Understanding Collaborative Coding with AWS CodeCommit
AWS CodeCommit emerges as a fully managed source control service, designed to host secure and scalable private Git repositories. This service alleviates the operational burden associated with self-managed Git servers, offering a robust solution for teams seeking to streamline their development workflows. Code Commit AWS integrates seamlessly with other AWS services, fostering a cohesive and efficient development environment.
The benefits of adopting Code Commit AWS extend beyond mere convenience. Scalability is inherent, automatically adjusting to the growing needs of your projects without requiring manual intervention. Security is paramount, with AWS CodeCommit leveraging IAM roles and permissions to control access and protect your valuable code assets. Furthermore, the tight integration with services like AWS CodePipeline and AWS CodeBuild enables automated continuous integration and continuous delivery (CI/CD) pipelines, accelerating software release cycles.
When comparing AWS CodeCommit to other popular version control systems like GitHub and GitLab, the distinctions become clear. While GitHub and GitLab offer broader ecosystems with extensive community features and public repositories, AWS CodeCommit excels within the AWS ecosystem. Its native integration with AWS services simplifies deployments, enhances security through IAM, and ensures data residency within the AWS infrastructure. For organizations heavily invested in AWS, Code Commit AWS provides a compelling advantage, offering a secure, scalable, and deeply integrated source control solution tailored to their specific needs. Choosing the right version control system depends on your project’s requirements, team’s familiarity, and the desired level of integration with your existing infrastructure. However, for AWS-centric development, Code Commit AWS presents a powerful and efficient option.
Setting Up Your AWS CodeCommit Repository: A Step-by-Step Approach
Creating a new repository in code commit aws is a foundational step toward leveraging its benefits. This process can be achieved through several methods, each catering to different preferences and levels of automation. The AWS Management Console offers a user-friendly graphical interface for creating a repository. Alternatively, the AWS Command Line Interface (CLI) provides a more programmatic approach, ideal for scripting and automation. CloudFormation allows infrastructure-as-code deployment, ensuring consistency and repeatability in repository creation. No matter what, the process to setup a repository in code commit aws is easy and fast.
Regardless of the method chosen, defining appropriate IAM roles and permissions is crucial. These roles determine who can access the code commit aws repository and what actions they can perform. Implementing the principle of least privilege is paramount; grant users only the minimum permissions necessary to fulfill their responsibilities. This approach minimizes the risk of unauthorized access or accidental data modification. A well-defined IAM policy specifies the resources (the repository), the actions allowed (e.g., read, write, delete), and the users or groups to whom the policy applies. Permissions can be set for individual users or, preferably, for groups of users with similar roles. For example, developers might have read and write access, while a build server might only have read access. Securing your AWS resources is a shared responsibility, with AWS providing the tools and best practices, and users responsible for implementing them effectively. The AWS CLI commands or CloudFormation templates used for repository creation should include configurations for encryption at rest, further safeguarding the code.
To secure the code commit aws repository, it’s vital to enable encryption both at rest and in transit. Encryption at rest ensures that the data stored within the repository is protected, while encryption in transit secures the data as it moves between the user and the repository. AWS CodeCommit integrates seamlessly with AWS Key Management Service (KMS) for managing encryption keys. Regularly review and update security configurations. This proactive approach ensures ongoing protection against potential vulnerabilities. Access keys should be managed and rotated to prevent unauthorized access. Multi-Factor Authentication (MFA) should be enforced for all users accessing the repository, adding an extra layer of security. Comprehensive monitoring and auditing mechanisms should be implemented to track access and modifications to the repository, enabling prompt detection and response to any suspicious activity. Following these best practices strengthens the security posture of your AWS CodeCommit repositories. You protect sensitive code effectively with code commit aws.
How to Perform Essential Git Operations in AWS CodeCommit
Performing essential Git operations within AWS CodeCommit is crucial for effective code management. This section outlines how to execute fundamental tasks using either the AWS CLI or a Git client, ensuring a smooth workflow when using code commit aws. These operations include cloning, adding, committing, branching, merging, and resolving conflicts, all essential for collaborative software development within the AWS ecosystem.
Cloning an AWS CodeCommit repository allows you to create a local copy for development. Use the `git clone` command followed by the repository’s clone URL, which can be found in the AWS Management Console. Once cloned, you can add changes using `git add`, stage them for commit, and then commit these changes with `git commit -m “Your commit message”`. Branching in code commit aws is equally straightforward. Use `git branch
Efficient code management in code commit aws also includes adhering to best practices. Employ descriptive commit messages to clearly convey the purpose of each change. Regularly pull updates from the remote repository using `git pull` to stay synchronized with the team’s work. When working on features, create dedicated branches to avoid directly committing to the main branch. Code reviews can be integrated into your workflow by using pull requests, allowing team members to review and approve changes before they are merged. Understanding these Git operations and adopting recommended practices will significantly enhance your ability to collaborate effectively and maintain code quality within AWS CodeCommit.
Securing Your Code with AWS CodeCommit: Best Practices
Securing your code within AWS CodeCommit is paramount for maintaining confidentiality, integrity, and availability. Implementing robust security measures protects sensitive data and prevents unauthorized access. This involves leveraging the features offered by both AWS CodeCommit and the broader AWS ecosystem. A fundamental aspect of securing your code commit aws repositories is the use of IAM policies. IAM policies define who can access the repository and what actions they can perform. By adhering to the principle of least privilege, you grant users only the necessary permissions, minimizing the potential attack surface. Regular reviews and updates to IAM policies are crucial to adapt to changing security needs and address emerging threats. Encryption is another critical component of a comprehensive security strategy for code commit aws. AWS CodeCommit encrypts your repositories at rest using AWS Key Management Service (KMS). This ensures that your code remains protected even if the underlying storage is compromised. Data in transit is also encrypted using HTTPS, safeguarding your code during transmission.
Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple authentication factors. Enabling MFA for all users accessing AWS CodeCommit significantly reduces the risk of unauthorized access due to compromised passwords. Regularly rotating access keys is also essential for maintaining a secure environment for your code commit aws. Access keys should be treated as highly sensitive credentials and rotated periodically to limit the impact of potential key compromise. AWS provides tools and services to automate access key rotation, simplifying the management process. In addition to these core security measures, consider implementing code review processes to identify and address potential security vulnerabilities before code is committed to the repository. Code reviews can help catch common coding errors and security flaws that might otherwise go unnoticed. Furthermore, regularly auditing your AWS CodeCommit environment helps ensure that your security controls are effective and compliant with relevant security standards and regulations.
Effective management of your code commit aws repositories includes proactive monitoring and logging. AWS CloudTrail can be used to track API calls made to AWS CodeCommit, providing valuable insights into user activity and potential security incidents. By analyzing CloudTrail logs, you can detect suspicious behavior and respond promptly to security threats. Implementing these best practices will significantly enhance the security posture of your AWS CodeCommit repositories, protecting your valuable code assets from unauthorized access and malicious attacks. Remember that security is an ongoing process, requiring continuous vigilance and adaptation to evolving threats. By prioritizing security within your code commit aws workflow, you can ensure the long-term confidentiality, integrity, and availability of your software projects.
Integrating AWS CodeCommit with Other AWS Services for Automated Workflows
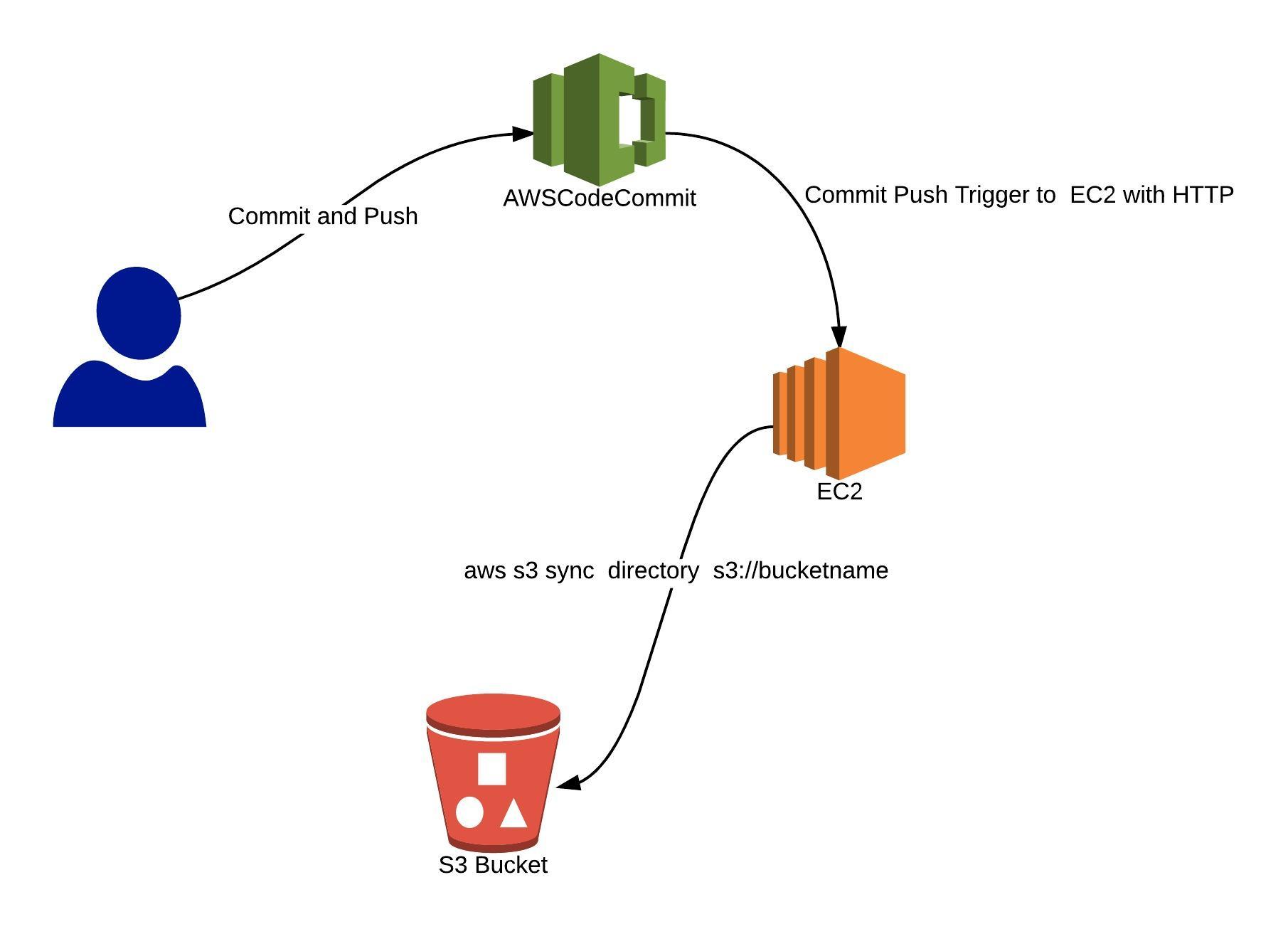
AWS CodeCommit’s true power lies in its seamless integration with other AWS services. These integrations create automated CI/CD pipelines, leading to faster and more reliable software releases. By connecting CodeCommit with services like AWS CodePipeline, AWS CodeBuild, AWS CodeDeploy, and AWS Lambda, development teams can automate every stage of the software development lifecycle. This creates a streamlined and efficient workflow. The integration of code commit aws unlocks possibilities for continuous integration and continuous delivery.
AWS CodePipeline orchestrates the entire release process, automatically building, testing, and deploying code changes whenever updates are committed to the CodeCommit repository. AWS CodeBuild handles the compilation, testing, and packaging of the application code. AWS CodeDeploy automates the deployment of applications to various environments, such as EC2 instances, Lambda functions, or on-premises servers. AWS Lambda can be triggered by CodeCommit events. It is used to automate tasks like code analysis, security checks, or notifications. These integrations greatly improve the code commit aws experience.
Consider a scenario where a developer commits a code change to the AWS CodeCommit repository. This triggers a CodePipeline pipeline. CodeBuild compiles and tests the code. Then CodeDeploy deploys it to a staging environment for further testing. Upon successful testing, CodeDeploy deploys the code to the production environment. The entire process is automated. It reduces manual intervention and minimizes the risk of errors. Configurations vary based on specific needs. For example, a serverless application could use Lambda for deployments. A web application might deploy to EC2 instances using CodeDeploy. Code commit aws benefits from the power of the aws ecosystem.
Troubleshooting Common Issues When Using AWS CodeCommit
Encountering issues while working with code commit aws is not uncommon. Permission errors frequently arise when IAM roles are not correctly configured. Users might face “Access Denied” messages, indicating that the IAM role lacks the necessary permissions to perform specific actions. The first step is to verify the IAM policy attached to the user or role. Ensure that the policy grants the required permissions for code commit aws operations, such as `codecommit:GetRepository`, `codecommit:GitPull`, and `codecommit:GitPush`. Double-check the resource ARNs in the policy to confirm they match the AWS CodeCommit repository being accessed. When troubleshooting, the AWS Management Console and AWS CLI offer valuable error messages that pinpoint the source of the problem. Regularly reviewing IAM configurations is vital for maintaining secure access to code commit aws repositories.
Authentication problems can also disrupt the workflow with code commit aws. These issues often stem from incorrect credential configurations or expired credentials. When using the AWS CLI, ensure that the AWS CLI is configured with valid credentials. Employ `aws configure` to set the access key ID, secret access key, and default region. For Git clients, configure the credential helper to manage authentication with AWS CodeCommit. Credential helpers streamline the authentication process, eliminating the need to repeatedly enter credentials. Connection issues, such as timeouts or inability to connect to the repository, might indicate network problems or incorrect repository URLs. Verify the network connectivity and confirm that the repository URL is accurate. Firewalls or security groups might be blocking access to the AWS CodeCommit endpoint. Review the network configuration to ensure that traffic to AWS CodeCommit is allowed.
Merge conflicts are an inherent part of collaborative coding, and effectively resolving them is crucial. When merge conflicts arise, carefully examine the conflicting changes and determine the correct resolution. Utilize Git tools, such as `git diff` and `git merge –tool`, to analyze the differences and resolve conflicts interactively. Communicate with other developers involved in the merge to understand the reasoning behind their changes. After resolving the conflicts, thoroughly test the changes to ensure that they function as expected. Committing the resolved merge provides a clean history and facilitates collaboration. Proactive communication and meticulous conflict resolution enhance code quality and team efficiency when using code commit aws.
Optimizing Your AWS CodeCommit Workflow for Enhanced Productivity
Strategies for optimizing your AWS CodeCommit workflow are crucial for enhanced productivity. Implementing branch protection rules is paramount. These rules prevent accidental or unauthorized modifications to critical branches, such as the main or release branches. Code review processes are equally important. They ensure that all code changes are thoroughly reviewed by multiple team members before being integrated into the main codebase. This helps identify potential bugs, improve code quality, and promote knowledge sharing within the team. Consistent commit message conventions are also essential. Well-formatted commit messages provide a clear history of changes, making it easier to understand the evolution of the codebase and troubleshoot issues. Using these strategies improves the collaborative development environment when using code commit aws.
Collaboration and communication within the development team are vital for ensuring code quality and consistency when using code commit aws. Tools like pull requests and code review workflows facilitate open discussions about code changes. These discussions help identify potential problems early on and ensure that all team members are aligned on the direction of the project. Establish and enforce coding standards that are crucial. These standards promote consistency across the codebase, making it easier to read, understand, and maintain. Automated code quality checks can be integrated into the development workflow using Git hooks. Git hooks are scripts that run automatically before or after certain Git events, such as commits or pushes. These hooks can be used to enforce coding standards, run tests, and prevent code that does not meet quality requirements from being committed. All these contribute to using code commit aws.
Leveraging Git hooks is an effective way to automate code quality checks and enforce coding standards within your code commit aws workflow. For example, a pre-commit hook can be used to run linters and style checkers to ensure that the code adheres to the established coding standards. A pre-push hook can be used to run unit tests and integration tests to verify that the changes do not introduce any regressions. By automating these checks, you can reduce the burden on developers and ensure that only high-quality code is committed to the repository. Regularly reviewing and refining your workflow is essential to ensure that it remains effective and efficient. Encourage feedback from team members and be open to making changes based on their suggestions. By continuously optimizing your workflow, you can improve productivity, reduce errors, and deliver high-quality software faster when using code commit aws.
Migrating Existing Git Repositories to AWS CodeCommit
Migrating existing Git repositories to AWS CodeCommit is a common task for organizations adopting AWS for their source control needs. This process allows teams to leverage the benefits of a fully-managed, secure, and scalable code commit aws service. The migration typically involves transferring repositories from platforms like GitHub, GitLab, Bitbucket, or even self-hosted Git servers. A well-planned migration ensures minimal disruption to development workflows and preserves the integrity of the code history.
The migration process generally consists of several key steps. First, the existing Git repository needs to be prepared for export. This might involve cleaning up unnecessary branches or tags to reduce the size of the repository. Next, a new repository must be created within AWS CodeCommit. This can be done via the AWS Management Console, the AWS CLI, or through infrastructure-as-code tools like CloudFormation. It’s crucial to configure the appropriate IAM roles and permissions to control access to the new code commit aws repository. Once the CodeCommit repository is ready, the existing Git repository can be mirrored or cloned into the new repository. Git commands like ‘git clone –mirror’ are useful for creating a complete copy of the source repository, including all branches and tags. Finally, after pushing the code to AWS CodeCommit, it’s important to verify that the migration was successful by checking out branches, reviewing commit history, and testing any build or deployment processes that rely on the repository.
However, migrating Git repositories to AWS CodeCommit can present certain challenges. Large repositories with extensive histories can take significant time and bandwidth to transfer. Network connectivity and bandwidth limitations can impact the speed of the migration. Repositories with numerous large binary files may require special handling. Security considerations are also paramount during the migration. Ensuring that credentials and access keys are securely managed is crucial to prevent unauthorized access to the code. Careful planning and execution are key to a smooth and successful migration to code commit aws, allowing organizations to fully utilize the advantages of AWS’s source control service. Furthermore, it’s important to inform the development team about the migration and provide them with the necessary instructions and support to adapt to the new environment. This includes updating their local Git configurations and familiarizing themselves with the AWS CodeCommit workflow. Thorough testing and validation after the migration are essential to ensure that all systems and processes are working as expected.