Why Image Scanning is Crucial for Container Security
Containerized applications offer numerous benefits, but deploying insecure images poses significant risks. Vulnerabilities in container images can lead to severe consequences, including data breaches and system compromises. These breaches can result in substantial financial losses, reputational damage, and regulatory penalties. Effective security measures are paramount. Container image scanning tools play a vital role in mitigating these risks by proactively identifying and addressing vulnerabilities before deployment. A robust security strategy is essential. Understanding the different types of scans available is the first step towards building this critical security layer. Proactive vulnerability detection through container image scanning tools is crucial for preventing costly security incidents.
The rise of containerization has brought efficiency, but also expanded the attack surface. Malicious code embedded within seemingly benign images can silently infiltrate systems. Compromised images can expose sensitive data, disrupt operations, and even grant attackers complete control. This underscores the importance of rigorous security checks before deploying any container image into production. Regular scanning, using a comprehensive suite of container image scanning tools, becomes a necessity in a secure DevOps pipeline. Ignoring security best practices can have devastating consequences.
Modern container image scanning tools offer various scan types to address these security threats. These tools use automated processes to thoroughly check for vulnerabilities and malicious code. The insights these tools provide allows developers to proactively address any identified issues. Investing in appropriate container image scanning tools and implementing best practices greatly reduces the risk of security incidents. A proactive approach to container security is cheaper and more efficient than reactive measures.
Understanding Different Types of Container Image Scans
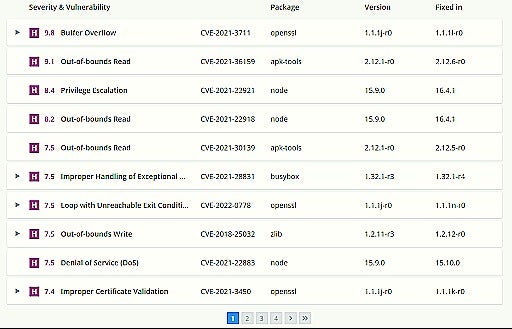
Container image scanning tools offer several scan types to ensure comprehensive security. Vulnerability scans identify known weaknesses in the software components within a container image. These scans leverage databases of known vulnerabilities (CVEs) to pinpoint potential exploits. For example, a vulnerability scan might reveal an outdated version of a library with a known security flaw. This allows developers to address these issues before deployment.
Malware scans, another critical aspect of container image scanning, actively search for malicious code within the image. These scans use various techniques to detect viruses, trojans, and other harmful software. Unlike vulnerability scans that focus on known weaknesses, malware scans detect malicious code regardless of whether it’s been previously identified. This is crucial for catching zero-day exploits and other unknown threats. Effective container image scanning tools often combine both vulnerability and malware scans for complete protection.
Compliance scans verify adherence to specific security standards and regulations. These scans check the container image against established guidelines such as those mandated by industry or government. This ensures that the container meets specific requirements, reducing the risk of non-compliance issues. For example, a compliance scan might check for the presence of specific security configurations or the absence of disallowed software. The importance of compliance scans depends heavily on regulatory requirements and industry best practices. Choosing the right container image scanning tools means selecting a tool that offers the necessary scan types to meet your specific security needs and compliance requirements. Many modern container image scanning tools provide all three types of scans, giving comprehensive analysis.
How to Choose the Right Container Image Scanning Tool for Your Needs
Selecting the optimal container image scanning tool requires careful consideration of several key factors. The size of your organization directly impacts the scale and complexity of your needs. Larger enterprises often require more robust, scalable solutions with advanced features like policy management and compliance reporting. Smaller organizations might find simpler, open-source tools sufficient for their security needs. Budget constraints naturally play a significant role. Open-source container image scanning tools offer a cost-effective alternative, while enterprise-grade solutions often come with licensing fees. However, these costs must be weighed against the potential financial consequences of security breaches.
Seamless integration with existing Continuous Integration/Continuous Delivery (CI/CD) pipelines is crucial for efficient workflow. A tool’s ability to integrate smoothly prevents workflow disruption. It also ensures automated security checks at critical stages of the software development lifecycle. The types of scans required are also a critical consideration. Some tools excel at vulnerability scanning, while others offer broader capabilities encompassing malware detection and compliance checks. Thoroughly assess your organization’s specific security requirements to match your tool selection appropriately. Ease of use and reporting capabilities are equally important. A user-friendly interface simplifies the scanning process, making it accessible to a wider range of team members. Clear, comprehensive reports are crucial for effective security management, enabling swift identification and remediation of vulnerabilities.
The selection of container image scanning tools should not be an afterthought. It’s a cornerstone of a comprehensive security strategy. Choosing the right tool allows organizations to mitigate risks, protect sensitive data, and ensure compliance with industry regulations. Remember, the best tool balances features, cost, and ease of use for your specific requirements. A thorough evaluation process is essential before committing to a particular solution. The right container image scanning tools are key to maintaining a secure container environment. Consider the long-term implications of your decision to ensure it continues to serve your needs as your organization grows and evolves. The process of selecting the right tools directly impacts the effectiveness of your container image security strategy.
Trivy: Open-Source Powerhouse for Vulnerability Detection
Trivy is a popular open-source container image scanning tool known for its speed and ease of use. It excels at vulnerability detection, efficiently scanning various container image types, including those from Docker, OCI, and various archive formats. Trivy’s comprehensive database of known vulnerabilities ensures that scans are thorough and accurate, providing users with detailed reports of potential security risks. The tool’s simple command-line interface makes it accessible to both experienced security professionals and less technical users. Integration into existing CI/CD pipelines is straightforward, allowing for seamless security checks during the software development lifecycle. Its open-source nature fosters community contributions, leading to constant improvements and updates, a crucial aspect for any container image scanning tools.
One of Trivy’s major strengths is its speed. It scans images significantly faster than many commercial alternatives. This makes it ideal for environments with high-volume container deployments where rapid feedback is critical. Furthermore, Trivy’s detailed reports highlight vulnerabilities and their severity levels, providing clear and actionable insights. This allows developers to prioritize remediation efforts and effectively address security risks before deploying containers to production. Trivy supports various scanning modes, enabling customization to suit specific needs and environments. This flexibility, combined with its open-source nature and extensive documentation, solidifies its position as a leading choice among container image scanning tools.
Compared to commercial solutions, Trivy offers a compelling alternative, particularly for smaller organizations or those with limited budgets. Its feature set rivals many paid tools while remaining free and readily available. Trivy’s ability to detect vulnerabilities in various package managers, including those used in diverse programming languages, enhances its versatility. However, while Trivy provides excellent vulnerability scanning, it might lack some advanced features found in enterprise-grade tools like policy management or extensive compliance reporting. Therefore, the choice between Trivy and more comprehensive container image scanning tools depends on the specific needs and security priorities of the organization.
Snyk: Comprehensive Security Platform for Developers
Snyk offers a comprehensive approach to container image scanning, going beyond simple vulnerability detection. This platform integrates seamlessly with popular CI/CD pipelines, allowing developers to incorporate security checks directly into their workflows. Snyk’s strength lies in its ability to identify vulnerabilities not only in container images but also in the code used to build them. This proactive approach helps prevent security issues before they reach production. The platform provides detailed reports, making it easy to understand and address identified vulnerabilities. Snyk’s user-friendly interface makes it accessible to developers of all skill levels, further enhancing its value in the realm of container image scanning tools.
Compared to Trivy, Snyk provides more extensive features. While Trivy excels as a lightweight and open-source option for vulnerability detection in container images, Snyk offers a broader suite of tools that address various aspects of application security. Snyk’s integration capabilities are particularly strong, making it a preferable choice for organizations with established CI/CD pipelines. However, this breadth of functionality comes at a cost; Snyk is a commercial product, unlike the open-source Trivy. The pricing model may be a barrier for smaller organizations or individual developers. Choosing between Snyk and Trivy often depends on budget, organizational size, and the desired depth of security analysis within the context of container image scanning tools.
In contrast to Anchore Engine, Snyk presents a more developer-centric approach to container security. Anchore Engine, as an enterprise-grade solution, prioritizes scalability, policy management, and compliance features. Snyk focuses on ease of use and integration with development workflows. While both are powerful container image scanning tools, their target audiences differ. Snyk caters to developers seeking streamlined integration and comprehensive vulnerability detection, while Anchore Engine targets larger organizations needing robust policy enforcement and advanced compliance capabilities within their broader container security strategy. The choice depends heavily on the specific needs and priorities of the organization utilizing these container image scanning tools.
Anchore Engine: Enterprise-Grade Container Security
Anchore Engine stands out as a robust container image scanning tool specifically designed for enterprise environments. Its comprehensive feature set addresses the complex security needs of large organizations. Policy management capabilities allow administrators to define and enforce security rules, ensuring compliance with internal standards and external regulations. This granular control over image deployments significantly reduces risks. The platform integrates seamlessly with existing CI/CD pipelines, automating the security scanning process and enhancing operational efficiency. This integration streamlines workflows and improves response times to potential threats.
A key advantage of Anchore Engine lies in its ability to perform deep analysis of container images, going beyond simple vulnerability checks. It assesses the overall composition of the image, identifying potential vulnerabilities in the underlying operating system and libraries. This detailed analysis provides a more complete understanding of the security posture of each image. Further, Anchore Engine offers robust compliance features, helping organizations meet industry-specific regulations. Detailed reporting and auditing capabilities aid in demonstrating compliance to auditors and regulators. The platform’s scalability allows it to handle large numbers of images and users, making it suitable for enterprises with extensive container deployments.
Compared to Trivy and Snyk, Anchore Engine offers a more sophisticated and comprehensive approach to container image scanning. While Trivy excels in its simplicity and open-source nature, and Snyk provides strong developer-centric features and integrations, Anchore Engine prioritizes enterprise-level scalability, policy management, and compliance. However, this enhanced functionality often comes with increased complexity and cost. The choice between these tools depends heavily on the specific needs and resources of the organization. A smaller organization might find Trivy or Snyk sufficient, while a large enterprise with complex security requirements would likely benefit from the comprehensive capabilities of Anchore Engine. Ultimately, selecting the right container image scanning tool hinges on carefully assessing organizational requirements and weighing the trade-offs between features, cost, and complexity.
Beyond the Tools: Implementing a Robust Image Security Strategy
While container image scanning tools are essential for identifying vulnerabilities, they represent only one part of a comprehensive container image security strategy. A multi-layered approach is crucial for minimizing risks. This includes using minimal base images, which reduces the attack surface by starting with a smaller, more secure foundation. Regularly updating dependencies is equally important; outdated software often contains known vulnerabilities that attackers can exploit. Implementing secure coding practices from the outset helps prevent vulnerabilities from ever being introduced into the image. These proactive measures, combined with the use of container image scanning tools, significantly improve overall security.
Beyond the code itself, image building processes should be carefully considered. Employing techniques like immutable infrastructure and automated builds helps ensure consistency and repeatability, reducing the chance of human error introducing vulnerabilities. Regularly scanning images with tools like Trivy, Snyk, and Anchore Engine throughout the development lifecycle—from build to deployment—is vital. This allows for early detection and remediation of security flaws. Integrating these scans into your CI/CD pipeline automates the process and ensures that no insecure image reaches production. By consistently employing a combination of proactive and reactive security measures, organizations can build and maintain a robust container image security posture. The power of container image scanning tools lies not just in their individual capabilities, but in their integration into a well-defined security process.
Prioritizing security from the initial stages of development is key. Secure coding practices, like input validation and proper error handling, can prevent many common vulnerabilities. Regular security audits and penetration testing further enhance the overall security posture. These audits provide an independent assessment of security effectiveness and identify any weaknesses missed by automated tools. Remember, while container image scanning tools are indispensable for identifying known vulnerabilities, a holistic approach combining proactive development practices, automated scanning, and regular security assessments provides the strongest defense. This layered strategy ensures that your organization can effectively address the ever-evolving landscape of container security threats.
Staying Ahead of the Curve: Continuous Monitoring and Updates
The security landscape constantly evolves. New vulnerabilities emerge regularly. Therefore, continuous monitoring is crucial for maintaining the security of your containerized applications. Regular container image scanning remains a cornerstone of this process. Employing container image scanning tools, such as Trivy, Snyk, or Anchore Engine, should be an ongoing practice, not a one-time event. These tools help identify newly discovered vulnerabilities in your images before they can be exploited. Proactive identification allows for swift remediation, minimizing risk exposure. Consistent scanning ensures your applications remain protected against evolving threats.
Beyond regular scanning, staying informed about the latest security advisories and best practices is vital. Subscribe to security newsletters and follow industry experts. Regularly update your container image scanning tools themselves. These tools are continuously improved, incorporating support for new technologies and vulnerability databases. Updates frequently enhance their effectiveness and accuracy, ensuring your scans remain comprehensive. Staying informed also extends to adopting secure coding practices and regularly updating dependencies within your applications. These combined efforts form a robust, proactive approach to container image security.
Investing time in a robust container image security strategy yields significant long-term benefits. By actively using container image scanning tools and maintaining awareness of emerging threats, organizations greatly reduce their vulnerability to attacks. This proactive approach not only safeguards valuable data but also strengthens the overall security posture. Implementing and maintaining a strong security strategy is an investment in operational resilience and minimizes costly disruptions. Consistent vigilance and continuous improvement are key to maintaining a secure container environment.