Understanding Computer Containers: A Modern IT Essential
Computer containers have emerged as a critical component of modern IT infrastructure, offering numerous benefits to organizations. Containers enable efficient resource utilization, streamlined application deployment, and improved system stability, making them an essential tool for businesses seeking to optimize their IT operations.
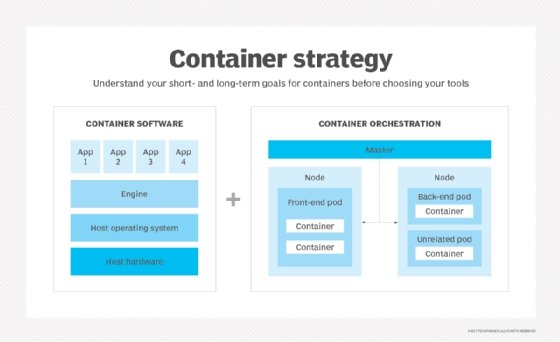
At their core, computer containers are a form of virtualization technology that allows applications and their dependencies to be packaged and isolated from the underlying infrastructure. This packaging ensures consistent application behavior across different computing environments, simplifying application deployment, scaling, and management.
Containers differ significantly from traditional virtual machines (VMs) in their approach to resource sharing and isolation. While VMs virtualize an entire operating system (OS) and all its resources, containers share the host OS and allocate only the necessary resources for each application. This shared approach results in reduced overhead, faster startup times, and more efficient resource utilization compared to VMs.
The growing popularity of computer containers can be attributed to their ability to simplify application development and deployment, enabling organizations to accelerate their digital transformation initiatives. By using containers, businesses can reduce the time and effort required to manage application dependencies, ensure compatibility, and maintain consistent application behavior across diverse computing environments.
As container technology continues to evolve, it is increasingly being integrated with other cutting-edge technologies such as microservices, DevOps, and cloud computing. This integration enables organizations to build highly scalable, resilient, and secure IT infrastructures that can adapt to ever-changing business needs and market conditions.
In summary, computer containers represent a powerful and versatile technology that is revolutionizing the way businesses manage their IT operations. By harnessing the benefits of containerization, organizations can improve their operational efficiency, accelerate application development and deployment, and enhance their overall competitiveness in the digital age.
How Computer Containers Differ from Virtual Machines
Computer containers and virtual machines (VMs) are both popular virtualization technologies, but they differ significantly in their approach to resource sharing, isolation, and application deployment. Understanding these differences is crucial for organizations seeking to optimize their IT infrastructure and choose the most suitable virtualization solution for their needs.
The primary distinction between computer containers and VMs lies in their resource sharing and isolation mechanisms. VMs virtualize an entire operating system (OS) and all its resources, creating a fully isolated environment for each application. In contrast, computer containers share the host OS and allocate only the necessary resources for each application, resulting in reduced overhead and faster startup times.
Container portability is another key differentiator between the two technologies. Computer containers are designed to be highly portable, allowing applications to run consistently across various computing environments. This portability simplifies application deployment, scaling, and management, making containers an attractive option for organizations seeking to streamline their IT operations.
System performance is also impacted by the choice between computer containers and VMs. Containers generally offer better performance than VMs due to their more efficient resource utilization and reduced overhead. However, VMs provide stronger isolation between applications, making them a better choice for scenarios requiring strict security or regulatory compliance.
When deciding between computer containers and VMs, organizations should consider factors such as application requirements, resource utilization, security, and compliance. For applications that demand high portability, efficient resource utilization, and fast startup times, computer containers are often the preferred choice. However, for applications requiring stringent security or regulatory compliance, VMs may be more appropriate due to their stronger isolation capabilities.
In summary, computer containers and virtual machines are distinct virtualization technologies with unique advantages and disadvantages. By understanding the differences between these two solutions, organizations can make informed decisions about which technology best suits their specific business needs and IT infrastructure requirements.
Top Computer Container Solutions in the Market
The market for computer container solutions is rapidly evolving, with several leading platforms offering innovative features and advantages for businesses. This section introduces three of the top computer container solutions available today: Docker, Kubernetes, and Podman.
Docker
Docker is a popular and widely adopted computer container solution, known for its simplicity, flexibility, and extensive ecosystem. Docker enables developers to create, deploy, and manage applications in lightweight, portable containers, making it an ideal choice for organizations seeking to streamline their application development and deployment processes.
Kubernetes
Kubernetes, also known as K8s, is an open-source container orchestration platform designed to automate the deployment, scaling, and management of computer containerized applications. Kubernetes offers advanced features such as self-healing, load balancing, and resource optimization, making it a popular choice for businesses seeking to build and manage complex, scalable IT infrastructures.
Podman
Podman, short for Pod Manager, is an open-source computer container engine and manager that enables developers to build, run, and manage OCI (Open Container Initiative) containers and container images. Podman is particularly well-suited for organizations seeking a lightweight, high-performance container solution that does not require a daemon to operate, providing enhanced security and resource efficiency.
Each of these computer container solutions offers unique features, advantages, and applications, making them suitable for various business needs and IT infrastructure requirements. By understanding the strengths and limitations of each platform, organizations can make informed decisions about which solution best aligns with their specific business objectives and IT strategies.
Selecting the Right Computer Container Solution for Your Business
Choosing the most suitable computer container solution for your business involves careful consideration of various factors, including scalability, security, and ease of use. By evaluating these factors and understanding your specific business needs, you can make an informed decision about which computer container solution best aligns with your IT strategy.
Scalability
Scalability is a critical factor when selecting a computer container solution, particularly for businesses seeking to build and manage complex, scalable IT infrastructures. Kubernetes, for example, offers advanced features such as self-healing, load balancing, and resource optimization, making it an ideal choice for organizations requiring high scalability.
Security
Security is another essential consideration when choosing a computer container solution. Computer containers can introduce new security challenges, such as increased attack surfaces and potential vulnerabilities. To mitigate these risks, businesses should look for container solutions that offer robust security features, such as network segmentation, access control, and vulnerability scanning. Podman, for instance, provides enhanced security by not requiring a daemon to operate, reducing the attack surface and resource overhead.
Ease of Use
Ease of use is a key factor in ensuring a smooth transition to a computer container solution. Docker, with its user-friendly interface and extensive ecosystem, is an excellent choice for businesses seeking a simple, flexible, and accessible container solution. By prioritizing ease of use, organizations can minimize the learning curve and accelerate the adoption of computer container technology.
In summary, selecting the right computer container solution for your business requires careful consideration of factors such as scalability, security, and ease of use. By evaluating these factors and understanding your specific business needs, you can make an informed decision about which computer container solution best aligns with your IT strategy and sets the foundation for a successful containerization journey.
Implementing Computer Containers in Your IT Infrastructure
Integrating computer containers into your existing IT infrastructure can provide significant benefits, including efficient resource utilization, streamlined application deployment, and improved system stability. To ensure a successful implementation, consider the following best practices for deployment, management, and monitoring.
Deployment
When deploying computer containers, it is essential to follow best practices such as using a consistent naming convention, organizing containers into manageable clusters, and ensuring proper resource allocation. By adhering to these practices, organizations can simplify the management and maintenance of their computer container infrastructure.
Management
Effective management of computer containers is crucial for ensuring optimal performance and security. Best practices for computer container management include regularly updating container images, monitoring resource usage, and implementing access control policies. By following these practices, organizations can maintain a secure, stable, and high-performing container infrastructure.
Monitoring
Monitoring computer container performance is essential for identifying and addressing potential issues before they impact system stability or security. Best practices for computer container monitoring include tracking resource utilization, monitoring network traffic, and setting up alerts for performance or security anomalies. By implementing robust monitoring strategies, organizations can proactively manage their computer container infrastructure and ensure optimal performance and security.
In summary, implementing computer containers in your IT infrastructure requires careful consideration of best practices for deployment, management, and monitoring. By following these practices, organizations can ensure a successful transition to computer container technology and maximize the benefits of this innovative IT solution.
Optimizing Computer Container Performance: Tips and Tricks
Computer containers offer numerous benefits, including efficient resource utilization, streamlined application deployment, and improved system stability. To maximize these benefits, it is essential to implement strategies that enhance computer container performance. This section discusses several tips and tricks for optimizing computer container performance, such as efficient resource allocation, container image size reduction, and caching techniques.
Efficient Resource Allocation
Efficient resource allocation is crucial for ensuring optimal computer container performance. By carefully allocating resources like CPU, memory, and storage, organizations can prevent performance bottlenecks and ensure that each container receives the necessary resources to operate effectively. Best practices for resource allocation include monitoring resource usage, setting resource limits, and adjusting resource allocations as needed.
Container Image Size Reduction
Smaller container images can significantly improve computer container performance by reducing the time and resources required for image downloads, transfers, and deployments. Best practices for reducing container image size include minimizing the number of unnecessary dependencies, optimizing build processes, and using multi-stage build strategies.
Caching Techniques
Caching techniques can help improve computer container performance by reducing the time and resources required for container image downloads and deployments. Best practices for caching include using local caching proxies, implementing content delivery networks (CDNs), and leveraging container image layer caching.
In summary, optimizing computer container performance requires careful consideration of strategies such as efficient resource allocation, container image size reduction, and caching techniques. By implementing these tips and tricks, organizations can maximize the benefits of computer container technology and ensure optimal performance, stability, and security.
Securing Computer Containers: Strategies and Tools
Computer containers have become an essential component of modern IT infrastructure, offering numerous benefits such as efficient resource utilization, streamlined application deployment, and improved system stability. However, computer containers also introduce new security challenges, making it crucial for organizations to implement robust security strategies and tools to protect their container infrastructure from potential threats.
Network Segmentation
Network segmentation is a key strategy for securing computer containers, as it helps prevent unauthorized access and lateral movement within the container infrastructure. By dividing the network into smaller, isolated segments, organizations can limit the attack surface and contain potential threats, making it more difficult for attackers to move laterally and compromise additional resources.
Access Control
Access control is another essential strategy for securing computer containers. By implementing strict access control policies, organizations can ensure that only authorized users and processes have access to container resources. Best practices for access control include using role-based access control (RBAC), implementing least privilege principles, and regularly reviewing access logs to detect and respond to potential security incidents.
Vulnerability Scanning
Vulnerability scanning is a critical tool for identifying and addressing potential security threats within computer container infrastructure. By regularly scanning container images, hosts, and registries for known vulnerabilities, organizations can proactively address security risks and maintain a secure container environment. Best practices for vulnerability scanning include using automated scanning tools, integrating scanning into the continuous integration/continuous delivery (CI/CD) pipeline, and prioritizing vulnerabilities based on risk and severity.
In summary, securing computer containers requires a comprehensive approach that includes strategies such as network segmentation, access control, and vulnerability scanning. By implementing these strategies and utilizing the appropriate tools, organizations can protect their container infrastructure from potential threats and maintain a secure, stable, and high-performing container environment.
Staying Updated on Computer Container Innovations and Trends
Computer containers have become an integral part of modern IT infrastructure, offering numerous benefits such as efficient resource utilization, streamlined application deployment, and improved system stability. As container technology continues to evolve, it is essential for organizations to stay informed about the latest innovations and trends to ensure they are leveraging the full potential of computer containers and maintaining a competitive edge in their respective industries.
Industry Resources
Numerous industry resources provide valuable insights and updates on computer container innovations and trends. These resources include industry blogs, news websites, podcasts, and magazines, which cover topics such as new container technologies, best practices, and real-world use cases. By regularly engaging with these resources, organizations can stay informed about the latest developments in the container ecosystem and identify opportunities to optimize their container infrastructure.
Communities and Forums
Communities and forums are another excellent source of information on computer container innovations and trends. These platforms enable organizations to connect with other container enthusiasts, share knowledge and experiences, and learn from experts in the field. By participating in these communities, organizations can gain valuable insights into the latest container technologies and trends, as well as receive feedback and guidance on their container strategies.
Industry Events
Industry events, such as conferences, meetups, and webinars, offer a unique opportunity for organizations to learn about the latest computer container innovations and trends directly from industry leaders and experts. These events provide a platform for organizations to network with other container enthusiasts, engage in discussions and debates, and gain hands-on experience with the latest container technologies. By attending these events, organizations can stay up-to-date on the latest container trends and position themselves as thought leaders in the field.
In summary, staying updated on computer container innovations and trends is crucial for organizations seeking to optimize their container infrastructure and maintain a competitive edge. By engaging with industry resources, communities, and events, organizations can stay informed about the latest container technologies and trends, identify opportunities to enhance their container strategies, and position themselves as thought leaders in the field.