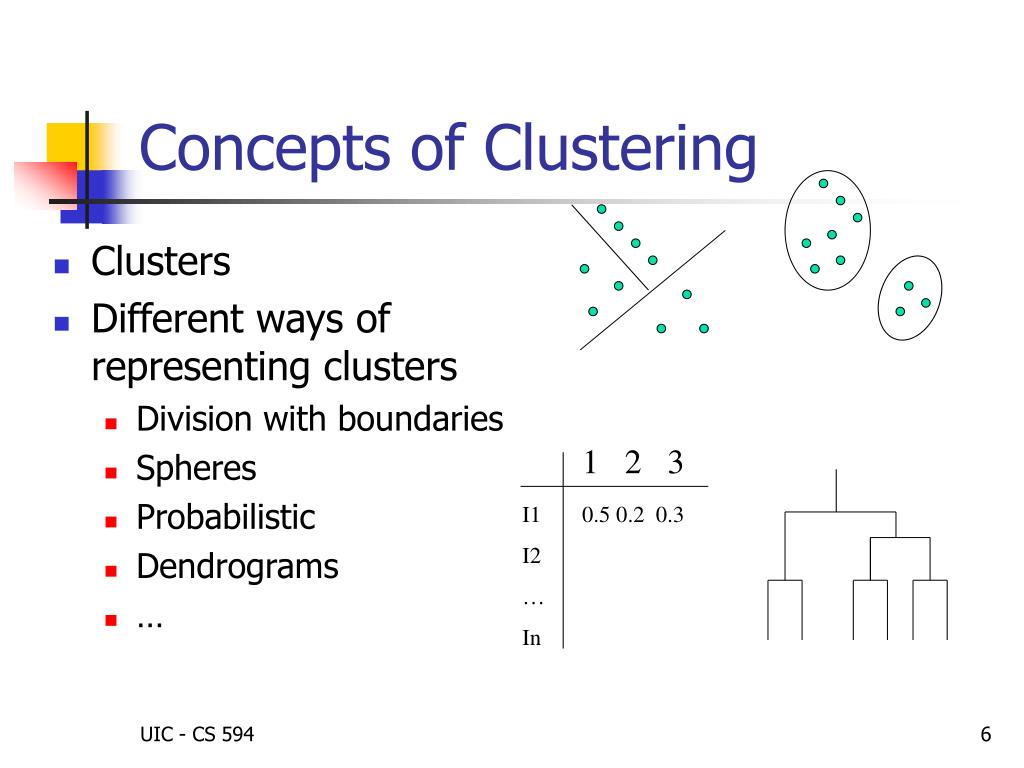
The Concept of Clusters and Their Importance
In the realm of data analysis, networking, and infrastructure management, the term ‘clusters‘ refers to a group of linked computers working together as a single system. The significance of clusters is evident in various applications, such as high-performance computing, load balancing, and fault-tolerant systems. A key process in setting up clusters is ‘create cluster’, which involves configuring individual nodes and establishing communication between them. This guide focuses on the best practices and steps to create cluster, ensuring optimal performance and longevity.
Choosing the Right Cluster Architecture
When it comes to creating clusters, selecting the appropriate architecture is crucial for meeting specific requirements. Various architectures are available, each designed to address unique needs. High-performance clusters, for instance, are tailored for applications demanding extensive computational power, such as scientific simulations or weather forecasting. Load-balancing clusters, on the other hand, distribute workloads evenly across nodes, ensuring consistent performance for applications like web hosting or content delivery.
Fault-tolerant clusters, as the name suggests, prioritize redundancy and failover capabilities, minimizing downtime and data loss for mission-critical applications. These architectures often employ techniques like data replication and real-time monitoring to maintain high availability. By understanding the specific needs and constraints of a project, one can choose the most suitable cluster architecture and optimize the ‘create cluster’ process for success.
Selecting the Ideal Components for Your Cluster
Creating a cluster involves assembling the right components, including hardware, software, and network configurations. The choice of components significantly impacts the cluster’s performance, scalability, and reliability. When planning to create cluster, consider the following:
- Hardware: Select high-quality servers and storage devices, ensuring compatibility and performance. Consider factors like processing power, memory, and network interface cards (NICs) when choosing hardware components.
- Software: Utilize robust cluster management software to streamline administration tasks and maintain system stability. Open-source solutions like OpenMPI, Rocks Cluster, or commercial offerings like Microsoft HPC Pack and IBM Spectrum LSF are popular choices for creating clusters.
- Network configurations: Implement high-speed, low-latency network connections to minimize communication delays between nodes. Opt for technologies like InfiniBand, iWARP, or RoCE, depending on your specific requirements and budget.
By carefully selecting components, you can optimize the ‘create cluster’ process and ensure a reliable, high-performance system tailored to your needs.
How to Create a Cluster: Step-by-Step Guide
Establishing a cluster, or ‘setting up a cluster’, involves several essential steps to ensure optimal performance and reliability. Here’s a comprehensive guide on how to create a cluster:
- Install the operating system: Install a compatible operating system on each node in the cluster. Ensure that all nodes have the same OS version and configuration for consistency.
- Configure network settings: Set up the network connections between nodes, ensuring each node can communicate with others. Configure IP addresses, subnet masks, default gateways, and DNS settings accordingly.
- Install cluster management software: Install a robust cluster management tool to streamline administration tasks and maintain system stability. Popular open-source and commercial solutions include OpenMPI, Rocks Cluster, Microsoft HPC Pack, and IBM Spectrum LSF.
- Register nodes: Register each node in the cluster management software, allowing the system to recognize and manage individual nodes as a cohesive unit.
- Configure shared storage: Set up shared storage devices accessible by all nodes in the cluster. This step is crucial for applications requiring data access from multiple nodes simultaneously.
- Test the cluster: Run tests to ensure that the cluster functions as expected. Monitor resource utilization, network communication, and application performance during the testing phase.
By following these steps, you can successfully create a cluster tailored to your needs, ensuring high performance, scalability, and reliability.
Monitoring and Managing Your Cluster
Monitoring and managing clusters are essential for maintaining optimal performance, longevity, and addressing potential issues before they escalate. Various tools and techniques are available to simplify cluster monitoring and management. Here are some key aspects to consider:
- Resource utilization: Monitor resource utilization, such as CPU, memory, and network usage, to ensure that the cluster operates within acceptable parameters. Tools like Ganglia, Nagios, and Zabbix can help track resource utilization and trigger alerts when thresholds are exceeded.
- Job scheduling: Implement job scheduling tools to manage and prioritize tasks across nodes. Solutions like Slurm, Torque, and Portable Batch System (PBS) can help streamline job scheduling and resource allocation.
- Health monitoring: Continuously monitor the health of individual nodes and the entire cluster. Tools like Pacemaker, Corosync, and Keepalived can help detect node failures and trigger failover mechanisms to maintain high availability.
- Software updates: Regularly update the cluster’s software components, including the operating system, cluster management tools, and application software. Implement a testing and validation process to ensure compatibility and stability before deploying updates in a production environment.
By effectively monitoring and managing clusters, you can ensure high performance, reliability, and a positive user experience. Regularly review monitoring data and adjust management strategies as needed to accommodate changing requirements and optimize cluster efficiency.
Scaling and Expanding Your Cluster
As your data processing needs grow, scaling and expanding your cluster becomes essential. Various scaling strategies can accommodate increasing workloads and maintain optimal performance. Here are some approaches to consider when scaling and expanding your cluster:
- Vertical scaling: Vertical scaling involves adding more resources, such as CPU, memory, or storage, to individual nodes. While this approach can improve performance, it has limitations, as there is a finite limit to how much you can upgrade a single node.
- Horizontal scaling: Horizontal scaling, or scaling out, adds more nodes to the cluster. This approach distributes the workload across a larger number of machines, increasing overall capacity and fault tolerance. Horizontal scaling is often more cost-effective and flexible than vertical scaling, as it allows for the addition of lower-cost, commodity hardware.
- Hybrid scaling: Hybrid scaling combines vertical and horizontal scaling techniques to optimize performance and cost-efficiency. By strategically adding resources to existing nodes and incorporating new nodes, you can create a balanced, scalable cluster tailored to your needs.
When expanding your cluster, consider the following best practices:
- Plan for growth: Anticipate future needs and plan your cluster expansion accordingly. Regularly review resource utilization and performance metrics to identify trends and potential bottlenecks.
- Maintain compatibility: Ensure that new hardware and software components are compatible with the existing cluster infrastructure.
- Test and validate: Before deploying changes in a production environment, thoroughly test and validate the new configuration to ensure compatibility and stability.
By understanding the different scaling strategies and best practices, you can effectively scale and expand your cluster to meet growing demands while maintaining optimal performance and cost-efficiency.
Security Best Practices for Clusters
Security is paramount when creating and managing clusters, as they often handle sensitive data and mission-critical workloads. Implementing robust security measures ensures the confidentiality, integrity, and availability of cluster components and data. Here are some best practices for securing clusters:
- Access control: Implement strict access control policies to regulate user and administrator access to the cluster. Utilize solutions like Lightweight Directory Access Protocol (LDAP), Role-Based Access Control (RBAC), or Access Control Lists (ACLs) to manage permissions effectively.
- Data encryption: Encrypt data at rest and in transit to protect it from unauthorized access. Use encryption algorithms like Advanced Encryption Standard (AES) or Rivest-Shamir-Adleman (RSA) to secure data communication between nodes and storage devices.
- Secure communication: Use secure communication protocols, such as Secure Shell (SSH) or Transport Layer Security (TLS), to encrypt and authenticate network traffic between cluster nodes and external systems.
- Security updates: Regularly apply security updates and patches to the operating system, cluster management software, and application software. Implement a testing and validation process to ensure compatibility and stability before deploying updates in a production environment.
- Intrusion detection and prevention: Deploy intrusion detection and prevention systems to monitor cluster traffic and detect potential security threats. Tools like Snort, Suricata, or Bro can help identify and mitigate malicious activities.
- Security audits: Perform regular security audits to identify vulnerabilities and ensure compliance with security policies and regulations. Utilize tools like OpenSCAP, Nessus, or Nexpose to automate vulnerability scanning and reporting.
By adhering to these security best practices, you can create a secure cluster environment that protects sensitive data and maintains the integrity of your infrastructure. Regularly review and update your security policies to address emerging threats and maintain a secure cluster creation process.